We're excited to announce the release of #Fedify 1.6.1, which marks the beginning of the 1.6 series following the retraction of version 1.6.0. This release introduces significant new capabilities that expand Fedify's deployment options and enhance security compatibility across the #fediverse.
🌐 Cloudflare Workers support
Fedify 1.6 introduces first-class support for Cloudflare Workers, enabling #serverless deployment of #ActivityPub applications at the edge.
New components
Key features
- Seamless integration with #Cloudflare's serverless runtime
- Automatic handling of queue message processing through Workers'
queue() method - Support for Node.js compatibility flag required for Fedify's cryptographic operations
- Manual queue processing via
Federation.processQueuedTask() method
For a complete working example, see the Cloudflare Workers example in the Fedify repository.
🏗️ Federation builder pattern
Fedify 1.6 introduces the FederationBuilder class and createFederationBuilder() function to support deferred federation instantiation. This pattern provides several benefits:
- Deferred instantiation: Set up dispatchers and listeners before creating the federation object
- Better code organization: Avoid circular dependencies and improve project structure
- Cloudflare #Workers compatibility: Accommodates binding-based architectures where resources are passed as arguments rather than globals
- Modular setup: Build complex federations piece by piece before instantiation
The builder pattern is particularly useful for large applications and environments like Cloudflare Workers where configuration data is only available at runtime.
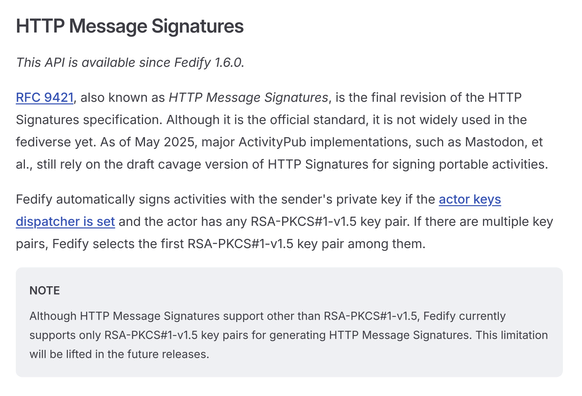
🔐 HTTP Message Signatures (RFC 9421)
Fedify 1.6 implements the official HTTP Message Signatures standard (RFC 9421) specification, the final revision of the HTTP Signatures specification.
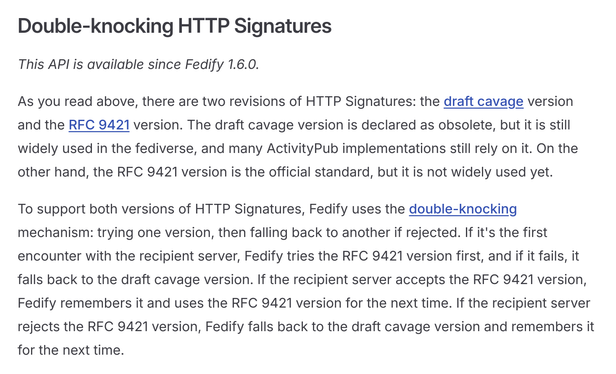
Double-knocking mechanism
To ensure maximum compatibility across the fediverse, Fedify 1.6 introduces an intelligent double-knocking mechanism:
- Primary attempt: RFC 9421 (HTTP Message Signatures) for modern implementations
- Fallback: Draft cavage version for legacy compatibility
- Adaptive caching: The system remembers which version each server supports to optimize future requests
This approach ensures seamless communication with both modern and legacy ActivityPub implementations while positioning Fedify at the forefront of security standards.
Interoperability testing
The RFC 9421 implementation has been thoroughly tested for interoperability with existing ActivityPub implementations that support RFC 9421 signature verification:
- Mitra 4.4.0: Successfully verified Fedify-generated RFC 9421 signatures
- Mastodon 4.4.0 development version: Tested RFC 9421 signature verification against Fedify's implementation (refer to Mastodon PR #34814, though Mastodon 4.4.0 has not yet been released)
These tests confirm that other ActivityPub implementations can successfully verify RFC 9421 signatures generated by Fedify, ensuring proper federation as the ecosystem gradually adopts the official specification. While these implementations currently support verification of RFC 9421 signatures, they do not yet generate RFC 9421 signatures themselves—making Fedify one of the first ActivityPub implementations to support both generation and verification of the modern standard.
🔍 WebFinger enhancements
Dedicated WebFinger lookup
The new Context.lookupWebFinger() method provides direct access to WebFinger data, offering developers more granular control over account discovery and resource resolution beyond the higher-level Context.lookupObject() method.
🛠 Context API improvements
Context data replacement
The new Context.clone() method enables dynamic context data replacement, providing greater flexibility in request processing and data flow management. This is particularly useful for middleware implementations and complex request routing scenarios.
🚀 Migration considerations
Backward compatibility
Fedify 1.6 maintains full backward compatibility with existing applications. The new HTTP Message Signatures and double-knocking mechanisms work transparently without requiring any code changes.
Node.js version requirement
Important: Fedify 1.6 requires Node.js 22.0.0 or later for Node.js environments. This change does not affect applications using Deno or Bun runtimes. If you're currently using Node.js, please ensure your environment meets this requirement before upgrading.
New deployment options
For new deployments, consider leveraging Cloudflare Workers support for:
- Global edge deployment with low latency
- Serverless scaling and automatic resource management
- Integration with Cloudflare's ecosystem of services
🎯 Looking forward
Fedify 1.6 represents a significant expansion of deployment possibilities while maintaining the framework's commitment to broad compatibility across the fediverse. The addition of Cloudflare Workers support opens new architectural patterns for federated applications, while the RFC 9421 implementation ensures Fedify stays current with emerging ActivityPub security standards.
For detailed migration guides, API documentation, and examples, please visit the Fedify documentation. Join our community on Matrix or Discord for support and discussions.
#fedidev #RFC9421 #HTTPSignatures #HTTPMessageSignatures #CloudflareWorkers