Welcome to my new followers. I have taken possession of your souls, for which I am eternally grateful.
By way of #introduction, here are a few things that I am sometimes known for:
I wrote the book API Security in Action published by Manning. It covers a lot about modern application security, JWTs, OAuth, Kubernetes, and is secretly a tutorial on cryptography in disguise.
I discovered the “Psychic Signatures” critical vulnerability in Java’s implementation of ECDSA signature verification (CVE-2022-21449).
My blog has made its way onto Hacker News a few times.
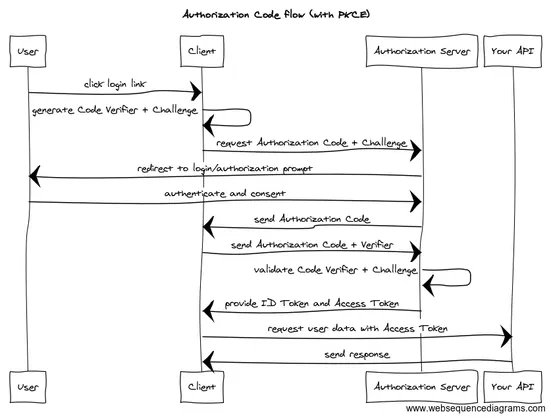
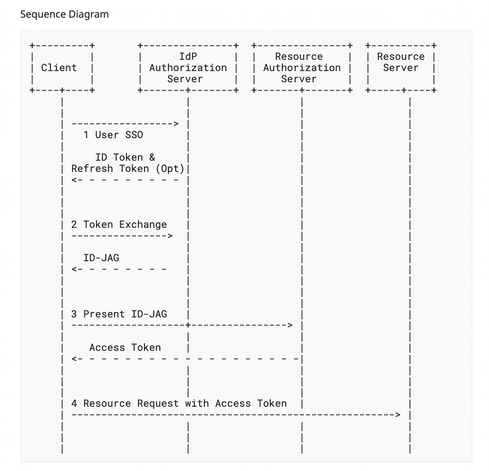
I’m fairly active in the #OAuth working group at the IETF. I used to be the Security Architect for ForgeRock (now part of Ping Identity).
In my past I have mostly been a software engineer. I also have a PhD in computer science, for what it’s worth, but only my bank calls me Dr and my daughter thinks I’m lying about that.
These days I run a company, Illuminated Security, that provides AppSec and Applied Cryptography consultancy, review, bespoke development, and training. I’m always happy to answer emails (eventually!) on most topics.


 Qiita - 人気の記事
Qiita - 人気の記事