pandoc
@pandoc@fosstodon.org
There is now an up-to-date pandoc-wasm package available on npm.
The credit for this goes to @gws and @johanneswilm thanks a lot!
@pandoc@fosstodon.org
There is now an up-to-date pandoc-wasm package available on npm.
The credit for this goes to @gws and @johanneswilm thanks a lot!
@LAYERED@oldbytes.space
Originally, I just wanted a few SF Symbol icons for my #Previous Admin. And then somehow it got completely out of hand. The result is a #React #Package that provides all 6,984 SF Symbols from Apple's Mac App in version 7 as React components. The screenshot shows the interactive preview page that comes with the package.
Here you can find a live demo of that webpage:
https://sfsymbolslib.layered.work
#WebDev #WebDevelopment #TypeScript #Emulator #RetroComputing #npm #SFSymbols

@hongminhee@hollo.social
Is it just me, or is #npm's trusted publishing unnecessarily rigid? Only one workflow filename allowed per package. It's like they never imagined a project having multiple release branches or evolving CI structures. Moving from build.yaml to publish.yaml shouldn't be this annoying. 😩
@Odaeus@vivaldi.net
Thinking of switching to #Proton as #Bitwarden has more and more stupid bugs that indicate a lack of any QA process. Seriously undermining my confidence that they won't be breached soon; especially with their giant #NPM graph.
Now I see they are using LLMs to write code (https://github.com/bitwarden/clients/blob/main/.claude/CLAUDE.md). That I know this is of course a benefit of #opensource but it's not really something I want to see in my password manager.
@Odaeus@vivaldi.net
Thinking of switching to #Proton as #Bitwarden has more and more stupid bugs that indicate a lack of any QA process. Seriously undermining my confidence that they won't be breached soon; especially with their giant #NPM graph.
Now I see they are using LLMs to write code (https://github.com/bitwarden/clients/blob/main/.claude/CLAUDE.md). That I know this is of course a benefit of #opensource but it's not really something I want to see in my password manager.
@nullagent@partyon.xyz · Reply to nullagent's post
Just checked back on the Sha1-Hulud virus/worm. FINALLY npm appears free of obviously infected packages.
I still however am seeing infected machines posting their private data publicly on GitHub.
Not only that, I can see infected developer's github repos are being defaced in realtime.
These microsoft owned platforms seem to be really struggling with stopping this worm.
Query for defaced repos 👇🏿
https://github.com/search?q=api.airforce&type=repositories&s=updated&o=desc
#NPM #microsoft #github #Sha1Hulud #WalkWithoutRhythm #cybersecurity
@nullagent@partyon.xyz · Reply to nullagent's post
I was able to track down 3 out of the remaining 5 affected packages and posted bug reports & security alerts to those developers I located.
Sure would be nice if NPM and GitHub did this automatically.... kinda feel like I've done an awful lot of free labor for Microsoft this week.
https://github.com/datapartyjs/walk-without-rhythm/issues/13
@nullagent@partyon.xyz · Reply to nullagent's post
Is NPM still dangerous?
Yes, we're down to five known infected packages still circulating on the Microsoft owned platform.
The following five packages continue to spread the Sha1-Hulud worm with no warning at all on the NPM page nor at download/install time:
hyper-fullfacing 1.0.3
@ifelsedeveloper/protocol-contracts-svm-idl 0.1.2
quickswap-ads-list 1.0.33
@seung-ju/react-native-action-sheet 0.2.1
tcsp 2.0.2
@nullagent@partyon.xyz · Reply to nullagent's post
Running my NPM checks again today, I see eight remaining infected packages still circulating on the Microsoft owned platform.
Unlike nodejs package index https://socket.dev NPM does not show ANY security warnings on these package's pages.
It's pretty wild that these known compromised packages have been circulating for four days now with now response or action from Microsoft despite it being one of the largest security stories this month.
@nullagent@partyon.xyz · Reply to nullagent's post
Now that the acute phase is slowing there's a VERY important question...
What is actual fucking value does Microsoft (a trillion dollar company) owning GitHub & NPM bring at all?
This shit was an absolute corporate buyout disaster. How the ever living fuck has microsoft owned NPM for FIVE years and still not done proper MFA requirements for publishing packages on NPM.
How the actual fuck are well known vulnerable packages STILL being propagated by NPM.
@nullagent@partyon.xyz · Reply to nullagent's post
Running my NPM checks again today, I see eight remaining infected packages still circulating on the Microsoft owned platform.
Unlike nodejs package index https://socket.dev NPM does not show ANY security warnings on these package's pages.
It's pretty wild that these known compromised packages have been circulating for four days now with now response or action from Microsoft despite it being one of the largest security stories this month.
@nullagent@partyon.xyz · Reply to nullagent's post
These sorts of NPM worms have been around for a LONG time.
It's typically due a common practice of low 2fa opt-in on NPM accounts.
So be sure to setup NPM 2FA if you're a package maintainer do that asap!
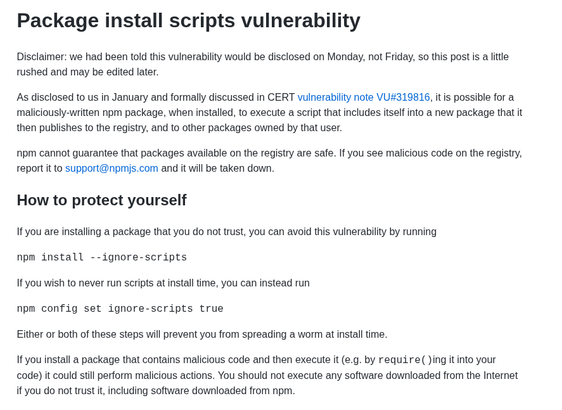
A lesser known NPM capability is that you can disable install time scripts. This may break some packages but its worth a try to see if your projects can work with out any install scripts. 👇🏿
https://blog.npmjs.org/post/141702881055/package-install-scripts-vulnerability
@nullagent@partyon.xyz · Reply to nullagent's post
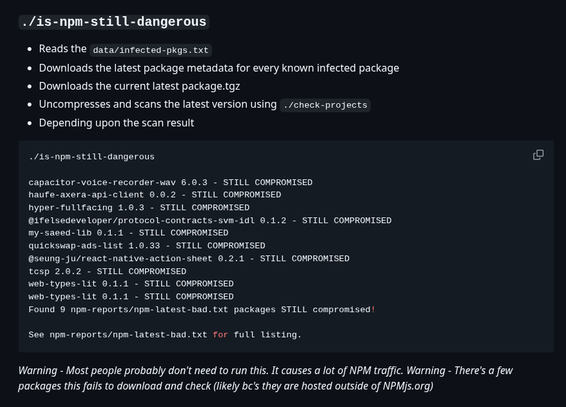
Just finished writing another tool, now I can see NINE known compromised packages are still up for download on NPM! ⚠️
This tool crawls the list of known bad packages and downloads the latest bundle.
It then runs my other checks against the downloaded bundle and logs the results.
https://github.com/datapartyjs/walk-without-rhythm
#WalkWithoutRhythm #Sha1Hulud #NPM #GitHub #Microsoft #nodejs #javascript #cybersecurity #devlog #bash
@nullagent@partyon.xyz · Reply to nullagent's post
Just finished writing another tool, now I can see NINE known compromised packages are still up for download on NPM! ⚠️
This tool crawls the list of known bad packages and downloads the latest bundle.
It then runs my other checks against the downloaded bundle and logs the results.
https://github.com/datapartyjs/walk-without-rhythm
#WalkWithoutRhythm #Sha1Hulud #NPM #GitHub #Microsoft #nodejs #javascript #cybersecurity #devlog #bash

@nullagent@partyon.xyz · Reply to nullagent's post
I've spent the last few hours writing down my scripts for detecting this so you can use them!
I'm hitting on two or three ways to detect it and will be adding more.
Watching the attack running I can see developers all over the world still doing their morning `npm i` and getting owned 😭
Maybe let the node developers in your life know about this tool 👇🏿
https://github.com/datapartyjs/walk-without-rhythm
#ShaiHulud #WalkWithoutRhythm #nodejs #javascript #npm #github #cybersecurity
@nullagent@partyon.xyz · Reply to nullagent's post
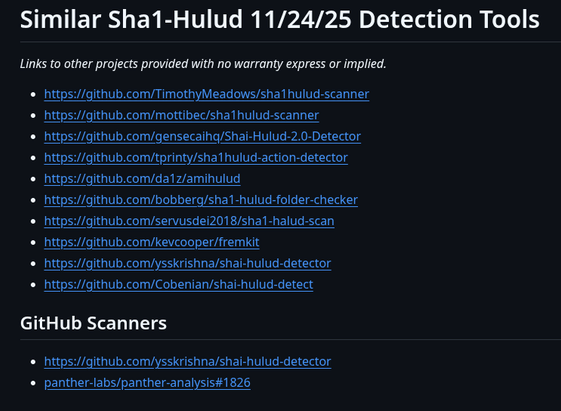
Updated my listing of Sha1-Hulud detection tools.
I now have found at least 12 other tools for detecting Sha1-Hulud compromise on your dev box and in infrastructure.
#WalkWithoutRhythm #Sha1Hulud #npm #github #nodejs #javascript #cybersecurity #devops
@nullagent@partyon.xyz · Reply to nullagent's post
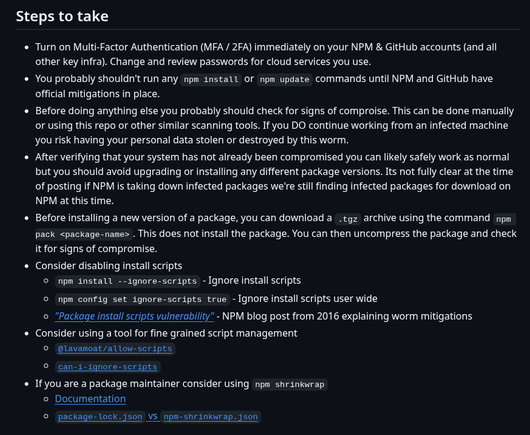
I've updated my suggestions to include links and info on how to get fine grained control over the scripts your projects run at compile time.
There's two fairly interesting community projects that seem to address this part of the problem and make it possible to disable most install scripts while keeping the ones your project actually requires.
https://github.com/datapartyjs/walk-without-rhythm?tab=readme-ov-file#steps-to-take
@nullagent@partyon.xyz
#Breaking There's an active nodejs supply chain attack going around.
From the looks of it many of these compromised packages have been mitigated but quite a few have not.
https://helixguard.ai/blog/malicious-sha1hulud-2025-11-24
#nodejs #cybersecurity #aws #github #npm #trufflehog #go #cyberattack #ShaiHulud #javascript #deno #browser #Sha1Hulud
@nullagent@partyon.xyz · Reply to nullagent's post
These sorts of NPM worms have been around for a LONG time.
It's typically due a common practice of low 2fa opt-in on NPM accounts.
So be sure to setup NPM 2FA if you're a package maintainer do that asap!
A lesser known NPM capability is that you can disable install time scripts. This may break some packages but its worth a try to see if your projects can work with out any install scripts. 👇🏿
https://blog.npmjs.org/post/141702881055/package-install-scripts-vulnerability

@nullagent@partyon.xyz · Reply to nullagent's post
Now that the acute phase is slowing there's a VERY important question...
What is actual fucking value does Microsoft (a trillion dollar company) owning GitHub & NPM bring at all?
This shit was an absolute corporate buyout disaster. How the ever living fuck has microsoft owned NPM for FIVE years and still not done proper MFA requirements for publishing packages on NPM.
How the actual fuck are well known vulnerable packages STILL being propagated by NPM.
@nullagent@partyon.xyz · Reply to nullagent's post
I spent more time searching for other Sha1-Hulud detection tools and found four more bringing it to 6 scanners (5 in nodejs).
Linked them all from my readme in case those work better for you.
Best way to beat a worm like this is to keep scanning and keep an eye out for the attacker to try and evade all of our tools.
By using more than one hopefully we make the attackers job harder to evade all of us.
https://github.com/datapartyjs/walk-without-rhythm?tab=readme-ov-file#similar-tools
#Sha1Hulud #WalkWithoutRhythm #nodejs #npm #github #microsoft
@nullagent@partyon.xyz · Reply to nullagent's post
GitHub has almost finished taking down the stolen data posted by the Sha1-Hulud npm/github worm. I only see about 400 repos remaining of the around 23k created by the worm.
This was the most visible evidence of the exploit, just because we can't clearly see the worm's uploads doesn't mean the worm is totally dead yet.
@nullagent@partyon.xyz · Reply to nullagent's post
I spent more time searching for other Sha1-Hulud detection tools and found four more bringing it to 6 scanners (5 in nodejs).
Linked them all from my readme in case those work better for you.
Best way to beat a worm like this is to keep scanning and keep an eye out for the attacker to try and evade all of our tools.
By using more than one hopefully we make the attackers job harder to evade all of us.
https://github.com/datapartyjs/walk-without-rhythm?tab=readme-ov-file#similar-tools
#Sha1Hulud #WalkWithoutRhythm #nodejs #npm #github #microsoft
@nullagent@partyon.xyz · Reply to nullagent's post
Just finished landing Exit Code support. So now if more scanners are made or one of the projects gets more features you can quickly switch to whichever makes the most sense for your use case!
I literally lost a ton of sleep on this volunteer incident response work so I'm going to go touch grass for a bit.
More hacks later tonight, still got some loose ends gnawing at me lol.
https://github.com/datapartyjs/walk-without-rhythm?tab=readme-ov-file#how-to-use
#nodejs #npm #javascript #Sha1Hulud #WalkWithoutRhythm #Sha1HuludScanner #cybersecurity
@nullagent@partyon.xyz · Reply to nullagent's post
The fork of the CrowdStrike scanner introduced me to a really good idea, I should support the same exit code design so that our tools can work in tandem.
Maybe we detect different things or maybe one vs the other works in your environment.
So I made an issue to track this support:
https://github.com/datapartyjs/walk-without-rhythm/issues/18
#CrowdStrike #Sha1HuludScanner #WalkWithoutRhythm #cybersecurity #npm #nodejs
@nullagent@partyon.xyz · Reply to nullagent's post
I located a second tool for detecting Sha1-Hulud infections. Haven't looked at the details of how it works.
Some notes:
This one appears to have been released by CrowdStrike and was paywalled. Someone decided to modify and release it publicly so license is unknown.
But awesome to see I'm in the big leagues with CrowdStrike and I maybe the first clean open source release of a tool for this.
https://github.com/TimothyMeadows/sha1hulud-scanner
#Sha1Hulud #Sha1HuludScanner #NPM #nodejs #cybersecurity #opensource
@nullagent@partyon.xyz · Reply to nullagent's post
Checking back in on my GitHub query and the stolen data is STILL showing up on github.
I can tell github looks to be deleting the repos a -little- bit faster than they are created. There's still over 15k repos full of stolen credentials and PII available for public download.
I've also noticed some new behavior I hadn't seen before where the worm is now making commits look like Linus Torvalds wrote them. Clearly a delay tactic.
@nullagent@partyon.xyz · Reply to nullagent's post
At the end of scanning for obvious compromise the `check-projects` script then builds a listing of all of your dependencies and all of the versions your project files mention.
You can find that info under `reports/`
I'm currently working on improving the `check-projects` script so that it will alert you if ANY of your package.json or package-lock.json mentions a known infected package.
#ShalHulud #WalkWithoutRhythm #npm #github #javascript #cybersecurity #threatresponse
@nullagent@partyon.xyz · Reply to nullagent's post
First pass is super simple and just looks for the file names & package.json signature for signs of infection anywhere in the path you tell it to search.
If it sees anything fishy it tells you where and stops until you've read the alert.
Oh and this only uses bash, sed, awk, grep, curl, and jq. So no npm, node or other big supply chains 🥴
https://github.com/datapartyjs/walk-without-rhythm/blob/main/check-projects
#ShalHulud #WalkWithoutRhythm #nodejs #npm #github #javascript
@nullagent@partyon.xyz · Reply to nullagent's post
Woot ok now that I have the dependency graph crawled I can just ship the listing of known bad NPM packages and just compare directly against that.
I updated the scanning script to alert if you have -any- version of an infected package.
You're gonna want to be very careful if you're not infected but have one of these dependencies present.
https://github.com/datapartyjs/walk-without-rhythm/blob/main/data/infected-pkgs-versions.txt
#ShalHulud #WalkWithoutRhythm #npm #github #javascript #cybersecurity #threatresponse
@nullagent@partyon.xyz · Reply to nullagent's post
At the end of scanning for obvious compromise the `check-projects` script then builds a listing of all of your dependencies and all of the versions your project files mention.
You can find that info under `reports/`
I'm currently working on improving the `check-projects` script so that it will alert you if ANY of your package.json or package-lock.json mentions a known infected package.
#ShalHulud #WalkWithoutRhythm #npm #github #javascript #cybersecurity #threatresponse
@nullagent@partyon.xyz · Reply to nullagent's post
First pass is super simple and just looks for the file names & package.json signature for signs of infection anywhere in the path you tell it to search.
If it sees anything fishy it tells you where and stops until you've read the alert.
Oh and this only uses bash, sed, awk, grep, curl, and jq. So no npm, node or other big supply chains 🥴
https://github.com/datapartyjs/walk-without-rhythm/blob/main/check-projects
#ShalHulud #WalkWithoutRhythm #nodejs #npm #github #javascript
@nullagent@partyon.xyz · Reply to nullagent's post
I'm quickly finding a mix of packages which were compromised, some were months ago and had the bad versions taken down.
However at the same time I'm noticing packages like the one below that were -just- hacked 19 hours ago and still have not been taken down yet!
With how this worm works its a bit of a pencils down moment... you probably should check your packages right now.
https://www.npmjs.com/package/capacitor-voice-recorder-wav?activeTab=code
@nullagent@partyon.xyz · Reply to nullagent's post
I've spent the last few hours writing down my scripts for detecting this so you can use them!
I'm hitting on two or three ways to detect it and will be adding more.
Watching the attack running I can see developers all over the world still doing their morning `npm i` and getting owned 😭
Maybe let the node developers in your life know about this tool 👇🏿
https://github.com/datapartyjs/walk-without-rhythm
#ShaiHulud #WalkWithoutRhythm #nodejs #javascript #npm #github #cybersecurity
@nullagent@partyon.xyz · Reply to nullagent's post
Ok I've downloaded some of the compromised packages and you can search your already downloaded node modules for possibly infected packages using this command:
find ./node_modules -type f -name "bun_environment.js"
You can check your user level node cache using:
find ~/.npm -type f -name "bun_environment.js"
Still sizing this one up but if you get any hits check and see if they are big files (around 10MB) and if so you're likely infected.
@nullagent@partyon.xyz · Reply to nullagent's post
Taking a second to understand the attack rate. I constructed this query below which shows you essentially an up to date listing of developers/code that's been compromised.
Once your box is infected and PII data has been found the worm then uses your github credentials to upload that content so ANYONE can now steal your credentials.
I'm finding multiple repos being popped every minute. This is an extremely active attack right now.
@nullagent@partyon.xyz · Reply to nullagent's post
I'm quickly finding a mix of packages which were compromised, some were months ago and had the bad versions taken down.
However at the same time I'm noticing packages like the one below that were -just- hacked 19 hours ago and still have not been taken down yet!
With how this worm works its a bit of a pencils down moment... you probably should check your packages right now.
https://www.npmjs.com/package/capacitor-voice-recorder-wav?activeTab=code
@nullagent@partyon.xyz
#Breaking There's an active nodejs supply chain attack going around.
From the looks of it many of these compromised packages have been mitigated but quite a few have not.
https://helixguard.ai/blog/malicious-sha1hulud-2025-11-24
#nodejs #cybersecurity #aws #github #npm #trufflehog #go #cyberattack #ShaiHulud #javascript #deno #browser #Sha1Hulud
@soatok@furry.engineer
Moving Beyond the NPM elliptic Package
If you're in a hurry, head on over to soatok/elliptic-to-noble and follow the instructions in the README in order to remove the elliptic package from your project and all dependencies in node_modules. Art: CMYKat Why replace the elliptic package? Yesterday, the Trail of Bits blog published an intern's post about finding cryptographic bugs in the elliptic library (a Javascript package on NPM) by using the Wycheproof.
http://soatok.blog/2025/11/19/moving-beyond-the-npm-elliptic-package/
#npm #crypto #cryptography #elliptic #security #infosec #cve #mitigation #appsec #javascript #js #npm #npmsecurity #npmpackages
@soatok@furry.engineer
Moving Beyond the NPM elliptic Package
If you're in a hurry, head on over to soatok/elliptic-to-noble and follow the instructions in the README in order to remove the elliptic package from your project and all dependencies in node_modules. Art: CMYKat Why replace the elliptic package? Yesterday, the Trail of Bits blog published an intern's post about finding cryptographic bugs in the elliptic library (a Javascript package on NPM) by using the Wycheproof.
http://soatok.blog/2025/11/19/moving-beyond-the-npm-elliptic-package/
#npm #crypto #cryptography #elliptic #security #infosec #cve #mitigation #appsec #javascript #js #npm #npmsecurity #npmpackages
@vladimirleonidovich@mastodon.social
@toxi@mastodon.thi.ng
An update: After several failed publish attempts, more searching, (re)reading and experimenting for the past 4 hours, I've now figured out a solution using #NPM granular access tokens... But to summarize & document the issues, in case someone else encounters the same pain points:
1) There seems to be a new incompatibility between the NPM auth changes and running `yarn npm publish --access public`. After working successfully for the past 8 years, that command now gives me 404, even after re-authenticating. It just doesn't seem to pick up the auth token configured in `$HOME/.npmrc`. As result I've now switched all my publish commands to just be `npm publish --access public`. That seems to work!
2) The wording about the 50 package limit on the NPM auth token docs is very confusing: "Each token can access up to 50 organizations, and up to either 50 packages, 50 scopes, or a combination of 50 packages and scopes." As written, this reads like these limits are omnipresent for each token, but in fact one can also create tokens which can access ALL packages under your control. The 50 limit only seems to apply when creating token which is only allowed a subset...
Summa summarum, it is #ThingUmbrella #ReleaseFriday after all (updates to https://thi.ng/geom, bug fixes for https://thi.ng/args) and I can now proceed to enjoy the start of the Glühwein season on this cold Friday night... 🎉

@patrick@hatoya.cafe
One Open-source Project Daily
The NPM drinking game recreated and cli-ified with Deno
https://github.com/ninest/drink-if-exists
#1ospd #opensource #deno #drinkinggame #game #npm

@patrick@hatoya.cafe
One Open-source Project Daily
The NPM drinking game recreated and cli-ified with Deno
https://github.com/ninest/drink-if-exists
#1ospd #opensource #deno #drinkinggame #game #npm
@zkat@toot.cat
lmao now legitimate security emails from NPM are considered phishing. What a shitshow.
@lovell@mastodon.social
🔒 If you publish packages to the npm registry and haven't already seen its new Trusted Publisher feature, please do take a look at https://docs.npmjs.com/trusted-publishers
🎟️ It uses short-lived OIDC tokens to allow CI-based automation of signed publish-with-provenance.
📈 According to https://github.com/sxzz/npm-top-provenance I maintain 6 of the top 50 packages that use this feature, and those 6 packages combined have over 600 million downloads each month!
@lovell@mastodon.social
🔒 If you publish packages to the npm registry and haven't already seen its new Trusted Publisher feature, please do take a look at https://docs.npmjs.com/trusted-publishers
🎟️ It uses short-lived OIDC tokens to allow CI-based automation of signed publish-with-provenance.
📈 According to https://github.com/sxzz/npm-top-provenance I maintain 6 of the top 50 packages that use this feature, and those 6 packages combined have over 600 million downloads each month!
@iamwaseem@mastodon.social
It's been some weeks with npm exploits. But there is a fix, Deno's limited permissions can help here.
https://deno.com/blog/deno-protects-npm-exploits
@iamwaseem@mastodon.social
It's been some weeks with npm exploits. But there is a fix, Deno's limited permissions can help here.
https://deno.com/blog/deno-protects-npm-exploits
@iamwaseem@mastodon.social
It's been some weeks with npm exploits. But there is a fix, Deno's limited permissions can help here.
https://deno.com/blog/deno-protects-npm-exploits
@dsilverz@calckey.world
#NPM from #Node.js ended up in the hands of Microsoft.
#RubyGems from #Ruby ended up in the hands of a nazi libertarian.
It feels like #OSS and #FOSS are being attacked on a daily basis.
Do anyone have information regarding #PyPi from #Python, is it also compromised? As far as I know, PyPi stopped working with pip search ("Use the browser") and the website needs JS to function (because it uses some PoW browser checking), so using Lynx or elinks as a sysadmin on a terminal-only machine in order to search for Python packages have been a no-no. Wonder how much it's due to similar phenomenon going on with Ruby and Node.js ecosystems.
@zkat@toot.cat
cross-posting my little rant about #npm #npmattack #javascript #typescript stuff here:
Random NPM thoughts of the day:
Furthermore, the registry MUST provide the following, based on this:
I think that's all I got off the top of my head for now.
There's honestly a lot of stuff that could be done on the client side to make life better, too, and y'all know I have a ton of thoughts on that, but I wanted to rant about registries for a bit, esp now that the NPM registry is crumbling.
@tanepiper@tane.codes
Oh no, not again... a meditation on #NPM supply chain attacks
https://tane.dev/2025/09/oh-no-not-again...-a-meditation-on-npm-supply-chain-attacks/
@tanepiper@tane.codes
Oh no, not again... a meditation on #NPM supply chain attacks
https://tane.dev/2025/09/oh-no-not-again...-a-meditation-on-npm-supply-chain-attacks/
@thisismissem@hachyderm.io · Reply to Emelia 👸🏻's post
Also, npm now supports trusted publishing: https://docs.npmjs.com/trusted-publishers
This means you don't need a static token in your CI/CD configuration anymore.
@thisismissem@hachyderm.io
Pro-tip for npm: rather than using a classic access token in your ~/.npmrc file, generate a granular access token that only has read permissions.
That way if something does compromise you, they only get access to the read token and cannot publish on your behalf.
@derekheld@infosec.exchange
A bunch of packages published by qix in NPM just got backdoored it looks like. Obfuscated code was added like two hours ago. #threatintel #npm
@ben@hardill.me.uk
@ben@hardill.me.uk

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@hongminhee@hollo.social
Introducing #Upyo!
A simple, cross-runtime email library that works seamlessly on #Deno, #Node.js, #Bun, and edge functions. Zero dependencies, unified API, and excellent testability with built-in mock transport.
Switch between #SMTP, #Mailgun, #SendGrid without changing your code. Available on #JSR & #npm!

@BastilleBSD@fosstodon.org
Are npm packages and dependencies an unmitigated disaster, or is it just me?
@Alex0007@mastodon.social
 🚲 🇳🇱
🚲 🇳🇱@lil5@social.linux.pizza
| Option | Voters |
|---|---|
| Deno | 4 (57%) |
| Bun | 3 (43%) |
@skry@mastodon.social
“slopsquatting, a new term for a surprisingly effective type of software supply chain attack that emerges when LLMs “hallucinate” package names that don’t actually exist. If you’ve ever seen an AI recommend a package and thought, “Wait, is that real?”—you’ve already encountered the foundation of the problem.
And now attackers are catching on.”
The Rise of Slopsquatting: How #AI Hallucinations Are Fueling... https://socket.dev/blog/slopsquatting-how-ai-hallucinations-are-fueling-a-new-class-of-supply-chain-attacks #npm #dev #infosec
Edit: more info: https://www.bleepingcomputer.com/news/security/ai-hallucinated-code-dependencies-become-new-supply-chain-risk/
@skry@mastodon.social
“slopsquatting, a new term for a surprisingly effective type of software supply chain attack that emerges when LLMs “hallucinate” package names that don’t actually exist. If you’ve ever seen an AI recommend a package and thought, “Wait, is that real?”—you’ve already encountered the foundation of the problem.
And now attackers are catching on.”
The Rise of Slopsquatting: How #AI Hallucinations Are Fueling... https://socket.dev/blog/slopsquatting-how-ai-hallucinations-are-fueling-a-new-class-of-supply-chain-attacks #npm #dev #infosec
Edit: more info: https://www.bleepingcomputer.com/news/security/ai-hallucinated-code-dependencies-become-new-supply-chain-risk/
@richiekhoo@hachyderm.io
Package Manager for Markdown
I'm working on a project that is intended to encourage folk to make markdown text files which can be bundled together in different bundles of text files using a package manager.
Question for coders; Which package manager would you suggest I use?
Main criterias (in order) are:
1. Easy for someone with basic command line skills to edit the file and update version numbers and add additional packages.
2. All being equal, more commonly and easy to setup is preferred.
#Markdown #CommonMark #PackageManager #Programming #Dev
#NPM #RubyGems #Cargo #PickingAMastodonInstance
#Ruby #Python #Rust #Javascript #NodeJs #Lisp #CommonGuide
@mapache@hachyderm.io
Rust cargo is the new npm-packages lol
@cheeaun@mastodon.social
Huh, Runkit has been gone for few months and npm pages are still linking to it https://github.com/orgs/community/discussions/141424
The forum is also filled with reports and spam https://discuss.runkit.com/ 😥
@deno_land@fosstodon.org
Are you still using npm transpile services like esm.sh and unpkg.com?
❌ dependency deduplication
❌ install hooks and native add-ons
❌ loading data files
Here's why we recommend importing npm packages natively via npm specifiers 👇
https://deno.com/blog/not-using-npm-specifiers-doing-it-wrong
@inautilo@mastodon.social
#Development #Launches
SQL Noir · A game to learn SQL by solving crimes https://ilo.im/162ciw
_____
#OpenSource #Game #Database #SQL #MySQL #SQLite #PostgreSQL #Npm #WebDev #Backend
@inautilo@mastodon.social
#Development #Launches
SQL Noir · A game to learn SQL by solving crimes https://ilo.im/162ciw
_____
#OpenSource #Game #Database #SQL #MySQL #SQLite #PostgreSQL #Npm #WebDev #Backend
@thisismissem@hachyderm.io
@deno_land@fosstodon.org
Are you still using npm transpile services like esm.sh and unpkg.com?
❌ dependency deduplication
❌ install hooks and native add-ons
❌ loading data files
Here's why we recommend importing npm packages natively via npm specifiers 👇
https://deno.com/blog/not-using-npm-specifiers-doing-it-wrong
@cryptadamist@universeodon.com · Reply to @reiver ⊼ (Charles) :batman:'s post
@reiver i built on #fedialgo to make a customizable feed algorithm that is pretty much how i interact with #mastodon these days. it's available as an #npm package.
here's the demo app: https://github.com/michelcrypt4d4mus/fedialgo_demo_app_foryoufeed
this is what the demo app looks like:
#CustomFeeds #FediDevs #FediverseCustomFeeds #FediverseFeeds #FediverseUX
@cryptadamist@universeodon.com · Reply to @reiver ⊼ (Charles) :batman:'s post
@reiver i built on #fedialgo to make a customizable feed algorithm that is pretty much how i interact with #mastodon these days. it's available as an #npm package.
here's the demo app: https://github.com/michelcrypt4d4mus/fedialgo_demo_app_foryoufeed
this is what the demo app looks like:
#CustomFeeds #FediDevs #FediverseCustomFeeds #FediverseFeeds #FediverseUX
@standarski@mastodon.social
🚀 npm install vs. npm ci
• npm install: 📦 Installs dependencies from package.json, updates package-lock.json if needed. Flexible but slower.
• npm ci: ⚡ Clean, fast install based only on package-lock.json. Reproducible builds, perfect for CI/CD.
💡Tip: Use npm ci for consistent, reliable deployments! ✅
#javascript #npm
@standarski@mastodon.social
🚀 npm install vs. npm ci
• npm install: 📦 Installs dependencies from package.json, updates package-lock.json if needed. Flexible but slower.
• npm ci: ⚡ Clean, fast install based only on package-lock.json. Reproducible builds, perfect for CI/CD.
💡Tip: Use npm ci for consistent, reliable deployments! ✅
#javascript #npm
@deno_land@fosstodon.org
Deno 🤝️ Nuxt.js
@deno_land@fosstodon.org
Deno 🤝️ Nuxt.js
@deno_land@fosstodon.org
Deno 🤝️ Nuxt.js
@deno_land@fosstodon.org
Deno 2.1.5 just landed —
▸ new QUIC API
▸ improved Discord.js compatibility
▸ better tasks support in workspaces
@deno_land@fosstodon.org
Deno 2.1.5 just landed —
▸ new QUIC API
▸ improved Discord.js compatibility
▸ better tasks support in workspaces
@deno_land@fosstodon.org
Deno 2.1.5 just landed —
▸ new QUIC API
▸ improved Discord.js compatibility
▸ better tasks support in workspaces
@deno_land@fosstodon.org
Deno 2.1.5 just landed —
▸ new QUIC API
▸ improved Discord.js compatibility
▸ better tasks support in workspaces
@deno_land@fosstodon.org
Deno is committed to web standards - that's why we co-founded WinterCG two years ago. Today marks the next step in that journey: WinterCG moves to Ecma International as technical comittee 55 (TC55).
Goodbye WinterCG, welcome WinterTC!
@deno_land@fosstodon.org
Deno is committed to web standards - that's why we co-founded WinterCG two years ago. Today marks the next step in that journey: WinterCG moves to Ecma International as technical comittee 55 (TC55).
Goodbye WinterCG, welcome WinterTC!
@deno_land@fosstodon.org
Deno 2.1.5 just landed —
▸ new QUIC API
▸ improved Discord.js compatibility
▸ better tasks support in workspaces
@deno_land@fosstodon.org
Deno is committed to web standards - that's why we co-founded WinterCG two years ago. Today marks the next step in that journey: WinterCG moves to Ecma International as technical comittee 55 (TC55).
Goodbye WinterCG, welcome WinterTC!
@deno_land@fosstodon.org
Deno is committed to web standards - that's why we co-founded WinterCG two years ago. Today marks the next step in that journey: WinterCG moves to Ecma International as technical comittee 55 (TC55).
Goodbye WinterCG, welcome WinterTC!
@deno_land@fosstodon.org
Thank you for your support in helping us reach 100,000 GitHub stars! ⭐️
@deno_land@fosstodon.org
Thank you for your support in helping us reach 100,000 GitHub stars! ⭐️
@deno_land@fosstodon.org
Deno can now finally be installed through npm!
npm install -g deno
npx deno eval -p 1+2
@thomasreggi@indieweb.social
Would love thoughts and feedback on my Future / deferred promise library:
https://www.npmjs.com/package/@reggi/future
Be kind ❤️
#JavasScript #js #npm #package #module #opensource #ts #typescript
@deno_land@fosstodon.org
Easily check for outdated dependencies with `deno outdated` 👇️
@deno_land@fosstodon.org
this wren wants to remind you that Deno permission flags have shorthands
@deno_land@fosstodon.org
Deno 2.1 is out 🎉️
✈️️ first class Wasm support
🌳️ Long Term Support branch
⭐️ Improved dependency management
and much more!
#deno #node #javascript #nodejs #typescript #webdev #npm #wasm
@angelikatyborska@mas.to
I wrote my thoughts on how to decide what's a regular dependency and what's a dev dependency in a JavaScript app (not library). It's surprisingly unclear... https://angelika.me/2024/11/11/dependencies-vs-dev-dependencies-javascript-apps/
@deno_land@fosstodon.org
Deno is a JavaScript package manager with more flexibility:
📦️ npm and JSR
🛠️️ package.json and deno.json
👟️ fast
@deno_land@fosstodon.org
The 🦕️ is out of the bag...
@deno_land@fosstodon.org
Curious about how the JSR logo and website design came together? 🤔️
Here's a 👀️ into our design process.
https://deno.com/blog/designing-jsr
#deno #node #javascript #typescript #webdevelopment #npm #jsr
@deno_land@fosstodon.org
Deno 1.46 is not only the last 1.x release, but also one of the biggest:
- Simpler CLI
- Multi-threaded web servers
- HTML, CSS, YAML support in `deno fmt`
- Better Node/npm compat (support for playwright, google-cloud, etc.)
and much more 👇️
@deno_land@fosstodon.org
Deno is known for its HTTP imports, but we've found it's insufficient for larger projects. This post explains the situation and how we've improved it.
@deno_land@fosstodon.org
std/data-structures, common data structures including red-black trees and binary heaps, is now stabilized at v1 on JSR
@fedify@hollo.social
The fedify command is now available on #npm! You can install it using the following command:
npm install -g @fedify/cli
Or if you use #Bun:
bun install -g @fedify/cli
@NosirrahSec@infosec.exchange
CVE-2023-49210 - node-openssl, this sounds like a malicious node package and it's just now popping in Defender Vulnerability Management inventories.
Did we miss some big story about this or is this just a case of the NVD backlog catching up and thus downstream ingestion of that information is just now making it to the masses?
I figured a malicious OSS package/update getting put into the ecosystem would be a hot article after the #xz #xz_utils debacle.
Anyone got better info than I do after doing some hunting? All I have are the initial detections from 3rd parties in November of 2023.