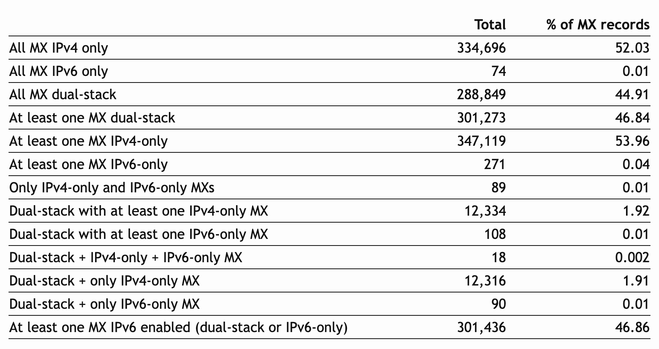
Remember the threads¹² about #LetsEncrypt removing a crucial key usage from certificates issued by them in predictive obedience to their premium sponsor Google?
We were at first concerned about #SMTP. While I had lived through this problem with #StartSSL by #StartCom back in 2011, I only had a vague recollection of Jabber but recalled in detail that it broke server-to-server SMTP verification (whether the receiving server acted on it or just documented it).
Well, turns out someone now reported that it indeed breaks #XMPP entirely: https://community.letsencrypt.org/t/do-not-remove-tls-client-auth-eku/237427/66
This means that it will soon no longer be possible at all to operate Jabber (XMPP) servers because the servers use the operating system’s CA certificate bundle for verification, which generally follows the major browsers’ root stores, which has requirements from the CA/Browser forum who apparently don’t care about anything else than the webbrowser, and so no CA whose root certificate is in that store will be allowed to issue certificates suitable for Jabber/XMPP server-to-server communication while these CAs are the only ones trusted by those servers.
So, yes, Google’s requirement change is after all breaking Jabber entirely. Ein Schelm, wer Böses dabei denkt.
While https://nerdcert.eu/ by @jwildeboer would in theory help, it’s not existent yet, and there’s not just the question of when it will be included in operating systems’ root CA stores but whether it will be included in them at all.
Google’s policy has no listed contact point, and the CA/B forum isn’t something mere mortals can complain to, so I’d appreciate if someone who can, and who has significant skills to argument this in English and is willing to, to bring it to them.
① mine: https://toot.mirbsd.org/@mirabilos/statuses/01JV8MDA4P895KK6F91SV7WET8
② jwildeboer’s: https://social.wildeboer.net/@jwildeboer/114516238307785904